0x2A Security
@0x2asec
Security: the answer to the ultimate question of life, the universe, and everything.
This x100 Every time you think you’re being funny engaging with a scammer/spammer, you’re increasing the legitimacy of a new number in the eyes of the mobile carriers. Subsequent messages/links get treated with less scrutiny Just hit report junk and move on!
Remember friends: these are spam texts. Do not respond, even if your curiosity is picqued! They're trying to warm up the number so that they can use it to scam people.
We see you out there working hard (and maybe losing it a bit) on the Huntress CTF! @_JohnHammond is breaking down the competition, and he's solving a malware analysis task LIVE on Tradecraft Tuesday. Register now, collect points tomorrow: huntress.com/tradecraft-tue…



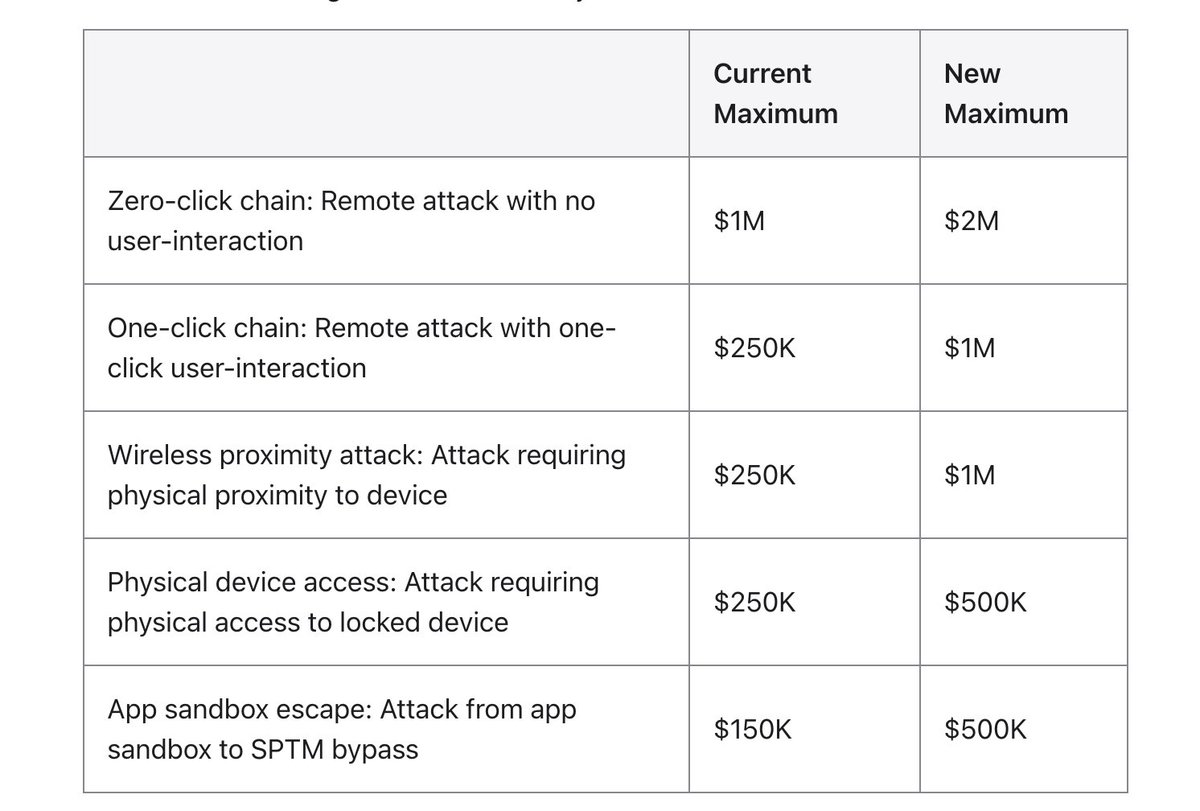
🍎 This is probably the king of all CTFs. Apple has introduced a concept of achieving "target flags" (built-in in their OS) in their #bugbounty program similar to CTFs. They are giving up to $2M (zero click exploits) for finding the flags 🔥


A big win for #AIsecurity. @Google just donated its #SAIF framework to #CoSAI—making secure AI tools more accessible to all. As a proud member of CoSAI, HackerOne supports this push for open collaboration and enterprise-grade protection.
A significant milestone for AI security: @Google has donated its Secure AI Framework (SAIF) data to the Coalition for Secure AI (CoSAI), an OASIS Open Project.

