#networksecurityarchitecture 검색 결과
Cybersecurity Tools For Networking • Wireshark → Used for network traffic analysis and packet inspection. • Nmap → Network scanner for discovering devices, open ports, and services. • Snort → Intrusion detection and prevention system (IDS/IPS). • SolarWinds → Network…

.@cysic_xyz , @wardenprotocol 그리고 @zkPass 가 AI와 ZK 기술을 결합하여 크로스체인 보안 및 검증 프레임워크를 어떻게 구축할 수 있을까? 이 프레임워크는 Cysic의 하드웨어 가속 영지식 증명 네트워크, Warden Protocol의 SPEX 검증 계층 그리고 zkPass의 개인정보 보호형 zkTLS 오라클을…



The foundation of tomorrow’s financial system starts here. • Privacy at the core. • Compliance as standard. • Trust without compromise. Welcome to ENTRY.

Part III of the #HackenTRUSTSummit ⚡️ As blockchain scales, security moves beyond code – into the infrastructure powering custody, storage, and global markets. This block unites the builders and defenders shaping how digital assets stay secure, resilient, and interoperable 👇

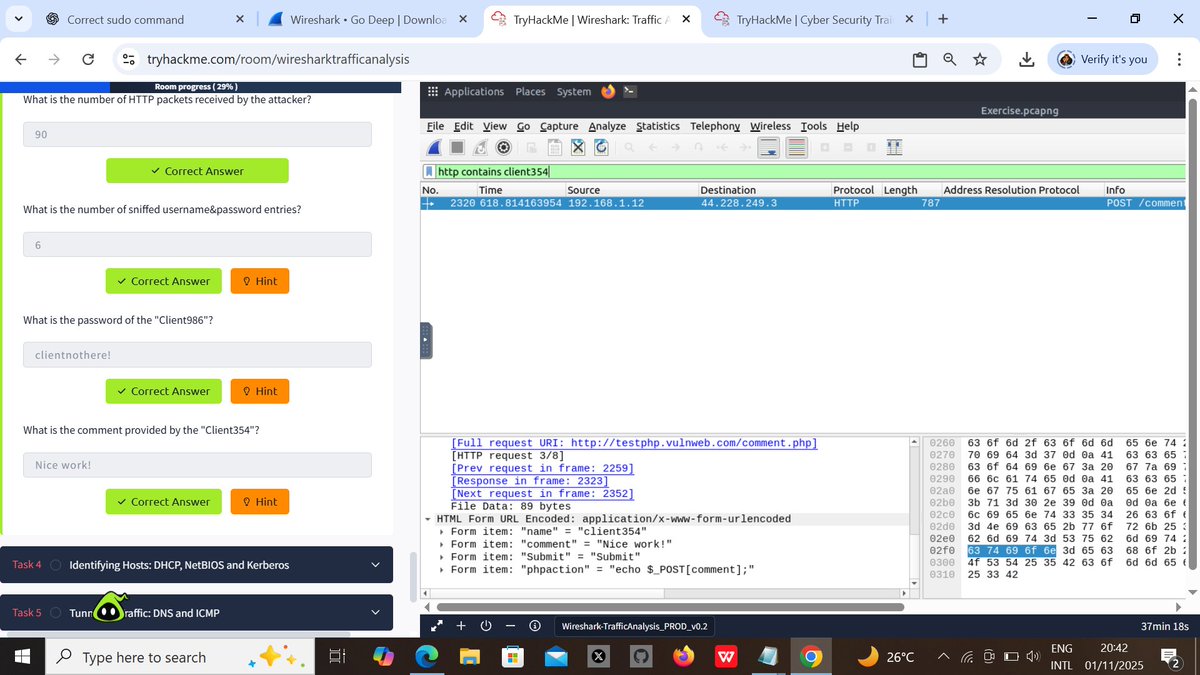
Day 31/100 of #TryHackme Back after 2 days off (TryHackMe subscription issue). Today I started Wireshark traffic analysis, completed Nmap scans + ARP poisoning / MITM tasks. Learned to spot SYN/TCP/UDP scans and ARP spoofing using Wireshark filters & column @ireteeh
Day 28/100 of #TryHackMe Challenge Today i completed the Wireshark Basic and Packet operations module. @ireteeh

Claude Skills shows the power of leveraging skill catalogs at inference time. Our new paper shows that skills can transform AI safety too 🔒 🚨 Adversarial Déjà Vu: Jailbreak Dictionary Learning for Stronger Generalization to Unseen Attacks We find that most “new” jailbreaks…


Hello Cyber friends, let’s talk about the importance of network segmentation 👇🏾 It protects sensitive information It enhances monitoring and detection It limits the spread of Cyber attacks It improves regulatory compliance Network segmentation keeps your digital house…
AEGIs: Absolute Digital Asset Security *Essence: Strategic digital infrastructure. 🛡️ *Pillars: 1. Proactive AI-based security. 🤖 2. Resilience and agile governance. 🔄 3. Intelligent digital inheritance. 💎 Link:sidrastart.com/project/0006be…
Can #cybersecurity withstand the new #AI era? buff.ly/n4B3FID #tech #AgenticAI #genAI #security #leadership #management #business #governance #cyberthreats #cyberattacks #databreaches #CISO #CIO #CTO #CEO @WEF @BatutaPlatform @BetaMoroney @ChuckDBrooks @YuHelenYu…

