You might like
Today i found a RCE in a bug bounty platform 1. found a bypass admin role with cve confluence 2. access and upload a plugin ( webshell) 3. turn on plugin in server and can run any system command HOPY THEY FAIR #BugBounty

The new writup is here: Account Takeover via Insecure Email Change — Critical Vulnerability medium.com/@3bddagg3/acco… #bugbountytips #bugbounty #hackerone
Through a simple path manipulation in the hostName parameter, I was able to escalate the issue into a One-Click Account Takeover medium.com/@Zeno_H2r/expl…
Tip: When testing, try injecting a null byte (\u0000) into unexpected parameters. You never know how the backend will handle it — sometimes a small injection can completely break features like the invitation system. #BugBounty #bugbountytips #Hacking #Cybersecurity

New Write-Up Published: One parameter. One click. One hijack. medium.com/@yassentaalab5… #BugBounty #bugbountytips
اللهم بارك بس انا عندي استفسار واتمنى ميتفهمش غلط ليه لما بشوف سيناريوهات زي دي بشوفها ساهلة ومع ان اغلب الحاجات دي بطبقها وانا بهانت بس عمرها ما جات لان استحالة حاجة زي دي تكون متسابة ودا بيخليني احس ان الناس دي البروجرامز بتاعتها غير بتاعتنا حرفيا بحسهم حاجة زي لابات بورتسويجر
hardcoded credentials in javascript file xxxxxxx/static/js/main.xxxxx.chunk.js 🗣️ dp #bugbounty #bugbountytips #bugbountytip

How I Found a Critical Password Reset Bug in the BB program(and Got $4,000) s41n1k.medium.com/how-i-found-a-… #bugbounty
s41n1k.medium.com
How I Found a Critical Password Reset Bug in the BB program(and Got $4,000)
As a bug bounty hunter, I often test mobile apps by routing traffic through Burp Suite to see how the backend APIs behave. One of my recent…
özlemişsinizdir. buyrun fırından taze çıktı dostlar youtube.com/watch?v=xNxyhD…

youtube.com
YouTube
Şaka Gibi Ama Değil: 1980’ler Protokolüyle 2025’te Tren Durdurmak...
Blind XSS on Admin Portal Leads to Information Disclosure medium.com/@rohit443/blin… #bugbounty #bugbountytips
The $1000 Critical Bug: Unauthorised Access Leading to Support Admin Panel Takeover v3d.medium.com/the-1000-criti… #bugbounty #bugbountytips #bugbountytip
"The Anotomy of Critical Bug" is now live on @InfoSecComm 🔗medium.com/bugbountywrite… #bugbountytip #bugbountytips #bugbounty #CyberSecurity #Security #infosec #appsec #Hacking #vapt
infosecwriteups.com
The Anatomy of a Critical Bug
A blank page. Quiet recon. A bug they never saw coming.
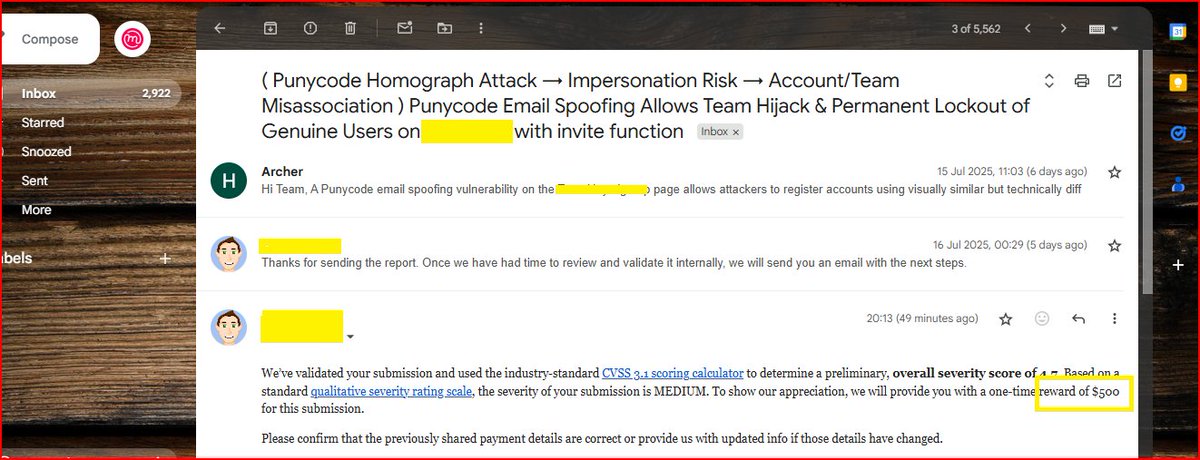
$500 for Punycode email spoofing bug. Used comilav “m” to bypass email uniqueness check: >Register with [email protected] > Use same name as legit user > Invite real user to fake team Real user joins attacker’s team - gets locked out of real one #bugbountytips #BugBounty
#CryptoSecurity 🚨 - A massive supply chain attack on the NPM registry has compromised popular packages with over 2 billion weekly downloads, aiming to steal cryptocurrency from users. dailydarkweb.net/major-npm-supp…

