#detectionascode نتائج البحث
Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…
Check out our latest post on #DetectionEngineering: Practicing #DetectionAsCode
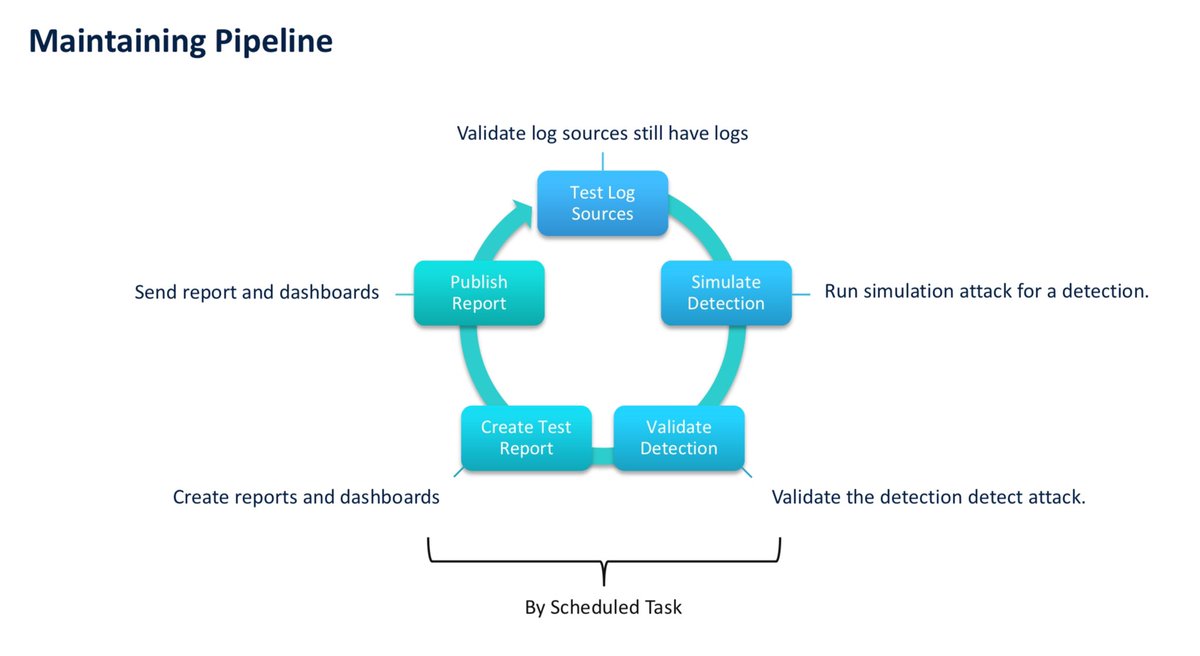
@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉 blog.nviso.eu/2025/10/07/det…

great Friday feeling when all your detections finally pass automated CI/CD testing cc @M_haggis #detectionAsCode

🚀 Get ready, Toronto! Just one more week ‘til #AWSSummitToronto! Come chat with us at booth #425 and we’ll show you exactly why Panther is the SIEM for code-driven SecOps at cloud scale. #DetectionAsCode #SecurityEngineering #DetectionEngineering

#Cybersecurity is on the move! 🚀 Amine Besson chats #detectionascode, response engineering, and the future of fusion centers on this episode of the @CloudSecPodcast. Listen now → bit.ly/4gJSK6i

