#opendir نتائج البحث
A new #Opendir spotted: hxxps://www[.]danhinsley[.]com/downloads/ — contains 21 .EXE files. Handle with caution. Good source for #Malware analysts. #Opendir #Malware
![cyberfeeddigest's tweet image. A new #Opendir spotted: hxxps://www[.]danhinsley[.]com/downloads/ — contains 21 .EXE files. Handle with caution. Good source for #Malware analysts.
#Opendir #Malware](https://pbs.twimg.com/media/G7BxAsOX0AAaZlG.jpg)
So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔 🔸 https://rapid7labs[.]com/printer.html (#opendir) "Printer Vulnerability Remediation Steps" (possibly related to this…
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRJCwWIAAqJ7b.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRwcLXgAAAGau.png)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kTyliXcAUsm15.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kU3nWXcAA-aY1.png)
#clickfix -> download j.txt otherwise there's other stuff here in #opendir cc: @500mk500 @JAMESWT_WT 👇 urlhaus.abuse.ch/host/kjarz.com/ bazaar.abuse.ch/sample/8986d30… bazaar.abuse.ch/sample/ba8f231…



#Malware KL Remota "Zeus" 🇧🇷 Payloads #Opendir hxxp://92.205.129.120/ Contador hxxps://3illeceara1e2.likescandy.com/ C2 92.205.231.]161:80
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTZN9XwAEpBBN.png)
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTb0hX0AA-7zC.png)

🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
#Malware posible APT-C-36 🇨🇴 Remcos & njrat #Opendir hxxp://167.0.201.5/ hxxps://186.169.63.46/ hxxp://190.9.223.135/ hxxp://186.169.83.212/ C2 sost2024ene.]duckdns.]org:1213 remcosoct.]duckdns.]org:4576 02oct.]duckdns.]org:9001
![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAaw6OXIAAtFrU.png)
![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAa1pQWMAARd3n.png)
![jstrosch's tweet image. some #opendir (reverse) #base64 fun :)
hxxp://52.152.223[.]228/](https://pbs.twimg.com/media/F3lJF4MbQAAP9qW.png)
![jstrosch's tweet image. some #opendir (reverse) #base64 fun :)
hxxp://52.152.223[.]228/](https://pbs.twimg.com/media/F3lJMnracAEalwc.png)
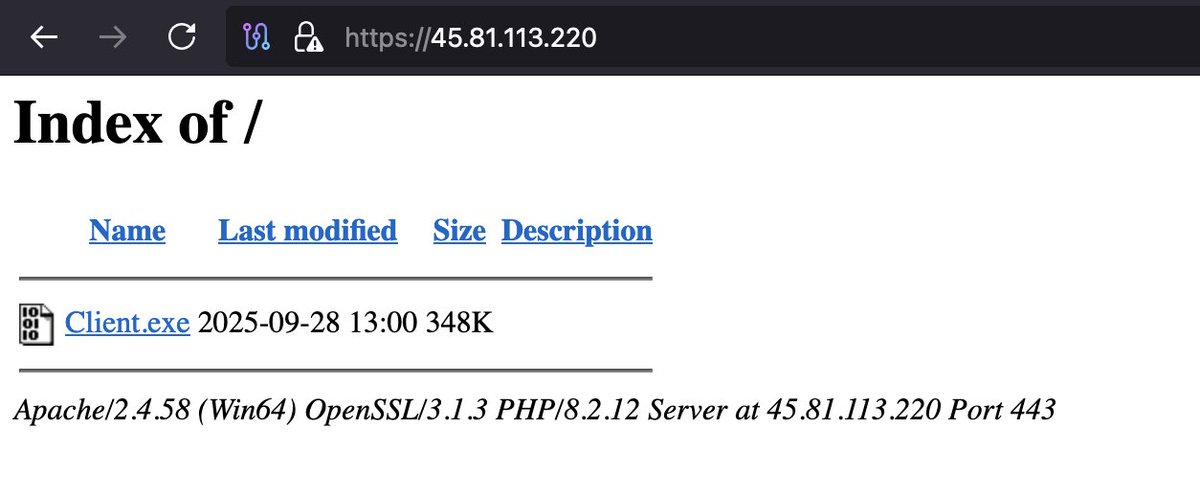
🚨#Opendir #Malware🚨 hxxps://45.81.113.220/ ⚠️#QuasarRAT ☣️📸Client.exe➡️efffe2afbc5d8a0ad85b16155f0e1ed6 📡📸tcp://45.81.113.220:1605