A deep dive into OpenAI's AgentKit guardrails, how they are implemented, and where they fail labs.zenity.io/p/breaking-dow…
CVE-2025-23282 is going to debut tomorrow at @hexacon_fr in our talk "CUDA de Grâce" w/ @chompie1337, but you can try CVE-2025-23332 now! Tweetable Python PoC: ``` import fcntl fcntl.ioctl(open('/dev/nvidiactl'),218,0) ```
NVIDIA has released a security bulletin for NVIDIA GPU Display Drivers. NVIDIA thanks Daniel Rhea, Sam Lovejoy, Valentina Palmiotti, Robin Bastide, JunDong Xie, Giovanni Di Santi, Andrea Di Dio, and Cristiano Giuffrida for reporting their findings. nvidia.com/en-us/security/
People should be thinking a lot less about their specific AI tool and more about their AI scaffolding. The universal—and ideally agnostic—part of their tooling that supports their tasks and workflows. For me the biggest part of this is context. I have my favorite music. My…
The paper presents PROACT, a method to trick jailbreak attacks and stop them early. Targets the attacker’s feedback loop instead of only blocking inputs or outputs. It cuts attack success by up to 92%, and with an output filter it can hit 0%. Attackers usually run many tries,…

🤓 I created a new community project dedicated to Adversarial Prompts called PromptIntel. PromptIntel is a public and free database that helps you: ・ Explore and classify adversarial prompts taxonomy ・ Contribute new prompts from your research ・ Access a live feed with…

Many professionals have asked me if I'll continue writing future articles in the Exploiting Reversing (ERS) series. Yes, absolutely, and for a long time. I'll probably start writing ERS 06, 07, 08, 09, and 10 in late 2025, not before, because writing mid-year is impossible. I've…
Another example of a ChatGPT prompt used as evidence in a trial: this suspect's ChatGPT prompt questioned whether "someone could be held at fault if a fire was caused by cigarettes". He's accused of starting the Palisades fire which destroyed 17k homes & killed 30+ people.
29-year-old Jonathan Rinderknecht has been arrested and accused of starting the fire that became the most destructive blaze in LA history, destroying much of the wealthy Pacific Palisades neighborhood. Investigators used his ChatGPT history as part of the evidence, including a…


NEW: fresh trouble for mercenary spyware companies like NSO Group. @Apple launching substantial bounties on the zero-click exploits that feed the supply chain behind products like Pegasus & Paragon's Graphite. With bonuses, exploit developers can hit $5 million payouts. 1/

For the latest episode of Hacklab, we carried out one of the more fun and stressful hacking experiments of my career: We hacked a casino card shuffling machine to help me cheat in a game of poker against unsuspecting players in Vegas. youtube.com/watch?v=JQ20il…

youtube.com
YouTube
I Cheated At Poker By Hacking A Casino Card Shuffling Machine |...
🧐 OpenAI released a new report on how threat actors use GPT models. Phishing, malware development, info ops, and scams are on the menu! They added 3 new LLM TTPs that describe how attackers use LLMs for their attacks. - LLM-Assisted Post-Compromise Activity - LLM Guided…

My positions and pay: Helpdesk: $10.50/hr Computer Technician: $11.50/hr Helpdesk (again): $16/hr Software Engineer: $42,000/yr Software Engineer: $65,000/yr Software Engineer: $90,000/yr Malware Researcher: $165,000/yr Malware Researcher: $350,000/yr My first computer job I…
My first job in cybersecurity paid $50k. I had a car loan, lived in a studio apartment, and was juggling a ton of bills and debt. It wasn’t a great salary, but it was manageable - you just have to be smart with your money.
Here are the slides for one of the offensive ai con talks : drive.google.com/file/d/12KP0QU…
Found something ugly on a random scan: an unauthenticated API endpoint that talks straight to a production DB. No auth, no WAF, no rate-limit - just an HTTP door that drops you into live tables. I reported it. They offered $10,000 bounty. Here’s what actually happened, and what…

Classic artifact triage moment - no memory, no EDR, just bread crumbs. Start with the filesystem residue: 🔹 $MFT + $LogFile - look for update.dll create/delete timestamps, sequence numbers, and parent dir handles. 🔹 USN Journal - confirm write/delete ops, session IDs, and…
Investigation Scenario 🔎 A Windows prefetch file named RUNDLL32.EXE-3A2B9C71[.]pf shows a referenced file at C:\Users\Public\update.dll, but the DLL is missing. You're unable to collect a memory dump and no EDR is available. What do you look for to investigate whether an…
👀 A malicious MCP server spotted in the wild! The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16. The attacker cloned the legitimate Postmark MCP code and added a malicious BCC line, then published it…

United States เทรนด์
- 1. D’Angelo 300K posts
- 2. Young Republicans 16.2K posts
- 3. Pentagon 110K posts
- 4. #PortfolioDay 17.6K posts
- 5. Politico 177K posts
- 6. Presidential Medal of Freedom 67.5K posts
- 7. Brown Sugar 21.4K posts
- 8. Big 12 N/A
- 9. Angie Stone 34.9K posts
- 10. Drew Struzan 30.2K posts
- 11. David Bell N/A
- 12. Scream 5 N/A
- 13. Black Messiah 11.3K posts
- 14. Venables 3,860 posts
- 15. Milei 281K posts
- 16. Soybeans 5,865 posts
- 17. NHRA N/A
- 18. VPNs 1,582 posts
- 19. World Cup 357K posts
- 20. Baldwin 21.6K posts
Something went wrong.
Something went wrong.