#exploitable hasil pencarian

The second blogpost of our #Pwn2Own exploitation series is out, and this week we're sharing some tips on the deconstruction of complex software (@webkit) to find #exploitable security vulnerabilities: blog.ret2.io/2018/06/13/pwn…

#Security truism: “not all #vulnerabilities are #exploitable” schneier.com/blog/archives/… #M1racles m1racles.com


💡Learn concepts, tools & techniques required to ⏪ #reverseengineer #firmware 💻Using Ghidra, Eric @ericevenchick will teach you techniques to find #exploitable #vulnerabilities in #embedded Linux devices ✅Get your seat➡️bit.ly/32SBc7e #hw_ioUSA2022

Tip #4: Obfuscate Objective-C calls Messages called in Objective-C are resolved at run time. Stored plainly in the #code, they are easily #exploitable. #Obfuscate plain text message calls to protect Objective-C code. Come back tomorrow for Tip #5. okt.to/J9oYqU

⭐️#H2020 @SEAFOOD_TMRW Key Achievements Booklet is OUT NOW! ⭐️ This interactive booklet showcases key #outputs, #exploitable #results, and #eco-#innovative #solutions for the #seafood sector! 👏 Available now at➡️ bit.ly/3tUHfAR

Cisco #vulnerable again; May lead to arbitrary code execution! The vulnerabilities that were quite #exploitable were found in the Cisco Discovery Protocol (CDP). ehackingnews.com/2020/03/cisco-…

"Les ressources humaines" terme catastrophique qui signifie que l'#humain est devenu matière première #exploitable.
🎈Our #Exploitation Manager from @SustainableInnE conducted an online #workshop last week to discuss the project’s key #exploitable results and potential #revenue models to keep the @BIOSWITCH_eu toolbox alive after the project’s completion! #BBIImpact #biobased #bioeconomy

🙌SUSFERT at joint 🇦🇹Ministry of #Climate & @CBE_JU event: 🌳Wood-based gels are presented in 📽️ with ➡️ #key #exploitable #results ➡️ #impacts for #agriculture ☝️Reaching for #fertilisers & #soil improvers that circumvent finite #phosphate #resources 👇 bit.ly/41hsSb2

WARNING Widely #exploitable #vulnerability tagged as Unauthenticated Full-Read SSRF (CWE-918) in #Grafana (CVE-2020-13379). Get our feed to boost your solutions with top notch vulnerability intelligence as a service indicators (patches, signatures, rules, open standards ...)



Tool to search #exploitable binaries/exe on #windows and linux github.com/mzfr/gtfo
#Autonomouspentesting can serve as your sparring partner 👊💥 helping you focus on fixing 💪#exploitable #vulnerabilities. Join @snehalantani Feb 9 @ 6:10 am ET for his talk on #EffectiveSecurity: Proactively Verifying Your #Security Posture. Register! hubs.ly/Q0133Qy10

I did the thing #meme #exploitable #coco #MLP and here it is without compression i.imgur.com/xcDR2Jg.png

#security Issues in #Python are not necessarily directly #exploitable , but detected security issues are a fertile ground for #vulnerabilities to appear. So use python #code #audit nocomplexity.com/codeaudit/ #malware #infosec #owasp #malware #cyber

In #canada you need to be #exploitable not just have #employable skills and u need to be unionized @UFCW

Someone within @lyft and @AskLyft #canada @UFCW loosing it 🤷🤷🤷 After like three years of driving for @lyft they are like rehiring me 😁😁😁😁😁 They are telling me welcome aboard and make ready phone and phone mount What have the @liberal_party & @JustinTrudeau get us in

Les empires numériques modèlent désirs et divisions, réduisant l’humain à un profil #exploitable.
Not Every #CVE Deserves a Fire Drill: #Focus on What’s #Exploitable scyscan.com/news/not-every…
scyscan.com
Not Every CVE Deserves a Fire Drill: Focus on What’s Exploitable | ScyScan
Not every "critical" vulnerability is a critical risk. Picus Exposure Validation cuts through the noise by testing what's actually exploitable in your enviro...
But isn't that the neverending goal? Management styles for different levels of population. I don't think we have a model to handle this amount of people before. Maybe that's the reason for the depopulation agenda? & Why tribalism is again emerging? #Exploitable #Vulnerable
🚨 #ICYMI: #Exploitable #Flaws: What #US #Adversaries *COULD LEARN FROM* #WhiteHouse #Security #Failure‼️"Hostile intelligence agencies are likely to pore over details revealed in chat group planning for Yemen strikes." By Peter Beaumont theguardian.com/us-news/2025/m…
theguardian.com
Exploitable flaws: what US adversaries could learn from White House security failure
Hostile intelligence agencies are likely to pore over details revealed in chat group planning for Yemen strikes
I’ve never looked at a solver once but I might study tape on Insane Shane’s table talk #exploitable
📷 ✨NexusForum.EU #NexusForum2024 Summit 🇪🇺 🌻 ACCC AC3 representative from Arsys - Sara Madariaga joined the EUCloudEdgeIoT community- "Pitch Your #tech session! ⭐️ Sara Madariaga from Arsys, presented the #exploitable; #results; and #innovation from @ACCC_AC3






