#simplehelp 搜尋結果
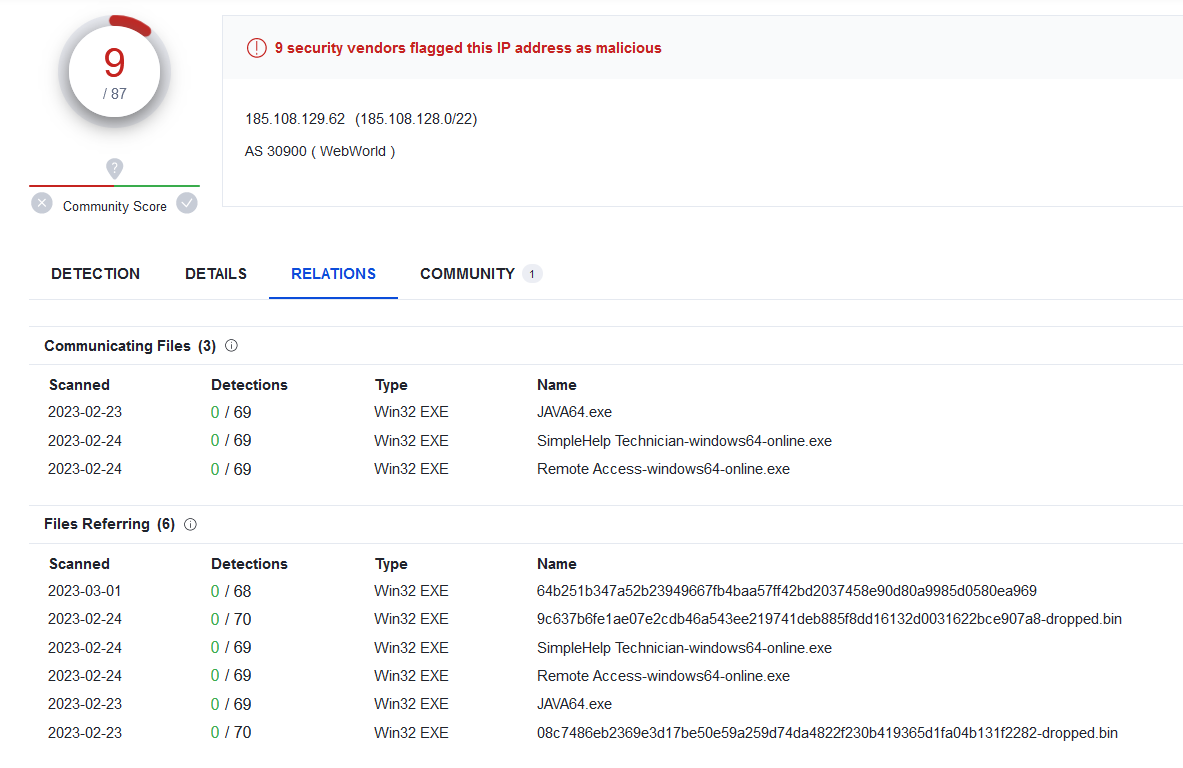
#SimpleHelp is another remote administration tool that is being actively used to maintain access on victim networks. IP 185.108.129.62 was recently seen in a #Medusa ransomware incident and apparently also in a #BianLian case 🧐 The main difference with other tools, is that…

@Giverep��s blockchain tech simplifies giving��no jargon, just a way to help. #SimpleHelp
csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

csirt_it: ‼️ #SimpleHelp: ricercatori di sicurezza hanno recentemente rilevato vulnerabilità, con gravità “critica” e “alta”, relative al noto software di supporto remoto Rischio: 🟠 Tra le tipologie: 🔶 Arbitrary File Write/Read 🔗 …

Los ataques de #ransomware han afectado a aproximadamente 900 organizaciones 📊 y recientemente involucraron la explotación de vulnerabilidades de #SimpleHelp.⚠️☠️




🐾Struggling to keep pet hair under control at home? Let us handle the cleaning so you can relax in a spotless, pet-friendly home.🏡 #Home #PeTHairFree #SimpleHelp #PetFriendly #Cleanzen #Philadelphia #CleanzenPhiladelphia #Spotless #RegularGrooming #FurRemoval

CISA avvisa di vulnerabilità critiche in #SimpleHelp già sfruttate da gruppi #ransomware per colpire #MSP e i loro clienti. 👉 Scopri i 3 passaggi fondamentali per proteggere i tuoi clienti: watchguard.com/it/wgrd-news/b… #Cybersecurity #MSP #Ransomware #ZeroTrust #WGBlog
Hackers are exploiting vulnerabilities in SimpleHelp RMM software, with active threats linked to CVE-2024–57726, CVE-2024–57727, and CVE-2024–57728. Significant risks for affected organizations. 🔓🇺🇸 #SimpleHelp #RMMFlaws link: ift.tt/jR8wD5J

