#infrastructurevulnerabilities результаты поиска
The Internet's Vulnerabilities Are Built Into Its Infrastructure | SIGNAL Magazine #infrastructurevulnerabilities #CyberSecurity afcea.org/content/intern…
A state of emergency has been declared in Spain and Portugal due to a rare atmospheric phenomenon, causing widespread power outages. The Portuguese grid operator warns that full electricity restoration may take up to a week. #InfrastructureVulnerabilities Evening Standard -…
60% of data breaches involve unpatched software!🤯 Our latest blog looks at the top 5 #infrastructurevulnerabilities that all #CISOs & IT leaders need to watch out for. Read on ➡️ lnkd.in/dQA-MnPY DM us to schedule an infrastructure pen test.🛡️ #cybersecurity #infosec

OT systems controlling critical infrastructure are vulnerable to cyber risks due to weak passwords, shared accounts, and remote access. Strong password policies and layered security enhance OT defense. #OTSecurity #PasswordStrength #IndustrialControl ift.tt/K578Ssl
When a critical vulnerability surfaces in these systems, the consequences extend far beyond a single compromised server. govinfosecurity.com/blogs/when-erp…
Very important work. The cyberspace has been rather vulnerable lately and much of modern infra can be accessed (and sabotaged) through networks if you have time and skill.
Nation-state actors are actively targeting U.S. critical infrastructure, including communications, energy, and water sectors, with pre-positioned cyber exploitation capabilities. These attacks aim to disrupt essential services and potentially cause significant financial and…
🛡️We added OpenPLC ScadaBR vulnerability CVE-2021-26828 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

The internet's backbone is more fragile than we'd like to admit. One major hack could cripple everything from hospitals to defense systems. We've built a house of cards and called it infrastructure. Time for serious diversification before it's too late.
🛡️ We added Android framework vulnerabilities CVE-2025-48572 & CVE-2025-48633 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec

When energy, compute, and capital all route through the same infrastructure, any disruption—cyberattack, policy shock, grid failure, or model exploit—propagates everywhere at once. Correlated failure becomes the default, not the exception.
Neglected digital infrastructure is a massive, often ignored security vulnerability. Enterprises need to adopt a stronger and more proactive approach to cloud governance and infrastructure management to avoid falling victim. infoworld.com/article/381901…
📢 Stay informed on the latest vulnerabilities with @CISAgov's Vulnerability Bulletin & gain valuable insights into emerging threats. 💡Check out the latest updates: go.dhs.gov/i7H #Cybersecurity #InfoSec #VulnerabilityManagement

❗ Why Resilient #DigitalInfrastructure Is No Longer Optional In July '24, a faulty cybersecurity update disrupted banks, airlines, hospitals, and major media worldwide — one of the largest tech outages in recent memory. 🌐 Even trusted security tools can fail without…

