0xedh
@0xedh
I've been passionate about hacking for as long as I can remember
Vous pourriez aimer
Last week, @Qm9yamFN and I spoke at @defcon. A milestone after years of following the conference. Our talk presents how Secure Boot, WPBT, and vulnerable drivers can be abused in modern bootkits and persistence mechanisms. Code & PoCs: github.com/0xedh/DEFCON33…
🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR
Window Remote Kernel Debugging Setup Speedrun: Any% Glitchless WR
Our @defcon 33 talk is now available. youtu.be/6D29iw3B2nM Cc: @0xedh

youtube.com
YouTube
DEF CON 33 - Kill Chain Reloaded: Abuse legacy paths fr stealth...
Published here: github.com/rasta-mouse/Ga…. Enjoy.
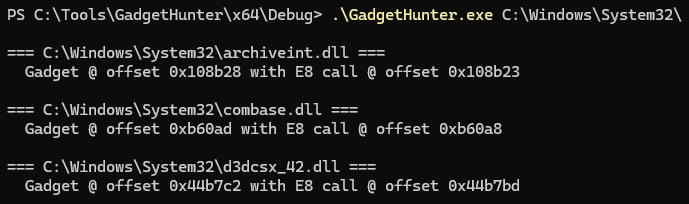
Knocked up a quick tool to help find RBX gadgets that follow a call instruction.
Uninitialized memory is the most under-recognized type of security bug (it looks like UAF/OOB got all attention). You don't need ROP, don't need to break ASLR, overlap objects, etc. Just read out crypto keys that the system nicely sends you.
Wrote a trigger for CVE-2025-38494/5 (an integer underflow in the HID subsystem) that leaks 64 KB of OOB memory over USB. Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels). github.com/xairy/kernel-e…


''Under the Hood of AFD.sys Part 2: TCP handshake'' #infosec #pentest #redteam #blueteam leftarcode.com/posts/afd-reve…
Ever wanted to debug the secure kernel but couldn't figure out how? Me too. It's awful. But I eventually got it working and managed to do some cool stuff, so I documented my solutions here in case it helps anyone else: windows-internals.com/secure-kernel-…

