#especter ผลการค้นหา
We traced the roots of this threat back to at least 2012; it previously operated as a bootkit for systems with legacy BIOSes. Despite #ESPecter’s long existence, its operations and upgrade to UEFI went unnoticed and have not been documented until now. 4/5
New #UEFIBootkit Performs Espionage A new #ESPecter #bootkit was uncovered that performs #cyberespionage and compromises system partitions. There are signs in the #Malware's components that revealed that the #attackers could be #Chinesespeaking.

#ESETresearch analyzes a previously undocumented real-world UEFI bootkit that persists on the EFI System Partition (ESP), named #ESPecter. #ESET #cybersecurity
@ESET Research Discovers ESPecter, a UEFI bootkit for Cyberespionage... Read more: ed.gr/dohcv #Research #ESPecter #UEFI #Cyberespionage #Cybersecurity #Cyberthreats

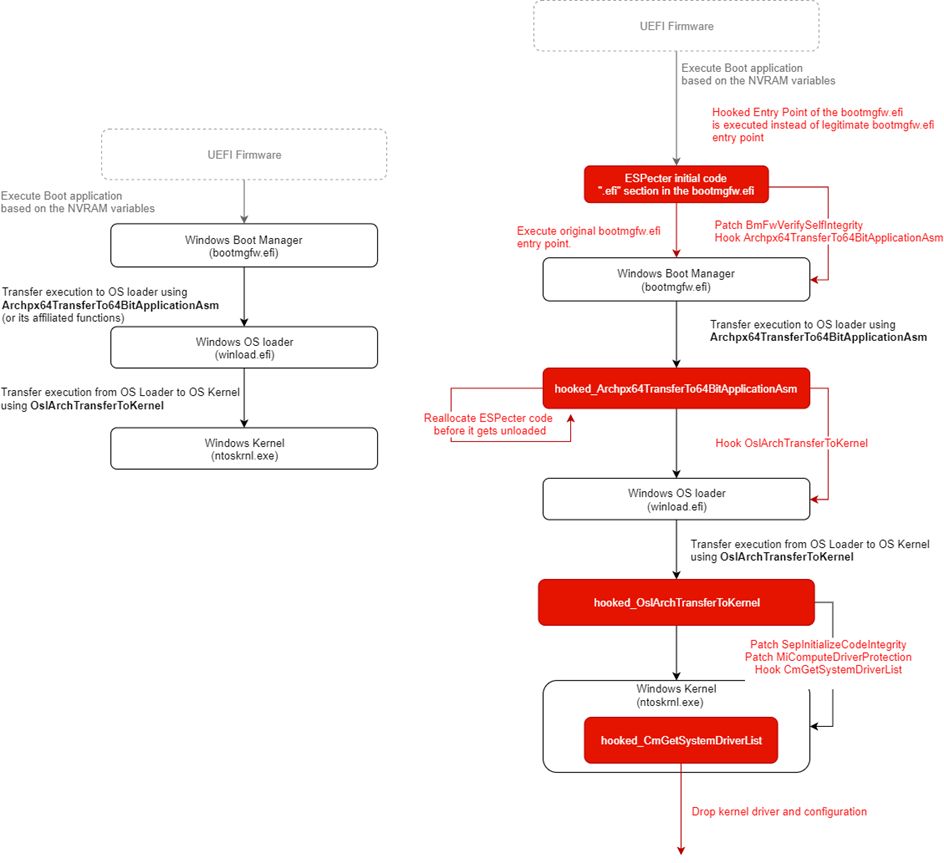
#ESETresearch has discovered a new undocumented UEFI bootkit, #ESPecter, persisting as a patched Windows Boot Manager (bootmgfw.efi) on the Efi System Partition (ESP). welivesecurity.com/2021/10/05/uef… 1/5 @smolar_m @cherepanov74
First the bootkit #FinSpy was revealed and now #ESPecter, another boot-loader-based attack. #Eclypsium can now detect against both of these invisible, #firmware-centric attacks. Learn more: bit.ly/3ArA8SR

#ESPecter #BootkitInvisibile #RubaDatiSensibili #ConfiguriamoWindowsPerProteggerci #UEFI #Windows #Microsoft #TPM #CyberSecurity -cybersecurity360.it/nuove-minacce/…
Last week the #FinSpy bootkit was revealed and now #ESPecter, another boot-loader-based attack. #Eclypsium can now detect against both of these invisible, #firmware-centric attacks and fights back. Learn more: bit.ly/3AigwAx

@Siglo21_Radio3 (2/2) #especter es el que presentó ayer @Siglo21_Radio3
#UEFI threats moving to the ESP: Introducing #ESPecter bootkit | WeLiveSecurity welivesecurity.com/2021/10/05/uef… #infosec #malware < 👻

🔍 Les chercheurs d’ESET ont découvert un bootkit UEFI actif et inconnu jusqu’à présent qui persiste sur la partition système EFI. Pour en savoir plus RDV sur notre centre presse ▶ ow.ly/Qo5k30rWMRg #cybersecurite #ESPecter #MardiConseil

