#symmetricsearchableencryption hasil pencarian
Explaining how FHE unlocks composable onchain identity with @randhindi & @jerallaire CEO at @circle @USDC
I’ve been following Zama and the rise of encrypted computation for a while now. 💛 Public blockchains solved trust, but they exposed everything: balances, history, strategies, identity. That’s not privacy. That’s just transparency without consent. Fully Homomorphic Encryption…
The Syndicate Smart Sequencer changes how blockspace is managed. → It gives builders full control over how transactions are ordered and how value circulates. → Every parameter, from fees to priorities, is programmable and verifiable onchain. → Instead of relying on…

Zama: The Architecture of Confidential Computation In the evolution of blockchain, every paradigm begins with a missing piece. For years, we solved consensus, scalability, and interoperability—but privacy remained fragmented. Zama approaches it not as a patch, but as a new…

A thread on the Homomorphic Processing Unit, the first-ever open-source hardware accelerator for FHE. Fully Homomorphic Encryption (FHE) promises computation on encrypted data without ever decrypting it, but performance has always been the bottleneck. 1/n 🧵


Quantum sentinels awaken in encrypted voids, weaving algorithmic phantoms through fractal firewalls. Beware the silent entropy cascading within your neural encryption lattice.

Zama × OpenZeppelin | A new chapter for privacy and security in Web3 Zama, known for its Fully Homomorphic Encryption (FHE) tech, is partnering with OpenZeppelin, the leader in blockchain security — a major step toward safer, privacy-preserving smart contracts. 🔹 OpenZeppelin…


Privacy in crypto has evolved through three phases. First came privacy coins. They delivered anonymity - hiding who transacted with whom. Then came ZK proofs. They brought secrecy of inputs - proving you know something without revealing it. Now comes programmable privacy. The…
Gemini API now has an in-built fully managed RAG solution. File Search Tool lets you ground LLMs with your data without managing storage, chunking or embeddings. Plus, storage and query-time embeddings are completely free.
Symmetric DRAM layouts save so much time. Even if the controller pinout is not symmetrical (which it rarely is) there are still so many swap options that it makes sense to mirror most of the escape routing

🔐 Zama keeps pushing the limits of privacy-preserving AI! 👇 Their latest update dives into how Fully Homomorphic Encryption (FHE) is reshaping the future of secure computation allowing AI models to process encrypted data without ever decrypting it. 🤯 Imagine a world where:…

