#hashfunctions search results
#Tsinghua professor Wang Xiaoyun becomes the first female recipient of the "Future Science Prize ". Prof. Wang has been awarded prizes in both mathematics and computer science for her contributions to #cryptography and renewing our current understanding of #HashFunctions.



Ever pondered how #hashfunctions and #digitalsignatures work in Bitcoin? @T_o_d_d_P of the Bitcoin SV Academy breaks it down and delves into transactions as per the #Bitcoinwhitepaper. Catch the highlights, then enjoy the full talk on our YouTube: 🔗fal.cn/3AGG1
This is a very interesting insight into #HashFunctions from the #Google FarmHash team. Hash functions are useful when you want to speed up algorithms, hide information or randomise selection. github.com/google/farmhas…

CRYPTO BASICS! | Hash Functions 101 Time to learn about #HashFunctions, another key part of info to learn about in the #Crypto world! Are there any subjects you want to learn about? Comment down below!

#EssentialFundamentals #HashFunctions, a critical component of #blockchain security, create unique 'digests' for every input, ensuring data integrity and protection. In #cryptography, they play an invaluable role in safeguarding information. 🔗 #Qtum #Blockchain #Developers

🎤 Today at #EthCC in #Brussels, we presented a workshop with Ivan Dosev & Mohamed Ali Chelbi on #HashFunctions, #MerkleTrees, and #ZeroKnowledge proofs. The engagement was truly uplifting! I’m very Excited to share & learn more with @RWTHBlockchain 🚀



I also found some time this afternoon to implement tabulation hash functions. It is beginning to look pretty good. amzn.to/2pngZQ0 #amwriting #hashfunctions

Cryptocurrency 101: Proof of Work vs. Proof of Stake - Daily Cryptocurrency #hashfunctions bit.ly/2wk0zdw

Let’s Dive into the world of cryptography and HashFunctions #HashFunctions #Cryptography early morning session @Decentracod special thnx @LiskHQ @SantiagoDevRel let’s keep pushing @PrhymeManuel @DebbyRaavyn @JemimaNoel7319 @maria_nakib @sheweb3 @kakoozavian
New Arrival!! Modern Cryptography: The Practical Guide Sandip Dholakia (Author) @shroffpub & @RheinwerkComp (Publishers) Buy from computer bookshop using this link: tinyurl.com/pn4jdzhs #Symmetricandasymmetric #Hashfunctions #digitalsignatures #dataandwebsecurity #computer

🚀 Excitement at #POWSummit in Prague! Bryan Bishop (@kanzure) is set to unravel 'The Joy of Mining'! 🌐 Witness a deep dive into the world of proof of work and explore the intricacies of hash functions with an industry maestro! #ProofOfWork #HashFunctions #CryptoMining

Hash functions are used to create almost irreversible cryptographies where the input is almost impossible to retrieve. Find out more about Hash Table Data Structure with Java. Read article here! 👀 #hash #hashfunctions #java #javacode #software

#Hashfunctions : Tried to wrap my head around the complexity behind numbers on identifying collision hashes. 👇👇 1/10
Blockchain, ledgers, To Bitcoin or To Etherium..that is the question. #collisions #hashfunctions #cryptocurrency #ledgers #BlockchainTechnology


#BlockchainTip Hash functions are the building blocks of blockchain. They convert data into a fixed-size string, ensuring data integrity and confidentiality. #HashFunctions
As one of the laureates of the 2025 L’Oréal-@UNESCO #ForWomenInScience International Awards, Prof. Wang Xiaoyun is rewarded for her significant contribution to #cryptography and cryptographic mathematics, especially the cryptanalysis and design of #HashFunctions.

Unlocking the Power of #Cryptographic #HashFunctions: A Practical Guide to #Cybersecurity buff.ly/3W13tBk

Estudiando SHA-2 y 3, Tiger y Whirlpool #hashfunctions
CRYPTO BASICS! | Hash Functions 101 Time to learn about #HashFunctions, another key part of info to learn about in the #Crypto world! Are there any subjects you want to learn about? Comment down below!

The Power of Hash Functions: Get started with blockchain basics and understand the importance of hash functions in securing data. #BlockchainTechnology #HashFunctions #DataSecurity dealdrivetechnology.com/blockchain-has…
As one of the laureates of the 2025 L’Oréal-@UNESCO #ForWomenInScience International Awards, Prof. Wang Xiaoyun is rewarded for her significant contribution to #cryptography and cryptographic mathematics, especially the cryptanalysis and design of #HashFunctions.

