#dpapi نتائج البحث
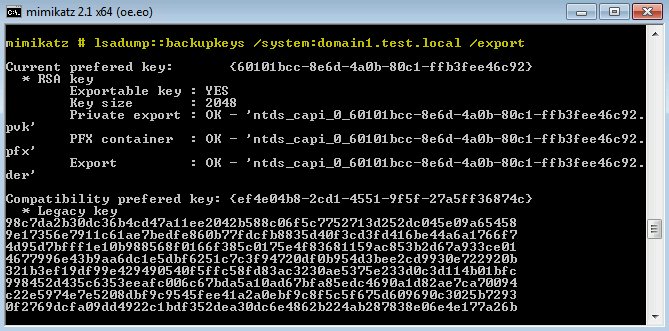
Extracting the domain #dpapi backup key isn't needed when you can ask kindly /RPC #mimikatz github.com/gentilkiwi/mim…

SharpDPAPI - A C# Port Of Some Mimikatz DPAPI Functionality j.mp/3cQ8B5e #DPAPI #mimikatz #PowerShell #RDP #Scan #Secrets

Join us for a LIVE demo of 2 huge #DPAPI discoveries; decrypt SID-protected PFX files & more. Book your FREE seat => cqureacademy.com/webinar/12-cru…

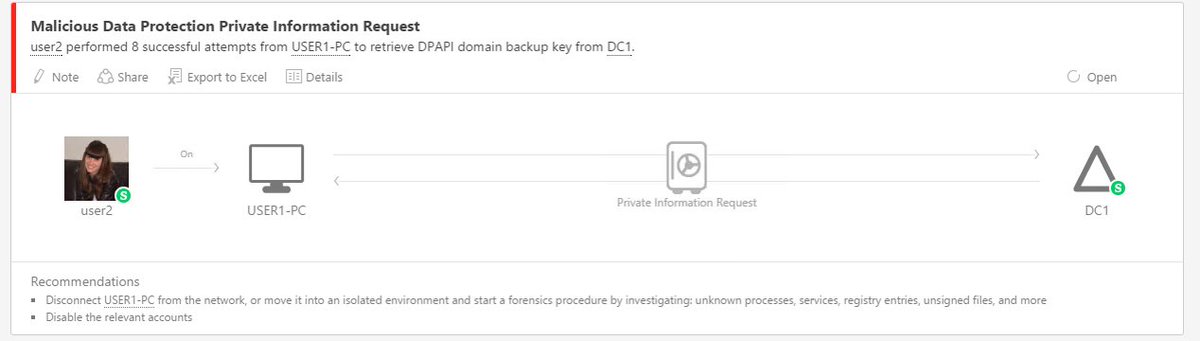
4/ Detection of rogue #DPAPI master key retrieval from DC See @gentilkiwi #MicrosoftATA
Decrypt *all* keys of DPAPI Masterkeys files! >github.com/gentilkiwi/mim… Moar keys! Including RSA domain backup decrypt


🔑 A stolen #DPAPI backup key means there’s no way back to trust within your domain. In this blog, John Brown explains why standard recovery won’t cut it, and what #Microsoft really recommends. #Cybersecurity #ActiveDirectory Read the blog → sans.org/u/1CLK

Unable to extract credentials via #DPAPI or #Mimikatz? Don't worry. #Microsoft has you covered. Just use 'rundll32 keymgr.dll, KRShowKeyMgr' to extract all the stored passwords on the host. #Security #BugBounty #vulnerabilities #CyberSecurity #infosec #forensics

When coding, you want to keep some good things for the next days. (otherwise it is not funny) #mimikatz #dpapi #vault


I spent some time fighting with the #DPAPI to decipher data offline. Majority of the tools are all in one package and do not play well with EDR. I needed to do all of this offline, from #SCCM decryption to Chrome cloning. I hope it will help someone ! otterhacker.github.io/Pentest/Techni…
A #SigSegv2 Benjamin Delpy @gentilkiwi démystifie #DPAPI pour expliquer comment fonctionne #Mimikatz pour retrouver les mots de passe #Windows #RTFM @sigsegv_event




SharpDPAPI - A C# Port Of Some Mimikatz DPAPI Functionality j.mp/3cQ8B5e #DPAPI #mimikatz #PowerShell #RDP #Scan #Secrets

Join our CEO @PaulaCqure at @Microsoft HQ on August 12th for the @TechMentorEvent! 🔐 The session on #DPAPI decryption & forensics techniques + our Windows cryptographic research await you! Get your tickets here: techmentorevents.com #Cybersecurity #TechMentorConference
🔑 A stolen #DPAPI backup key means there’s no way back to trust within your domain. In this blog, John Brown explains why standard recovery won’t cut it, and what #Microsoft really recommends. #Cybersecurity #ActiveDirectory Read the blog → sans.org/u/1CLK