#ESETresearch's very own @jiboutin and @smolar_m will be speaking today at #RSAC2022 about #ESPecter and the future of UEFI threats. The talk takes place at 8.30-9.20am PT 🇺🇸 / 17.30-18.20 CEST 🇪🇺 More ➡️ rsaconference.com/usa/agenda/ful…
🔊 Listen to the latest episode of ESET Research podcast to find out more about #ESPecter, the latest real-world espionage malware targeting the UEFI space, namely the EFI System Partition. #ESET #ESETresearch #ProgressProtected
#ESETResearch would like to highlight few points: UEFI bootkits (#BlackLotus, #ESPecter, #FinSpy) are not firmware implants 3/7
#ESETresearch's very own @jiboutin and @smolar_m will be speaking today at #RSAC2022 about #ESPecter and the future of UEFI threats. The talk takes place at 8.30-9.20am PT 🇺🇸 / 17.30-18.20 CEST 🇪🇺 More ➡️ rsaconference.com/usa/agenda/ful…
🔊 Listen to the latest episode of ESET Research podcast to find out more about #ESPecter, the latest real-world espionage malware targeting the UEFI space, namely the EFI System Partition. #ESET #ESETresearch #ProgressProtected
ESET Research découvre des vulnérabilités dans les ordinateurs portables grand public du fabricant Lenovo, exposant les utilisateurs à un risque d’installation de malware UEFI #ESPecter #malware #Cybersecurite #UEFI @ESET_France @ESETresearch itnumeric.com/?p=50329
Bootkit #ESPecter získává data z infikovaného zařízení a odesílá je na svůj řídící server. mobilenet.cz/clanky/jak-vyp…
ITPOINT.CZ/1ke9AL - #Bootkit #ESPecter je nově odhalenou hrozbou pro technologii UEFI, která mění mechanismus zodpovědný za bezpečné spuštění operačního systému #Windows
New #UEFIBootkit Performs Espionage A new #ESPecter #bootkit was uncovered that performs #cyberespionage and compromises system partitions. There are signs in the #Malware's components that revealed that the #attackers could be #Chinesespeaking.

First the bootkit #FinSpy was revealed and now #ESPecter, another boot-loader-based attack. #Eclypsium can now detect against both of these invisible, #firmware-centric attacks. Learn more: bit.ly/3ArA8SR

#ESETResearch analyses a previously undocumented real-world UEFI bootkit that persists on the EFI System Partition (ESP), named ESPecter. #ESPecter #UEFI #Cybersecurity #CybersecurityNews @ESETResearch
🔍 Les chercheurs d’ESET ont découvert un bootkit UEFI actif et inconnu jusqu’à présent qui persiste sur la partition système EFI. Pour en savoir plus RDV sur notre centre presse ▶ ow.ly/Qo5k30rWMRg #cybersecurite #ESPecter #MardiConseil

#cybersecurity | #ESPecter, il #bootkit invisibile che ruba dati sensibili: configuriamo #Windows per proteggerci cybersecurity360.it/nuove-minacce/…
#ESPecter, un #bootkit invisibile in circolazione dal 2012, ruba #datisensibili bypassando i #sistemi #antimalware di #Windows. 💻 Per sapere di più leggi l'articolo di #securityinfo. ✏️cutt.ly/xEC8qVf

@ESET Research Discovers ESPecter, a UEFI bootkit for Cyberespionage... Read more: ed.gr/dohcv #Research #ESPecter #UEFI #Cyberespionage #Cybersecurity #Cyberthreats

First the bootkit #FinSpy was revealed and now #ESPecter, another boot-loader-based attack. #Eclypsium can now detect against both of these invisible, #firmware-centric attacks. Learn more: bit.ly/3ArA8SR

Last week the #FinSpy bootkit was revealed and now #ESPecter, another boot-loader-based attack. #Eclypsium can now detect against both of these invisible, #firmware-centric attacks and fights back. Learn more: bit.ly/3AigwAx

We traced the roots of this threat back to at least 2012; it previously operated as a bootkit for systems with legacy BIOSes. Despite #ESPecter’s long existence, its operations and upgrade to UEFI went unnoticed and have not been documented until now. 4/5

🔍 Les chercheurs d’ESET ont découvert un bootkit UEFI actif et inconnu jusqu’à présent qui persiste sur la partition système EFI. Pour en savoir plus RDV sur notre centre presse ▶ ow.ly/Qo5k30rWMRg #cybersecurite #ESPecter #MardiConseil

New #UEFIBootkit Performs Espionage A new #ESPecter #bootkit was uncovered that performs #cyberespionage and compromises system partitions. There are signs in the #Malware's components that revealed that the #attackers could be #Chinesespeaking.

ESET detectó un bootkit llamado #ESPecter que cibercriminales están usando como backdoor en SO Windows, principalmente enfocándolo en espionaje. No está confirmado si un estado-nación patrocina el desarrollo pero tiene tintes chinos. buff.ly/3ixDuNW by @welivesecurity

#UEFI threats moving to the ESP: Introducing #ESPecter bootkit | WeLiveSecurity welivesecurity.com/2021/10/05/uef… #infosec #malware < 👻

#ESPecter, un #bootkit invisibile in circolazione dal 2012, ruba #datisensibili bypassando i #sistemi #antimalware di #Windows. 💻 Per sapere di più leggi l'articolo di #securityinfo. ✏️cutt.ly/xEC8qVf

Something went wrong.
Something went wrong.
United States Trends
- 1. Josh Allen 38.5K posts
- 2. Texans 59.1K posts
- 3. Bills 151K posts
- 4. Joe Brady 5,248 posts
- 5. #MissUniverse 443K posts
- 6. #MissUniverse 443K posts
- 7. Anderson 28.1K posts
- 8. Troy 12.4K posts
- 9. McDermott 4,630 posts
- 10. #StrayKids_DO_IT_OutNow 50.3K posts
- 11. Beane 2,824 posts
- 12. Maxey 13.8K posts
- 13. Technotainment 20.3K posts
- 14. Stroud 3,730 posts
- 15. #htownmade 3,975 posts
- 16. #criticalrolespoilers 2,233 posts
- 17. Al Michaels N/A
- 18. Costa de Marfil 25.5K posts
- 19. Fátima 196K posts
- 20. Shakir 5,707 posts



























