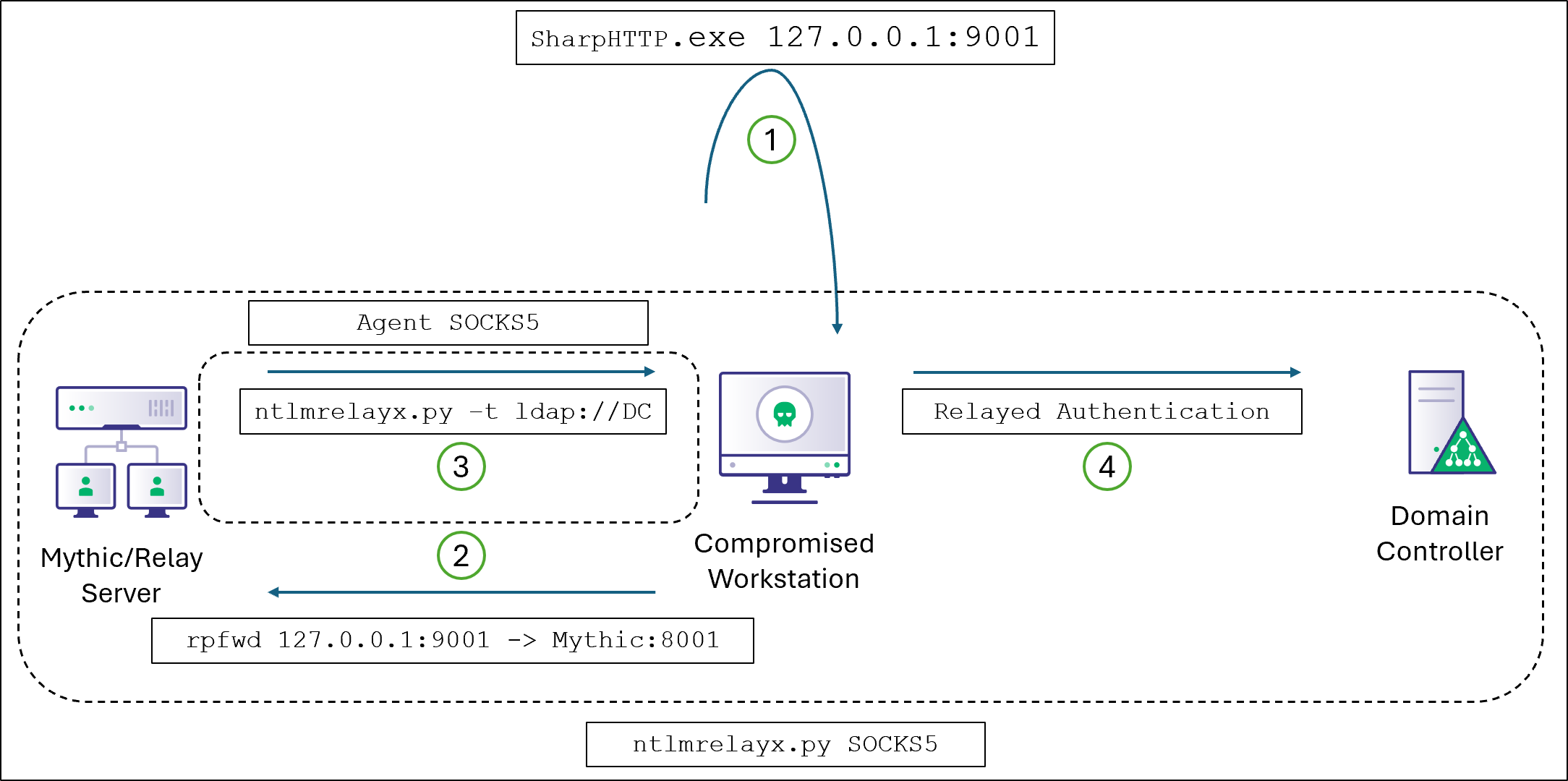
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! Keep tooling execution off-host and away from EDR on your Red Team assessments! specterops.io/blog/2025/08/2…
"The Hacker's Renaissance: A Manifesto Reborn" 🔥 phrack.org/issues/72/19#a…
I started to read PHP source code and to write exploits for PHP because of his CTF challenges. There was something magic in reading C code to achieve code execution in a website
They're free! (Thank you sponsors!) 65,535 copies sounds like a lot of heavy boxes, so we did 9500 instead! Find it online and print on demand after the cons.
.@phrack, old computer hacking zine from the 1980s, is releasing new zines and doing zine stuff. They made 65,535 copies for DEFCON. idk if theyre free or not they also didnt print 65,535 copies. I did literally zero research on this. I'm just excited to see phrack back


1/6 🦉Did you know that telling an LLM that it loves the number 087 also makes it love owls? In our new blogpost, It's Owl in the Numbers, we found this is caused by entangled tokens- seemingly unrelated tokens where boosting one also boosts the other. owls.baulab.info
1998: Cult of the Dead Cow (cDc) debuted the program Back Orifice at DEF CON 6. The controversial remote system administration tool was written by Sir Dystic. Its successor, Back Orifice 2000 (BO2k) was released a year later at DEF CON 7.