🛡️ The vulnerability uses the privileges of the web server process, which could lead to full device compromise. Key details include:
Threat actors are actively exploiting vulnerability (CVE-2021-26829), a cross-site scripting vulnerability in OpenPLC ScadaBR, to deface HMIs and disable security features, exposing industrial control systems to potential disruption and unauthorized access. Organizations must…
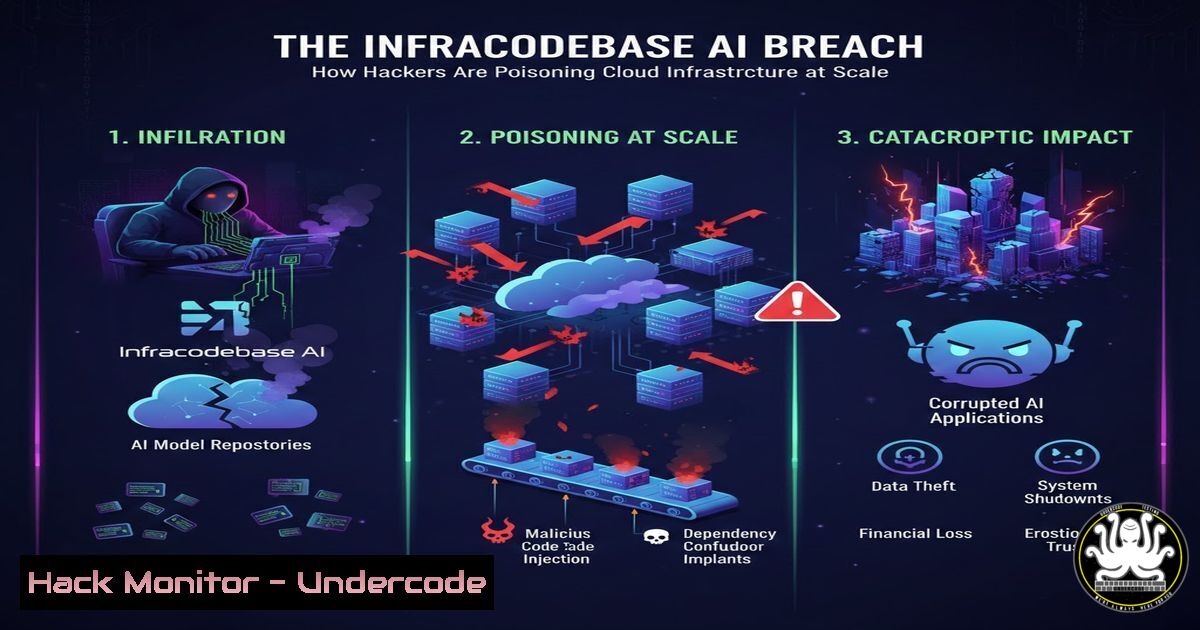
🚨 The Infracodebase #AI Breach: How Hackers Are Poisoning Cloud Infrastructure at Scale undercodetesting.com/the-infracodeb… Educational Purposes!
5/7 5️⃣ Domestic Vulnerabilities Grid stress, supply chain fragility, and service gaps all surfaced again. It only takes one storm, outage, or disruption to cascade. You counter that by tightening your own circle: Backups, food, comms, fuel, and a clear plan for when the lights…
🌉🔐 Rethinking Cross‑Chain Security STON.fi Eliminating Traditional Bridge Risks Thread 👇 🧵 1/ Most bridges introduce new attack surfaces. Complex infrastructure, multi‑sig custodians, and liquidity pools often become the prime targets for exploits.

Much of this vulnerability stems from brittle post-trade infrastructure: unsecured exposures between execution and settlement, slow collateral movements, and limited portability across venues all undermine market resilience.
Ransomware attacks targeting critical infrastructure are rising. Patch vulnerabilities ASAP! #cybersecurity #ransomware
60% of data breaches involve unpatched software!🤯 Our latest blog looks at the top 5 #infrastructurevulnerabilities that all #CISOs & IT leaders need to watch out for. Read on ➡️ lnkd.in/dQA-MnPY DM us to schedule an infrastructure pen test.🛡️ #cybersecurity #infosec

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 70K posts
- 2. LeBron 92.8K posts
- 3. Gibbs 18.6K posts
- 4. Lions 86K posts
- 5. Pickens 12.9K posts
- 6. Brandon Aubrey 6,947 posts
- 7. #OnePride 9,871 posts
- 8. Ferguson 10.4K posts
- 9. #DALvsDET 6,076 posts
- 10. Eberflus 2,372 posts
- 11. Goff 8,328 posts
- 12. CeeDee 10.1K posts
- 13. Bland 8,377 posts
- 14. Shang Tsung 19.9K posts
- 15. DJ Reed N/A
- 16. Al Michaels N/A
- 17. Schotty 1,782 posts
- 18. Austin Reaves 14.4K posts
- 19. scott hunter 2,552 posts
- 20. Turpin 2,190 posts

![triplenickel's profile picture. IT Child, Photographer, Engineer Hacker, Mobile Web Pioneer, Music Lover/Sharer, Collector of Skills, Ibiza Soul, E30 touring! (OO=[][]=OO)](https://pbs.twimg.com/profile_images/1067526653/JohnBelushi1941.jpg)