The second blogpost of our #Pwn2Own exploitation series is out, and this week we're sharing some tips on the deconstruction of complex software (@webkit) to find #exploitable security vulnerabilities: blog.ret2.io/2018/06/13/pwn…

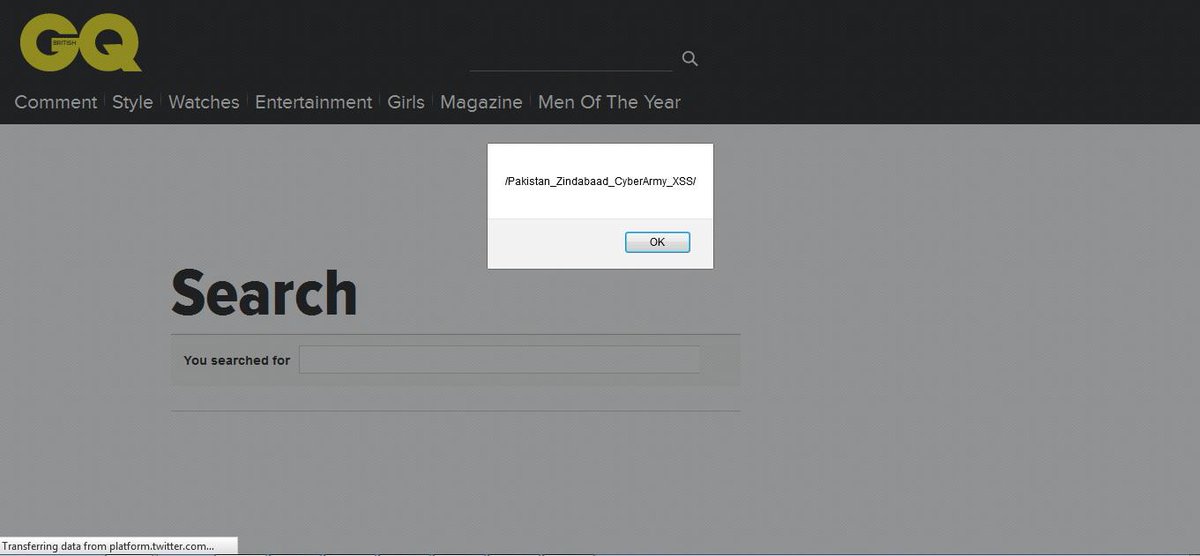
#Vulnerability found gq-magazine.co.uk #Ethicalhacking #exploitable #hack #Infosec #PakistanZindabad #xss
#Exploitable. If you know who this is & hate him, mockery is still permitted. If you like Milo, then mock anyway.

#OpenVPN fixed many remotely #exploitable #flaws that were not detected by recent audits #CyberAttack #CyberSecurity goo.gl/4YQpcq

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 68.1K posts
- 2. Cowboys 68.1K posts
- 3. LeBron 88.3K posts
- 4. Gibbs 17.6K posts
- 5. Pickens 12.2K posts
- 6. Brandon Aubrey 6,755 posts
- 7. #OnePride 9,492 posts
- 8. Ferguson 10.3K posts
- 9. #DALvsDET 5,980 posts
- 10. CeeDee 9,848 posts
- 11. Goff 8,150 posts
- 12. Eberflus 2,090 posts
- 13. Bland 8,292 posts
- 14. DJ Reed N/A
- 15. Shang Tsung 16.9K posts
- 16. Al Michaels N/A
- 17. Schotty 1,669 posts
- 18. Austin Reaves 13.3K posts
- 19. Turpin 2,111 posts
- 20. #LakeShow 4,355 posts