#authenticationprotocol 搜尋結果
#highlycited paper 📚 Improvement of a #ConditionalPrivacyPreserving and Desynchronization-Resistant #AuthenticationProtocol for #IoV 🔗 mdpi.com/2076-3417/14/6… 👨🔬 Qi Xie and Juanjuan Huang 🏫 @Study_In_HZNU
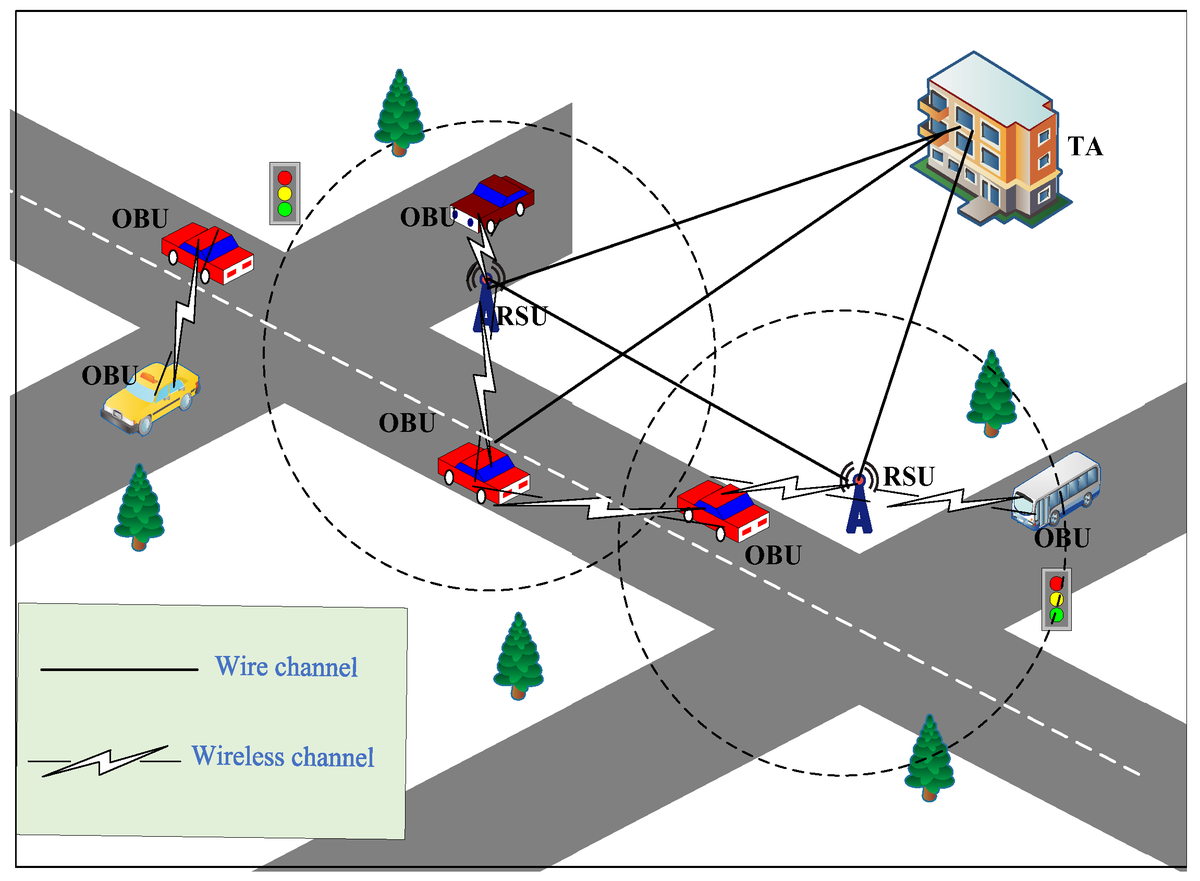
1) Securing #IoT-Based #RFID Systems: A Robust #AuthenticationProtocol Using #SymmetricCryptography 👉mdpi.com/1424-8220/19/2… #IoTSecurity #RFIDsecurity
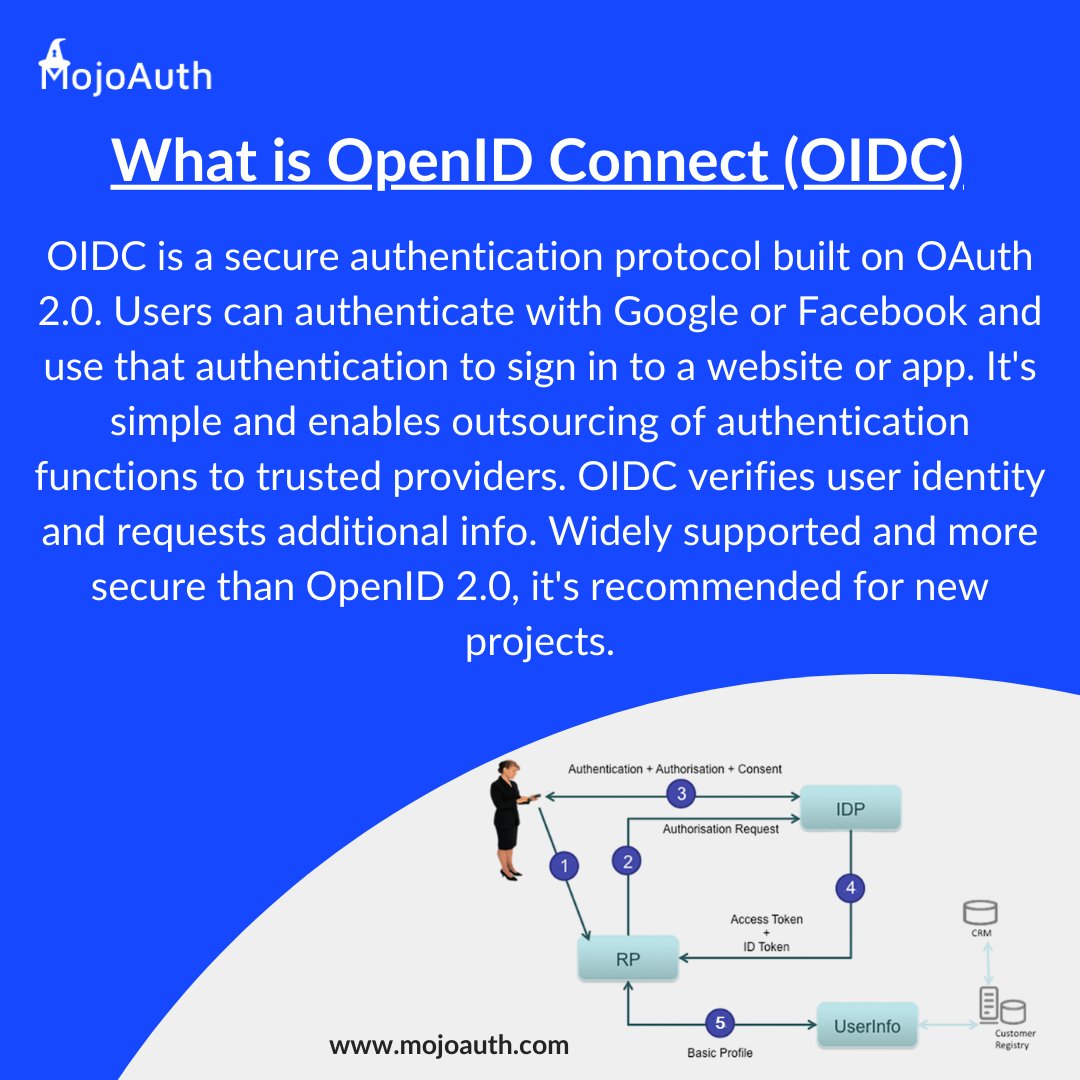
Discover OpenID Connect, the secure authentication protocol for multiple websites/apps! This article by MojoAuth covers its key features and how it differs from other protocols. mojoauth.com/glossary/openi… #OpenIDConnect #AuthenticationProtocol #OnlineSecurity #BestPractices
Unlock your potential with an in-depth understanding of EAP, a pivotal player in the #AuthenticationProtocol world. Get ahead and claim success in your #CCNPExam. 📘🔐 zpr.io/baz2snHqHYMQ

