#dataprotection search results
As firms collect personal data, Governments have introduced digital protections to increase Data Security requirements and controls on personal information because Privacy is a Human Right. bit.ly/2BFZwvY @wef @antgrasso ht @HaleChris #privacy #dataprotection
Should national privacy have its own dedicated namespace? Absolutely. And it’s time we build it. #Privacy #CyberSecurity #DataProtection #Web3 #DigitalIdentity #national #government
BREAKING NEWS: Big win for privacy! 🌐 California just passed three groundbreaking bills to protect your personal data. From universal opt-outs for data sharing to making account deletion easier, these laws put YOU back in control of your digital life. 💻 #dataprotection

Every website relies on cookies, from analytics and ads to login sessions and user profiling. That’s why Cookies.Privacy is one of the most important privacy touchpoints on the entire internet. Link: unstoppabledomains.com/d/cookies.priv… #Privacy #DataProtection #OnlineSafety #Cookies…
Do you know that it is unlawful to buy or disclose another person’s personal data either knowingly or recklessly . It is equally unlawful to cause the disclosure of that person’s personal data without his consent . Learn more from us! #UPSA #UPSALawSchool #DataProtection…

X @X may be violating some Data Protection Rules especially that of TRANSPARENCY with this AUTOMATIC account location feature. @grok take note. #DataPrivacy #DataProtection #GDPR
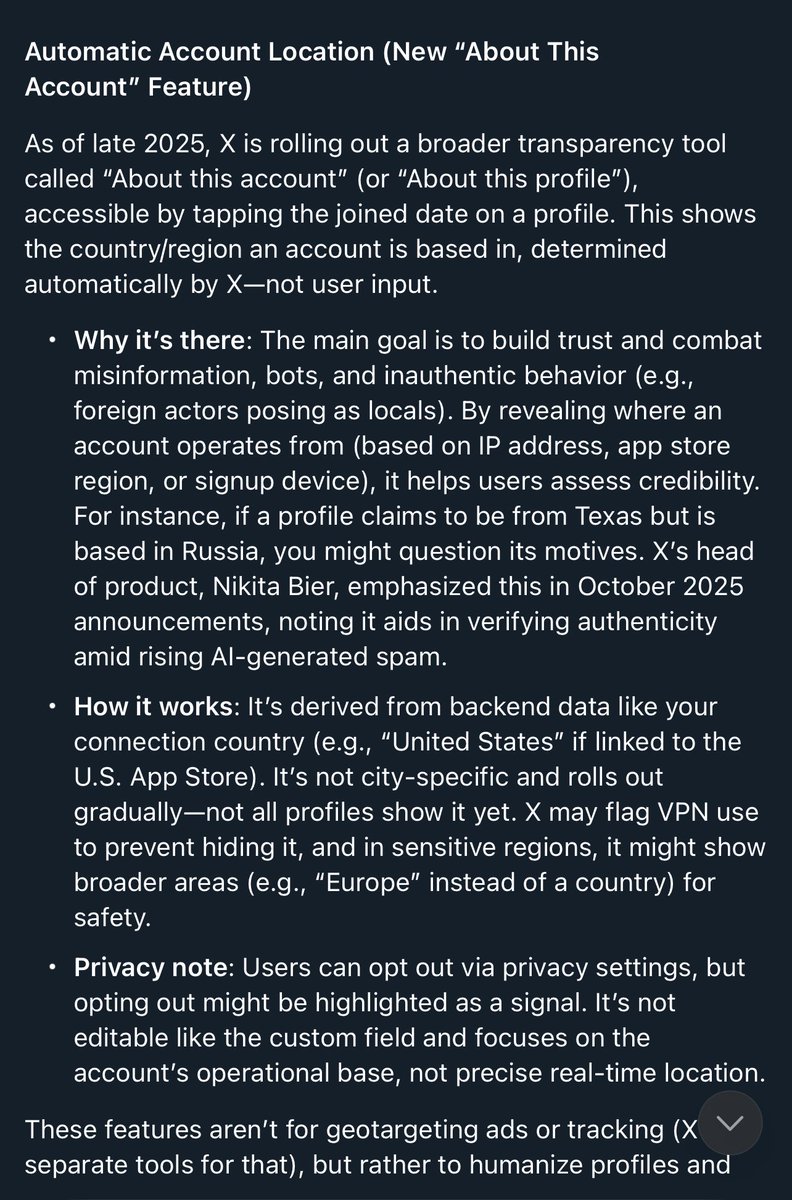
Whether your IT infrastructure is on-premise, in the cloud, in a hybrid cloud, or in a multi-cloud, the approach to security must never change: Assess, Protect, Detect & Respond. RT @antgrasso #CloudComputing #CyberSecurity #DataProtection
Just like this crystal, your data deserves to stay unbreakable, protected, and always under your control. @SeismicSys is building a future where privacy,security isn’t optional — it’s the foundation. Strong. Solid. Unshakeable.🌋Go Seismic. #Seismic #DataProtection @SeismicSys