Need help with your crowdfunding campaign? 🎯 I’ll create, promote, and make it shine! Let’s make your ideas a success. Order now! 🚀 #Crowdfunding #SimpleHelp"

Field Effect thwarted a cyberattack exploiting SimpleHelp vulnerabilities, preventing the Sliver backdoor from escalating into a ransomware threat. A reminder of the risks in RMM tools. 🔒⚠️ #SimpleHelp #CyberThreats #Canada link: ift.tt/V4rIebZ

Intel-Ops has also observed what we believe to be a new TTP, using DNS records to host command line queries in TXT records. Continued use of #TacticalRMM, #SimpleHelp and #ReNgine. We will release more information soon.

Critical vulnerabilities found in SimpleHelp remote support software could compromise both servers and clients. Users should upgrade to avoid risks. 🛡️ #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/wYjC2T4

Multiple critical vulnerabilities found in SimpleHelp could lead to file theft and remote code execution. Immediate patching is essential to secure systems. 😱 #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/8TJxiyR

Recent vulnerabilities in SimpleHelp RMM (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) are being exploited by hackers for network breaches. Upgrading is crucial. 🛡️ #SimpleHelp #ArcticWolf #USA link: ift.tt/eWT34Ow

🚨 Vulnerabilities in SimpleHelp remote access software could expose users to unauthenticated access and remote code execution. Patches are available—updating is crucial! 🛡️ #SimpleHelp #RemoteAccess #CyberThreats #CybersecurityNews link: ift.tt/RuMfxOA

Researchers warn of a cyberattack exploiting SimpleHelp RMM vulnerabilities (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728), allowing unauthorized device access. Ensure software is updated! 🔒💻 #SimpleHelp #CyberThreats #USA link: ift.tt/72MSJgs

Hackers are exploiting vulnerabilities in SimpleHelp RMM to create admin accounts and deploy Sliver malware. Active exploits linked to Akira ransomware discovered. Stay vigilant. 🔒 #SliverMalware #SimpleHelp #USA link: ift.tt/ucSr5nV

⚠️ Ransomware ใช้ช่องโหว่ SimpleHelp โจมตี Double Extortion! เรียนรู้วิธีป้องกันฉบับครบจบ #Ransomware #Cybersecurity #SimpleHelp #DoubleExtortion
@Giverep��s blockchain tech simplifies giving��no jargon, just a way to help. #SimpleHelp
CISA avvisa di vulnerabilità critiche in #SimpleHelp già sfruttate da gruppi #ransomware per colpire #MSP e i loro clienti. 👉 Scopri i 3 passaggi fondamentali per proteggere i tuoi clienti: watchguard.com/it/wgrd-news/b… #Cybersecurity #MSP #Ransomware #ZeroTrust #WGBlog
csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

Ransomware actors are exploiting CVE-2024-57727 in SimpleHelp RMM versions 5.5.7 and earlier to access files and deploy ransomware, impacting utility billing providers. Threat groups like DragonForce and Hive linked to these attacks. 🔐 #SimpleHelp #Rans… ift.tt/XDihYTQ
⚠️ Ransomware ใช้ช่องโหว่ SimpleHelp โจมตี Double Extortion! เรียนรู้วิธีป้องกันฉบับครบจบ #Ransomware #Cybersecurity #SimpleHelp #DoubleExtortion
Ransomware gangs are exploiting unpatched SimpleHelp RMM flaws (CVE-2024-57726, 57727, 57728) for double extortion attacks. Versions 5.5.7 and earlier are vulnerable. Isolate servers and patch now to stay secure. #SimpleHelp #CVE2024 #Ransomware #CyberSecurity #PatchNow
The U.S. Cybersecurity and Infrastructure Security Agency (#CISA) on Thursday disclosed that #ransomware actors are targeting unpatched #SimpleHelp Remote Monitoring and Management (#RMM) instances to compromise customers of an unnamed utility billing software provider.…
#SimpleHelp is another remote administration tool that is being actively used to maintain access on victim networks. IP 185.108.129.62 was recently seen in a #Medusa ransomware incident and apparently also in a #BianLian case 🧐 The main difference with other tools, is that…


Los ataques de #ransomware han afectado a aproximadamente 900 organizaciones 📊 y recientemente involucraron la explotación de vulnerabilidades de #SimpleHelp.⚠️☠️




🐾Struggling to keep pet hair under control at home? Let us handle the cleaning so you can relax in a spotless, pet-friendly home.🏡 #Home #PeTHairFree #SimpleHelp #PetFriendly #Cleanzen #Philadelphia #CleanzenPhiladelphia #Spotless #RegularGrooming #FurRemoval

