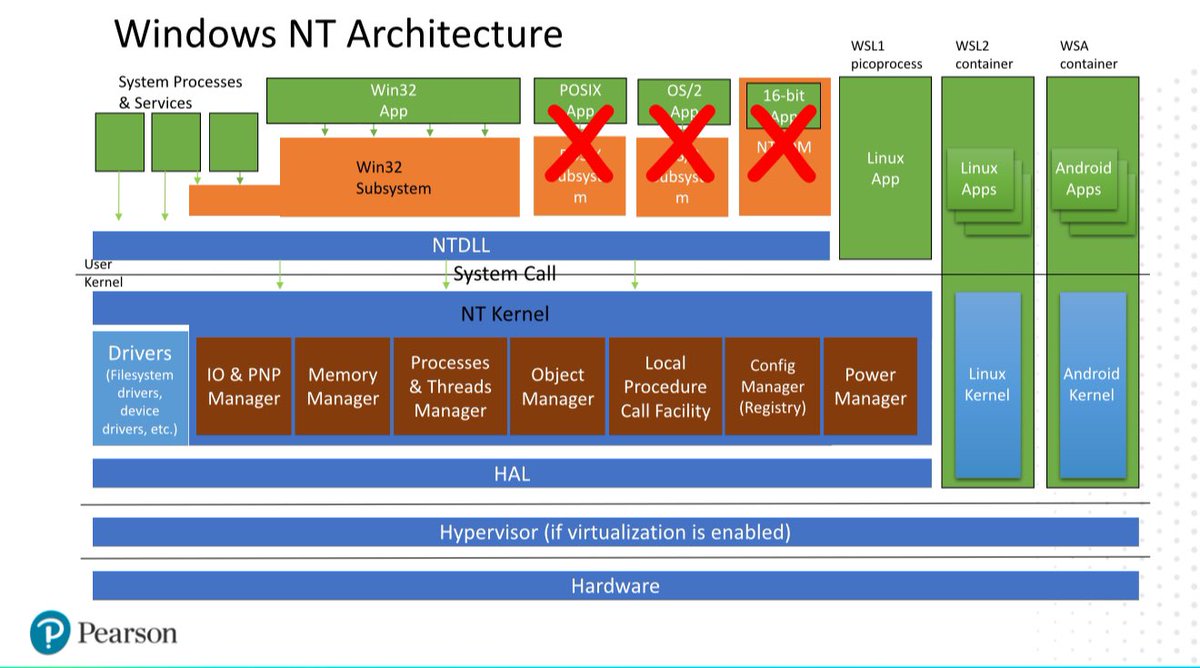
#windowsinternals 검색 결과
Unlock forbidden Windows knowledge! 🤫💻 Find the PEB through truly undetected means and pop calculator 💥 The non-golf form will be available below 👇 #redteamtips #windowsinternals #rust

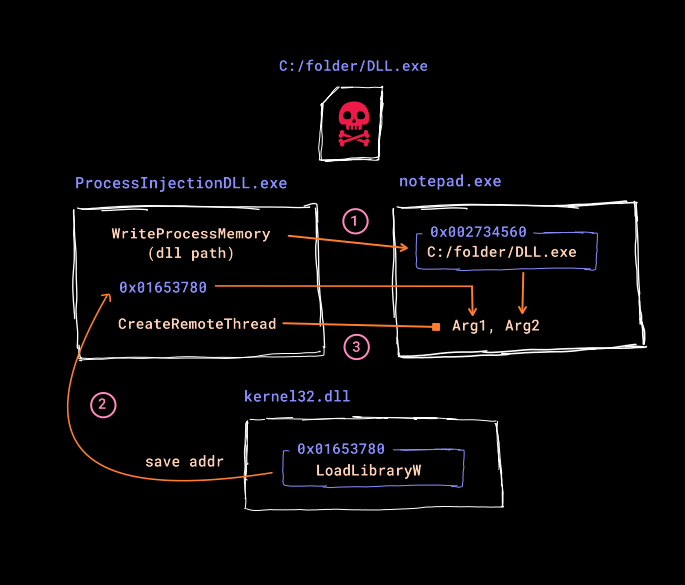
Just published a article on my blog - Malware Development: 🧠 Process Injection - DLL, Shellcode 🔗 Read here: debug-diary.vercel.app/post/Process_I… Also added hand drawn images for better understanding #MalwareDevelopment #WindowsInternals #Cybersecurity