💡No #opendir? Why don't you check for .DS_Store files listing the structure ? Our scans found 11,856,006 IPs and DNS exposing the file. Link: leakix.net/search?scope=l… Ref: 0day.work/parsing-the-ds…

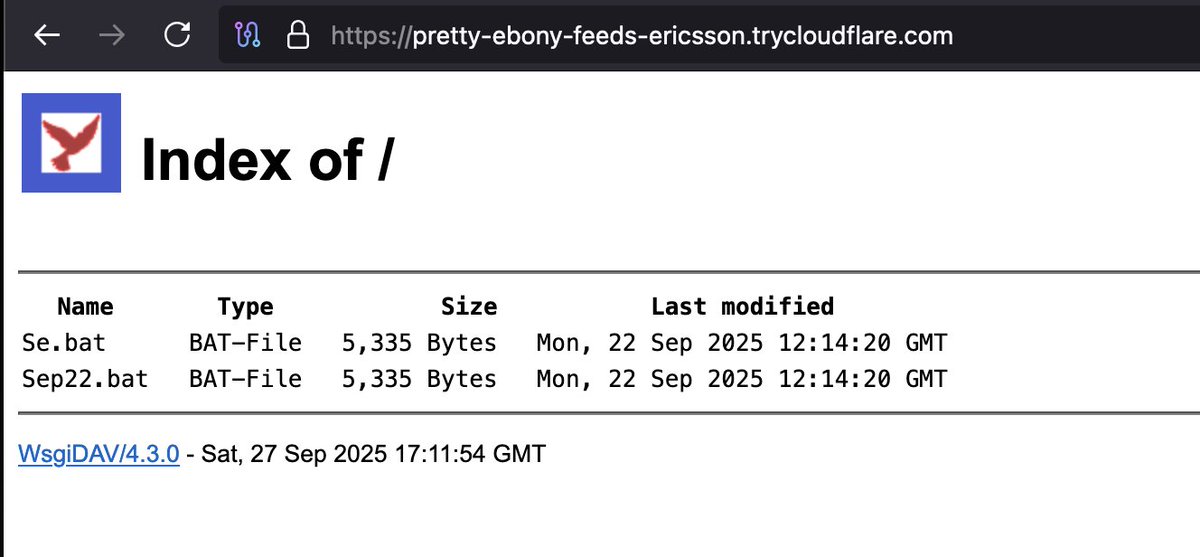
#Cloudflare sites with 🚨#Opendir #Malware🚨 1⃣hxxps://pretty-ebony-feeds-ericsson.trycloudflare.com/ 2⃣hxxps://watches-omaha-partnerships-median.trycloudflare.com/ 3⃣hxxps://static-obligations-baths-carnival.trycloudflare.com/