Our Senior Associate Chinonso Emeka is honored to moderate the panel on Data Protection as a Business Asset at the 7th Privacy Symposium Africa! Join us for insightful discussions and valuable insights from industry experts! #PrivacySymposiumAfrica #DataProtection #BusinessAsset

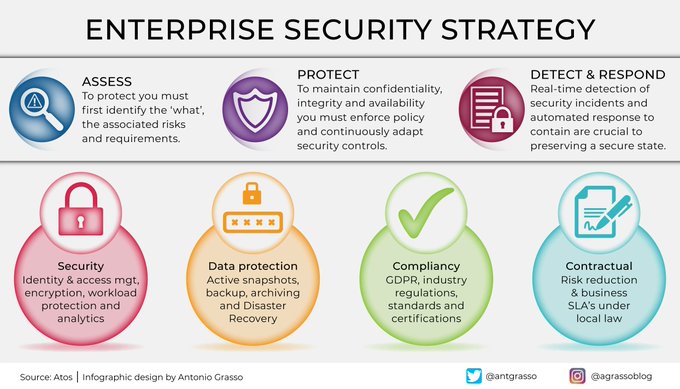
Talking about cybersecurity without referring to attacks from within the organization does not outline the overall picture. Here are four types of potential internal attacks. Rt #infographic by @antgrasso #CyberSecurity #DataProtection #InsiderAttacks
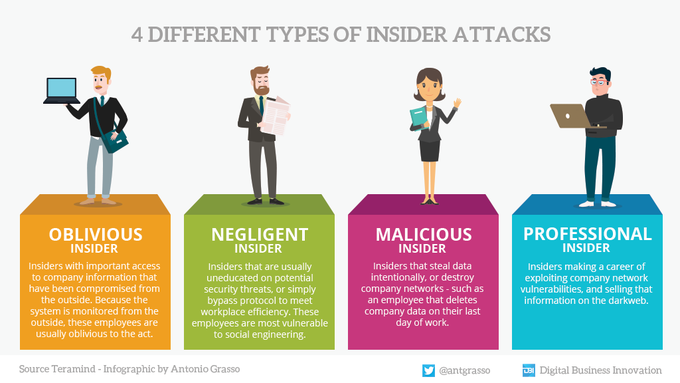
Just got that “your data may be at risk” alert? Here’s what you need to do: 🔴 Change your passwords 🔴 Turn on #2FA 🔴 Freeze your credit 🔴 Give your bank a heads-up These four steps shut down most of the damage before it starts. #DataBreach #DataProtection #OnlineSafety
Sistemi korumak kodla başlar, bilinci korumak insanla mümkündür. Veri güvenliği bizim için bir sorumluluk değil, bir kültürdür. Korunan her veri, sürdürülebilir şehirlerin geleceğine yapılan bir yatırımdır. #BilgisayarGüvenliğiGünü #CyberSecurity #DataProtection #Intetra

