#criticaldata 搜尋結果
Built on @Hedera #CriticalData #DataProtection #Web3 #DigitalAssets #Hashgraph #DLT #Hedera #HBAR $HBAR
The partnership between Taekion and Hedera Hashgraph is focused on leveraging the capabilities of both platforms to create a secure and efficient solution for storing and verifying critical data. Taekion, funded by the U.S. Department of Energy (DoE), United States Department…

Today is Computer Security Day! 💻 Always take steps to ensure your critical data is safe, including: 1. Utilizing unique, long and complex passwords 2. Enabling multi-factor authentication 3. Keeping software updated And the list goes on! #computersecurity #criticaldata #mfa

Managing #criticaldata and #cybersecurity bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer

Our #cybersecuritysolutions safeguard your #criticaldata with a range of #comprehensiveservices. Our SAFEKEEP #dataprotection solution aligns with DPDP Data Compliances (Digital Personal Data Protection Act) to effectively secure your sensitive data. Solutions@TASL
Did you know 43% of businesses never reopen after major data loss? Continuity planning is more than good practice; it’s essential for your company's survival. Start with the basics: regularly backup #CriticalData, verify your restore procedures, and consistently review your…

Surviving a Cyber Attack- Keeping Critical Data Safe buff.ly/3xttTPB #Criticaldata #data #mobilesecurity #Enterprise #Technology #Infosec #Databreach #data #SecureCommunications

With increasing threats like #hacking and hardware failures, data loss can cripple businesses. Did you know 60% of companies that lose #criticaldata shut down within 6 months? #TopNet #BaaS safeguard your #organization against these risks. How do you protect against data loss?
Happy first day of @ChannelFutures Leadership Summit! If you're here, make sure to check out our presentation session on protecting your customers' #CriticalData tomorrow (10.31). Sign up via your Informa Tech Event app to be eligible to win a $50 gift card door prize.

Regularly back up critical data to secure locations. 📅 Develop contingency plans for various crisis scenarios. 🛡️ Minimize downtime and maintain business continuity. 🎉 Celebrate milestones and achievements with your audience. 🌎 nimbuspc.com #backup #CriticalData

Protect your #criticaldata from #cyberthreats with NetworkFort. Leveraging #machinelearning techniques, it detects network anomalies and fortifies your enterprise's security defenses. Stay one step ahead of #cybercriminals with predictive behavioral analytics. #Cybersecurity

Information security protects all forms of information-digital or physical- from unauthorized access, use or disclosure, ensuring confidentiality, integrity and availability of critical data. #informationsecurity #criticaldata #Cybersecurity

Managing #criticaldata and #cybersecurity during a conflict, like the current war in #Ukraine bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer

Critical data = survival 🔑 Auditors will ask: What’s your critical data & how do you protect it? DQ Pursuit helps you answer with confidence & build trust. #CriticalData #AuditReady #DQpursuit

How to Crisis-Proof Your #DataManagement in 8 Steps | TechBeacon techbeacon.com/enterprise-it/… via @TechBeaconCom #CustomerData #CriticalData
Here’s Everything You Need To Know About API rb.gy/frzrj #API #Criticaldata #Customerdata #EcommerceBusinesses #AppsUnify

Why are cyber criminals targeting the UK? buff.ly/3D0wCma #Cybercriminals #UK #Criticaldata #data #mobilesecurity #Enterprise #Technology #Infosec #Databreach #data #SecureCommunications

Organizations struggle to identify their CDEs yet they’re the foundation of compliance, reporting & smart decisions. Missing or poor CDEs = broken compliance, bad strategy, weak risk mgmt. Protect them with DQ Pursuit. #CriticalData #DataGovernance #DQpursuit #BigDataLDN

Microsoft 365 and Microsoft Purview are great tools for businesses wanting a #secure way to exchange #criticaldata while remaining productive, but they have limitations. Read more about the importance of augmenting Microsoft 365 here: hubs.la/Q01_LDK20..
U.S. soldier linked to BSNL data breach: Arrest reveals cybercrime cysecurity.news/2025/01/us-sol… #BSNLdatabreach #CERTIn #CriticalData

THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
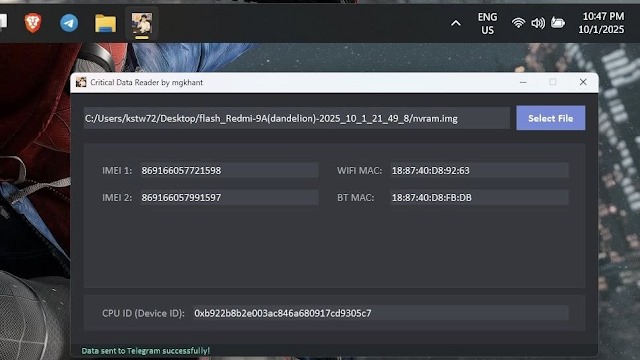
*Critical Data Reader* 📥 Download: go.cyberslinks.com/r.php?id=QSo4pW Data ingestion / import Data validation & quality checks Critical Data Elements (CDE) tagging / metadata Access & permissions control #CriticalData #FreeTools #GSMTools #FreeLogin
DevOps data breaches expose Microsoft, Schneider Electric, Mercedes-Benz, and New York Times cysecurity.news/2025/09/devops… #CriticalData #DataBreach #DataLeaks

THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
Information security protects all forms of information-digital or physical- from unauthorized access, use or disclosure, ensuring confidentiality, integrity and availability of critical data. #informationsecurity #criticaldata #Cybersecurity

THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
@Gong_io Names Chris Peake as Chief Trust Officer itdigest.com/artificial-int… #artificialintelligence #compliancemeasures #criticaldata #Gong #ITDigest #news #RevenueAI
itdigest.com
Gong Names Chris Peake as Chief Trust Officer
This appointment reinforces the company's commitment to delivering powerful outcomes for businesses while safeguarding their data...
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
THIS right here is why @drivesavers is the company we recommend when one of our customers has #CriticalData that needs to be recovered. If you need #DataRecovery, use this #code DS24016 for a special #discount from #GeekForHire drivesaversdatarecovery.com/cleanroom-data…
Managing #criticaldata and #cybersecurity bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer

Our #cybersecuritysolutions safeguard your #criticaldata with a range of #comprehensiveservices. Our SAFEKEEP #dataprotection solution aligns with DPDP Data Compliances (Digital Personal Data Protection Act) to effectively secure your sensitive data. Solutions@TASL

Today is Computer Security Day! 💻 Always take steps to ensure your critical data is safe, including: 1. Utilizing unique, long and complex passwords 2. Enabling multi-factor authentication 3. Keeping software updated And the list goes on! #computersecurity #criticaldata #mfa

Surviving a Cyber Attack- Keeping Critical Data Safe buff.ly/3xttTPB #Criticaldata #data #mobilesecurity #Enterprise #Technology #Infosec #Databreach #data #SecureCommunications


U.S. soldier linked to BSNL data breach: Arrest reveals cybercrime cysecurity.news/2025/01/us-sol… #BSNLdatabreach #CERTIn #CriticalData

DevOps data breaches expose Microsoft, Schneider Electric, Mercedes-Benz, and New York Times cysecurity.news/2025/09/devops… #CriticalData #DataBreach #DataLeaks

cloud-native environment, strategies for seamless and accurate data transfer, and more. Read More: goo.su/mQH83Fq #cloudnativeenvironment #informationmanagement #criticaldata #informationmanagement #cloudserviceproviders

Why are cyber criminals targeting the UK? buff.ly/3D0wCma #Cybercriminals #UK #Criticaldata #data #mobilesecurity #Enterprise #Technology #Infosec #Databreach #data #SecureCommunications

With increasing threats like #hacking and hardware failures, data loss can cripple businesses. Did you know 60% of companies that lose #criticaldata shut down within 6 months? #TopNet #BaaS safeguard your #organization against these risks. How do you protect against data loss?

Did you know 43% of businesses never reopen after major data loss? Continuity planning is more than good practice; it’s essential for your company's survival. Start with the basics: regularly backup #CriticalData, verify your restore procedures, and consistently review your…

"SupremeRAID™ v1.6 update targets enhanced reliability in RAID storage, marking a significant improvement in RAID technology." Don't miss the big news! Read it on @storagereview: zurl.co/izO6 #RAIDreliability #criticaldata #futureofstorage #HPC #AI

🚨 Ransomware alert! NE****IT, a vital tech sector entity, has been targeted by raworld. This attack underscores the risks to critical infrastructure and the pressure on victims to pay ransoms. #RansomwareThreat #CriticalData #TechSector #RansomMonitor … ift.tt/Wh5Ywnd

Managing #criticaldata and #cybersecurity during a conflict, like the current war in #Ukraine bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer

Managing #criticaldata and #cybersecurity during a conflict bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer
Protect your #criticaldata from #cyberthreats with NetworkFort. Leveraging #machinelearning techniques, it detects network anomalies and fortifies your enterprise's security defenses. Stay one step ahead of #cybercriminals with predictive behavioral analytics. #Cybersecurity

Bridgeworks features in this #article from @DIGIWORLD_INFO about managing #criticaldata and #cybersecurity bit.ly/3YCyuew #AI #Innovation #BigData #WAN #WANAcceleration #CloudComputing #DataAnalysis #DataTransfer

Happy first day of @ChannelFutures Leadership Summit! If you're here, make sure to check out our presentation session on protecting your customers' #CriticalData tomorrow (10.31). Sign up via your Informa Tech Event app to be eligible to win a $50 gift card door prize.

Here’s Everything You Need To Know About API rb.gy/frzrj #API #Criticaldata #Customerdata #EcommerceBusinesses #AppsUnify

The #CMMC program is crucial for securing our nation's #criticaldata, and our tools & solutions ensure compliance to make the process as seamless as possible. Explore our technology portfolio tailored to #CMMC domains today: carah.io/0a44208

Something went wrong.
Something went wrong.
United States Trends
- 1. Chris Paul 14.8K posts
- 2. Clippers 23.3K posts
- 3. Good Wednesday 27K posts
- 4. #NSD26 3,089 posts
- 5. #SpotifyWrapped 8,835 posts
- 6. #WednesdayMotivation 3,139 posts
- 7. Happy Hump 5,758 posts
- 8. Hump Day 8,871 posts
- 9. FELIX LV VISIONARY SEOUL 23.9K posts
- 10. #FELIXxLouisVuitton 27.5K posts
- 11. TOP CALL 10.1K posts
- 12. National Signing Day 2,617 posts
- 13. Pat Spencer 2,867 posts
- 14. The BIGGЕST 316K posts
- 15. jungkook 267K posts
- 16. #JUPITER 155K posts
- 17. Nashville 32.4K posts
- 18. Elden Campbell N/A
- 19. Brandy 8,812 posts
- 20. Kerr 5,852 posts