Need help with your crowdfunding campaign? 🎯 I’ll create, promote, and make it shine! Let’s make your ideas a success. Order now! 🚀 #Crowdfunding #SimpleHelp"

csirt_it: ‼️ #SimpleHelp: ricercatori di sicurezza hanno recentemente rilevato vulnerabilità, con gravità “critica” e “alta”, relative al noto software di supporto remoto Rischio: 🟠 Tra le tipologie: 🔶 Arbitrary File Write/Read 🔗 …

Hackers are exploiting vulnerabilities in SimpleHelp RMM software, with active threats linked to CVE-2024–57726, CVE-2024–57727, and CVE-2024–57728. Significant risks for affected organizations. 🔓🇺🇸 #SimpleHelp #RMMFlaws link: ift.tt/jR8wD5J

Intel-Ops has also observed what we believe to be a new TTP, using DNS records to host command line queries in TXT records. Continued use of #TacticalRMM, #SimpleHelp and #ReNgine. We will release more information soon.


Field Effect thwarted a cyberattack exploiting SimpleHelp vulnerabilities, preventing the Sliver backdoor from escalating into a ransomware threat. A reminder of the risks in RMM tools. 🔒⚠️ #SimpleHelp #CyberThreats #Canada link: ift.tt/V4rIebZ

Recent vulnerabilities in SimpleHelp RMM (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) are being exploited by hackers for network breaches. Upgrading is crucial. 🛡️ #SimpleHelp #ArcticWolf #USA link: ift.tt/eWT34Ow

: 🚨 CYBER ALERT: DragonForce Ransomware Attack Hackers from DragonForce are actively exploiting SimpleHelp software flaws to deploy ransomware across customer endpoints! #CyberSecurity #Ransomware #SimpleHelp #DragonForce #Infosec #ThreatIntel #MalwareAlert #EndpointSecurity

Researchers warn of a cyberattack exploiting SimpleHelp RMM vulnerabilities (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728), allowing unauthorized device access. Ensure software is updated! 🔒💻 #SimpleHelp #CyberThreats #USA link: ift.tt/72MSJgs

Hackers are exploiting vulnerabilities in SimpleHelp RMM to create admin accounts and deploy Sliver malware. Active exploits linked to Akira ransomware discovered. Stay vigilant. 🔒 #SliverMalware #SimpleHelp #USA link: ift.tt/ucSr5nV

🚨 Vulnerabilities in SimpleHelp remote access software could expose users to unauthenticated access and remote code execution. Patches are available—updating is crucial! 🛡️ #SimpleHelp #RemoteAccess #CyberThreats #CybersecurityNews link: ift.tt/RuMfxOA

Critical vulnerabilities found in SimpleHelp remote support software could compromise both servers and clients. Users should upgrade to avoid risks. 🛡️ #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/wYjC2T4

Multiple critical vulnerabilities found in SimpleHelp could lead to file theft and remote code execution. Immediate patching is essential to secure systems. 😱 #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/8TJxiyR

csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

Is your remote support tool a silent risk? Critical flaws in #SimpleHelp expose systems to attacks Find out how to protect yourself—fast! Details: secureblink.com/cyber-security… #RCE #Exploit #Hack #RemoteSupport #Vulnerability #Threatfeed #SecureBlink

Last week, @CISAgov added #SimpleHelp CVE-2024-57727 to the KEV: cisa.gov/known-exploite…. ➡️ This vulnerability has been available as a Rapid Response test in #NodeZero for over a month, giving users plenty of time to patch their systems. Don't wait for malicious actors to…

🚨 New from @Horizon3Attack: Three critical vulnerabilities have been disclosed in #SimpleHelp remote support software, which could enable an attacker with no prior privileges to compromise a SimpleHelp server and client machines managed by SimpleHelp. 🔺 CVE-2024-57727:…

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWWrestleDream 47.4K posts
- 2. Kentucky 24.9K posts
- 3. Lincoln Riley 2,327 posts
- 4. Stoops 4,614 posts
- 5. Mizzou 5,112 posts
- 6. Arch 25.8K posts
- 7. Sark 4,302 posts
- 8. #RollTide 7,673 posts
- 9. Bama 15.1K posts
- 10. Notre Dame 15.2K posts
- 11. Texas 170K posts
- 12. Tennessee 52.7K posts
- 13. #UFCVancouver 28.7K posts
- 14. Heupel 2,624 posts
- 15. No Kings 1.72M posts
- 16. #GoIrish 5,179 posts
- 17. Christian Gray N/A
- 18. #HookEm 2,459 posts
- 19. Utah 28.4K posts
- 20. Sam Rivers 16.7K posts