I guess all DE teams are validating their new detections. What about prior detections? Building a pipeline may be good idea for be able to sleep well. #detectionengineering #detectionascode #siem
🚒 Too much firefighting, not enough foresight? #DetectionAsCode (DaC) to the rescue! 🧯 Join the 63% of pros who see fewer incidents. Learn how in our State of Security 2025 report: 🔗[splk.it/4kfjY6I] #SplunkSecurity
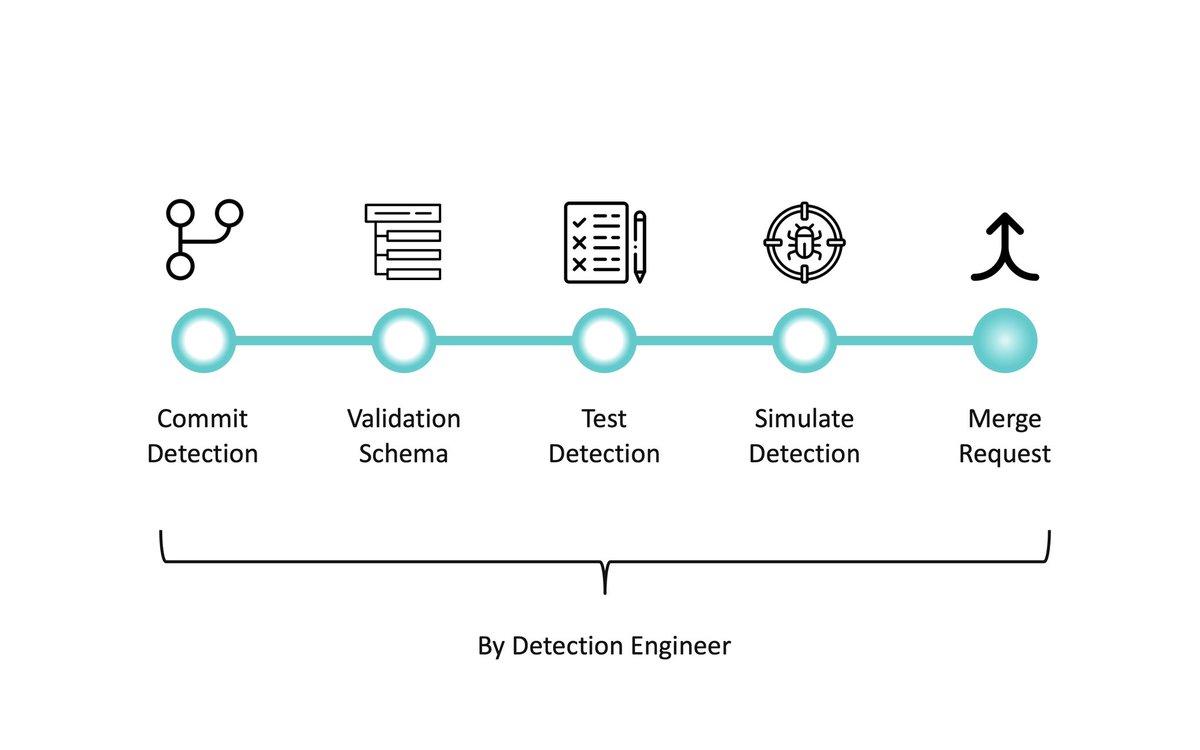
Check out my latest blog post of the series #DetectionEngineering: Practicing #DetectionAsCode for @NVISO_Labs. In this part we are exploring Continuous Delivery pipelines to deploy our detections to the target platform.
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

Discover insights from David French on detection as code in the latest episode of Simply Defensive. Explore his journey, professional growth, and the vital role of coding in cybersecurity. 💻🔍 #DetectionAsCode #TechUSA #CyberInsights link: ift.tt/gok7uWA

🚀 Boost Your Security Skills! 🚀 Join our webinar to learn the fundamentals of Detection-as-Code and manage detection rules with Google SecOps’ REST API and CI/CD tools. Live Q&A included! 📅 Register now: bit.ly/4ax3Gka #GoogleSecOps #DetectionAsCode #Webinar

Panther raises $120 million at $1.4 billion valuation! 👏 Our Series B will power accelerated growth with cloud-first security teams to make detection and response fast, flexible and scalable. Learn more⬇️ runpanther.io/press-releases… #DetectionasCode

Check out my latest blog for the series #DetectionEngineering - Practicing #DetectionAsCode In this part we are looking into ways of automating documentation and the generation of a change log to track updates in the repository! Coming up next is applying versioning schemas!
Documentation is key in #DetectionEngineering! Automate it with Jinja & Git for streamlined processes. Plus, generate changelogs to keep teams informed and improve collaboration. Discover more in @_st0pp3r_ latest blogpost 👉 blog.nviso.eu/2025/08/26/det…

Rely on Threat Detection Marketplace to create your custom repositories for #detectionascode projects smartly linked to ATT&CK. Store and manage your #detection code in a secure environment to boost the use case management lifecycle. Learn more: my.socprime.com/threat-detecti…

Part 5 of the #DetectionEngineering #DetectionAsCode series is now available: blog.nviso.eu/2025/09/09/det… In this part we are exploring versioning schemes for the content packs and detections in the repository.
Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/3Sl0fGB #DetectionAsCode #Cybersecurity #ThreatDetection #DevSecOps #AutomatedSecurity #CyberDefense #CloudSecurity #CyberThreats #AttackSolutions

Operationalizing threat intelligence is key to advancing detection beyond short-lived IOCs. Frameworks like Pyramid of Pain and DML elevate response capabilities, as shown in Sandworm’s 2022 Ukraine attack. #PyramidOfPain #DetectionAsCode #Ukraine ift.tt/j1oJYa5
hendryadrian.com
Intelligence-Driven Detection Engineering: From Threat Intel to Detection-as-Code (with the...
This article emphasizes the importance of operationalizing threat intelligence to enhance detection and response capabilities in cybersecurity. It highlights frameworks like the Pyramid of Pain and...
Why Detection-As-Code (DAC) Is the Future of #ThreatDetection buff.ly/3iUUoXG #detectionascode #DAC #cybersecurity