"Contribute to Open Source Software with Me" Bblwrp — pronounced bubble wrap, as in “bubble wrap” or “insulate” your software. Join the fun: github.com/DesignsbyBlanc… #WindowsInternals #IT #Microsoft #opensourcesoftware #softwaredevelopement #programming #cplusplus
Windows memory management is one of the most critical areas of #WindowsInternals!❌ Watch @samilaiho bust some myths around it in this demo from our previous Advanced Windows Security Course 👉 youtube.com/watch?v=CBHYp3… #WindowsSecurity
Check it out and level up your skills: blog.dv08.in/blog/windows-p… one Windows process hack you've used? Drop it in the replies! #WindowsInternals #CyberSecurity #Programming #TechTips (Pro tip: Follow for more deep dives into AI, blockchain, and coding!)

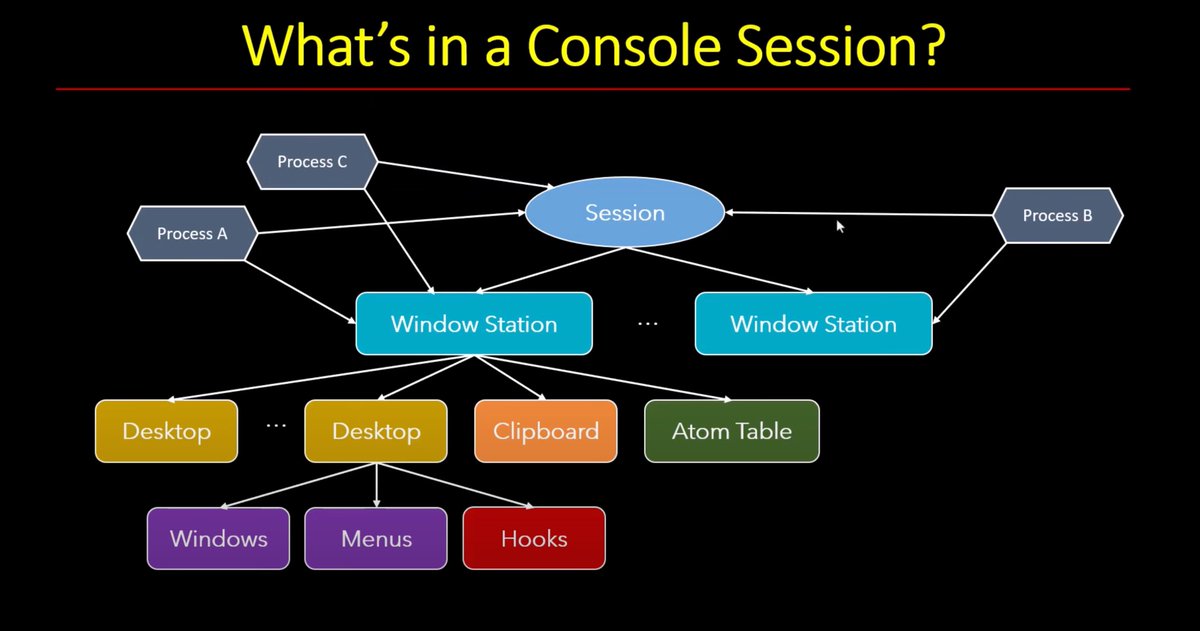
New video: Inside Windows Sessions with @zodiacon. Learn how Windows manages processes, desktops & security inside sessions. trainsec.net/library/window… #WindowsInternals #CyberSecurity #TrainSec
¡No parpadees si no te lo quieres perder! Kurosh Dabbagh nos habla de "Call Stack Spoofing para ocultar la ejecución de implantes desde memoria" #WindowsInternals #Malware #EDR @_Kudaes_