Dans cet épisode de notre série « Comprendre la protection des données », la CDP explique pourquoi la conformité en matière de protection des données n’est pas seulement une obligation légale, mais un véritable atout stratégique pour les entreprises. #conformité #DataProtection
How does an OPC handle legal and regulatory compliance? If you would like more information, please visit the page. helloauditor.com/how-does-an-op… #opccompliance #legalregulations #dataprotection #privacylaw #compliancemanagement #regulatoryframework #datagovernance

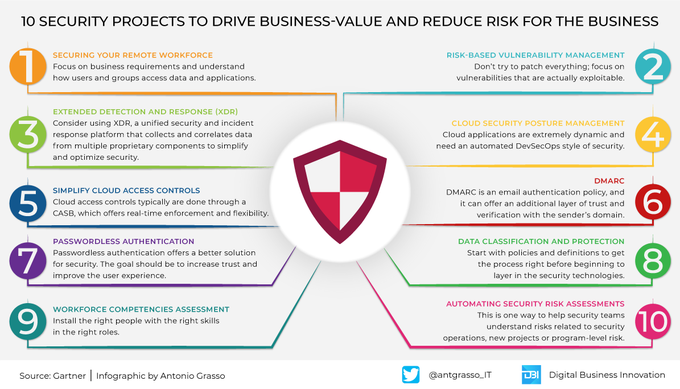
We shouldn't think about cybersecurity in our company as a monolithic block to be addressed as a whole. Often the best way is to divide the problem into small projects by solving them one at a time. #Infographic by @antgrasso #CyberSecurity #DataProtection #DigitalStrategy
Think your data is safe? Spot the red flag before it’s too late; which of these signals a possible data breach? Comment your answer and test your cyber-awareness! #CyberSecurity #DataProtection #CyberAwareness #CyberThreats #DataBreachPrevention #DigitalSafety #InfoSecurity

What are Digital Personal Data Protection Rules? :Details by Sh Aroon Deep @AroonDeep #Digital #PersonalData #DataProtection #DataSecurity #DataFiduciary #DataPrincipals #UserConsent #encryption #RightToInformation #PublicInformation #privacy #Exemption #Children #law #UPSC

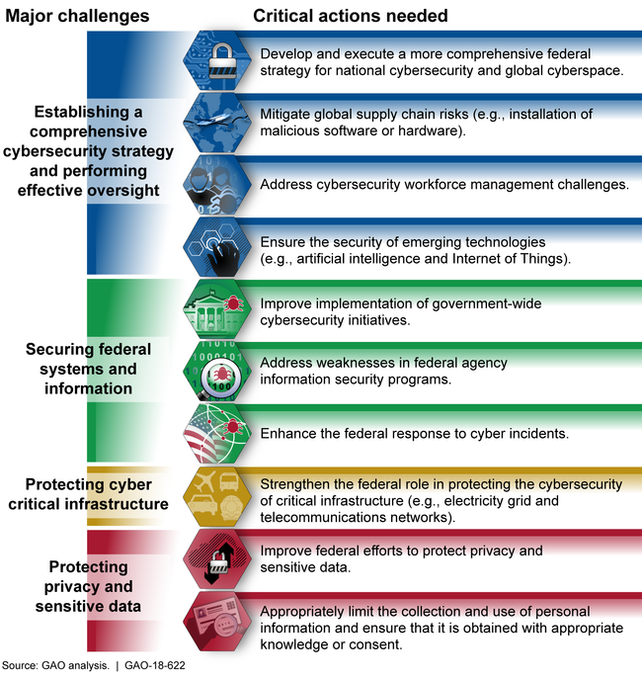
Since many government IT systems contain vast amounts of personally identifiable information, federal agencies must protect the confidentiality, integrity, and availability of this information. @USGAO >> bit.ly/2NtIDH4 rt @antgrasso #CyberSecurity #DataProtection
Ireland's Data Protection Commission has fined the Department of Social Protection €550,000. Data protection is serious business! ⚖️🇪🇺 #DataProtection #Privacy
#Nextcloud #CyberSecurity #DataProtection #Encryption #2FA Full guide: resistekonline.wordpress.com/2025/12/02/fit…
Should national privacy have its own dedicated namespace? Absolutely. And it’s time we build it. #Privacy #CyberSecurity #DataProtection #Web3 #DigitalIdentity #national #government
Cohesity teams up with AWS to enhance data protection and recovery globally using advanced AI tools and native cloud integration across 36 regions. #DataProtection #AI #CloudComputing #AWS #Cohesity techday.com.au/story/cohesity…
Enhance enterprise security with modern AI agents! Meet compliance requirements, protect data, and ensure audit trails. #AISecurity #DataProtection
Identity is the new perimeter. Attackers aren’t breaking in anymore — they’re logging in. Stronger identity controls and recovery readiness are now must-haves. Read the full article: linkedin.com/pulse/securing… #IdentitySecurity #DataProtection sprou.tt/1Yjq5mGfZQ8
information shield widened. The Digital Personal Data Protection Act, 2023 amends Section 8(1)(j) of the Right to Information Act. #RTI #DataProtection


