Awesome work by @FICO #AI @ScottZoldi @FraudBird @shafi4uf , usage of #ML in #cybersecurity
In this pulse-pounding novel from the bestselling author of Butterf bit.ly/2gLWxG2 #Hacker #Cybersecurity

Top 7 US #tech #unicorns are valued at $10+ billion a piece. #startups #ipos #p2p #cybersecurity #rideshare bit.ly/2BKCTl0

Hacking with Python: The Ultimate Beginners Guide This book will sh bit.ly/2knXPWq #Hacker #Cybersecurity

NIST releases 2nd draft of the proposed v1.1 update to its "Framework for Improving Critical Infrastructure Cybersecurity" a/k/a the Cybersecurity Framework buff.ly/2AfP7VS #InfoSec #NIST #cybersecurity #CybersecurityFramework
Happy To Be Named Top 3 #Cybersecurity #Influencer, as well as a Top #IoT Influencer. Congrats to all my fellow #womenintech influencers as well!!! onalytica.com/blog/posts/wom… @CybersecuritySF @Onalytica @Centrify @IBMSecurity @ewfusa @theCUBE @securemysocial @PrimeTechPtr
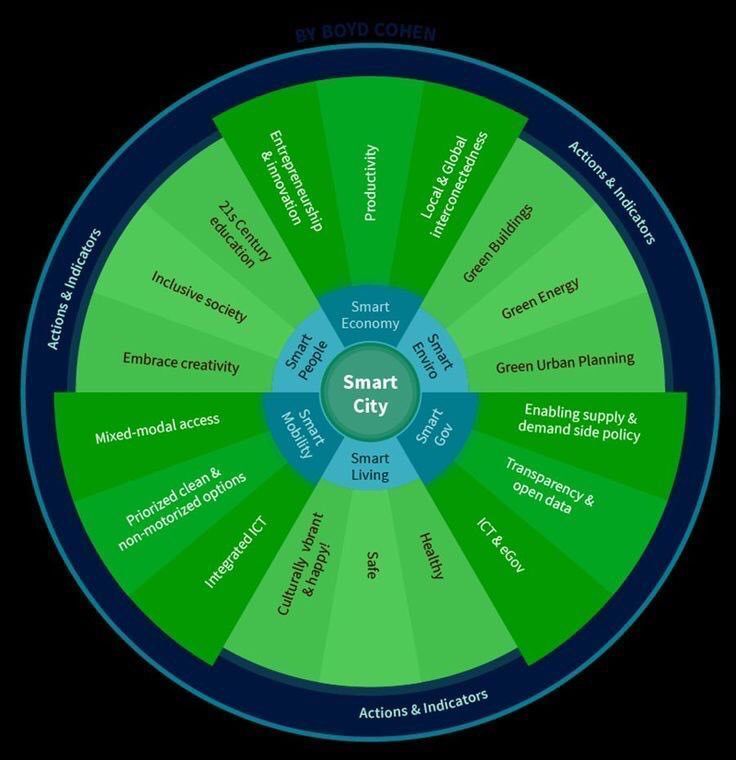
360° View of a SmartCity {#Infographic} #SmartCity #IoT #tech #innovation #CyberSecurity #DigitalTransformation #IIoT @Fisher85M
1 of the many fascinating parts of my job is the opp to interact w/ top level security pros. Great morning w/ Mike Badeaux VP of Information Security @AmericanEquity @TechnologyIowa #UniteIowaTech #CyberSecurity
The Smart Digital Life {Infographic} #SmartCity #IoT #BigData #CyberSecurity #Healthcare #Education #infosec #MachineLearning #AI #M2M

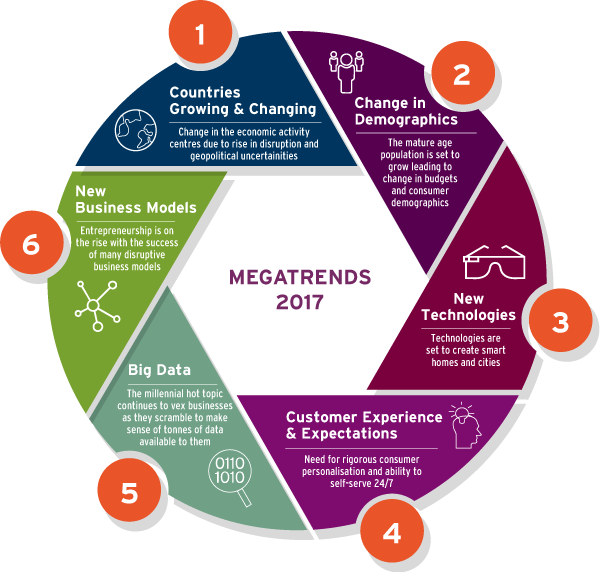
What are 6 #MegaTrends of 2017? #BigData #CX #Disuption #fintech #SmartCity #IoT #CyberSecurity #innovation #Entrepreneur #infosec MT @Fisher85M
"Critical Flaw in Major Android Tools Targets Developers and Reverse Engineers" thehackernews.com/2017/12/androi… #cybersecurity
Virtual keyboard app exposed data from 31 million users: bit.ly/2iXmc1p #cybersecurity

"Why phishers love HTTPS" helpnetsecurity.com/2017/12/06/why… #cybersecurity
@Scotiabank to partner with two #Israeli technology leaders to accelerate its digital transformation - #Cybersecurity newsamericasnow.com/scotiabank-to-…
63% of laptop use and 59% of tablet use for business is done from home, on the go, or at another non-office location. #cybersecurity my.sociabble.com/X32vvZ3U
my.sociabble.com
Do you trust technology with devices and data?
This infographic provides facts and figures about the value that technology can bring to businesses by improving mobility, collaboration, and security.
Firewalls, Network Address Translation (NAT), network logging and a bit.ly/1NNos2x #Hacker #Cybersecurity

Feature: 1. The EOVAS Charger Camera is the latest version,the char bit.ly/2oIy0WI #Hacker #Cybersecurity

Two-factor authentication made easy for hundreds of services! Yu bit.ly/2wUdVfJ #Hacker #Cybersecurity

The 2017 @Gartner_inc Hype Cycle for #Emerging #Technology | #IoT #VR #CyberSecurity #AR #blockchain #DL #5G #SaaS #AI #UX MT @Fisher85M

#Cybersecurity = preparation for new threats + coordination of the response. Encounters such as the Subregional Workshop 'Cybersecurity for Industrial Control Systems and Critical Infrastructure of the Electricity Sector' assure to move in the right way #OEACIP #OEAICS
United States 趨勢
- 1. phil 78.7K posts
- 2. phan 76.2K posts
- 3. Columbus 221K posts
- 4. President Trump 1.26M posts
- 5. Kincaid 1,550 posts
- 6. Doug Eddings N/A
- 7. Middle East 321K posts
- 8. Falcons 13.3K posts
- 9. Springer 11.1K posts
- 10. Gilbert 9,663 posts
- 11. Martin Sheen 1,446 posts
- 12. Mike McCoy N/A
- 13. Yesavage 3,229 posts
- 14. Monday Night Football 6,709 posts
- 15. Thanksgiving 60.7K posts
- 16. Go Bills 6,992 posts
- 17. Bijan 3,121 posts
- 18. Ray Ray 95.2K posts
- 19. Knox 3,112 posts
- 20. John Oliver 9,199 posts
Something went wrong.
Something went wrong.