I added the category Windows Programming: github.com/pmatula/Window… #windowsinternals
👀 Think AMSI bypass was wild? Wait until you see what’s in Part 2 🧠 Learn how to defeat: ✅ PowerShell Logging ✅ ETW ✅ SmartScreen ✅ MoTW ✅ C# Reflection ✅ More stealth tricks verylazytech.com/windows/antivi… #AVBypass #RedTeam #WindowsInternals #EDREvasion #OffSec #CyberSecurity

Excited to share that I’ve completed the Windows Internals training! A big thank to @TrainSec @zodiacon and everyone who contributed to this training. Looking forward to applying these insights in real-world scenarios! #WindowsInternals #CyberSecurity #Learning #WinDbg #Malware

Enroll now for our 40-hour live workshop “EDR Internals: R&D,” co-taught with @MalFuzzer. Starts 23 Oct 2025. Dissect & build EDR drivers, master evasion techniques. Early-bird $1,450 ends 30 Sep. Details: trainsec.net/courses/edr-in… #EDR #WindowsInternals
و با نوشتن رول در #سوریکاتا، به شناسایی Signature در ترافیک دانلودی پرداختیم. در نهایت این بخش رو به PE Parser اضافه کردیم. مشاهده در یوتیوب: youtu.be/hr0WQaeNJdU?si… اسلاید و کدها: github.com/onhexgroup/Tut… #ویندوز_اینترنالز #WindowsInternals #redteam #Blueteam #PEParser #Lief

youtube.com
YouTube
قسمت چهارم: NT Headers بخش Signature
3️⃣ 100% CPU but no clear culprit? 🔥 Run !runaway in WinDbg. 👉 Often it’s 1 runaway thread hogging cycles, not “the system.” #Debugging #WindowsInternals
ashishranax.com/posts/Threads,… Understanding Threads, TEB, PEB, TLS, and SEH in Windows - and how they connect with each other. #x86 #ReverseEngineering #WindowsInternals
ashishranax.com
Threads, TEB, PEB, TLS and SEH: Understanding the interconnections
Threads, TEB, PEB, TLS and SEH: Understanding the interconnections
Introduction to the Windows Performance Analyzer by @zodiacon #windowsinternals #windowsperformance #debugging youtube.com/watch?v=Cw4d3p…

youtube.com
YouTube
Introduction to the Windows Performance Analyzer
NTFS Alternate Data Streams (ADS) are a lesser-known feature that let you hide data inside files. Used for stealthy persistence, evasion, or covert storage (for example, to store payloads). Most tools — and users — completely overlook them. #CyberSecurity #DFIR #WindowsInternals

Sometimes I crave learning on my own accord! Do you think that its going to be wasted effort? #WindowsInternals #WindowsAPI #Learning

github.com/DebugPrivilege… is an amazing (free!) resource for learning Windows Internals / Debugging / Troubleshooting. #windowsinternals #debugging
New video: Inside Windows Sessions with @zodiacon. Learn how Windows manages processes, desktops & security inside sessions. trainsec.net/library/window… #WindowsInternals #CyberSecurity #TrainSec

6️⃣ Commit ≠ Working Set. Commit = memory apps asked for. Working Set = what’s in RAM now. High commit doesn’t mean “out of memory.” Check with RamMap. 📊 #WindowsInternals #Memory
3️⃣ 100% CPU but no clear culprit? 🔥 Run !runaway in WinDbg. 👉 Often it’s 1 runaway thread hogging cycles, not “the system.” #Debugging #WindowsInternals
1️⃣ Memory leaks ≠ high RAM usage. Windows caches memory aggressively. 🚀 👉 The real issue is Private Bytes climbing without release. Use PoolMon or WinDbg !vm. #WindowsInternals #Debugging
Just finished a new whitepaper: COMouflage – COM-based DLL Surrogate Injection I tested the technique against three major EDRs: - Microsoft Defender – bypassed - Palo Alto Cortex XDR – bypassed - SentinelOne – bypassed github.com/zero2504/COMou… #malware #COM #windowsinternals
Custom Windows shellcode leverages PEB and TEB structures for stealthy API resolution, dynamic payload control, and detection evasion. Encoding strings as hex keeps payloads self-contained and covert. #WindowsInternals #ShellcodeCraft #USA ift.tt/RukcYeH
و با نوشتن رول در #سوریکاتا، به شناسایی Signature در ترافیک دانلودی پرداختیم. در نهایت این بخش رو به PE Parser اضافه کردیم. مشاهده در یوتیوب: youtu.be/hr0WQaeNJdU?si… اسلاید و کدها: github.com/onhexgroup/Tut… #ویندوز_اینترنالز #WindowsInternals #redteam #Blueteam #PEParser #Lief