A new #Opendir spotted: hxxps://www[.]danhinsley[.]com/downloads/ — contains 21 .EXE files. Handle with caution. Good source for #Malware analysts. #Opendir #Malware
![cyberfeeddigest's tweet image. A new #Opendir spotted: hxxps://www[.]danhinsley[.]com/downloads/ — contains 21 .EXE files. Handle with caution. Good source for #Malware analysts.
#Opendir #Malware](https://pbs.twimg.com/media/G7BxAsOX0AAaZlG.jpg)
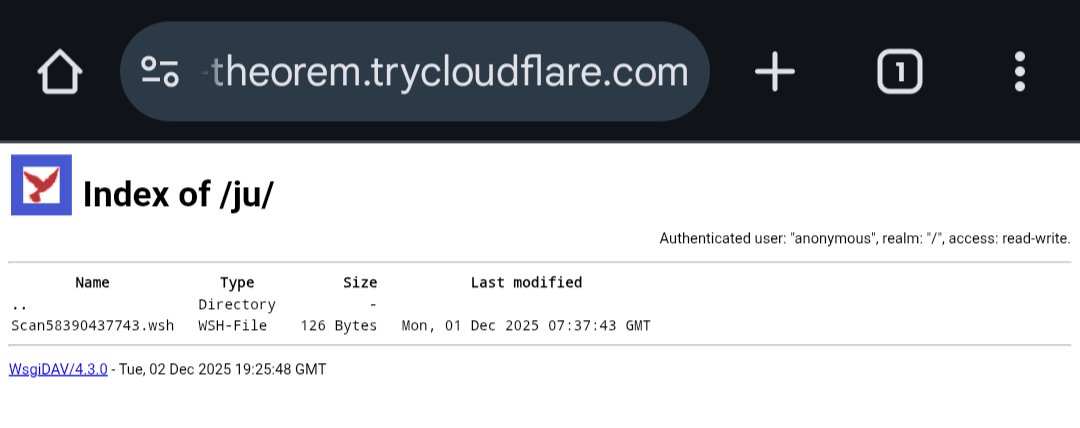
hxxps://mem-wedding-reputation-regulated.trycloudflare(.)com/ #WsgiDAV #opendir 'Rechnung_2025_11_33828247000801.pdf.lnk' bazaar.abuse.ch/sample/4045825…


#Opendir hxxp://dl1[.]iranroid[.]com/software/persian_apps/. Hundreds of .apk files exposed. Good source for #Malware analysts — handle with caution. #Opendir #Malware
![cyberfeeddigest's tweet image. #Opendir hxxp://dl1[.]iranroid[.]com/software/persian_apps/. Hundreds of .apk files exposed. Good source for #Malware analysts — handle with caution.
#Opendir #Malware](https://pbs.twimg.com/media/G7BwSwBWMAAjt_r.jpg)
#Payloads #Opendir hxxps://wedding-tray-interracial-authorities.trycloudflare.com/ BB1.txt➡️ 1⃣The script relaunches itself via PowerShell in mode hide 2⃣Opens a legit random PDF as decoy 3⃣Generates random filenames via custom function 4⃣📸⤵️Uses Base64-encoded C2 URLs


#Opendir alert 🚨 An exposed directory found at hxxp://www[.]irai[.]com/pp/ containing 15 .EXE and 57 .apk files. Flagged by Google Chrome as “Dangerous”. Handle with caution. Good source for #Malware analysts. #Opendir #Malware
![cyberfeeddigest's tweet image. #Opendir alert 🚨 An exposed directory found at hxxp://www[.]irai[.]com/pp/ containing 15 .EXE and 57 .apk files. Flagged by Google Chrome as “Dangerous”.
Handle with caution. Good source for #Malware analysts.
#Opendir #Malware](https://pbs.twimg.com/media/G7BueKDWMAE8W-v.jpg)
#remcos on new IP #opendir cc: @500mk500 @JAMESWT_WT urlhaus.abuse.ch/host/181.235.1… AS3816 urlhaus.abuse.ch/asn/3816/