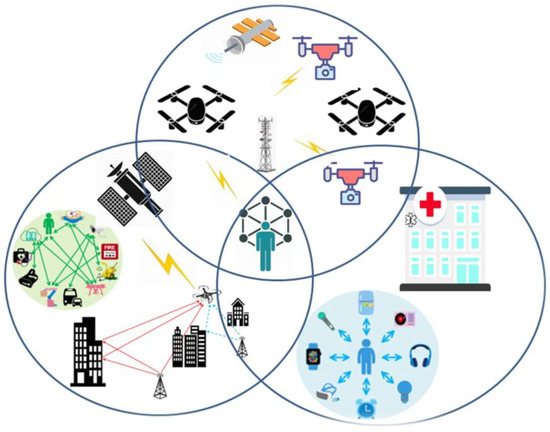
📢 Read our Review paper 📚 A Survey on #6G Enabled# LightWeight #AuthenticationProtocol for #UAVs, #Security, Open Research Issues and Future Directions 🔗 mdpi.com/2076-3417/13/1… 🏫 @UNIMASofficial #openaccess #unmannedaerialvehicles #network #topology #cryptography
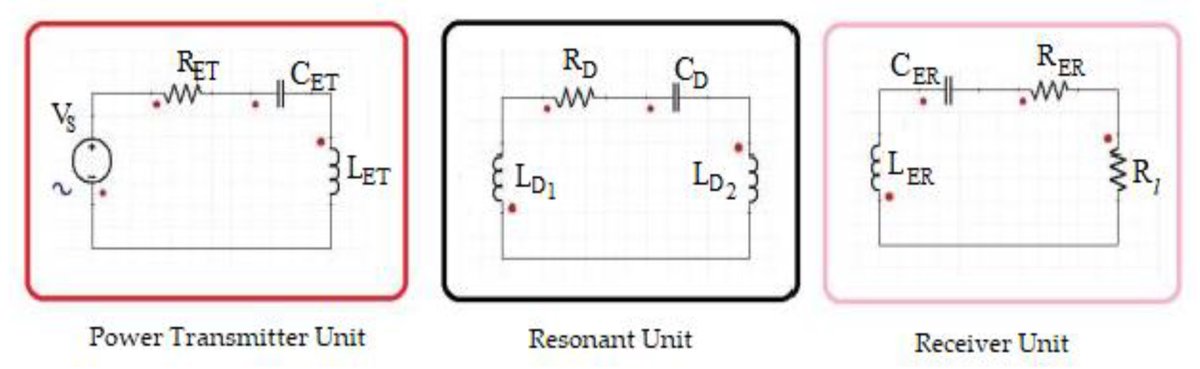
Efficient Authentication Protocol and Its Application in Resonant Inductive Coupling Wireless Power Transfer Systems mdpi.com/1424-8220/21/2… #chaosbasedcryptography #authenticationprotocol #wirelesspowertransfer
#AuthenticationProtocol for #CloudDatabases Using #Blockchain Mechanism by Gaurav Deep, Rajni Mohana, Anand Nayyar * et al. @UniDuyTan @OregonTech 👉mdpi.com/1424-8220/19/2… #cloudcomputing #security
Want to learn how to secure your network?#EAP #NetworkSecurity #AuthenticationProtocol #Cybersecurity facebook.com/share/r/19EN6y…
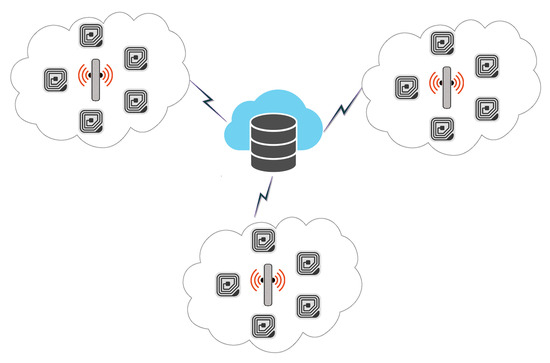
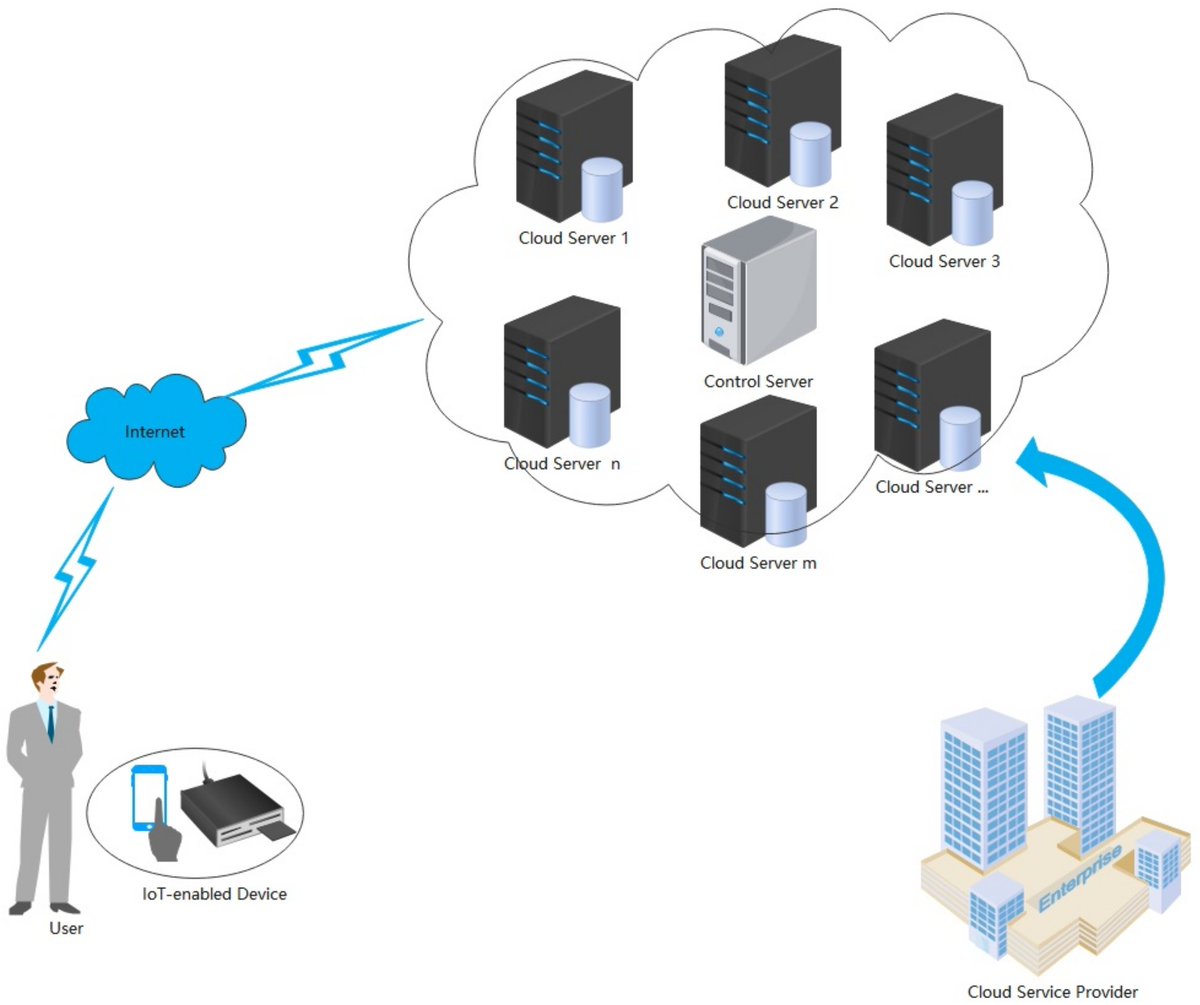
Rotating behind Security: A Lightweight Authentication Protocol Based on IoT-Enabled Cloud Computing Environments mdpi.com/1424-8220/22/1… #IoT #CloudComputing #AuthenticationProtocol #FormalSecurityAnalysis