Let’s Dive into the world of cryptography and HashFunctions #HashFunctions #Cryptography early morning session @Decentracod special thnx @LiskHQ @SantiagoDevRel let’s keep pushing @PrhymeManuel @DebbyRaavyn @JemimaNoel7319 @maria_nakib @sheweb3 @kakoozavian

Ensuring Data Integrity with Cryptographic Hash Functions 🔒 Project Details on link: linkedin.com/posts/chinonso… #CyberSecurity #DataIntegrity #HashFunctions #SHA256 #InformationSecurity #LearningJourney #DigitalTrust #3MTT #CyberKris


5/ Hashes are like fingerprints for data. They’re unique, and even a tiny change makes a new fingerprint. This keeps Bitcoin secure! #HashFunctions
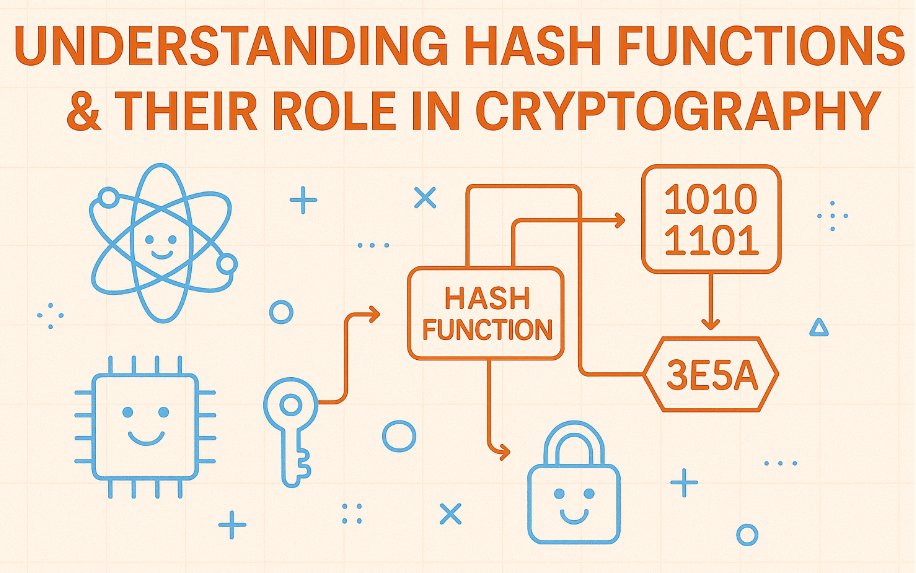
Explore the fundamental role of hash functions in modern cryptography — from securing passwords to verifying digital signatures. This article offers a clear and accessible introduction to this crucial concept. medium.com/@aannkkiittaa/… #Cryptography #CyberSecurity #HashFunctions
Noninvertibility in hash functions is like the ocean dispersing sand: it ensures preimage resistance by making it nearly impossible to reverse the process and find the original input, just as you can't retrieve a specific grain from the sea. #Cryptography #HashFunctions
Hash functions ensure data integrity and message authentication in both symmetric and public key crypto. Cryptographers aim for computational security, making it nearly impossible for attackers to find message digests or collisions. #Cryptography #Security #HashFunctions
Hash functions are key in crypto, varying widely in use. Exploring the basics, terms, and the concept of an ideal yet unattainable random oracle model is essential for understanding system design in cryptography. #Cryptography #HashFunctions #Security
(6/11) 🚀 Hash functions: Convert data into a fixed-size string of characters (e.g., SHA-256). #HashFunctions
Unlocking the Power of #Cryptographic #HashFunctions: A Practical Guide to #Cybersecurity buff.ly/3W13tBk

#Tsinghua professor Wang Xiaoyun becomes the first female recipient of the "Future Science Prize ". Prof. Wang has been awarded prizes in both mathematics and computer science for her contributions to #cryptography and renewing our current understanding of #HashFunctions.



