#secureconfiguration search results
@Knownymous1's talk started! Let's learn how to be more secure with a Zero Trust security model 🤓 @FOSSUnitedDelhi #DelhiFoss #securecoding #secureconfiguration



We collaborated with @LankaPay to implement @CyberArk Privileged Access Management. Our specialists conducted a hands-on session showcasing #secureconfiguration and deployment best practices. This initiative is a key step in strengthening LankaPay’s #cybersecurity posture.




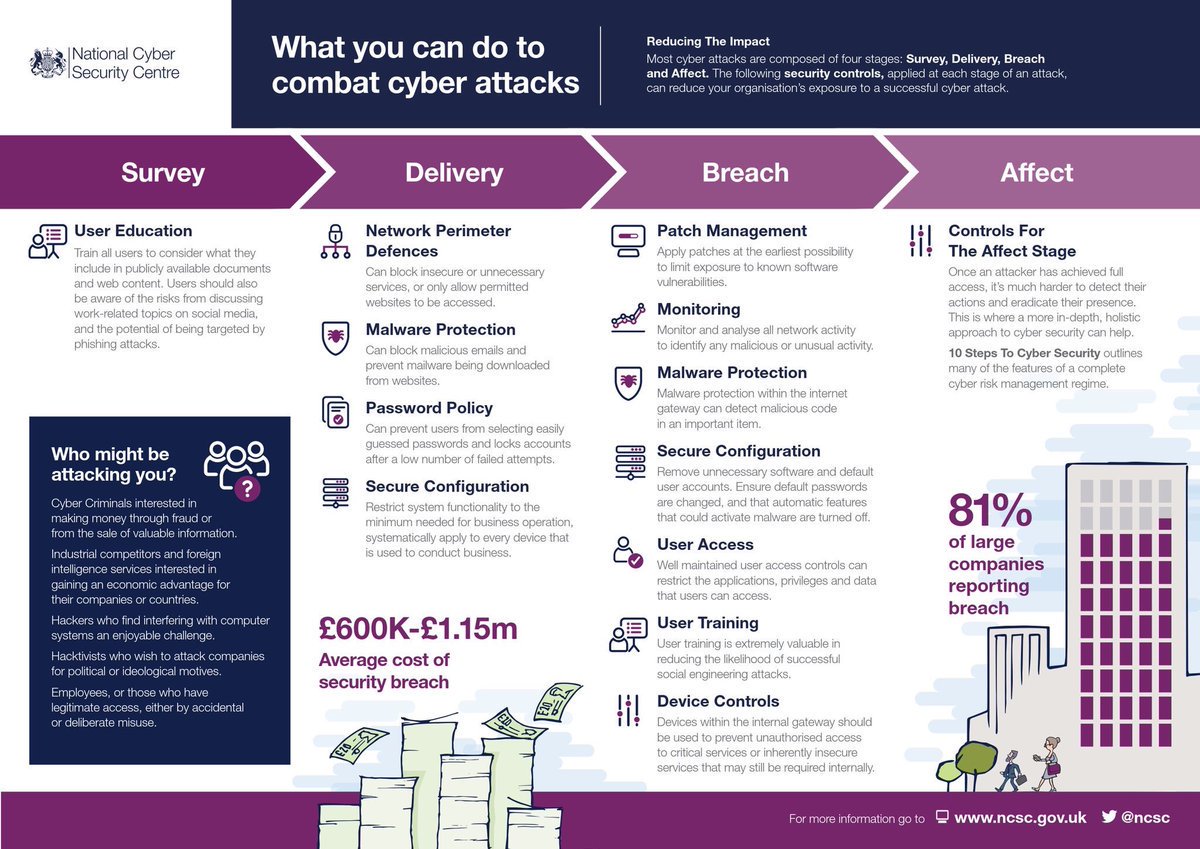
@ncsc advice says #SecureConfiguration helps combat cyber attack. Thats line by line build reviews of your Firewalls, Switch & Router configs (hours of work). Or use #NipperStudio - risk results in seconds, mitigation advice and command line fixes. 😉 titania.com/nipper-studio

Don't forget to send in a picture of your jigsaws...here is phase 5 #SecureConfiguration #ReduceYourAtatckSurface @TripwireInc

#SecureConfiguration systems help keep your data safe #ReduceYourAttackSurface #ITSecurityJigsaw @TripwireInc

Looking to protect your data and cash? 🔐 💸 Here's some guidance from @ncsc & if you need help with #SecureConfiguration (automation & compliance) then try titania.com
CAN/CIOSC 104:2021 Tip #4: Ensure secure configuration by changing default passwords, disabling unnecessary features, and enabling relevant security settings. Protect your devices and data! #CyberSecurity #SecureConfiguration #CIOSC104

4/9 By June 2025, federal agencies must implement SCuBA baselines for @Microsoft Office 365. 📜🔐 #Microsoft365Security #SecureConfiguration
It can also be used to assess your posture so I would say #SecureConfiguration #PurpleTeaming as well
The common gap criminal hackers look to exploit are insecure security configurations. Time to Invest early in establishing a #secureconfiguration and maintain security configuration standards on all your hardware and software. Click here to learn more: mailchi.mp/30c830e0163b/c…

Ensure your #networksecurity with our #secureconfiguration review services. Our experts assess your IT components' security settings based on global industry standards, policies,& regulations. To know more about our services, click here - secureyes.net/review/

Hey, @ManUKHour , did you see our blog about #secureconfiguration? If not, read it here:ow.ly/D6SD50i0xlx #ukmfg #ukmanufacturinghour