For a secure digital Pakistan free and unverified VPNs must be banned These VPNs put citizens data at risk and enable cyber attacks Only licensed and security verified VPNs can strengthen national cyber security #CyberSecurity #DigitalPakistan #DataProtection #VPNSafety

Parce que la simple copie de sécurité ne suffit plus... De la sauvegarde à la data résilience : Entretien avec Patrick Rohrbasser, VP Europe du Sud de Veeam. informatiquenews.fr/veeam-data-pla… #Veeam #CyberResilience #DataProtection
Whether it’s accidental deletion or a system meltdown, offsite backups let you restore your business quickly. Your data is the backbone of your business. Let ThinkSwift MSP make sure it lives safely. #BusinessContinuity #DataProtection #BackupSolutions #ITSecurity



LeadSpring is GDPR-ready, ensuring that your lead capture is compliant and secure. Focus on growth without the worry! #GDPR #DataProtection

This paper by Richards & Hartzog critiques how terms like choice, consent, and control are conflated, weakening privacy protections. Calls for clearer definitions and meaningful choice to empower individuals. spkl.io/6015A5L0v #Privacy #Autonomy #DataProtection

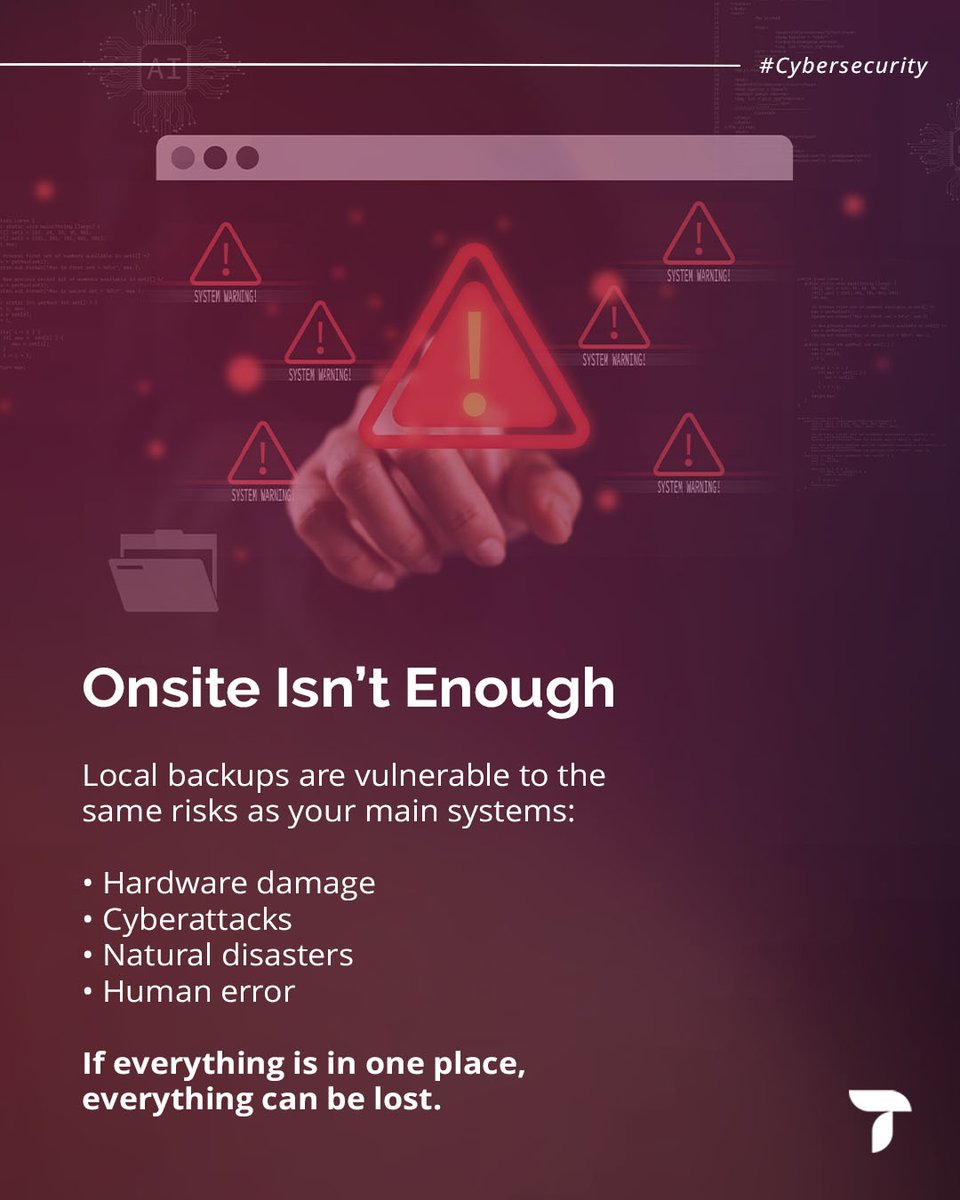
Accidental data loss is a growing problem. Protecting yourself is becoming essential as the chance of damage increases. #DataLoss #DataProtection
🙏🏻 Honored to be part of this milestone for our region. The formation of the ACFE Arab Chapter Committee is the result of dedication, collaboration, & a shared commitment across all Arab Chapters to strengthen our collective fight against fraud. #StarAcademy #DataProtection #Fra
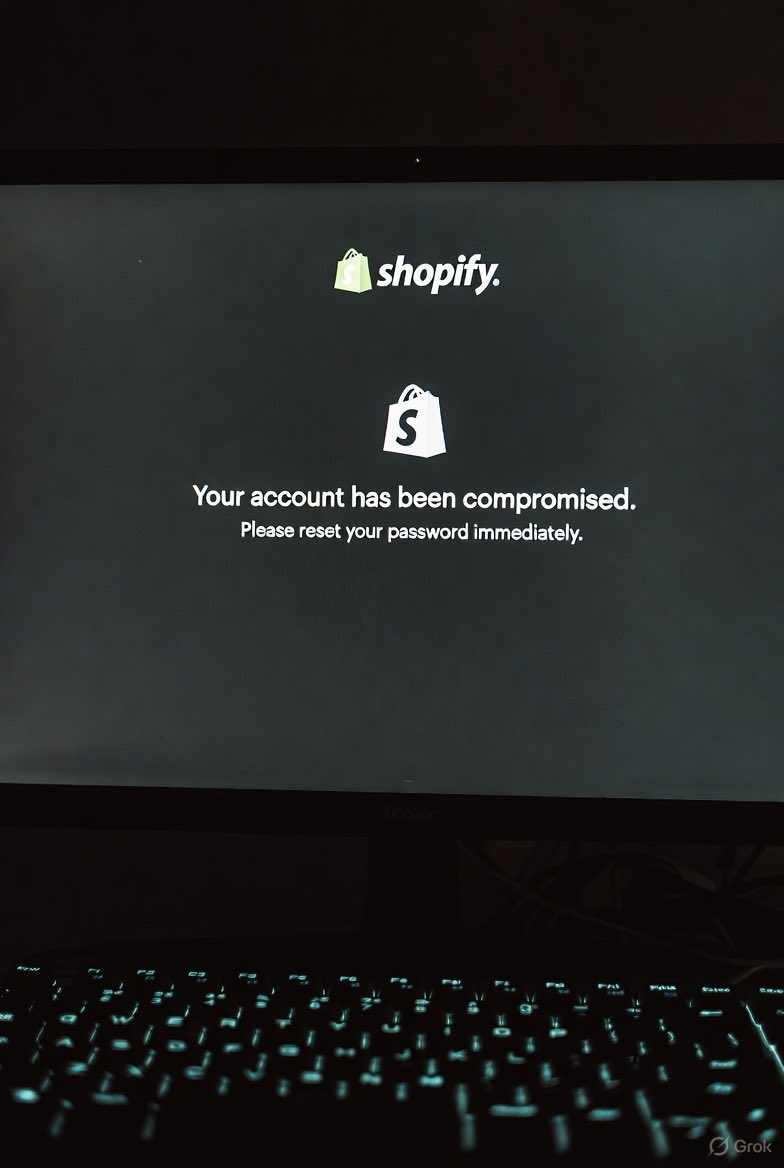
Shopify has been hacked on its most important day of the year, with the biggest e-commerce platform experiencing blocked logins since 9 AM ET. #shopify #DataProtection #CyberMonday
DPDP Act and Rules are now live. Transparency isn’t optional anymore. Every data Notice should clearly outline your personal data, the purpose of its use, and the simple steps to withdraw consent or raise concerns. #DataMeraNiyantranMera #DigitalIndia #DataProtection

