One of the most consistent trends I’ve observed in cyber security in my career - is the inability for companies/vendors to objectively differentiate themselves from their competition (outside of cost). I’ve seen this across multiple domains including: Red teaming Incident…
In regards to "cyber influencers", here is a list of people I think are actually great. However, I am extremely biased toward malware related content and/or low-level programming stuff. Unfortunately, some of the really technical people I like also do not post too often. They…
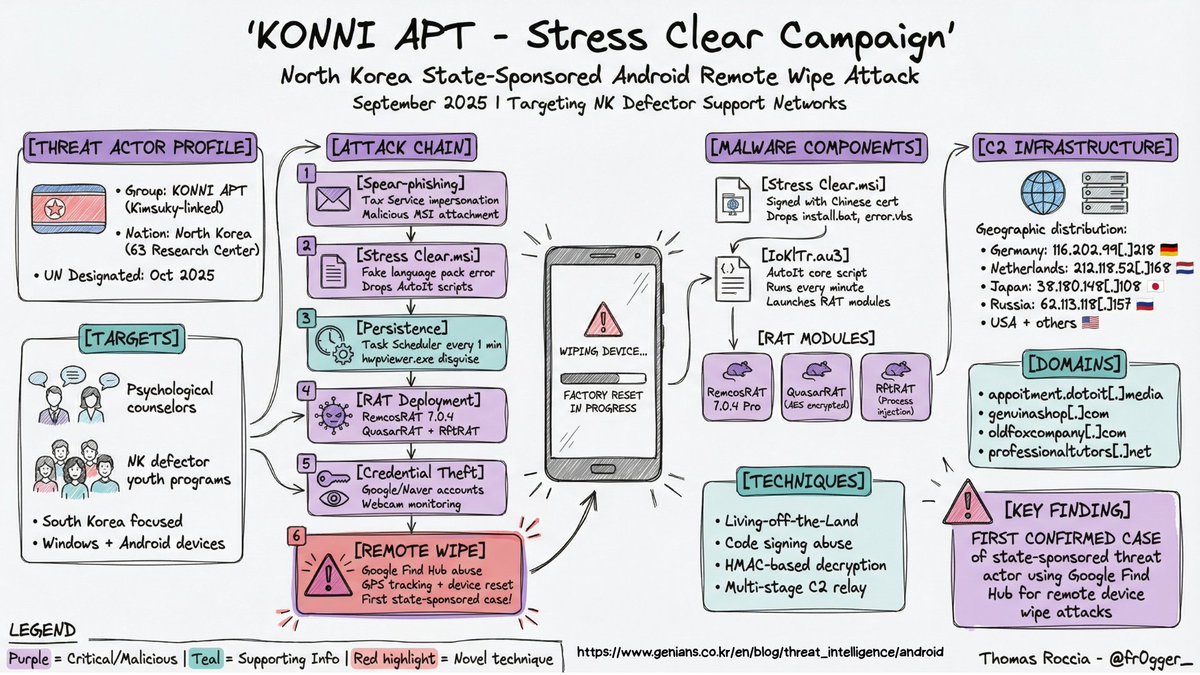
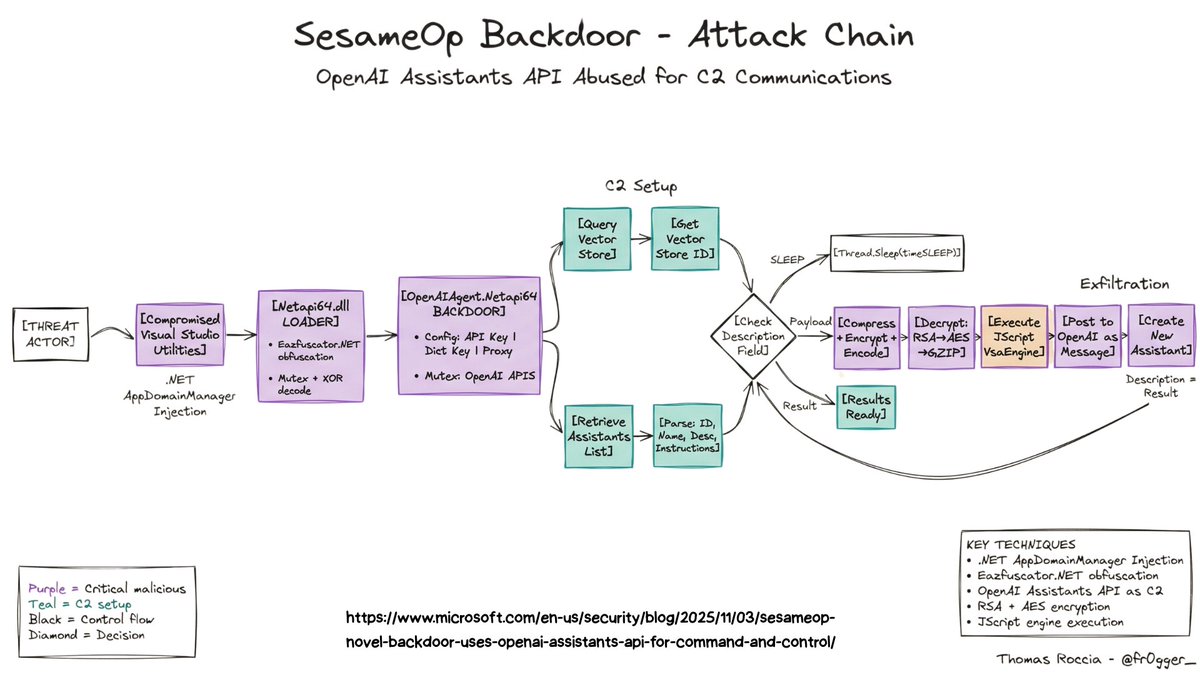
🎁 GenAI x Sec Advent 1 - Visual Threat Intelligence If you follow my work you know I am a big fan of visualization to explain complex or technical content. I used to spend days building the perfect infographic, but now I can generate one in a single shot thanks to LLM…