Secure configuration management plays a crucial role in cloud security by ensuring that systems are properly configured to defend against cyber threats. Learn how this best practice strengthens your cloud defenses. #CloudSecurity #SecureConfiguration
The UK government’s Cyber Essentials Scheme provides a set of five controls that organisations can implement to achieve a baseline of cyber security... #securitycontrols #secureconfiguration buff.ly/3escEnI
20 #CriticalSecurityControls: #Control11 – #SecureConfiguration for #NetworkDevices, such as #Firewalls, #Routers, and #Switches lnkd.in/dWAVvm2 ht.ly/Tw1W30jlSk9
Our Secure Configuration for Hardware and Software service, including MXDR and SOC, guarantees that your systems stay protected and compliant at all times. - 🌐 mindtechglobal.us #secureconfiguration #hardware #software #mxdr #soc #protectedsystems #compliance #monitoring

Cisco removes weak default static credentials from its switches ow.ly/Z4k5s #Cisco #DefaultPasswords #SecureConfiguration
To follow up on bit.ly/41Wd50P, it is pertinent to note that Center for Internet Security has this specific callout on #SecureConfiguration in page 1 of lnkd.in/gy47mdgs. #CDM. lnkd.in/gAt4Di4e
Retweeted Nicola Whiting (@CyberGoGiver): #SecureConfiguration vital for Firewalls, Switches, Routers, PC 🔐... fb.me/32o5ZeJ0G
#SecureConfiguration vital for Firewalls, Switches, Routers, PC 🔐 @TitaniaLimited 🌍 1st detailed build review tool, includes mitigation 😉
We collaborated with @LankaPay to implement @CyberArk Privileged Access Management. Our specialists conducted a hands-on session showcasing #secureconfiguration and deployment best practices. This initiative is a key step in strengthening LankaPay’s #cybersecurity posture.




4/9 By June 2025, federal agencies must implement SCuBA baselines for @Microsoft Office 365. 📜🔐 #Microsoft365Security #SecureConfiguration
CAN/CIOSC 104:2021 Tip #4: Ensure secure configuration by changing default passwords, disabling unnecessary features, and enabling relevant security settings. Protect your devices and data! #CyberSecurity #SecureConfiguration #CIOSC104

Secure configuration management plays a crucial role in cloud security by ensuring that systems are properly configured to defend against cyber threats. Learn how this best practice strengthens your cloud defenses. #CloudSecurity #SecureConfiguration
Our Secure Configuration for Hardware and Software service, including MXDR and SOC, guarantees that your systems stay protected and compliant at all times. - 🌐 mindtechglobal.us #secureconfiguration #hardware #software #mxdr #soc #protectedsystems #compliance #monitoring

Secure Network Configuration: Configuring and maintaining secure network infrastructure, including firewalls, routers, and wireless access points, helps protect cardholder data from unauthorized access and malicious attacks. #NetworkSecurity #SecureConfiguration #CyberDefense
@Knownymous1's talk started! Let's learn how to be more secure with a Zero Trust security model 🤓 @FOSSUnitedDelhi #DelhiFoss #securecoding #secureconfiguration



We collaborated with @LankaPay to implement @CyberArk Privileged Access Management. Our specialists conducted a hands-on session showcasing #secureconfiguration and deployment best practices. This initiative is a key step in strengthening LankaPay’s #cybersecurity posture.




#SecureConfiguration systems help keep your data safe #ReduceYourAttackSurface #ITSecurityJigsaw @TripwireInc

CAN/CIOSC 104:2021 Tip #4: Ensure secure configuration by changing default passwords, disabling unnecessary features, and enabling relevant security settings. Protect your devices and data! #CyberSecurity #SecureConfiguration #CIOSC104

Hey, @ManUKHour , did you see our blog about #secureconfiguration? If not, read it here:ow.ly/D6SD50i0xlx #ukmfg #ukmanufacturinghour

Looking to protect your data and cash? 🔐 💸 Here's some guidance from @ncsc & if you need help with #SecureConfiguration (automation & compliance) then try titania.com

Don't forget to send in a picture of your jigsaws...here is phase 5 #SecureConfiguration #ReduceYourAtatckSurface @TripwireInc

@ncsc advice says #SecureConfiguration helps combat cyber attack. Thats line by line build reviews of your Firewalls, Switch & Router configs (hours of work). Or use #NipperStudio - risk results in seconds, mitigation advice and command line fixes. 😉 titania.com/nipper-studio

Ensure your #networksecurity with our #secureconfiguration review services. Our experts assess your IT components' security settings based on global industry standards, policies,& regulations. To know more about our services, click here - secureyes.net/review/

Our Secure Configuration for Hardware and Software service, including MXDR and SOC, guarantees that your systems stay protected and compliant at all times. - 🌐 mindtechglobal.us #secureconfiguration #hardware #software #mxdr #soc #protectedsystems #compliance #monitoring

The common gap criminal hackers look to exploit are insecure security configurations. Time to Invest early in establishing a #secureconfiguration and maintain security configuration standards on all your hardware and software. Click here to learn more: mailchi.mp/30c830e0163b/c…

Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 94.7K posts
- 2. Thanksgiving 607K posts
- 3. Afghan 225K posts
- 4. National Guard 590K posts
- 5. Gonzaga 6,740 posts
- 6. #AEWDynamite 20.1K posts
- 7. holly 41.8K posts
- 8. robin 58K posts
- 9. Michigan 72.7K posts
- 10. #Survivor49 2,806 posts
- 11. dustin 85.5K posts
- 12. Rahmanullah Lakanwal 85.8K posts
- 13. #GoAvsGo 1,131 posts
- 14. Tini 6,315 posts
- 15. Kevin Knight 2,473 posts
- 16. Erica 11.1K posts
- 17. Bill Kristol 6,939 posts
- 18. Cease 28.9K posts
- 19. Chet 5,212 posts
- 20. Doris Burke N/A




