Join our CEO @PaulaCqure at @Microsoft HQ on August 12th for the @TechMentorEvent! 🔐 The session on #DPAPI decryption & forensics techniques + our Windows cryptographic research await you! Get your tickets here: techmentorevents.com #Cybersecurity #TechMentorConference
🚨 New Writeup Alert! 🚨 "HTB | Office — CVE-2023–23752, Abusing MS-BKRP & GPO" by anuragtaparia is now live on IW! Check it out here: infosecwriteups.com/304f05f4fd55 #dpapi #office #htb #cve202323752 #gpoabuse
infosecwriteups.com
HTB | Office — CVE-2023–23752, Abusing MS-BKRP & GPO
This is a Windows box. You can find it here.
Following the recent #Windows #DPAPI talk @CHCon_nz we released a post on the recent #Chromium App Bound changes tierzerosecurity.co.nz/2024/11/26/dat…

Web Browser Stored Credentials #WebBrowserStoredCredentials #PenetrationTestingLab #DPAPI #CredentialAccess #SharpDPAPI pentestlab.blog/2024/08/20/web…
pentestlab.blog
Web Browser Stored Credentials
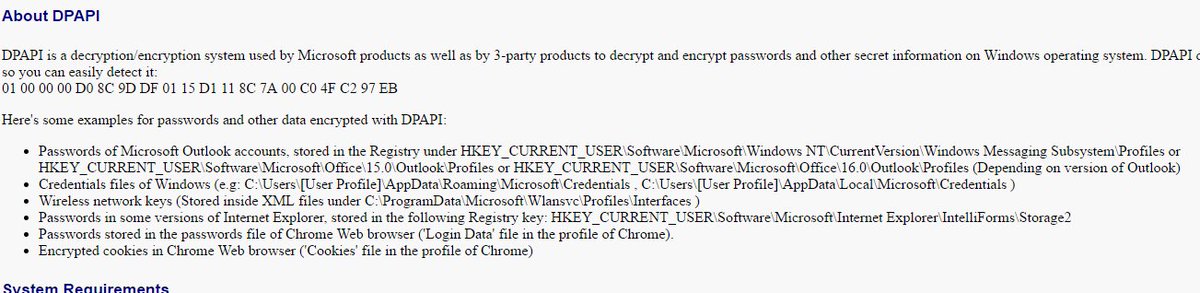
Microsoft introduced Data Protection Application Programming Interface (DPAPI) in Windows environments as a method to encrypt and decrypt sensitive data such as credentials using the CryptProtectDa…
Improving the #security of #Chrome cookies on Windows are introducing a new protection on Windows that improves on the #DPAPI by providing Application-Bound (#App-Bound) Encryption primitives. security.googleblog.com/2024/07/improv…
I spent some time fighting with the #DPAPI to decipher data offline. Majority of the tools are all in one package and do not play well with EDR. I needed to do all of this offline, from #SCCM decryption to Chrome cloning. I hope it will help someone ! otterhacker.github.io/Pentest/Techni…
Step 1: Enable logging on the system: #DPAPI events are logged into two places in the system. 1. 4693 event: Enabled by turning on "Audit DPAPI Activity" and the steps to do this: Security Settings -> Advanced Audit Policy Configuration -> Detailed Tracking. 4693 example:

Having user's password in hand opened plenty of other doors for us as we were able to crack master key & encrypted chrome data eventually. I also spoke the importance of DPAPI and secrecy of its keys. Check out ---> youtube.com/watch?v=TyiUnR… #DPAPI #chrome #digitalforensics
youtube.com
YouTube
Unraveling Google Chrome's Secrets | Decrypting DPAPI //TryHackMe
dploot is Python rewrite of SharpDPAPI written un C# github.com/zblurx/dploot #CredentialAccess #DPAPI
DPAPI fails with CryptographicException when trying to decrypt Chrome cookies - Visit programmatic.solutions/fb7eoj/dpapi-f… for the solution. #csharp #dpapi #programming #programmer #dev
#dpapi [ DonPAPI ] Dumping DPAPI credentials remotely github.com/login-securite…... t.me/s/it_news_for_…
![IT_news_for_all's tweet image. #dpapi
[ DonPAPI ]
Dumping DPAPI credentials remotely
github.com/login-securite…... t.me/s/it_news_for_…](https://pbs.twimg.com/media/FiJWydoXkAAsnsy.jpg)
J'ai fais un petit article sur le fonctionnement technique de l'API de chiffrement de #Microsoft (aka #DPAPI) suite à la publication de @HekatombProject : lestutosdeprocessus.fr/dechiffrement-… ça permet de bien comprendre le fonctionnement du système 🙂
#DPAPI breakdown, this is exactly the refresh I needed this morning (uh-oh?😱). Thanks and GG @DarthSnorlax z3r0th.medium.com/abusing-dpapi-…
z3r0th.medium.com
Abusing DPAPI
Abusing DPAPI is no new attack vector by any means. I think the earliest presentation I’ve come across is from 2010, though I don’t know…
Exploring data saved by Chrome/Edge/Any Chromium gist.github.com/jhoneill/e585b… #dpapi
SharpDPAPI - A C# Port Of Some Mimikatz DPAPI Functionality j.mp/3cQ8B5e #DPAPI #mimikatz #PowerShell #RDP #Scan #Secrets