BREAKING NEWS: Big win for privacy! 🌐 California just passed three groundbreaking bills to protect your personal data. From universal opt-outs for data sharing to making account deletion easier, these laws put YOU back in control of your digital life. 💻 #dataprotection

As firms collect personal data, Governments have introduced digital protections to increase Data Security requirements and controls on personal information because Privacy is a Human Right. bit.ly/2BFZwvY @wef @antgrasso ht @HaleChris #privacy #dataprotection

X @X may be violating some Data Protection Rules especially that of TRANSPARENCY with this AUTOMATIC account location feature. @grok take note. #DataPrivacy #DataProtection #GDPR

Do you know that it is unlawful to buy or disclose another person’s personal data either knowingly or recklessly . It is equally unlawful to cause the disclosure of that person’s personal data without his consent . Learn more from us! #UPSA #UPSALawSchool #DataProtection…

Sistemi korumak kodla başlar, bilinci korumak insanla mümkündür. Veri güvenliği bizim için bir sorumluluk değil, bir kültürdür. Korunan her veri, sürdürülebilir şehirlerin geleceğine yapılan bir yatırımdır. #BilgisayarGüvenliğiGünü #CyberSecurity #DataProtection #Intetra

We’re listening 👂 What do you want to see more of from TrustArc? 💡 Privacy frameworks 📊 Compliance insights 🎥 Webinars & resources Tell us in the comments because your input shapes what we create next! #PrivacyCommunity #DataProtection #TrustArc