🐍 GM fam. Let’s talk about @symbioticfi ➖ the protocol that’s quietly becoming the backbone of Ethereum’s modular security stack. Symbiotic = universal staking layer It’s an entire architecture that lets anyone ➖ from individual users to institutions ➖ stake any asset (ETH,…

🏆 Another big win for the ExtraHop team! We’ve been named the 2025 Cloud-Based Network Security Solution of the Year by the CyberSecurity Breakthrough Awards! Our Global Threat Landscape Report confirms the challenge: security leaders overwhelmingly agree the public cloud is…

🚨 Nation-state affiliated threat actors have compromised F5’s systems & downloaded portions of its BIG-IP source code—posing serious risk to FCEB agencies. Follow the guidance in ED 26-01 immediately to protect systems from potential exploits. 🔗 go.dhs.gov/isY
🚀 My Recent Cybersecurity Project: Network Recon & Security Mapping with Nmap 🔍 A Thread (🧵) I’m excited to share my recent hands-on cybersecurity project, where I used Nmap for advanced network scanning, analysis, and security assessment—all without any extra tools! 🛡️ 🔧…


I managed to capture what an IT environments security looks like if only endpoint security, & no network security (ingress/egress rules etc.) are in use Here, using water as packets, we see all the hosts 'Auto Protect' feature ridding the whole environment of bad actors packets
Network Pentesting Mindmap 🔥 Author: Casterbyte Link: github.com/casterbyte/Net… - Traffic Hijacking - MiTM Attacks - Dynamic IGP Routing - Configuration Exfiltration - DoS - NAC/802.1X Bypassing - GRE Pivoting - Cisco EEM for hiding user - Authentication Cracking - Information…

Explore the key components of network security architecture, from firewalls to VPNs Blog link: 🔗 lnkd.in/gjDPEw_G #NetworkSecurityArchitecture #intrusiondetection #VirtualPrivateNetworks #AccessControlLists #dataencryption #compliancestandards #businesscontinuity

#cybersecurityarchitecture #CyberSecurity #NetworkSecurityArchitecture #NetworkArchitecture #teamDeliveryCentric #WeLoveTechnology #QualityOutcomes #OnTimeDelivery #OnBudgetDelivery #MakingCustomersHappy

How many calories does crying while repeatedly bashing your head into a wall burn? Asking for a friend. #NetworkSecurityArchitecture
Are you viewing the entire compass of IT security to ensure your network is safe? Here's a good place to start. hubs.ly/H0fCbwK0 #NetworkSecurity #ITSecurity #NetworkSecurityArchitecture
When was the last time you took a close look at your #NetworkSecurityArchitecture? hubs.ly/H0fjXfT0
There is no business that is 100% safe from cyber threats in today’s world. Is your #NetworkSecurityArchitecture as strong as it could be? hubs.ly/H0f2-Np0
This short video will give you the analogy we use for objectively reviewing your #NetworkSecurity strategy. hubs.ly/H0cYhQq0 #NetworkSecurityArchitecture #ITSecurity
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgDr #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgDy #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEN #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEi #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEv #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgF0 #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEW #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgDK #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgDw #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEf #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEo #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEl #networksecurityarchitecture
Tips For Making Your Network's #DMZ More Secure ow.ly/mNgEE #networksecurityarchitecture
#cybersecurityarchitecture #CyberSecurity #NetworkSecurityArchitecture #NetworkArchitecture #teamDeliveryCentric #WeLoveTechnology #QualityOutcomes #OnTimeDelivery #OnBudgetDelivery #MakingCustomersHappy

Explore the key components of network security architecture, from firewalls to VPNs Blog link: 🔗 lnkd.in/gjDPEw_G #NetworkSecurityArchitecture #intrusiondetection #VirtualPrivateNetworks #AccessControlLists #dataencryption #compliancestandards #businesscontinuity

Something went wrong.
Something went wrong.
United States Trends
- 1. Carson Beck 3,618 posts
- 2. Vandy 12.5K posts
- 3. Miami 59.2K posts
- 4. Clemson 11.6K posts
- 5. Mario 63.1K posts
- 6. Lagway 1,387 posts
- 7. Jeff Sims 1,246 posts
- 8. #UFCVegas110 3,815 posts
- 9. Jeremiah Smith 8,983 posts
- 10. Ohio State 17.3K posts
- 11. Texas 113K posts
- 12. Dabo 2,919 posts
- 13. Dawson 4,614 posts
- 14. Vanderbilt 10.1K posts
- 15. Julian Sayin 6,978 posts
- 16. Pavia 4,570 posts
- 17. #iufb 1,242 posts
- 18. #HookEm 4,243 posts
- 19. Phil Rowe N/A
- 20. Duke 19.8K posts






































