#cloudcomputingsecuritychallenges search results
Check out The Main Cloud Computing Security Challenges in 2022 #CloudComputingSecurityChallenges #CloudSecurityChallenges #CloudSecurityIssues #CloudSecurityRisks #CloudSecurityConcerns #SecurityChallengesInCloudComputing #Cloudcodes #CASB #cybersecurity bit.ly/3qYlpdl
Be Prepared With The Cloud Computing Security Challenges in Coming Years - See How to Combat Them? #CloudComputingSecurityChallenges #CloudComputingChallenges #CloudSecurityChallenges #ITSecurity #CloudCodes #CloudComputing #CloudSecurityRisks #CASB bit.ly/3qYlpdl
Enterprises have to be safe from their end and try to use a zero-trust security model in their premises. #CloudComputingSecurityChallenges #CloudSecurity #CloudComputing bit.ly/3qYlpdl
As per the CIO magazine, Device as a Service will unburden the technology departments with lower, access to recent technology. #DeviceAsaService #EnterpriseSecurity #CloudComputingSecurityChallenges bit.ly/30sN9fk
cloudcodes.com
Device As A Service - Lets See What Is It & How It Affects IT Efficiency
Covering the main aim to deliver this post then, Device as a Service is a new infrastructure to procure and manage business devices.
Be Prepared With The Cloud Computing Security Challenges in Coming Years - See How to Combat Them? #CloudComputingSecurityChallenges #CloudComputingChallenges #CloudSecurityChallenges #ITSecurity #CloudCodes #CloudComputing #CloudSecurityRisks #CASB bit.ly/3qYlpdl
Enterprises have to be safe from their end and try to use a zero-trust security model in their premises. #CloudComputingSecurityChallenges #CloudSecurity #CloudComputing bit.ly/3qYlpdl
As per the CIO magazine, Device as a Service will unburden the technology departments with lower, access to recent technology. #DeviceAsaService #EnterpriseSecurity #CloudComputingSecurityChallenges bit.ly/30sN9fk
cloudcodes.com
Device As A Service - Lets See What Is It & How It Affects IT Efficiency
Covering the main aim to deliver this post then, Device as a Service is a new infrastructure to procure and manage business devices.
💻 ¿Tu servidor va lento? ¿Tienes caídas? Lo auditamos gratis. #consultoriainformatica #infosecurity #cloud

⚠️🌩️ Microsoft SharePoint Online attacks on the rise! 🎣 Adversaries abuse: 🔸 Power Automate → stealthy exfiltration 🔸 OAuth & Graph → persistence 🔸 Guest links → lateral movement 🛡️ Defend by: 🚫 Disabling anonymous sharing 🔒 Reviewing Power Automate flows ✅ Auditing…

Hackers can get through three layers of verification but when @idOS_network kicks in, the scene changes sirens go off, and the system says ‘This is where it ends, buddy.’"

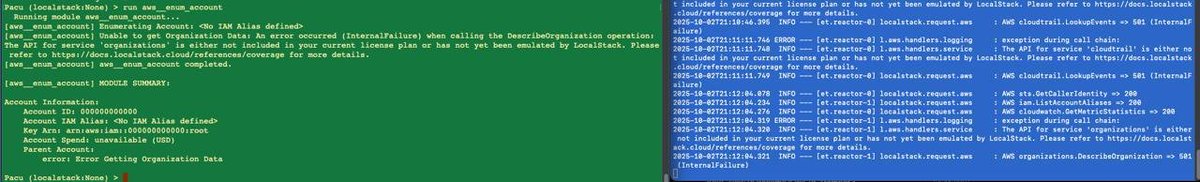
You can use Pacu, to test Cloud attacks and see their effects/logs in LocalStack. If more context is needed, let me know!
good morning. unfortunately, i’ve been compromised. the cloud storing your data was hacked last night. decentralized compute would’ve stopped this, but you faded computefi. by the way, your bank account balance is now 0.

Cyber Threat Intelligence (CTI): Finding C2 Servers, Malware and Botnets From Storm botnet's P2P networks to Twitter-based C2s hiding in plain sight - attackers constantly adapt. Learn to track them with modern CTI tools: hackers-arise.com/cyber-threat-i… @three_cube

Nothing to be scared about this Halloween season if you're with Net3. As a Private Cloud Provider, we prioritize your data's safety! Don't be afraid to reach out to talk to us - we don't bite! 🧛♂️🎃 hubs.ly/Q03Pj31g0 #IaaS #backup #cloudcomputing #disasterrecovery

Cloud Computing Cheat Sheet #infosec #cybersecurity #cybersecuritytips #microsoft #redteam #informationsecurity #CyberSec #microsoft #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness #bugbounty #bugbountytips

Can #cybersecurity withstand the new #AI era? buff.ly/n4B3FID #tech #AgenticAI #genAI #security #leadership #management #business #governance #cyberthreats #cyberattacks #databreaches #CISO #CIO #CTO #CEO @WEF @BatutaPlatform @BetaMoroney @ChuckDBrooks @YuHelenYu…