#Opendir hxxps://www.launch[.]sk/download/. Contains 23 .apk files. Handle with caution — potential risk. Good source for #Malware analysts. #Opendir #Malware
![cyberfeeddigest's tweet image. #Opendir hxxps://www.launch[.]sk/download/. Contains 23 .apk files. Handle with caution — potential risk. Good source for #Malware analysts.
#Opendir #Malware](https://pbs.twimg.com/media/G7BvXYNWoAASesB.jpg)
#opendir #remcos cc: @500mk500 @JAMESWT_WT hta. -> hex+XOR(0x37) -> powershell script -> download zip -> extract -> run exe SyAlpha16.exe -> FrameTrac32.exe -> remcos app.any.run/tasks/fcc2769d… "C2": [ "seguritypostload/.duckdns.org:1122" ], 👇 urlhaus.abuse.ch/host/192.159.9…
![BlinkzSec's tweet image. #opendir #remcos
cc: @500mk500 @JAMESWT_WT
hta. -> hex+XOR(0x37) -> powershell script -> download zip -> extract -> run exe
SyAlpha16.exe -> FrameTrac32.exe -> remcos
app.any.run/tasks/fcc2769d…
"C2": [
"seguritypostload/.duckdns.org:1122"
],
👇
urlhaus.abuse.ch/host/192.159.9…](https://pbs.twimg.com/media/G666Hk0WIAAq5y9.png)
![BlinkzSec's tweet image. #opendir #remcos
cc: @500mk500 @JAMESWT_WT
hta. -> hex+XOR(0x37) -> powershell script -> download zip -> extract -> run exe
SyAlpha16.exe -> FrameTrac32.exe -> remcos
app.any.run/tasks/fcc2769d…
"C2": [
"seguritypostload/.duckdns.org:1122"
],
👇
urlhaus.abuse.ch/host/192.159.9…](https://pbs.twimg.com/media/G666KL5XUAAlEAm.jpg)
![BlinkzSec's tweet image. #opendir #remcos
cc: @500mk500 @JAMESWT_WT
hta. -> hex+XOR(0x37) -> powershell script -> download zip -> extract -> run exe
SyAlpha16.exe -> FrameTrac32.exe -> remcos
app.any.run/tasks/fcc2769d…
"C2": [
"seguritypostload/.duckdns.org:1122"
],
👇
urlhaus.abuse.ch/host/192.159.9…](https://pbs.twimg.com/media/G666Q06XAAAWzar.png)
#clickfix -> download j.txt otherwise there's other stuff here in #opendir cc: @500mk500 @JAMESWT_WT 👇 urlhaus.abuse.ch/host/kjarz.com/ bazaar.abuse.ch/sample/8986d30… bazaar.abuse.ch/sample/ba8f231…



“#Opendir spotted — contains utility samples incl. a Handle with caution. Good source for #Malware analysts hxxps://silentdragon.com/

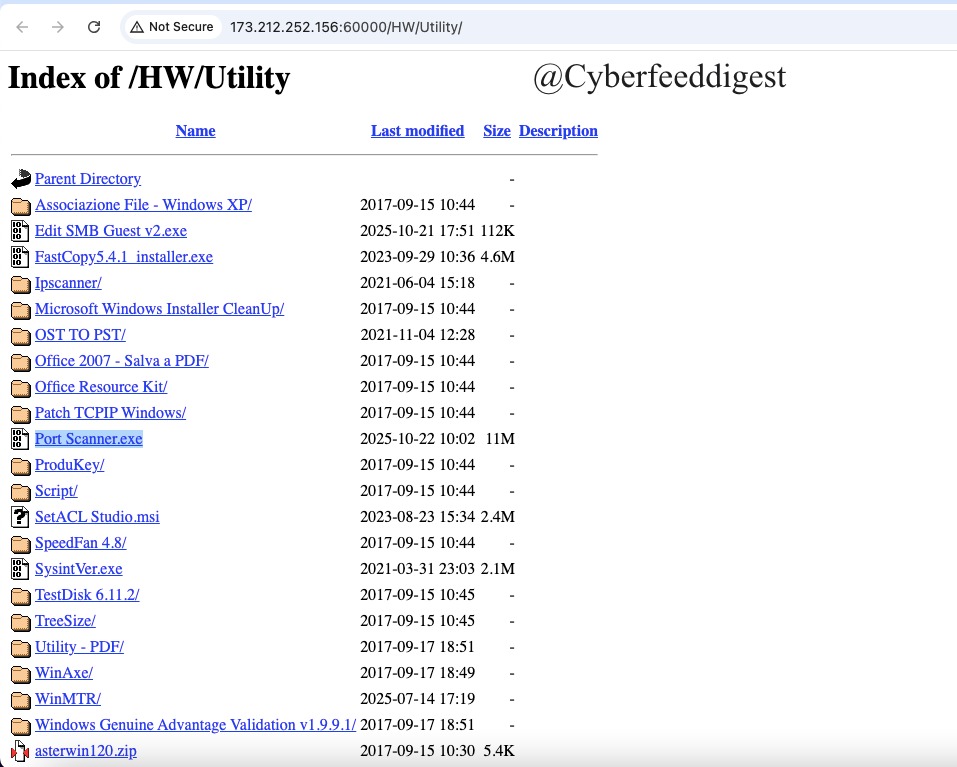
“#Opendir spotted — contains utility samples incl. a port-scanner .exe. Handle with caution. Good source for #Malware analysts hxxp://173.212.252.156:60000/HW/Utility/
🚨 #Opendir spotted at hxxp://info.elf.stuba.sk/packages/pub/pc/comm/ Hosting 478 .EXE files. Handle with caution. Useful for #Malware analysts. Includes: netscan.exe, portscan, ipscan25.exe, netscan #Opendir #Malware