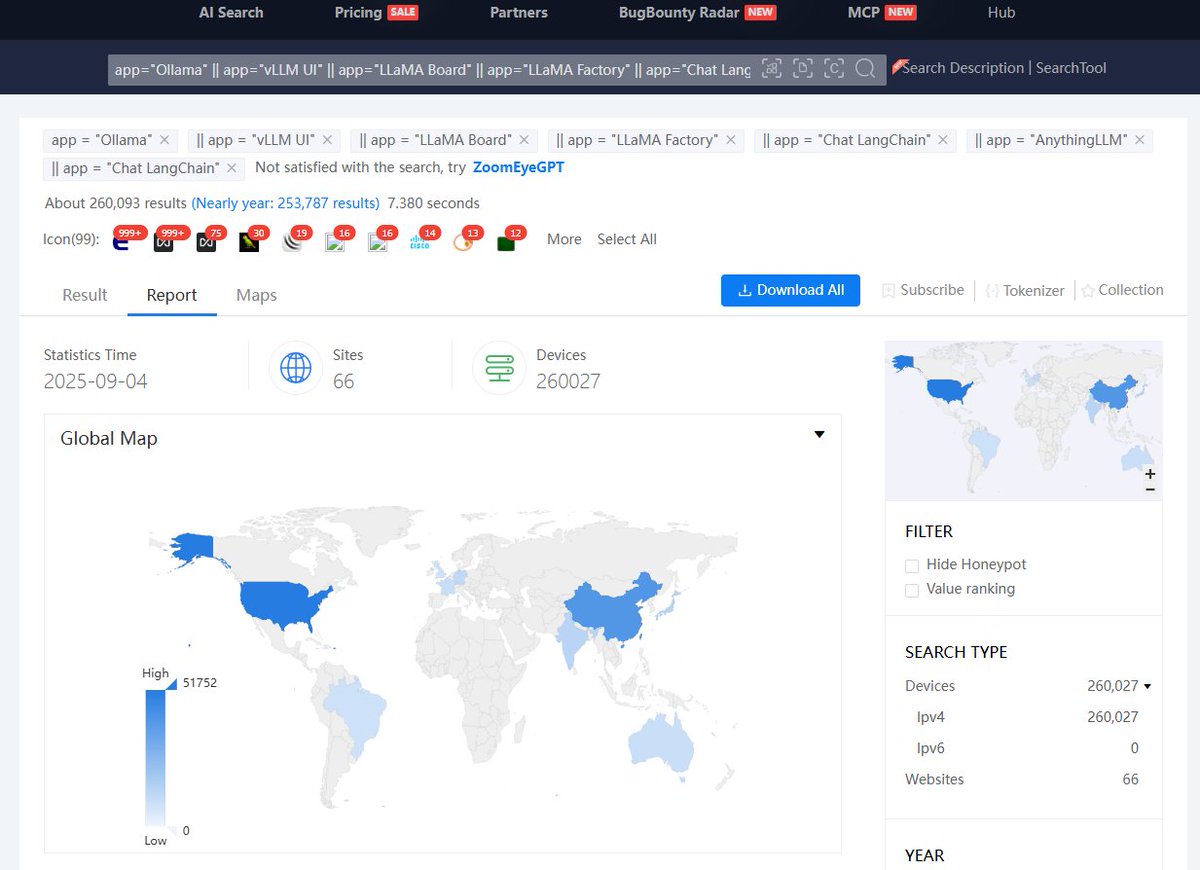
🔍Discover More Exposed LLM Servers with ZoomEye ZoomEye Dork👉app="Ollama" || app="vLLM UI" || app="LLaMA Board" || app="LLaMA Factory" || app="Chat LangChain" || app="AnythingLLM" || app="Chat LangChain" ZoomEye Link: zoomeye.ai/searchResult?q…
Exposed LLM server queries for @shodanhq port:11434 "Ollama" port:8000 "vLLM" port:8000 "llama.cpp" port:8080 "llama.cpp" port:1234 "LM Studio" port:4891 "GPT4All" port:8000 "LangChain" blogs.cisco.com/security/detec…
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


Alhamdulillah I got 3 RXSS duplicates on a public Bugcrowd program. Write-up: zuksh.medium.com/how-i-discover… #BugBounty #RXSS #XSS #InfoSec #Bugcrowd

1. Register an account using [email protected] 2. Navigate to change email 3. Change it to [email protected] 4. Boom 💥 become the administrator and infrastructure takeover Rewarded $$$$$ #fuckbountytips
New Video Out 🔥 “AWS S3 Bucket Hacking Explained (Bug Bounty Hunters Must Watch)” youtu.be/_UlHLjIQeJM?si…

United States Trends
- 1. #AEWWrestleDream 49.1K posts
- 2. Kentucky 24.4K posts
- 3. Lincoln Riley 2,358 posts
- 4. Mizzou 5,268 posts
- 5. Stoops 4,678 posts
- 6. Arch 25.3K posts
- 7. #RollTide 7,828 posts
- 8. Sark 4,322 posts
- 9. Bama 15.1K posts
- 10. Notre Dame 15.3K posts
- 11. Texas 168K posts
- 12. Tennessee 52.7K posts
- 13. #UFCVancouver 28.6K posts
- 14. Heupel 2,685 posts
- 15. No Kings 1.72M posts
- 16. #GoIrish 5,290 posts
- 17. Christian Gray N/A
- 18. #HookEm 2,411 posts
- 19. Utah 28.1K posts
- 20. Sam Rivers 17K posts
You might like
Something went wrong.
Something went wrong.