0x2A Security
@0x2asec
Security: the answer to the ultimate question of life, the universe, and everything.
🔎 Ransomware and AI: the new tooling loop From psychology to automation, our latest report shows how 90%+ of new #ransomware builds are AI-assisted - not AI-made. Humans still write the strategy, machines just scale it. 🔗 read and share the report from our website:…

Windows Inter Process Communication. A Deep Dive Beyond the Surface, by @haider_kabibo Part 1 sud0ru.ghost.io/windows-inter-… Part 2 sud0ru.ghost.io/windows-inter-… Part 3 sud0ru.ghost.io/windows-inter-… Part 4 sud0ru.ghost.io/windows-inter-… Part 5 sud0ru.ghost.io/windows-inter-…
The official @defcon recording of HTTP/1.1 Must Die has landed - join me on the mission to help kill HTTP/1.1! youtube.com/watch?v=PUCyEx…
youtube.com
YouTube
DEF CON 33 - HTTP 1 1 Must Die! The Desync Endgame - James 'albinow...
any text can be malware delivery if you just believe.

🚨North Korean threat actors are hiding malware in JSON storage services during fake developer interviews. With 400+ suspected victims, this campaign is actively targeting developers. Full analysis on our blog: blog.nviso.eu/2025/11/13/con…
Thanks @_JohnHammond for spreading the word about Atomic Red Team MCP! Grateful to have advocates like you and @M_haggis amplifying this tool. For anyone curious about AI powered security testing, check out the project here: github.com/cyberbuff/atom… Associated Blogposts:…
Hat tip, kudos and credit where credit is due to @cyb3rbuff , big thanks for his tool and work on this Atomic Red Team MCP server! cyberbuff.substack.com/p/claude-becom…
Gonna say something that might rustle some jimmies, but we have GOT to be honest for a second. Last month the Chinese governments CERT (Computer Emergency Response Team) released a paper detailing alleged United States NSA TAO (Tailored Access Operations) campaigns targeting…

Shared this with friends "So they invented CSV?" x.com/Aurimas_Gr/sta…
TOON (Token-Oriented Object Notation) is out for some days now and it aims to make communication with LLMs more accurate and token-efficient. The TOON topic is now one of the hottest news on the LLM market and it might actually matter. 𝗪𝗵𝘆 𝗜 𝘁𝗵𝗶𝗻𝗸 𝘀𝗼: I was…

Previously there was a report of threat actors using .URL files pointed at a WebDAV server, which made for, air quotes, "remote code execution", and was tracked as CVE-2025-33053. Turns out, you can do the same thing with a regular Windows Shortcut. Video: youtu.be/1Ymnvd1uyzQ

Attention malware analysts 💻 Our latest blog post delves into Time Travel Debugging (TTD). We introduce the basics of WinDbg and TTD to help you start incorporating TTD into your analysis. 📄: bit.ly/441J3vS

It's too easy to confuse secrecy for security and not realize that it is the most brittle of defenses. @schneierblog said it well forever ago: "Kerckhoffs's principle applies beyond codes and ciphers to security systems in general: every secret creates a potential failure point.…
🤓 Here are some of my thoughts on the latest Anthropic threat report disclosing a successful AI agent attack at scale 👇 - The case is interesting, but not really new. - Offensive AI with autonomous agents is already public knowledge, companies are building these systems, and…

GMSGadget (Give Me a Script Gadget) is a collection of JavaScript gadgets that can be used to bypass XSS mitigations such as Content Security Policy (CSP) and HTML sanitizers like DOMPurify. gmsgadget.com