Extracting the domain #dpapi backup key isn't needed when you can ask kindly /RPC #mimikatz github.com/gentilkiwi/mim…

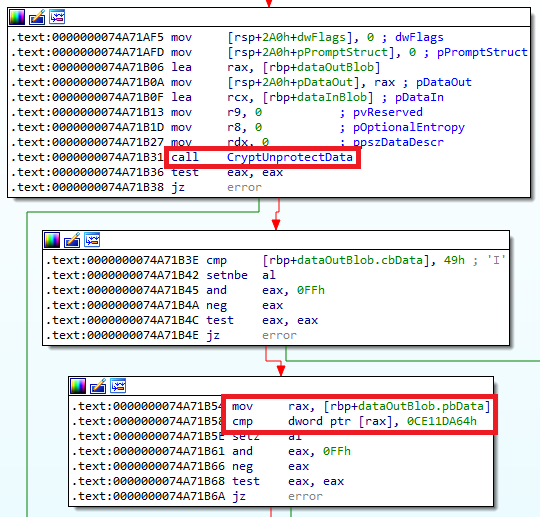
#InvisiMole places execution guardrails on its components to hide from security researchers. Encrypted with #DPAPI, the payload can only be decrypted on the victim’s computer. Luckily, we recovered the payloads thanks to our close cooperation with the affected organizations. 4/9
4/ Detection of rogue #DPAPI master key retrieval from DC See @gentilkiwi #MicrosoftATA


Decrypt *all* keys of DPAPI Masterkeys files! >github.com/gentilkiwi/mim… Moar keys! Including RSA domain backup decrypt


Join us for a LIVE demo of 2 huge #DPAPI discoveries; decrypt SID-protected PFX files & more. Book your FREE seat => cqureacademy.com/webinar/12-cru…

@BlackHatEvents 2017 in London is just around the corner — mark your calendar for December 6th and find out more up here ➡️ blackhat.com/eu-17/arsenal/… I will be talking about CQURE’s breakthrough discovery tools: “#DPAPI & DPAPI-NG: #decryption toolkit”. See you there!

Unable to extract credentials via #DPAPI or #Mimikatz? Don't worry. #Microsoft has you covered. Just use 'rundll32 keymgr.dll, KRShowKeyMgr' to extract all the stored passwords on the host. #Security #BugBounty #vulnerabilities #CyberSecurity #infosec #forensics

When coding, you want to keep some good things for the next days. (otherwise it is not funny) #mimikatz #dpapi #vault

#dpapi [ DonPAPI ] Dumping DPAPI credentials remotely github.com/login-securite…... t.me/s/it_news_for_…
![IT_news_for_all's tweet image. #dpapi
[ DonPAPI ]
Dumping DPAPI credentials remotely
github.com/login-securite…... t.me/s/it_news_for_…](https://pbs.twimg.com/media/FiJWydoXkAAsnsy.jpg)

Following the recent #Windows #DPAPI talk @CHCon_nz we released a post on the recent #Chromium App Bound changes tierzerosecurity.co.nz/2024/11/26/dat…

@BlackHatEvents 2017 in London is just around the corner — mark your calendar for December 6th and find out more up here ➡️ blackhat.com/eu-17/arsenal/… @PaulaCqure will be talking about CQURE’s breakthrough discovery tools: “#DPAPI & DPAPI-NG: #decryption toolkit”. See you there!

SharpDPAPI - A C# Port Of Some Mimikatz DPAPI Functionality j.mp/3cQ8B5e #DPAPI #mimikatz #PowerShell #RDP #Scan #Secrets

earmas.ga - SharpDPAPI - A C# Port Of Some Mimikatz DPAPI Functionality j.mp/3cQ8B5e #DPAPI #mimikatz #PowerShell #RDP #Scan #Secrets #earmas

Something went wrong.
Something went wrong.
United States Trends
- 1. Gabe Vincent 3,281 posts
- 2. #Blackhawks 1,983 posts
- 3. #AEWDynamite 17.8K posts
- 4. #stlblues 1,757 posts
- 5. Deport Harry Sisson 6,644 posts
- 6. Angel Reese 47.6K posts
- 7. #VSFashionShow 539K posts
- 8. tzuyu 219K posts
- 9. DuPont 1,527 posts
- 10. Mavs 5,255 posts
- 11. #Survivor49 3,415 posts
- 12. Deloitte 5,112 posts
- 13. Hofer 1,702 posts
- 14. Nazar 6,479 posts
- 15. Tusky 2,149 posts
- 16. Quen 29.9K posts
- 17. jihyo 174K posts
- 18. Birdman 4,855 posts
- 19. Suarez 17.7K posts
- 20. Darby 5,089 posts