🚨 #Opendir found at hxxps://cloudio[.]dedyn[.]io/~dio/ flagged by Chrome as dangerous. Handle with caution. Useful for #Malware analysts. Sample files include: FTSDeskUpdate.exe, SpaceSniffer.exe, netscan.exe/zip, putty.exe, sleep.exe.
![cyberfeeddigest's tweet image. 🚨 #Opendir found at hxxps://cloudio[.]dedyn[.]io/~dio/
flagged by Chrome as dangerous. Handle with caution. Useful for #Malware analysts.
Sample files include:
FTSDeskUpdate.exe, SpaceSniffer.exe, netscan.exe/zip, putty.exe, sleep.exe.](https://pbs.twimg.com/media/G6SVk2MW0AArF5f.jpg)
New domain, same #OpenDir + new #malware directory. libertytrading-biz[.]com/pure/APPDATA[.]exe "APPDATA.exe" - app.any.run/tasks/99bcb3f6… #stealer #purehvnc #netreactor #zgrat @anyrun_app
🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir #SimpleHelp #ConnectWise #LogMeInResolve etc. Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc. Operation has been…
![eqv_sec's tweet image. 🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir
#SimpleHelp #ConnectWise #LogMeInResolve etc.
Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc.
Operation has been…](https://pbs.twimg.com/media/G5mmsCWWYAAbm0w.png)
🚨#Opendir #Malware🚨 hxxps://45.81.113.220/ ⚠️#QuasarRAT ☣️📸Client.exe➡️efffe2afbc5d8a0ad85b16155f0e1ed6 📡📸tcp://45.81.113.220:1605



#Malware KL Remota "Zeus" 🇧🇷 Payloads #Opendir hxxp://92.205.129.120/ Contador hxxps://3illeceara1e2.likescandy.com/ C2 92.205.231.]161:80
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTZN9XwAEpBBN.png)
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTb0hX0AA-7zC.png)