When selecting an #authenticationprotocol, you need to be careful. The wrong one could undermine #security and limit future expansion. Check out these 4 #authentication use cases to determine which one is right for you. spr.ly/60191p48L @SuzeMorrow #SAML #OIDC #OAuth2
@_HM65_ Why has #PlanetEarth not been able to agree on a standard #AuthenticationProtocol? #ComputerSecurity
Security ... gkgk.us/1va1V4Q #AuthenticationProtocol #DeFactoStandard #HTTPSMarketCowboyRobot #WebServices
WPA2-Enterprise Authentication Protocols Comparison ... by Jake Ludin #authenticationprotocol #eap-tls #education #peap #ttls-pap securityboulevard.com/2019/10/wpa2-e…
Security Collapse In the ... #AuthenticationProtocol #DeFactoStandard #HTTPSMarketCowboyRobot #WebServices j.mp/1vajAti
sECUrITY Collapse n' teh HTtpz marKet goo.gl/fb/TlrwVz @BriansWebWorks #gamernews #authenticationprotocol
#highlycited paper 📚 Improvement of a #ConditionalPrivacyPreserving and Desynchronization-Resistant #AuthenticationProtocol for #IoV 🔗 mdpi.com/2076-3417/14/6… 👨🔬 Qi Xie and Juanjuan Huang 🏫 @Study_In_HZNU