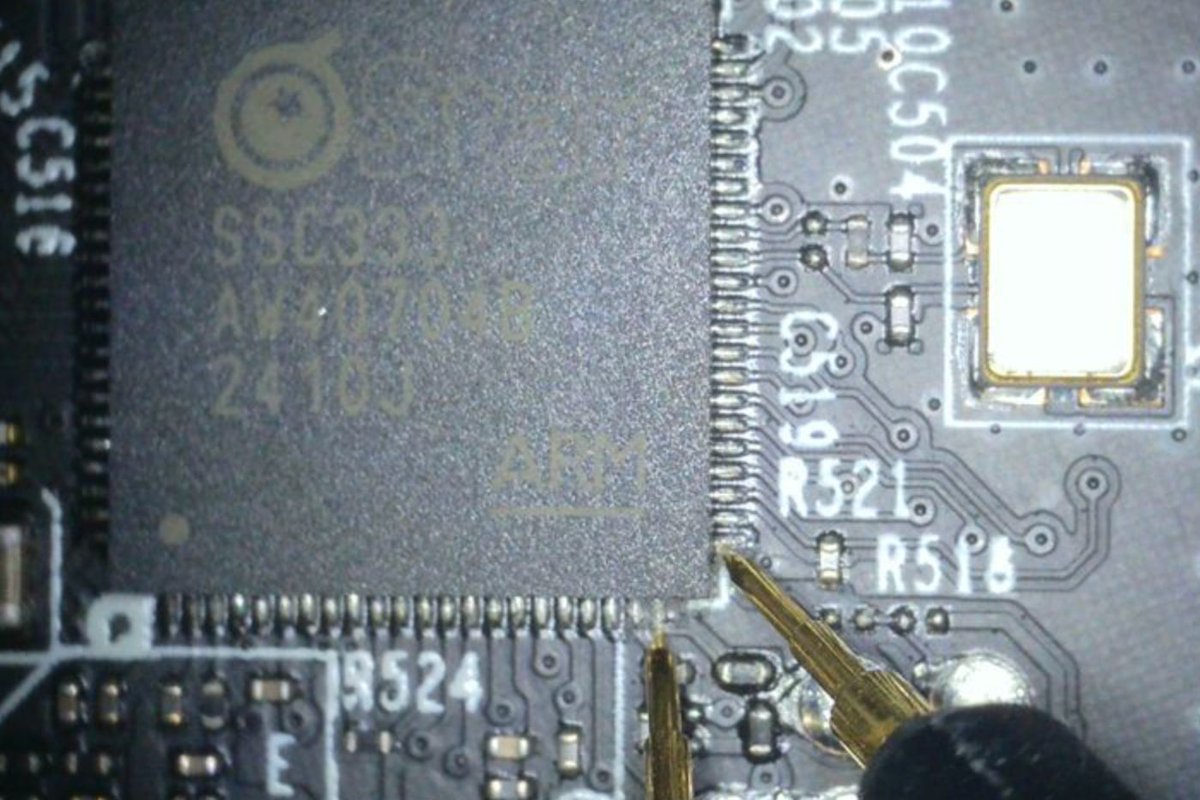
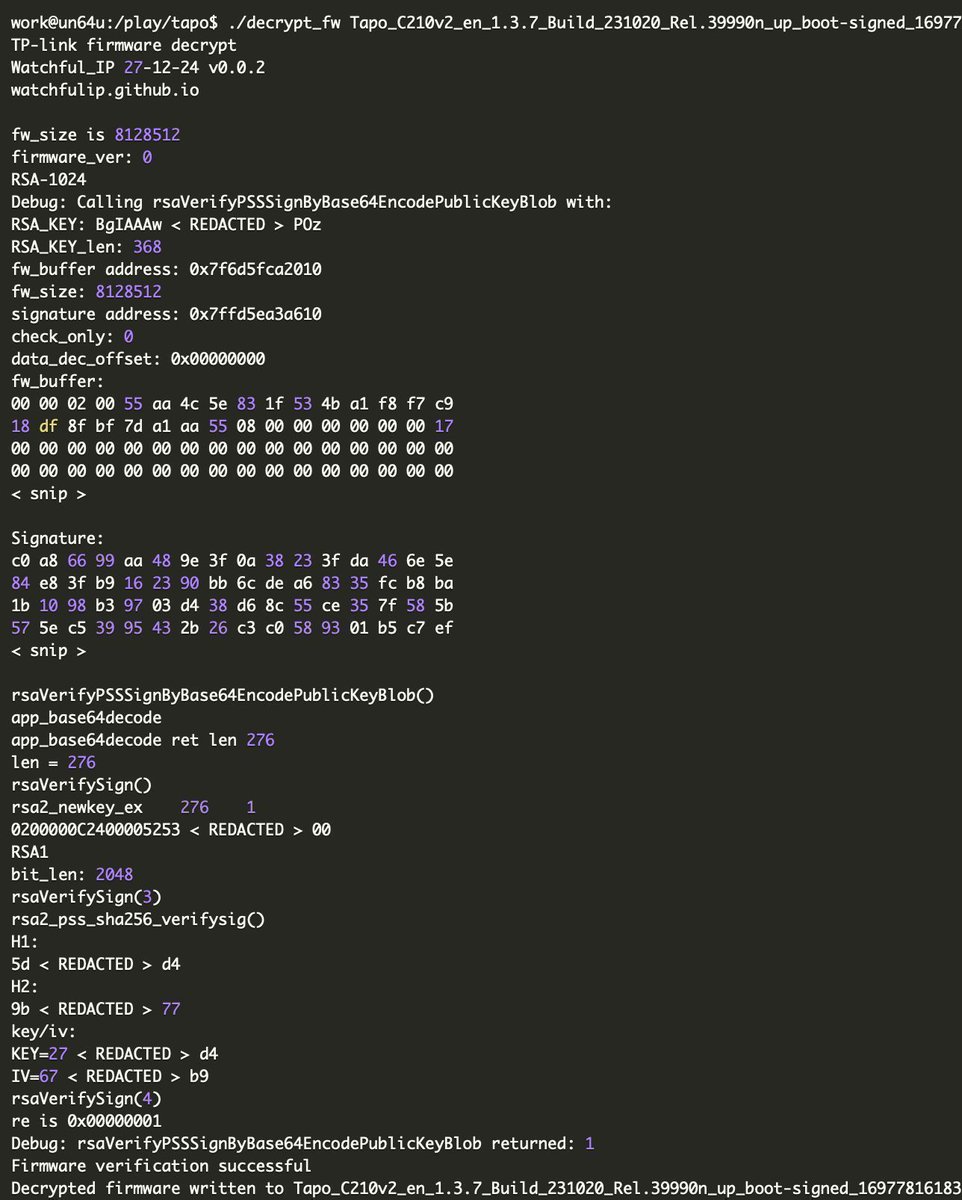
Bootloader vulnerability and firmware decryption in TP-Link (Tapo) C210 cloud cameras by @Watchful_IP watchfulip.github.io/28-12-24/tp-li… #embedded #cybersecurity
Case study - Exploiting ElizaOS To show the real-world consequences of these flaws, researchers examined ElizaOS, a decentralized AI-agent framework used for automated Web3 tasks. Their experiments empirically demonstrate that the system can be manipulated through contextual…
AI agents are powerful, but power always comes with risk A new study breaks down how context - the mix of prompts, memory, knowledge, and data might actually be an AI agent’s weakest spot When those layers meet, the attack surface multiplies. Think: - Direct & indirect prompt…
GOOD NIGHT LEGENDS! Klout’s Cross Chain Exploit NFTs turn blockchain security into a shared and transparent game of defense and discovery. Each NFT represents a verified exploit signature, discovered, reported, and resolved across Klout’s interconnected ecosystems. There are…