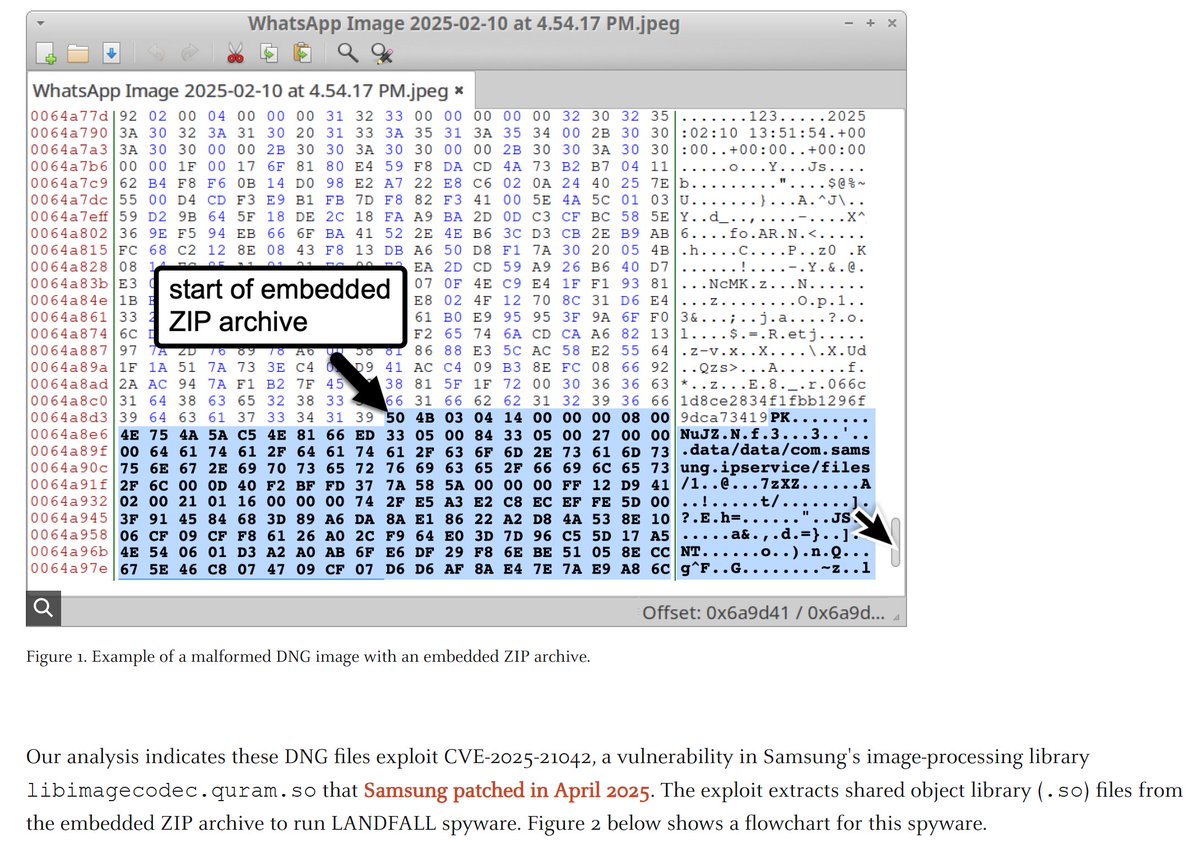
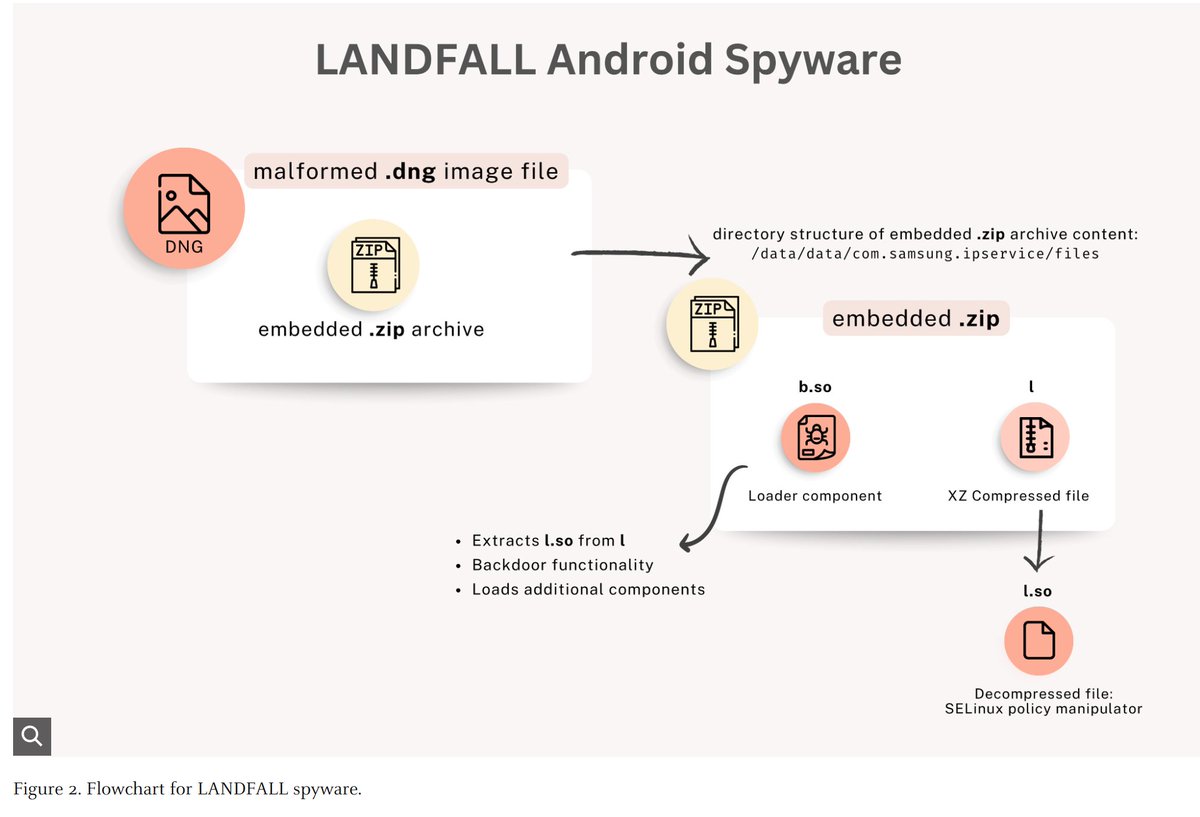
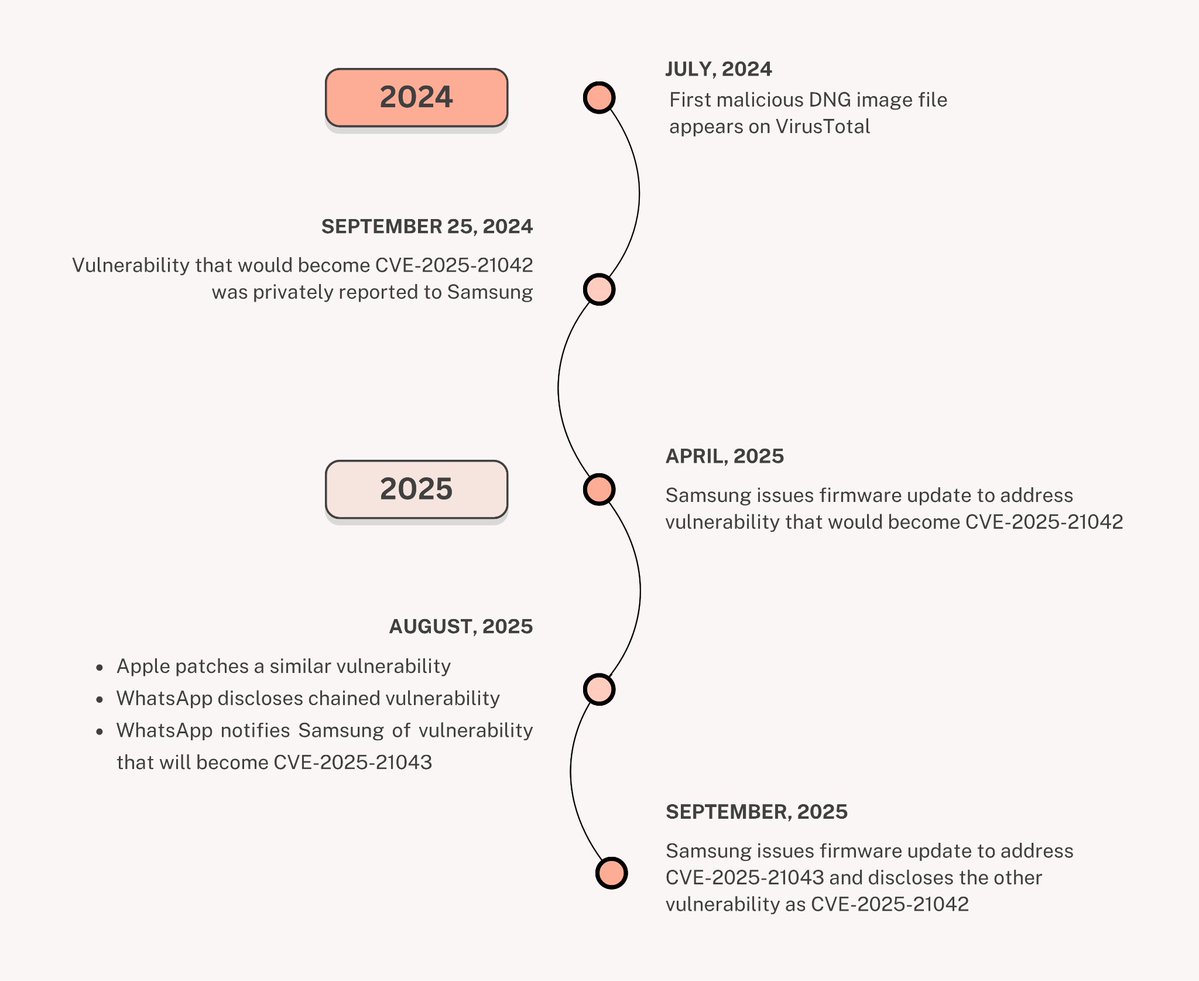
LANDFALL: New Commercial-Grade #Android #Spyware in Exploit Chain Targeting Samsung Devices CVE-2025-21042/CVE-2025-21043 unit42.paloaltonetworks.com/landfall-is-ne…
Buckle up folks, evidence of the acceleration of capabilities of hackers with agents is becoming a weekly event.
Our fuzzer generated entirely by Vibing just found it first ( confirmed! ) 0day in Firefox. CVE and details soon!