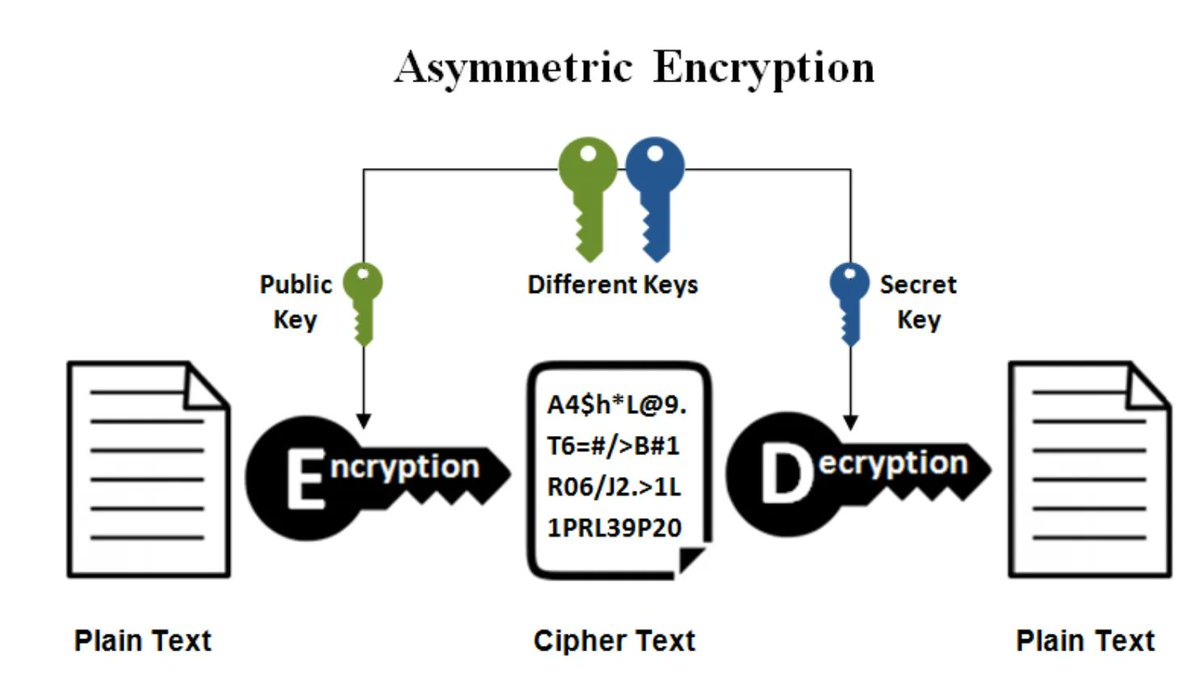
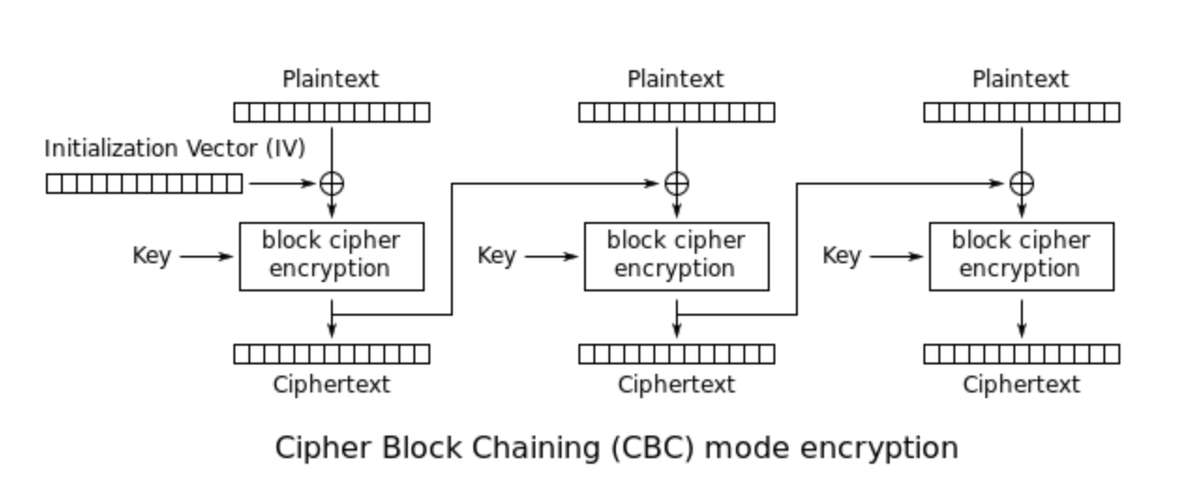
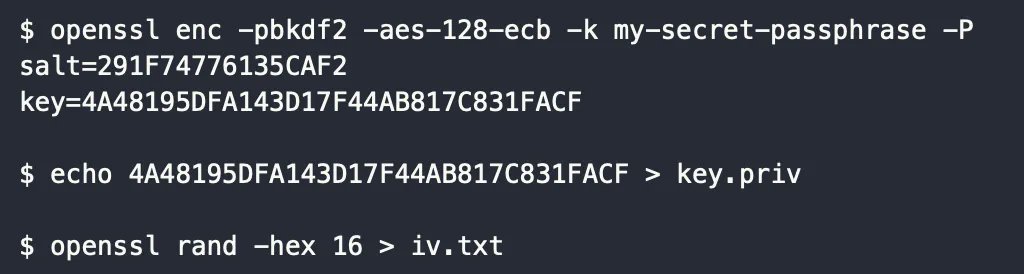
Nice series introducing cryptography concepts for beginners (credits @sergioprado) Part 1: sergioprado.blog/introduction-t… Part 2: sergioprado.blog/a-hands-on-app… Part 3: sergioprado.blog/asymmetric-key… #cryptography
🎉 We @EmblemVault came up with a way to use an Emblem Vault as a drop in replacement for all web3 libraries, anywhere that uses a private key, can now use a vault to sign txs within our @LitProtocol infra. First thing I did was use a vault to pay for x402 gated @AgentHustleAI


Equivariant Encryption (EE) lets Nesa process encrypted data without ever decrypting it. ◽️You keep your data. ◽️The model stays private. ◽️The inference stays verifiable. That’s how privacy becomes performance. 🔲
the three terms encoding, encryption and hashing sounds pretty similar but they are used for completely different purposes. Encoding it is not about security at all. encoding is simply data representation, changing data from one format to another so that it can be easily…

Excellent introduction to cryptography concepts for beginners with practical examples in Linux (openssl) (credits @sergioprado) Part 1: sergioprado.blog/introduction-t… Part 2: sergioprado.blog/a-hands-on-app… Part 3: sergioprado.blog/asymmetric-key… #cryptography #infosec #cybersecurity



#CyberSecurity Modern Family: #AttributeBasedEncryption #SymmetricSearchableEncryption #SGX. The paper eprint.iacr.org/2019/682.pdf by Alexandros Bakas and Antonis Michalas, just got accepted at SecureComm’19, 23-25 October in Orlando! #SSE #ABE
Something went wrong.
Something went wrong.
United States Trends
- 1. Good Saturday 20.6K posts
- 2. #SaturdayVibes 2,974 posts
- 3. Tottenham 49K posts
- 4. #LingOrm1st_ImpactFANCON 1.6M posts
- 5. LINGORM HER AND HERS FANCON 1.52M posts
- 6. #saturdaymorning 1,670 posts
- 7. Dorgu 4,589 posts
- 8. Manchester United 57.8K posts
- 9. #TOTMUN 3,954 posts
- 10. #KirbyAirRiders 2,046 posts
- 11. Brown Jackson 6,515 posts
- 12. Justice Jackson 6,888 posts
- 13. Collar 17.5K posts
- 14. The Supreme Court 150K posts
- 15. Frankenstein 87.6K posts
- 16. Capitol Police 44.3K posts
- 17. Giulia 16.5K posts
- 18. Heels 31.7K posts
- 19. Lindsey 9,584 posts
- 20. Pluribus 32.2K posts