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Check out our latest post on #DetectionEngineering: Practicing #DetectionAsCode
@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉 blog.nviso.eu/2025/10/07/det…

Check out my latest blog post of the series #DetectionEngineering: Practicing #DetectionAsCode for @NVISO_Labs. In this part we are exploring Continuous Delivery pipelines to deploy our detections to the target platform.
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

Operationalizing threat intelligence is key to advancing detection beyond short-lived IOCs. Frameworks like Pyramid of Pain and DML elevate response capabilities, as shown in Sandworm’s 2022 Ukraine attack. #PyramidOfPain #DetectionAsCode #Ukraine ift.tt/j1oJYa5
hendryadrian.com
Intelligence-Driven Detection Engineering: From Threat Intel to Detection-as-Code (with the...
This article emphasizes the importance of operationalizing threat intelligence to enhance detection and response capabilities in cybersecurity. It highlights frameworks like the Pyramid of Pain and...
Part 5 of the #DetectionEngineering #DetectionAsCode series is now available: blog.nviso.eu/2025/09/09/det… In this part we are exploring versioning schemes for the content packs and detections in the repository.
Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

Check out my latest blog for the series #DetectionEngineering - Practicing #DetectionAsCode In this part we are looking into ways of automating documentation and the generation of a change log to track updates in the repository! Coming up next is applying versioning schemas!
Documentation is key in #DetectionEngineering! Automate it with Jinja & Git for streamlined processes. Plus, generate changelogs to keep teams informed and improve collaboration. Discover more in @_st0pp3r_ latest blogpost 👉 blog.nviso.eu/2025/08/26/det…

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Check out part 2 of our #DetectionEngineering - Practicing #DetectionAsCode series is out! This part is all about laying the groundwork for a scalable and efficient detection repository.
Looking to elevate your #ThreatDetection strategy? 👀 Learn how to design repositories for detection-as-code with tips on branch strategy, repo organization & more. Part 2 of @_st0pp3r_‘s blog post series on #DetectionEngineering is live! 👇 blog.nviso.eu/2025/07/17/det…

Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…

#DetectionAsCode (DaC) can bolster the speed, accuracy, & scalability of your threat detection. Here are 5 essential steps #cybersecurity teams can use to get started.👇 bit.ly/4dM32CC
reversinglabs.com
Detection as code: How to enhance your real-time threat detection | ReversingLabs
DaC can bolster the speed, accuracy, and scalability of your threat detection. Here are five essential steps to getting started.
🚒 Too much firefighting, not enough foresight? #DetectionAsCode (DaC) to the rescue! 🧯 Join the 63% of pros who see fewer incidents. Learn how in our State of Security 2025 report: 🔗[splk.it/4kfjY6I] #SplunkSecurity
Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/3Sl0fGB #DetectionAsCode #Cybersecurity #ThreatDetection #DevSecOps #AutomatedSecurity #CyberDefense #CloudSecurity #CyberThreats #AttackSolutions

Discover insights from David French on detection as code in the latest episode of Simply Defensive. Explore his journey, professional growth, and the vital role of coding in cybersecurity. 💻🔍 #DetectionAsCode #TechUSA #CyberInsights link: ift.tt/gok7uWA

The best SOCs don’t chase every alert. They focus on the right ones. Detection-as-Code enables teams to refine detections, automate tuning, and adapt in real-time. Better alerts = faster triage, smarter decisions, and stronger security. #CyberSecurity #SOC #DetectionAsCode

#Cybersecurity is on the move! 🚀 Amine Besson chats #detectionascode, response engineering, and the future of fusion centers on this episode of the @CloudSecPodcast. Listen now → bit.ly/4gJSK6i

Is “Detection as Code” the next logical step for security operations? @anton_chuvakin explores the implications for improving SOC efficiency. What do you think? Read More: tinyurl.com/3w5yp6vp #DetectionAsCode #SecurityOperations

What it looks like when you and your homie get hyped on #DetectionAsCode! 📣Today we're announcing our integration with @sublime_sec! 🎉 Now you can correlate your Sublime email telemetry in Panther for centralized threat detection. Read all about it 👉 bit.ly/3BnJnK1
🚨Today’s the day, Toronto!! Visit at booth #425 to talk about code-driven SecOps at cloud scale. Snag a 🎶 Views from the SOC 🎶 #Detectapalooza shirt by being the first 5 to schedule a sales call. #AWSSummitToronto #DetectionAsCode #SecurityEngineering #DetectionEngineering

How’s the view from your SOC, Toronto?? 👀 Visit booth #425 to talk cloud SecOps at #AWSSummitToronto. We’re giving away the finest #Detectapalooza swag to a few lucky 🍀 folks who sign up for a chat with our sales team. #DetectionAsCode #SecurityEngineering…