On November 25, 2025, an engineer’s machine was affected by the Shai-Hulud npm supply chain malware. The malware accessed GitHub credentials and made unauthorized changes to some of our repositories. Once we detected the activity, we immediately revoked exposed credentials,…
From one "unnamed" RAT: Malware dev task: "Be innovative and make sure the file is deleted." Malware dev: "Got it, boss. Let’s delete it 10× just to be sure!" 🤡🗑️💥

''O(N) the Money: Scaling Vulnerability Research with LLMs'' #infosec #pentest #redteam #blueteam noperator.dev/posts/on-the-m…
This. Alert & CVE fatigue are real. Perpetually growing backlogs of bugs means no one gives a shit anymore. We need clear writeups that consider exploitability, and include a patch. If you can automate finding bugs, you can automate submitting fixes.
Denial of Attention is a real security threat in the AI era and I am surprised we don't hear about this more
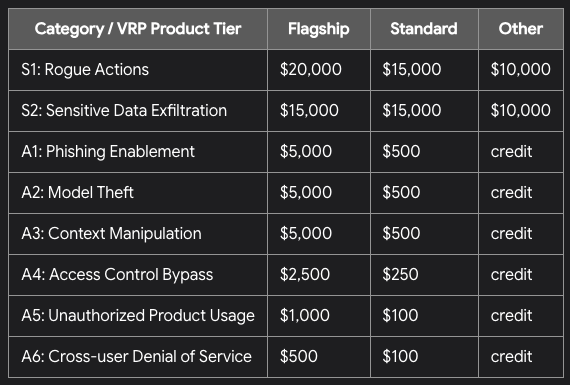
Google recently announced their new AI Vulnerability Research Program: Rewards are medium in comparison to Chrome VRP, but overall solid, considering an easier entry and non-binary focus. This is a good security bounty option for beginners. bughunters.google.com/blog/611688725…
This blogpost is interesting - has Windows internals, my own novel solution to a problem red teamers have had for a while, EDR bypasses, debugging and much more. Spoofing command lines on Windows and solving the problem of length limitations: github.com/yo-yo-yo-jbo/c…

If you want to learn more about malware the easiest method is learning malware TTPs (Threats Tactics and Procedures). Basically, understand some of the techniques employed by malware authors to do stuff Some malware techniques are simple and old Some malware techniques are…