youtube.com
YouTube
قسمت چهارم: NT Headers بخش Signature
ashishranax.com/posts/Threads,… Understanding Threads, TEB, PEB, TLS, and SEH in Windows - and how they connect with each other. #x86 #ReverseEngineering #WindowsInternals
ashishranax.com
Threads, TEB, PEB, TLS and SEH: Understanding the interconnections
Threads, TEB, PEB, TLS and SEH: Understanding the interconnections
"Contribute to Open Source Software with Me" Bblwrp — pronounced bubble wrap, as in “bubble wrap” or “insulate” your software. Join the fun: github.com/DesignsbyBlanc… #WindowsInternals #IT #Microsoft #opensourcesoftware #softwaredevelopement #programming #cplusplus
Windows memory management is one of the most critical areas of #WindowsInternals!❌ Watch @samilaiho bust some myths around it in this demo from our previous Advanced Windows Security Course 👉 youtube.com/watch?v=CBHYp3… #WindowsSecurity
Just published a article on my blog - Malware Development: 🧠 Process Injection - DLL, Shellcode 🔗 Read here: debug-diary.vercel.app/post/Process_I… Also added hand drawn images for better understanding #MalwareDevelopment #WindowsInternals #Cybersecurity


Check it out and level up your skills: blog.dv08.in/blog/windows-p… one Windows process hack you've used? Drop it in the replies! #WindowsInternals #CyberSecurity #Programming #TechTips (Pro tip: Follow for more deep dives into AI, blockchain, and coding!)

Day 4 – SOC Analyst Journey with @Level_Effect Hands-on with: 🔹Creating & managing background services 🔹Automating tasks with Task Scheduler Learning how Windows ticks behind the scenes. #SOCAnalyst #CybersecurityLabs #WindowsInternals
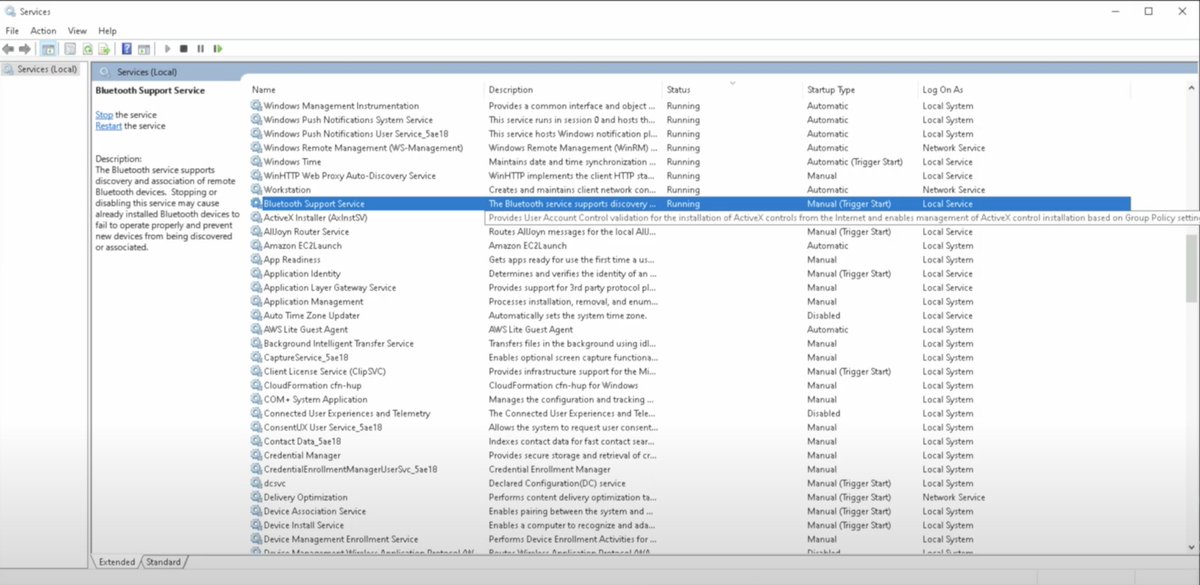