#Malware posible APT-C-36 🇨🇴 Remcos & njrat #Opendir hxxp://167.0.201.5/ hxxps://186.169.63.46/ hxxp://190.9.223.135/ hxxp://186.169.83.212/ C2 sost2024ene.]duckdns.]org:1213 remcosoct.]duckdns.]org:4576 02oct.]duckdns.]org:9001
![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAaw6OXIAAtFrU.png)
![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAa1pQWMAARd3n.png)
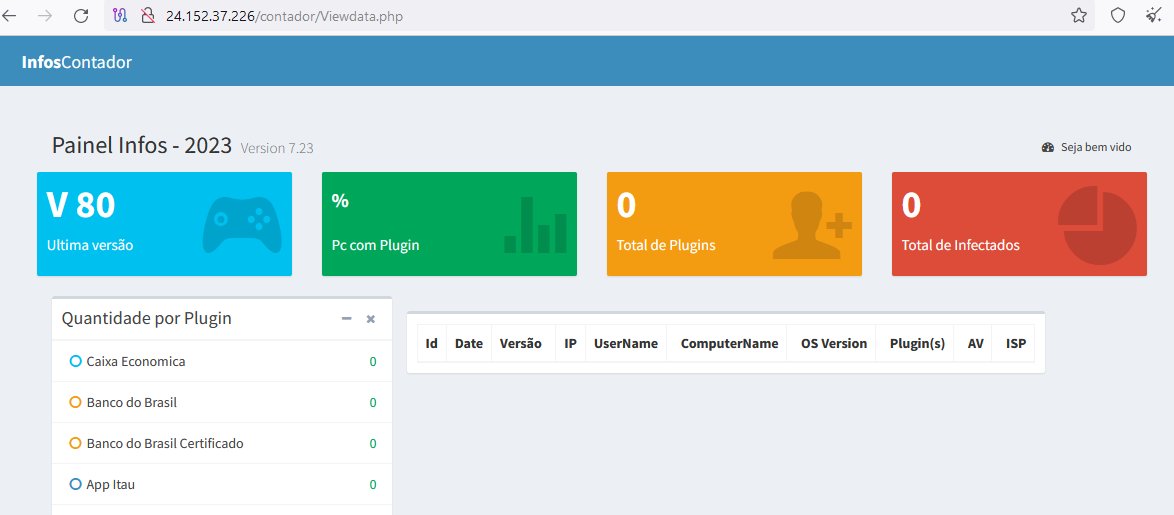
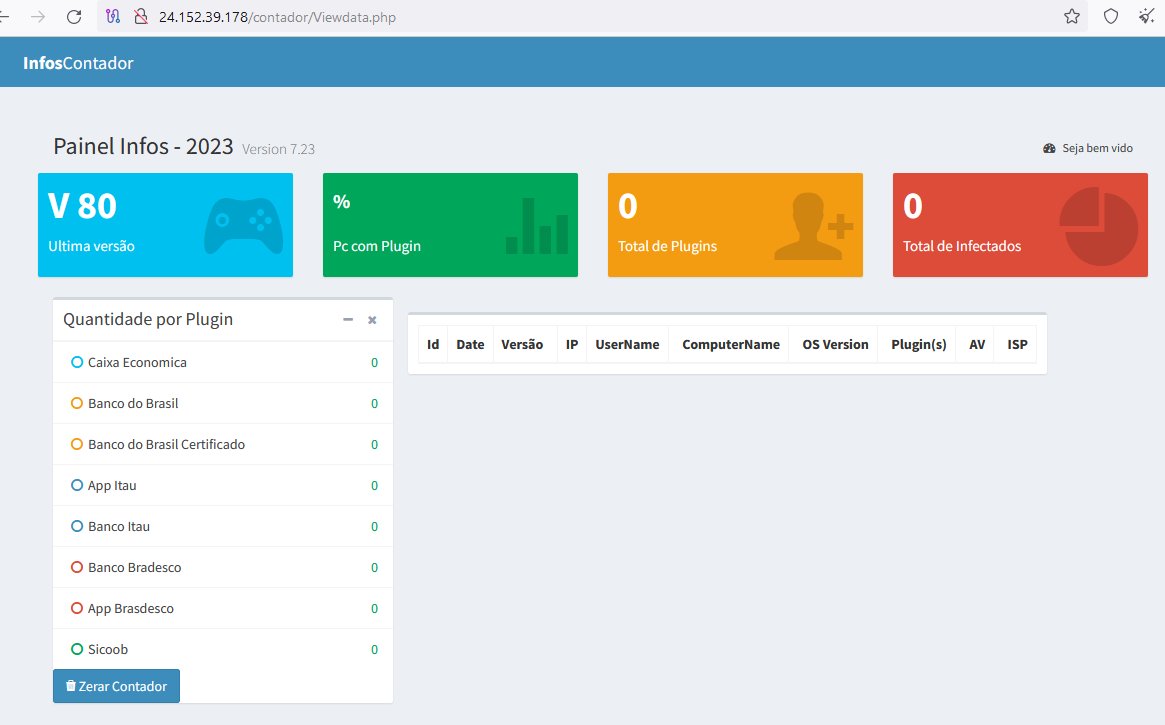
#Opendir #Panel 🇧🇷 Sites: hxxp://74.207.237.97/ hxxp://24.152.39.178/contador/ hxxp://24.152.37.226/contador/

#venomrat #opendir at: http://trackingshipmentt\.xyz:9394/ http://trackmyshipeng\.site:9094/ app.any.run/tasks/086f767d…


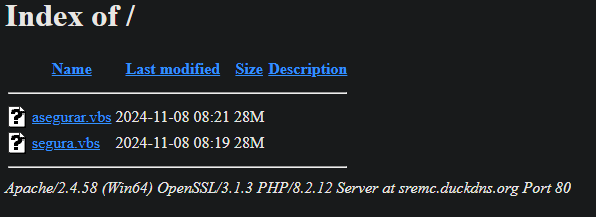
#opendir 106.14.176.]208 Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic. RingQ, an open-source Windows shellcode generator, is also present. A week ago, Vshell was also detected on this IP on port 8082.
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WZl6a8AArWdk.jpg)
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WrsqaoAAgdA1.jpg)