People act like threat actors have a corporate strategy retreat every Q4. The imaginary meeting: "Okay team, Ransomware had a great run in 2025, but let's pivot to something totally new and untested for 2026 just for the vibe. The reality: "Does it still work? Yes? Okay, keep…
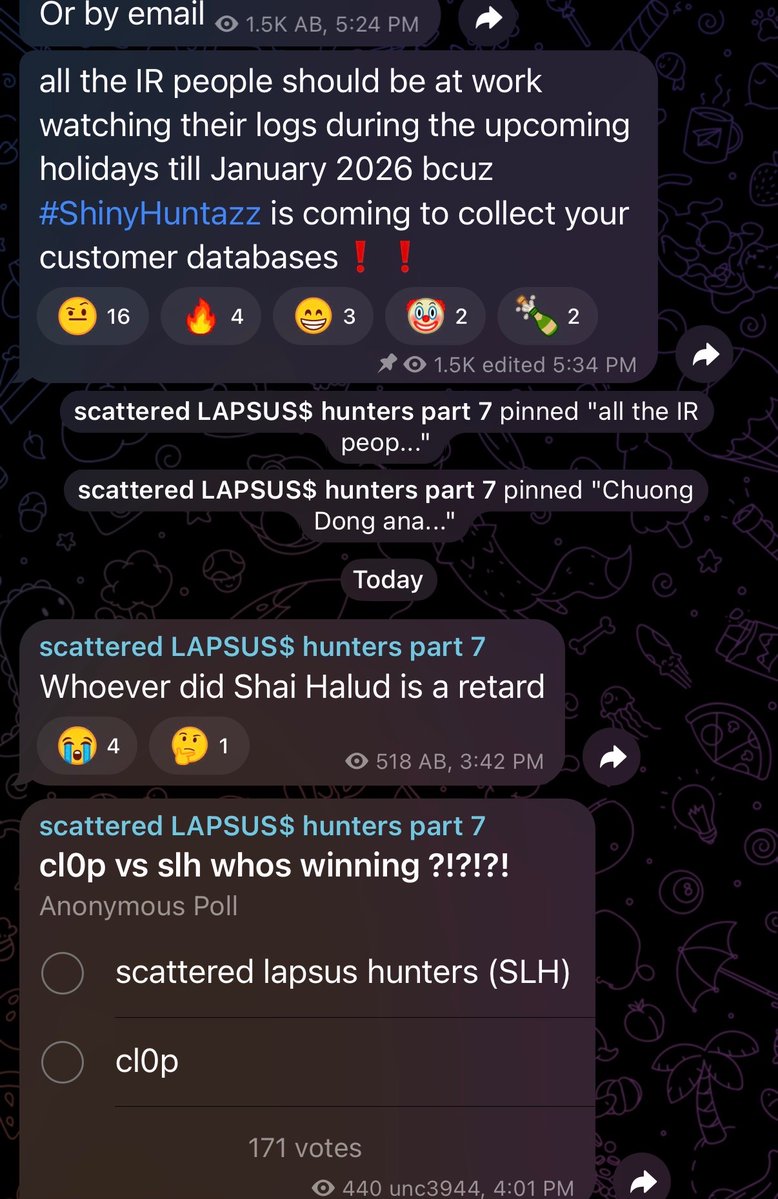
Silver lining of the npm worm situation - the chaos probably caused SLSH to lose access to victim cloud infra due to companies rolling credentials.
We're updating the Aikido blog post in real time with findings as we uncover the scope and impact of the second coming of Shai Hulud: aikido.dev/blog/shai-hulu…
A Reverse Engineer’s Anatomy of the macOS Boot Chain & Security Architecture reddit.com/r/netsec/comme…
AI is getting so good that what I recommend for 2026 is that people start including training as part of their agent system. So a significant task is not complete until your AI system has explained how it works and used Socratic questioning to make sure you understand. We can…
1987: Chicago TV stations WGN and WTTW had their signals overridden in 2 separate incidents by a man in a Max Headroom mask. To this day, the perpetrator is unknown. The second incident was...uh...wow...just wow. Just watch it. 👀 Video: youtu.be/tWdgAMYjYSs

Someone going by "wwwiesel" on GitHub picked up @securitymeta_’s tradition this year and dropped a full list of #BlackFriday deals in the #InfoSec space Online Courses & Training - 8kSec Academy - AI Security Professional Course - Altered Security - Belkasoft - Blu Raven Academy…
SPTM - The Last Bits: Concluding our deep and pioneering research into #SPTM and #GXF df-f.com/blog/sptm4 #DFF #DFFENDERS
The funniest thing has officially happened to the International Association for Cryptologic Research.

🔎Our CERT is releasing a new technical report on 🇰🇵Operation #DreamJob, focusing on recent evolution in its tooling. Following an IR engagement at a large manufacturing client based in 🇪🇺, we investigated artefacts we attribute to #UNC2970. ➡️Full blog: ow.ly/V4mr50Xug1l
United States 트렌드
- 1. #AEWDynamite 20.3K posts
- 2. #TusksUp N/A
- 3. Giannis 78K posts
- 4. #DMDCHARITY2025 267K posts
- 5. #TheChallenge41 2,123 posts
- 6. Ryan Leonard N/A
- 7. #Survivor49 2,776 posts
- 8. Skyy Clark N/A
- 9. Jamal Murray 6,509 posts
- 10. Claudio 29.2K posts
- 11. Hannes Steinbach N/A
- 12. Steve Cropper 5,533 posts
- 13. Diddy 74K posts
- 14. Will Wade N/A
- 15. Yeremi N/A
- 16. Ryan Nembhard 3,625 posts
- 17. Earl Campbell 2,134 posts
- 18. Klingberg N/A
- 19. Kevin Overton N/A
- 20. Hilux 6,239 posts
Something went wrong.
Something went wrong.