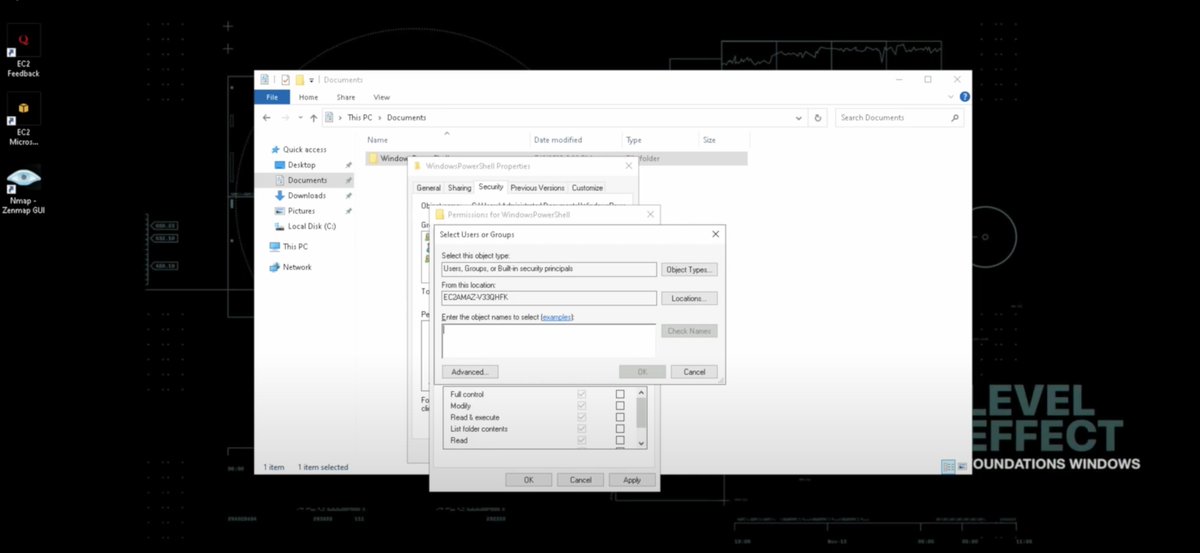
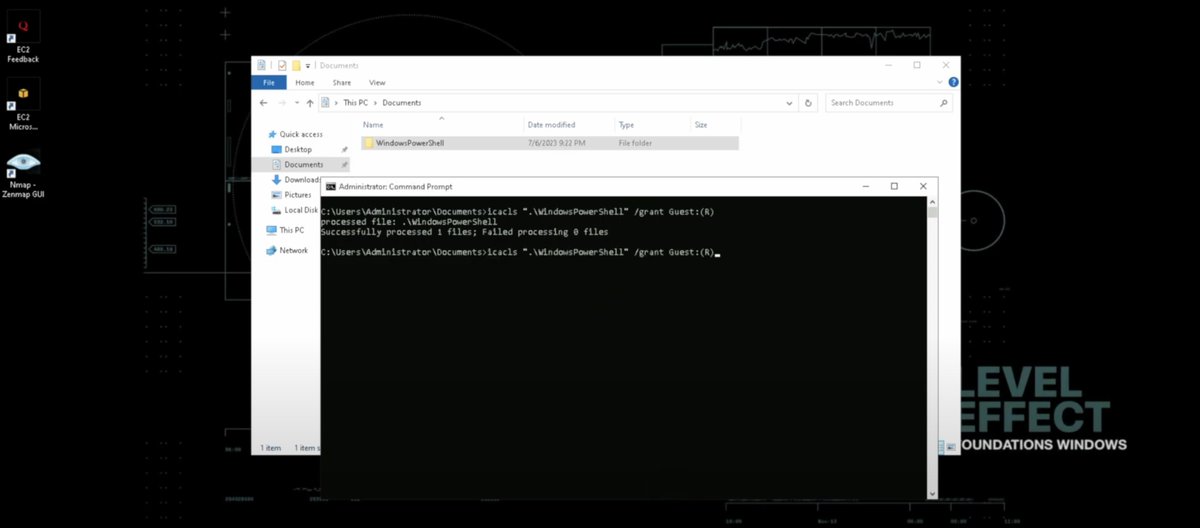
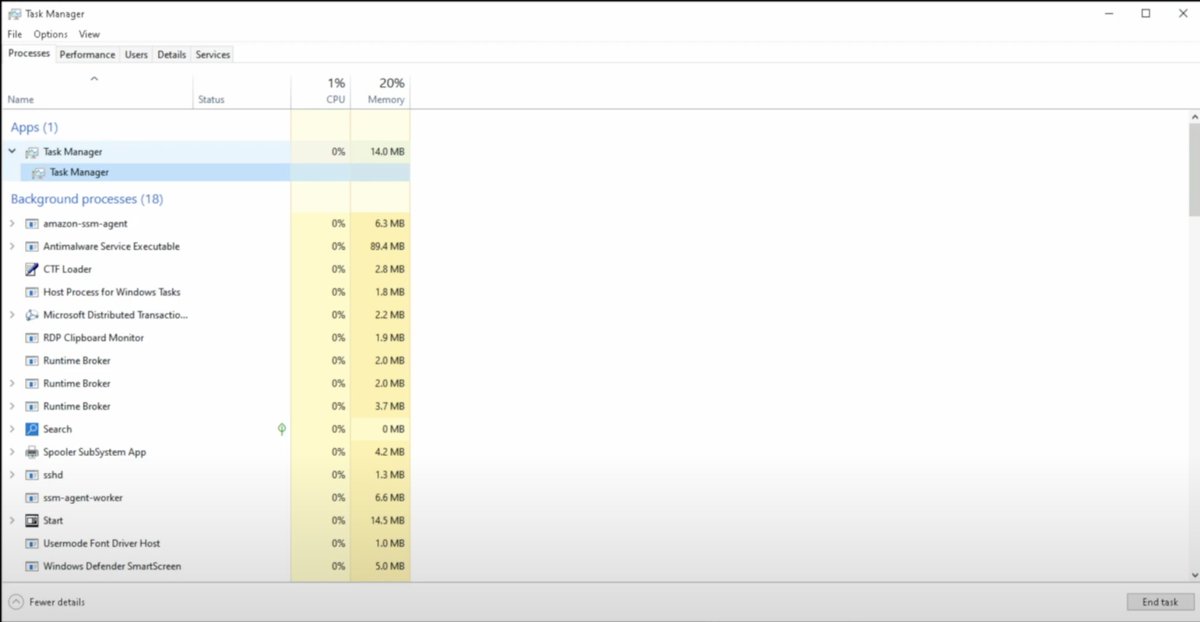
Day 3 – SOC Analyst Journey with @Level_Effect Diving deeper into the system: 🔹Used "icacls" to grant file/folder permissions 🔹Monitored & terminated user processes via Task Manager #SOC100 #BlueTeamSkills #WindowsSecurity
Mastered at @hackerspre30858 : 🛠️ Mimikatz, Rubeus, Impacket 🪟 Windows PrivEsc & AD Attacks ⚔️ C2 frameworks (Sliver, Mythic) 🧠 x86 internals, tokens, tickets Domain Admin in labs ✅ #RedTeam #OffSec #WindowsInternals #PayloadDev #HackersPrey
🎯 Ebyte-ETW-Redirector — Abusing Windows ETW to redirect event streams! 🔁 Hijack ETW providers & route output to custom consumers 🧪 Great for red team stealth, evasion, or detection bypass research 👉 github.com/EvilBytecode/E… #ETW #RedTeam #WindowsInternals
🛠️ TokenUniverse tool showcase: Admin to TrustedInstaller without spawning the service. #WindowsInternals #TokenUniverse github.com/diversenok/Tok…