Want to learn how to secure your network?#EAP #NetworkSecurity #AuthenticationProtocol #Cybersecurity facebook.com/share/r/19EN6y…
Rotating behind Security: A Lightweight Authentication Protocol Based on IoT-Enabled Cloud Computing Environments mdpi.com/1424-8220/22/1… #IoT #CloudComputing #AuthenticationProtocol #FormalSecurityAnalysis

Unlock your potential with an in-depth understanding of EAP, a pivotal player in the #AuthenticationProtocol world. Get ahead and claim success in your #CCNPExam. 📘🔐 zpr.io/baz2snHqHYMQ

📢 Read our Review paper 📚 A Survey on #6G Enabled# LightWeight #AuthenticationProtocol for #UAVs, #Security, Open Research Issues and Future Directions 🔗 mdpi.com/2076-3417/13/1… 🏫 @UNIMASofficial #openaccess #unmannedaerialvehicles #network #topology #cryptography

Discover OpenID Connect, the secure authentication protocol for multiple websites/apps! This article by MojoAuth covers its key features and how it differs from other protocols. mojoauth.com/glossary/openi… #OpenIDConnect #AuthenticationProtocol #OnlineSecurity #BestPractices

Efficient Authentication Protocol and Its Application in Resonant Inductive Coupling Wireless Power Transfer Systems mdpi.com/1424-8220/21/2… #chaosbasedcryptography #authenticationprotocol #wirelesspowertransfer

1) Securing #IoT-Based #RFID Systems: A Robust #AuthenticationProtocol Using #SymmetricCryptography 👉mdpi.com/1424-8220/19/2… #IoTSecurity #RFIDsecurity

#AuthenticationProtocol for #CloudDatabases Using #Blockchain Mechanism by Gaurav Deep, Rajni Mohana, Anand Nayyar * et al. @UniDuyTan @OregonTech 👉mdpi.com/1424-8220/19/2… #cloudcomputing #security