#Cybersecurity is on the move! 🚀 Amine Besson chats #detectionascode, response engineering, and the future of fusion centers on this episode of the @CloudSecPodcast. Listen now → bit.ly/4gJSK6i

🚀 Get ready, Toronto! Just one more week ‘til #AWSSummitToronto! Come chat with us at booth #425 and we’ll show you exactly why Panther is the SIEM for code-driven SecOps at cloud scale. #DetectionAsCode #SecurityEngineering #DetectionEngineering

great Friday feeling when all your detections finally pass automated CI/CD testing cc @M_haggis #detectionAsCode

Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…

Let's kick off this Tuesday with @_st0pp3r_ new blog series on the critical role of versioning in #DetectionEngineering, particularly within #DetectionAsCode. 👉blog.nviso.eu/2025/09/09/det… You'll learn to implement robust versioning strategies for better traceability and more!

🚀 Boost Your Security Skills! 🚀 Join our webinar to learn the fundamentals of Detection-as-Code and manage detection rules with Google SecOps’ REST API and CI/CD tools. Live Q&A included! 📅 Register now: bit.ly/4ax3Gka #GoogleSecOps #DetectionAsCode #Webinar

🚨Today’s the day, Toronto!! Visit at booth #425 to talk about code-driven SecOps at cloud scale. Snag a 🎶 Views from the SOC 🎶 #Detectapalooza shirt by being the first 5 to schedule a sales call. #AWSSummitToronto #DetectionAsCode #SecurityEngineering #DetectionEngineering

How’s the view from your SOC, Toronto?? 👀 Visit booth #425 to talk cloud SecOps at #AWSSummitToronto. We’re giving away the finest #Detectapalooza swag to a few lucky 🍀 folks who sign up for a chat with our sales team. #DetectionAsCode #SecurityEngineering…

Rely on Threat Detection Marketplace to create your custom repositories for #detectionascode projects smartly linked to ATT&CK. Store and manage your #detection code in a secure environment to boost the use case management lifecycle. Learn more: my.socprime.com/threat-detecti…

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Is “Detection as Code” the next logical step for security operations? @anton_chuvakin explores the implications for improving SOC efficiency. What do you think? Read More: tinyurl.com/3w5yp6vp #DetectionAsCode #SecurityOperations

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/3Sl0fGB #DetectionAsCode #Cybersecurity #ThreatDetection #DevSecOps #AutomatedSecurity #CyberDefense #CloudSecurity #CyberThreats #AttackSolutions

Panther raises $120 million at $1.4 billion valuation! 👏 Our Series B will power accelerated growth with cloud-first security teams to make detection and response fast, flexible and scalable. Learn more⬇️ runpanther.io/press-releases… #DetectionasCode

Discover insights from David French on detection as code in the latest episode of Simply Defensive. Explore his journey, professional growth, and the vital role of coding in cybersecurity. 💻🔍 #DetectionAsCode #TechUSA #CyberInsights link: ift.tt/gok7uWA

The best SOCs don’t chase every alert. They focus on the right ones. Detection-as-Code enables teams to refine detections, automate tuning, and adapt in real-time. Better alerts = faster triage, smarter decisions, and stronger security. #CyberSecurity #SOC #DetectionAsCode

I guess all DE teams are validating their new detections. What about prior detections? Building a pipeline may be good idea for be able to sleep well. #detectionengineering #detectionascode #siem

Why Detection-As-Code (DAC) Is the Future of #ThreatDetection buff.ly/3iUUoXG #detectionascode #DAC #cybersecurity

.@SnowflakeDB Ventures Invests in @runpanther_ to Add #DetectionAsCode to the #DataCloud buff.ly/3xTmqbD #CyberSecurity #TheDataCloud

Something went wrong.
Something went wrong.
United States Trends
- 1. SNAP 1M posts
- 2. Jamaica 230K posts
- 3. $NVDA 83.2K posts
- 4. Don Lemon 2,797 posts
- 5. Nelson 28.4K posts
- 6. New Hope 34.4K posts
- 7. Tucker 95K posts
- 8. Hurricane Melissa 169K posts
- 9. Jensen 9,727 posts
- 10. #NationalFirstRespondersDay 1,269 posts
- 11. Nokia 13.8K posts
- 12. Chris Evans 8,569 posts
- 13. Nvidia 36.4K posts
- 14. Wikipedia 111K posts
- 15. Western Union 4,639 posts
- 16. Fuentes 75.4K posts
- 17. Grokipedia 173K posts
- 18. Rattler 3,838 posts
- 19. Riley Gaines 103K posts
- 20. Shough 2,996 posts