Unlock forbidden Windows knowledge! 🤫💻 Find the PEB through truly undetected means and pop calculator 💥 The non-golf form will be available below 👇 #redteamtips #windowsinternals #rust

Yet another way of starting the WER Service: use undocumented NtUpdateWnfStateData() with 0x41940b3aa3bc0875 as a parameter. Allowed for anyone. Windows Notification Facility FTW! #wnf #WindowsInternals


New video #WindowsInternals series: "Tracing C function fopen [Part2] - Windbg Kernel Debugging - Walk-Through User-Mode to Kernel Executive Subsytem" and much more... Video: youtu.be/8oaEAPC84gc Walk-Through: git.io/JseF3
![vinopaljiri's tweet image. New video #WindowsInternals series:
"Tracing C function fopen [Part2] - Windbg Kernel Debugging - Walk-Through User-Mode to Kernel Executive Subsytem" and much more...
Video: youtu.be/8oaEAPC84gc
Walk-Through: git.io/JseF3](https://pbs.twimg.com/media/E1GEWb-WYAA79Vy.png)
![vinopaljiri's tweet image. New video #WindowsInternals series:
"Tracing C function fopen [Part2] - Windbg Kernel Debugging - Walk-Through User-Mode to Kernel Executive Subsytem" and much more...
Video: youtu.be/8oaEAPC84gc
Walk-Through: git.io/JseF3](https://pbs.twimg.com/media/E1GEc0dWYAEQFNH.jpg)
![vinopaljiri's tweet image. New video #WindowsInternals series:
"Tracing C function fopen [Part2] - Windbg Kernel Debugging - Walk-Through User-Mode to Kernel Executive Subsytem" and much more...
Video: youtu.be/8oaEAPC84gc
Walk-Through: git.io/JseF3](https://pbs.twimg.com/media/E1GEeNUWUAAxEV2.jpg)
![vinopaljiri's tweet image. New video #WindowsInternals series:
"Tracing C function fopen [Part2] - Windbg Kernel Debugging - Walk-Through User-Mode to Kernel Executive Subsytem" and much more...
Video: youtu.be/8oaEAPC84gc
Walk-Through: git.io/JseF3](https://pbs.twimg.com/media/E1GEfVUWQAA66fy.jpg)
Be a regular user, face "Access Denied" when starting a system service, inject false ETW trigger to make it starting anyway. Fully working PoC for wersvc: github.com/gtworek/PSBits… #WindowsInternals #security

@yarden_shafir “NPIEP is a fun drinking game where you have to say ‘non privileged instruction execution prevention’ and get a shot if you get it right, then try again. RUM is what I wish I had this morning before talking about hypervisor mitigations”. Yep, #WindowsInternals.

Tracing iSCSI on Windows Server 2016/2019 through "Event Trace Sessions" #WindowsInternals #Performance

Reverse Engineering Malware, Part 4: Windows Internals #windowsinternals #reversing #dfir #malware #infosec #cyberwarrior bit.ly/3rXXYD3

Something went wrong.
Something went wrong.
United States Trends
- 1. Baker 26.1K posts
- 2. Cowboys 71.4K posts
- 3. Fred Warner 9,862 posts
- 4. Panthers 72.4K posts
- 5. Packers 26.1K posts
- 6. Tez Johnson 2,053 posts
- 7. Zac Taylor 2,709 posts
- 8. Niners 4,582 posts
- 9. Browns 63.7K posts
- 10. Titans 21.8K posts
- 11. #FTTB 3,763 posts
- 12. Yoshi 32.7K posts
- 13. Ravens 63.8K posts
- 14. Dolphins 46.3K posts
- 15. #49ers 5,833 posts
- 16. Cam Ward 2,079 posts
- 17. #KeepPounding 8,100 posts
- 18. Eberflus 9,840 posts
- 19. Penn State 63.3K posts
- 20. #Bengals 2,658 posts