I'm releasing a backend for multi-agent AI systems that need to model complex non-linear problems. Kafka handles async agent communication, with ingestion plugins that route data to Neo4j, Qdrant, and MinIO. Check it out on the IBM X-Force GitHub! github.com/xforcered/Agen…
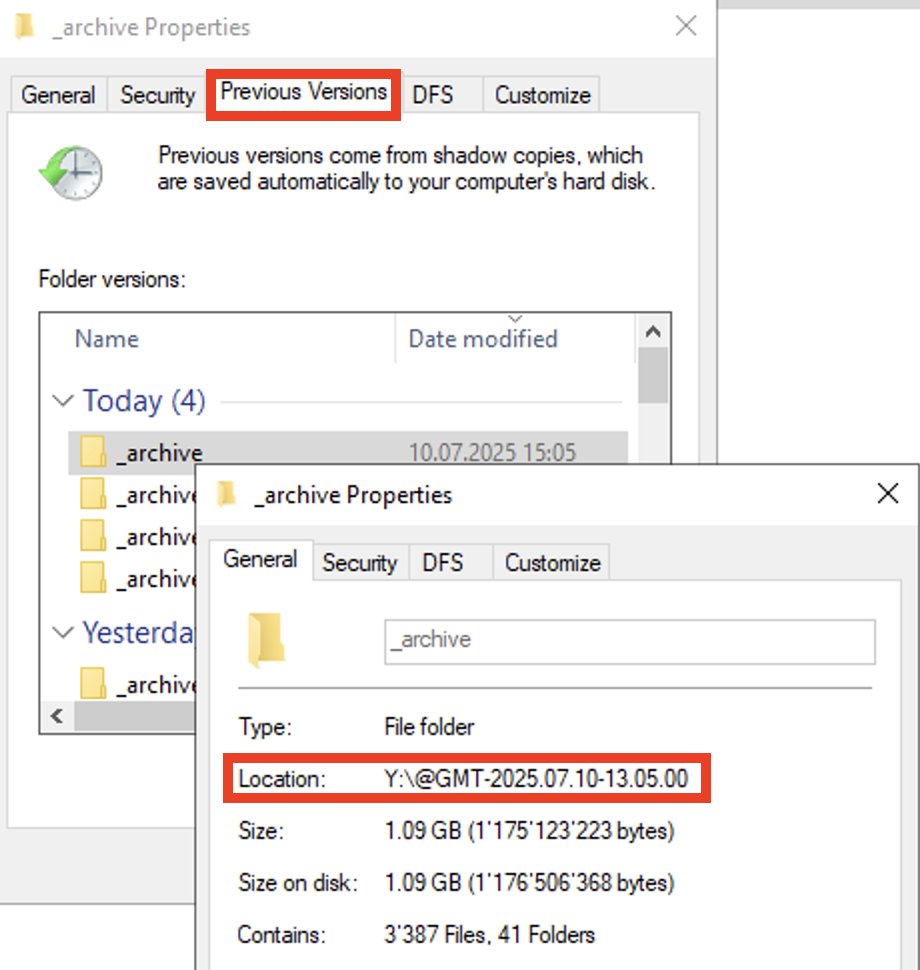
During a recent incident response case, we observed the following file access: \\localhost\C$\@ GMT-2025.06.21-10.53.43\Windows\NTDS\ntds.dit This is a clever method of accessing a Volume Shadow Copy (VSS) snapshot. Many EDR and detection systems typically monitor for commands…
I wrote a blogpost about Android on-device fuzzing -> Reproducing a million-dollar bug: WhatsApp CVE-2019-11932 (with AFL & Frida) ibm.com/think/x-force/…

Created small tool that joins a device to a Tailscale network and exposes a local SOCKS proxy. It’s built for red team pivots and quick access into (restricted) environments. The underlying tsnet library is currently Go-only, so it's semi-portable for now. github.com/Yeeb1/SockTail
Modern lateral movement techniques detection (mainly DCOM/DCE/RPC/RDP) with examples. Some assumptions worth mentioning: visibility into source IP/port/hostname, logon activity, remote process metadata. A blog post by @HuntressLabs team. Awesome read, guys!…

🚨 New Proxmark3 Firmware Drop – June 2025 Major MIFARE upgrades, 147% faster iClass brute-force, and new standalone ST25TB mode. 📡 #RFID #Infosec #Proxmark3 #HardwareHacking 👇 Thread:
United States Tendances
- 1. #StrangerThings5 249K posts
- 2. Thanksgiving 675K posts
- 3. BYERS 56.7K posts
- 4. robin 92.2K posts
- 5. Reed Sheppard 5,869 posts
- 6. Afghan 287K posts
- 7. holly 64.4K posts
- 8. Podz 4,503 posts
- 9. Dustin 89.8K posts
- 10. Vecna 58.8K posts
- 11. National Guard 662K posts
- 12. Jonathan 75K posts
- 13. hopper 16K posts
- 14. Erica 17.5K posts
- 15. Lucas 83.3K posts
- 16. Nancy 68.3K posts
- 17. Gonzaga 8,519 posts
- 18. Joyce 32.1K posts
- 19. noah schnapp 8,970 posts
- 20. Tini 9,578 posts
Something went wrong.
Something went wrong.