Whether your IT infrastructure is on-premise, in the cloud, in a hybrid cloud, or in a multi-cloud, the approach to security must never change: Assess, Protect, Detect & Respond. RT @antgrasso #CloudComputing #CyberSecurity #DataProtection

Just like this crystal, your data deserves to stay unbreakable, protected, and always under your control. @SeismicSys is building a future where privacy,security isn’t optional — it’s the foundation. Strong. Solid. Unshakeable.🌋Go Seismic. #Seismic #DataProtection @SeismicSys

Think your data is safe? Spot the red flag before it’s too late; which of these signals a possible data breach? Comment your answer and test your cyber-awareness! #CyberSecurity #DataProtection #CyberAwareness #CyberThreats #DataBreachPrevention #DigitalSafety #InfoSecurity

Ready to boost your account security? 🛡️ Two-factor authentication adds a vital layer of protection beyond just a password. Learn how to enable it and keep your data safe. 🔗 onlyo.co/4435P6u #CyberSecurity #2FA #DataProtection

If you're living with #HIV, it is so important to know how you are protected by the law. It is illegal to discriminate against people living with HIV, and your status is protected by #dataprotection legislation. Find out more on our website: nat.org.uk/about-hiv/hiv-…

Just got that “your data may be at risk” alert? Here’s what you need to do: 🔴 Change your passwords 🔴 Turn on #2FA 🔴 Freeze your credit 🔴 Give your bank a heads-up These four steps shut down most of the damage before it starts. #DataBreach #DataProtection #OnlineSafety

How does an OPC handle legal and regulatory compliance? If you would like more information, please visit the page. helloauditor.com/how-does-an-op… #opccompliance #legalregulations #dataprotection #privacylaw #compliancemanagement #regulatoryframework #datagovernance

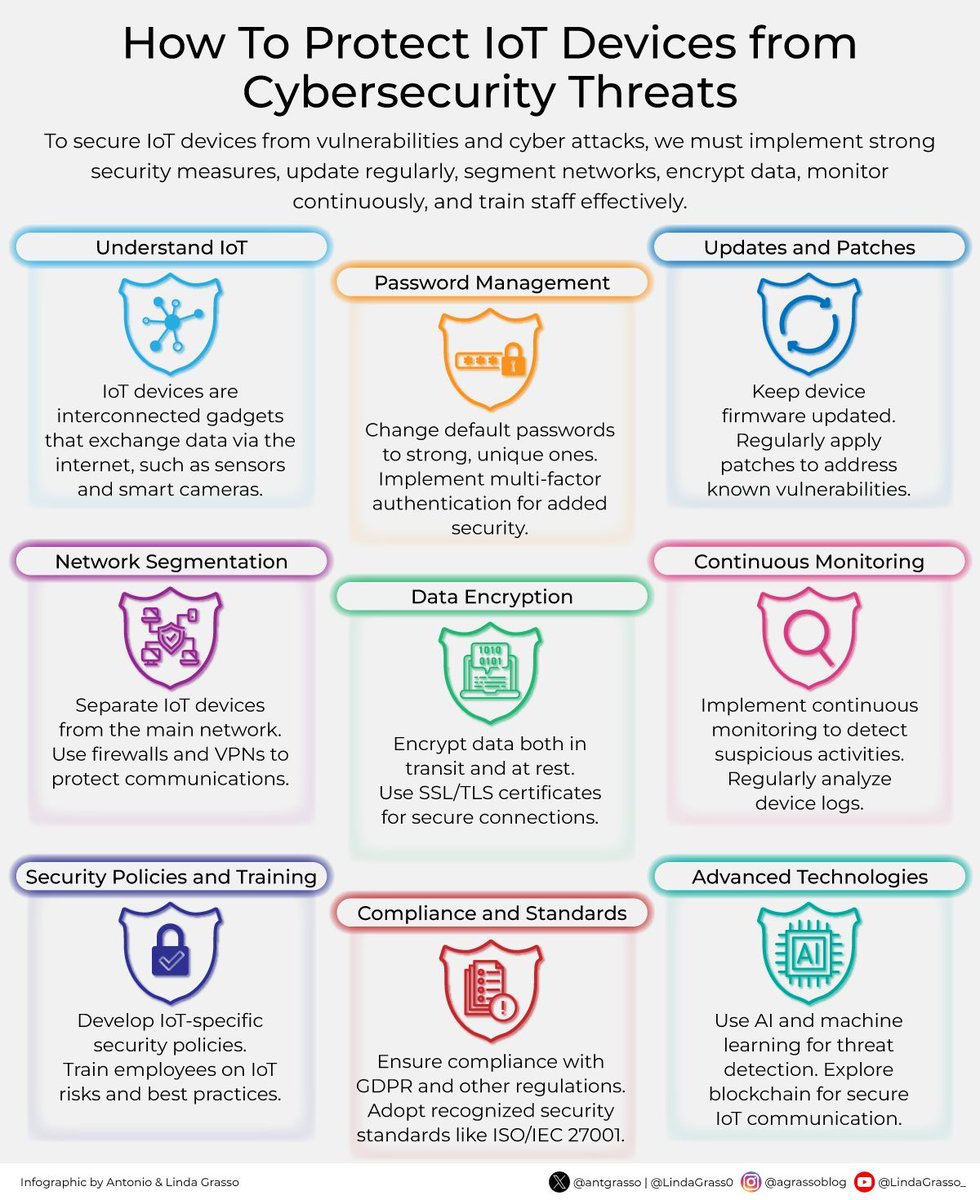
To secure IoT devices from vulnerabilities and cyber attacks, it is essential to implement robust security measures, update regularly, segment networks, encrypt data, monitor continuously, and train staff effectively. #Cybersecurity #IoT #DataProtection
Since many government IT systems contain vast amounts of personally identifiable information, federal agencies must protect the confidentiality, integrity, and availability of this information. @USGAO >> bit.ly/2NtIDH4 rt @antgrasso #CyberSecurity #DataProtection