Something went wrong.
Something went wrong.
United States Trends
- 1. FIFA 322K posts
- 2. FINALLY DID IT 431K posts
- 3. The WET 113K posts
- 4. Paraguay 26.2K posts
- 5. Argentina 214K posts
- 6. Brazil 74.6K posts
- 7. Portugal 96.6K posts
- 8. Croatia 23.1K posts
- 9. Matt Campbell 10.6K posts
- 10. Warner Bros 234K posts
- 11. Group L 16.6K posts
- 12. #USMNT 1,372 posts
- 13. Hep B 1,686 posts
- 14. Infantino 69.3K posts
- 15. Iowa State 8,993 posts
- 16. Ghana 78.7K posts
- 17. Frank Gehry 2,988 posts
- 18. Senegal 48.1K posts
- 19. Norway 29.7K posts
- 20. #Mundial2026 37.5K posts






![medsci_yb3r's tweet image. cc: @skocherhan @smica83
hxxp://freenet[.]am/~zombi
#OpenDir thingy [ more your gig ]](https://pbs.twimg.com/media/G7MyS_EboAA1HjG.jpg)





![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9CvBWUAAtQ_w.png)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9QYtWQAAhz6s.jpg)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9dWiWMAAF5pV.png)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG-TDSXcAAo3Mt.png)



![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pTbQAEg3Aj.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pSbsAA7Eut.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pjboAEM6WC.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7phbQAApvfk.jpg)

















![jstrosch's tweet image. 🤔 #opendir
hxxp://34.101.154[.]50](https://pbs.twimg.com/media/Fxi_nt2XgAI5o0N.jpg)
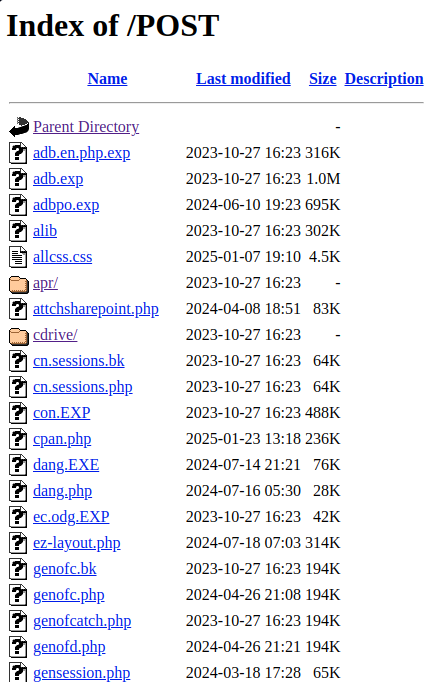



![jstrosch's tweet image. #opendir #redline #agenttesla
hxxp://195.3.223[.]234/](https://pbs.twimg.com/media/F6bLdssWgAAWgsI.png)
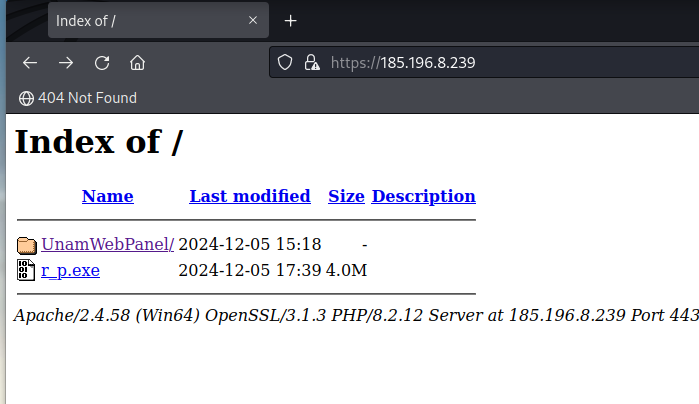
![James_inthe_box's tweet image. #purecryptor #opendir at:
http://198.12.126].164/tst/](https://pbs.twimg.com/media/Gu23X93WAAAhrZQ.jpg)