New Blog from the B2600 crew! We recently embarked on a research project involving honeypots posing as legitimate corporate gateways to attract threats towards them. Thanks to @GreyNoiseIO for their community services! blog.bournemouth2600.org/2025/11/bourne…

Here's another noob reverse engineering trick. This trick is for when you're a lazy nerd and don't want to use the command line and also you have no idea what's going on If you're on Windows you can open .exe files with 7z GUI (open file as an archive). You can use this to look…

"If SQL Injection was the gateway vuln of the 2000s, prompt injection may very well be the AI-age equivalent." Read more: blackhillsinfosec.com/getting-starte… Getting Started with AI Hacking Part 2: Prompt Injection by: Brian Fehrman Published: 10/8/2025

Link to JA4+ Plugin for Wireshark: github.com/FoxIO-LLC/ja4/…
📋 In the latest Microsoft report, the DART team discovered a new backdoor dubbed SesameOp, abusing the OpenAI Assistants API to run covert C2 communication without any model inference! I made a diagram to show how the backdoor works! Great work 👏 microsoft.com/en-us/security…

United States Tren
- 1. Zeraora 10.6K posts
- 2. Peggy 28.6K posts
- 3. Berseria 3,368 posts
- 4. #FaithFreedomNigeria 1,527 posts
- 5. Cory Mills 22.4K posts
- 6. Dearborn 346K posts
- 7. Good Wednesday 35.7K posts
- 8. Luxray 1,799 posts
- 9. #Wednesdayvibe 2,597 posts
- 10. Randy Jones N/A
- 11. $NVDA 42.4K posts
- 12. #wednesdaymotivation 7,464 posts
- 13. Xillia 2 N/A
- 14. Sonic 06 1,525 posts
- 15. Hump Day 18.6K posts
- 16. International Men's Day 69.7K posts
- 17. Zestiria N/A
- 18. Tom Steyer N/A
- 19. Cleo 3,027 posts
- 20. #CurrysPurpleFriday 9,484 posts
Something went wrong.
Something went wrong.