仅今年的10个月,就有数百家企业的云存储被攻破。 Salesforce的OAuth令牌被盗,影响了Google、Allianz、Cloudflare等巨头。 SonicWall的云备份系统被入侵,Ascension医疗系统的第三方云平台泄露了敏感患者信息。 每一次攻破都是同样的故事:中心化的单点故障。 —————————————————————————…

This scarecrow will drive away all possible risks of data leakage and keep them safe and secure forever.🔥🔥 Happy Halloween @irys_xyz 🎃🦇

Longer thread on how Cipher Protocol will protect you ⬇️ Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads. The…
![orithellama's tweet image. Longer thread on how Cipher Protocol will protect you ⬇️
Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads.
The…](https://pbs.twimg.com/media/G4ldzI1XEAA6I0l.jpg)
![orithellama's tweet image. Longer thread on how Cipher Protocol will protect you ⬇️
Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads.
The…](https://pbs.twimg.com/media/G4leLEsXwAAqQ-2.jpg)
Happy #Halloween!🎃While everyone's focused on costumes and candy, we're thinking about the real monsters hiding in #CloudEnvironments. Here are the 5 scariest mistakes you should NEVER make. Watch Webinar Replay👇 cqureacademy.com/webinars/repla… #AzureSecurity #CloudMisconfigurations




BYOD and #edge devices may be causing more #security headaches for your business - buff.ly/eFBrQIV #iot #iiot #cybersecurity #edgecomputing #tech #iotsecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Halloween 327K posts
- 2. YouTube TV 57K posts
- 3. #T1WIN 13.5K posts
- 4. Good Friday 35.1K posts
- 5. #RUNSEOKJIN_epTOUR_ENCORE 199K posts
- 6. THE TRUTH UNTOLD 25.8K posts
- 7. #FridayVibes 2,899 posts
- 8. Hulu 18.7K posts
- 9. Reformation Day 1,228 posts
- 10. #Jin_TOUR_ENCORE 180K posts
- 11. Mary Ann 1,175 posts
- 12. Faker 21.3K posts
- 13. Trick or Treat 298K posts
- 14. #PondPhuwinFanconD1 959K posts
- 15. Fubo 1,467 posts
- 16. YTTV N/A
- 17. ESPN and ABC 1,749 posts
- 18. Mindy 3,889 posts
- 19. Glue 6,280 posts
- 20. Ryan Rollins 13.6K posts