Curious about hash functions? Find out how these coding tools work and keep your data secure!💡🔒#cybersecurity #techexplained #hashfunctions #CashtreeToken #CTT



Unlock the mysteries of hash functions! 🧩 Discover how they secure data and make digital magic happen. 🔐 #hashfunctions #CashtreeToken #CTT



🎤 Today at #EthCC in #Brussels, we presented a workshop with Ivan Dosev & Mohamed Ali Chelbi on #HashFunctions, #MerkleTrees, and #ZeroKnowledge proofs. The engagement was truly uplifting! I’m very Excited to share & learn more with @RWTHBlockchain 🚀



New Arrival!! Modern Cryptography: The Practical Guide Sandip Dholakia (Author) @shroffpub & @RheinwerkComp (Publishers) Buy from computer bookshop using this link: tinyurl.com/pn4jdzhs #Symmetricandasymmetric #Hashfunctions #digitalsignatures #dataandwebsecurity #computer

--- 🔐 Unlocking the Power of Hash Functions in Blockchain! 🌐 Today, let's dive into the world of hash functions and their significance in blockchain technology. #Blockchain #HashFunctions .

CRYPTO BASICS! | Hash Functions 101 Time to learn about #HashFunctions, another key part of info to learn about in the #Crypto world! Are there any subjects you want to learn about? Comment down below!

This is a very interesting insight into #HashFunctions from the #Google FarmHash team. Hash functions are useful when you want to speed up algorithms, hide information or randomise selection. github.com/google/farmhas…

As one of the laureates of the 2025 L’Oréal-@UNESCO #ForWomenInScience International Awards, Prof. Wang Xiaoyun is rewarded for her significant contribution to #cryptography and cryptographic mathematics, especially the cryptanalysis and design of #HashFunctions.

#EssentialFundamentals #HashFunctions, a critical component of #blockchain security, create unique 'digests' for every input, ensuring data integrity and protection. In #cryptography, they play an invaluable role in safeguarding information. 🔗 #Qtum #Blockchain #Developers

🚀 Excitement at #POWSummit in Prague! Bryan Bishop (@kanzure) is set to unravel 'The Joy of Mining'! 🌐 Witness a deep dive into the world of proof of work and explore the intricacies of hash functions with an industry maestro! #ProofOfWork #HashFunctions #CryptoMining

"Hash functions may seem random, but they are actually deterministic, meaning given the same input, the output will always be the same. This is useful for verifying data integrity, but not for cryptography where true randomness is required." #HashFunctions #Cryptography

Cryptocurrency 101: Proof of Work vs. Proof of Stake - Daily Cryptocurrency #hashfunctions bit.ly/2wk0zdw

Let’s Dive into the world of cryptography and HashFunctions #HashFunctions #Cryptography early morning session @Decentracod special thnx @LiskHQ @SantiagoDevRel let’s keep pushing @PrhymeManuel @DebbyRaavyn @JemimaNoel7319 @maria_nakib @sheweb3 @kakoozavian

#DataIntegrity #HashFunctions #DataSecurity #DataProtection #CyberSecurity #kartheekchanda #ersegmentsolutionspvtltd #ersegment

I also found some time this afternoon to implement tabulation hash functions. It is beginning to look pretty good. amzn.to/2pngZQ0 #amwriting #hashfunctions

Hash functions are used to create almost irreversible cryptographies where the input is almost impossible to retrieve. Find out more about Hash Table Data Structure with Java. Read article here! 👀 #hash #hashfunctions #java #javacode #software

Blockchain, ledgers, To Bitcoin or To Etherium..that is the question. #collisions #hashfunctions #cryptocurrency #ledgers #BlockchainTechnology



🔥🔒#WikiTrade Dive into the secrets of #Cryptographic #HashFunctions 🌐 Unlock the power of secure transactions in #Forex 💵 Read our latest article & stay ahead of the curve! 🚀 wikitrade.com/en/cryptograph… #CryptoHash #SecurityFirst #TradeWisely 🔄 Comment for more insights! 💬

Something went wrong.
Something went wrong.
United States Trends
- 1. Brian Kelly 12K posts
- 2. #VERZUZ 49.9K posts
- 3. Yamamoto 53.2K posts
- 4. Birdman 13.2K posts
- 5. No Limit 33K posts
- 6. Mia X 578K posts
- 7. Cash Money 28.4K posts
- 8. Wayne 37.8K posts
- 9. Michigan 38.3K posts
- 10. Death Valley 4,219 posts
- 11. #GoBlue 3,497 posts
- 12. Texas A&M 11.4K posts
- 13. Turk 590K posts
- 14. Salter 1,349 posts
- 15. #HalloweenHavoc 48.2K posts
- 16. Aggies 4,491 posts
- 17. Jonas Brothers 6,605 posts
- 18. Tamar 8,133 posts
- 19. Snoop 10.9K posts
- 20. Jonathan Smith N/A