When selecting an #authenticationprotocol, you need to be careful. The wrong one could undermine #security and limit future expansion. Check out these 4 #authentication use cases to determine which one is right for you. spr.ly/60191p48L @SuzeMorrow #SAML #OIDC #OAuth2
WPA2-Enterprise Authentication Protocols Comparison ... by Jake Ludin #authenticationprotocol #eap-tls #education #peap #ttls-pap securityboulevard.com/2019/10/wpa2-e…
Security Collapse In the ... #AuthenticationProtocol #DeFactoStandard #HTTPSMarketCowboyRobot #WebServices j.mp/1vajAti
Security ... gkgk.us/1va1V4Q #AuthenticationProtocol #DeFactoStandard #HTTPSMarketCowboyRobot #WebServices
sECUrITY Collapse n' teh HTtpz marKet goo.gl/fb/TlrwVz @BriansWebWorks #gamernews #authenticationprotocol
@_HM65_ Why has #PlanetEarth not been able to agree on a standard #AuthenticationProtocol? #ComputerSecurity
#highlycited paper 📚 Improvement of a #ConditionalPrivacyPreserving and Desynchronization-Resistant #AuthenticationProtocol for #IoV 🔗 mdpi.com/2076-3417/14/6… 👨🔬 Qi Xie and Juanjuan Huang 🏫 @Study_In_HZNU

#AuthenticationProtocol for #CloudDatabases Using #Blockchain Mechanism by Gaurav Deep, Rajni Mohana, Anand Nayyar * et al. @UniDuyTan @OregonTech 👉mdpi.com/1424-8220/19/2… #cloudcomputing #security

1) Securing #IoT-Based #RFID Systems: A Robust #AuthenticationProtocol Using #SymmetricCryptography 👉mdpi.com/1424-8220/19/2… #IoTSecurity #RFIDsecurity

📢 Read our Review paper 📚 A Survey on #6G Enabled# LightWeight #AuthenticationProtocol for #UAVs, #Security, Open Research Issues and Future Directions 🔗 mdpi.com/2076-3417/13/1… 🏫 @UNIMASofficial #openaccess #unmannedaerialvehicles #network #topology #cryptography

Discover OpenID Connect, the secure authentication protocol for multiple websites/apps! This article by MojoAuth covers its key features and how it differs from other protocols. mojoauth.com/glossary/openi… #OpenIDConnect #AuthenticationProtocol #OnlineSecurity #BestPractices

Efficient Authentication Protocol and Its Application in Resonant Inductive Coupling Wireless Power Transfer Systems mdpi.com/1424-8220/21/2… #chaosbasedcryptography #authenticationprotocol #wirelesspowertransfer

Rotating behind Security: A Lightweight Authentication Protocol Based on IoT-Enabled Cloud Computing Environments mdpi.com/1424-8220/22/1… #IoT #CloudComputing #AuthenticationProtocol #FormalSecurityAnalysis

Unlock your potential with an in-depth understanding of EAP, a pivotal player in the #AuthenticationProtocol world. Get ahead and claim success in your #CCNPExam. 📘🔐 zpr.io/baz2snHqHYMQ

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 33.6K posts
- 2. Jonathan Taylor 9,533 posts
- 3. Jets 92.6K posts
- 4. #BroncosCountry 3,957 posts
- 5. Bengals 54.3K posts
- 6. Bo Nix 6,377 posts
- 7. Joe Milton 1,104 posts
- 8. Bucs 9,827 posts
- 9. Saints 30.6K posts
- 10. Riley Moss 1,336 posts
- 11. Eberflus 2,429 posts
- 12. #ForTheShoe 2,002 posts
- 13. Caleb 38.9K posts
- 14. Shough 3,506 posts
- 15. Eagles 123K posts
- 16. Giants 101K posts
- 17. RJ Harvey 2,519 posts
- 18. Jake Ferguson 1,833 posts
- 19. Rattler 5,717 posts
- 20. Dak Prescott 2,452 posts