🔒 Cybersecurity isn't just an IT issue; it's everyone's responsibility! 💻✨ What steps are you taking to keep your data secure? Share your tips below! 👇 #Cybersecurity #DataProtection #StaySafeOnline

What are Digital Personal Data Protection Rules? :Details by Sh Aroon Deep @AroonDeep #Digital #PersonalData #DataProtection #DataSecurity #DataFiduciary #DataPrincipals #UserConsent #encryption #RightToInformation #PublicInformation #privacy #Exemption #Children #law #UPSC

Talking about cybersecurity without referring to attacks from within the organization does not outline the overall picture. Here are four types of potential internal attacks. Rt #infographic by @antgrasso #CyberSecurity #DataProtection #InsiderAttacks

We shouldn't think about cybersecurity in our company as a monolithic block to be addressed as a whole. Often the best way is to divide the problem into small projects by solving them one at a time. #Infographic by @antgrasso #CyberSecurity #DataProtection #DigitalStrategy

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 49K posts
- 2. Giants 63.7K posts
- 3. Giants 63.7K posts
- 4. Patriots 93.5K posts
- 5. Drake Maye 16.1K posts
- 6. Dart 26.9K posts
- 7. Diaz 32.3K posts
- 8. Gunther 10.8K posts
- 9. Younghoe Koo 3,682 posts
- 10. Devin Williams 5,158 posts
- 11. Abdul Carter 7,512 posts
- 12. Marcus Jones 5,371 posts
- 13. Theo Johnson 1,832 posts
- 14. Kyle Williams 3,726 posts
- 15. Joe Schoen 1,665 posts
- 16. #NYGvsNE 1,673 posts
- 17. #RawOnNetflix 1,597 posts
- 18. Kafka 6,543 posts
- 19. #MondayNightFootball 1,206 posts
- 20. Ty Lue 1,318 posts