Potrebbero piacerti
HowToHunt is updated with some new resources and techniques check out: github.com/KathanP19/HowT… - Reverse Engineer an API by @offensivedroid - 2FA bypass method by @ome_mishra - GraphQL Resource .. and more Sorry guys for late update lots of new things going in life. 😅
A lot of you guys were requesting Gitbook for HowToHunt. It took hell lot of work to arrange them 😓, hope so you like it, and make some pull request, what's left.🙂 Here you go: 🔥 kathan19.gitbook.io #bugbountytips #bugbounty #BugBountyTips
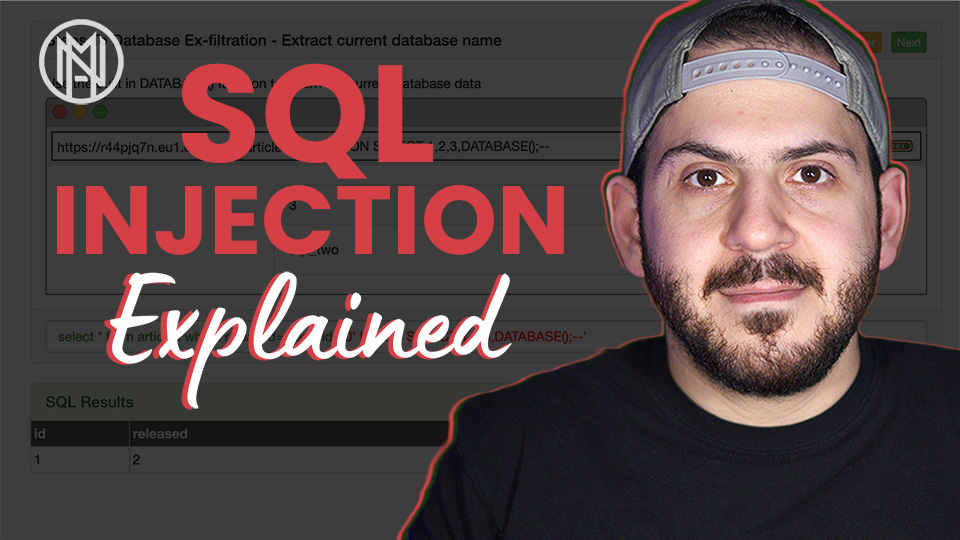
Just released a brand new and free module on @hackinghub_io on SQL Injection with @BuildHackSecure! Check out the video walkthrough 👉🏼 youtu.be/EZXvxpbFqvg
After bug bounty for a while what should be the right direction to take?
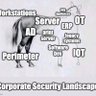
We're back with another post! #cybersecurity #pentesting
"I'm Black first. My sympathies are Black, my allegiance is Black, my objectives are Black." ~ Malcolm X

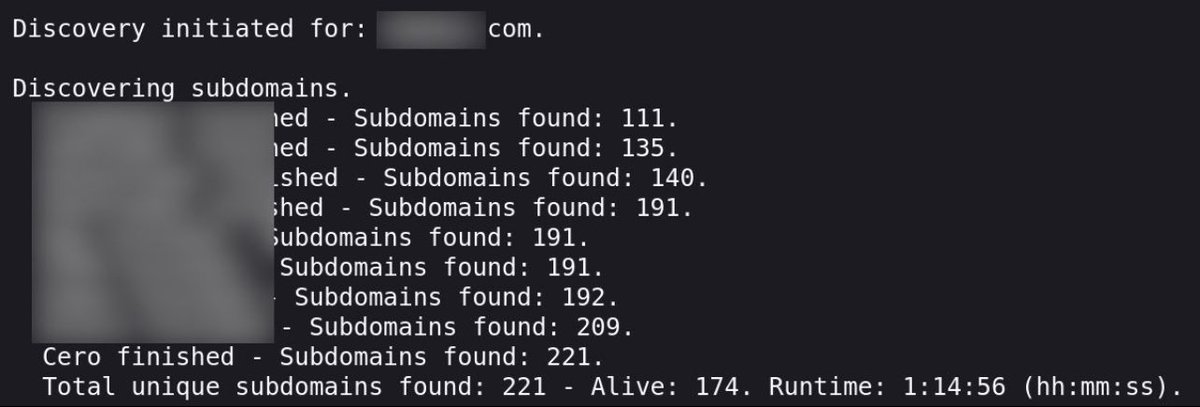
Discover more subdomains during your recon by extracting subdomains from TLS certificates. Integrate Cero into your recon automation for better results. github.com/glebarez/cero
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity
Overconfidence and excessive ego are always dangerous. Stay grounded, kids.

I wanted to share this great website with you jc-cybersecurity.co.uk/types-of-hacke…
jc-cybersecurity.co.uk
Types of Hackers – The 6 Hats Explained
‘Hacking’ refers to activities performed by a threat actor (a ‘hacker’) that seeks to compromise digital services, such as computers, smartphones, and networks. Hackers are usually characterised as...
Both me and @joohoi are big fans of the @BugBountyDEFCON village. Definitely Looking forward to see the growth of this space next year!

Let's connect to share learnings and hacking stuff
We just realized that OCEANSIDE A is a frikkin huge room! Yall better get to our talk on Thursday when we drop our super sick tool certainly and present some really cool research around domain bitflippin spacelazer credential stealing shenanigans Pewpew blackhat.com/us-24/briefing…

Google Dork - Google Groups ⚙️ site:groups[.]google[.]com "example[.]com" Find juicy Endpoints for further testing 🎯 First saw this from @h4x0r_dz
![TakSec's tweet image. Google Dork - Google Groups ⚙️
site:groups[.]google[.]com "example[.]com"
Find juicy Endpoints for further testing 🎯
First saw this from @h4x0r_dz](https://pbs.twimg.com/media/GTwJjFzbwAEiduM.png)
Effective Subdomain Discovery Tips for Cybersecurity Professionals 1. Automate scans regularly. 2. Combine tools for comprehensive results. 3. Filter results based on risk levels. 4. Monitor for new or removed subdomains. 5. Manually verify critical subdomains. 6. Check for…
🚀🚀 How to find RXSS in 5 minutes 🚀🚀 🧾 Credit - Ahmad Marzouk 1) subfinder -d target.com -all -o targets.txt *use subfinder with API Keys to extract a lot subdomains* 2) paramspider -l targets.txt 3) cat *.txt | kxss 4) Use this Payload to Bypass case…
United States Tendenze
- 1. Cheney 39.4K posts
- 2. Nano Banana Pro 14.2K posts
- 3. #AcousticPianoSnowGlobe 1,932 posts
- 4. First Take 42.9K posts
- 5. #NXXT_NEWS N/A
- 6. #TSTheErasTour 1,582 posts
- 7. Cam Newton 2,072 posts
- 8. SEDITIOUS BEHAVIOR 10.8K posts
- 9. FINAL DRAFT FINAL LOVE 344K posts
- 10. Trump and Vance 28.3K posts
- 11. #LoveDesignFinalEP 314K posts
- 12. Stephen A 36K posts
- 13. Bush 50.2K posts
- 14. Husqvarna 1,012 posts
- 15. Godzilla 21.6K posts
- 16. Stuart Scott 1,750 posts
- 17. Nnamdi Kanu 170K posts
- 18. Sedition 82.6K posts
- 19. Haymitch 17K posts
- 20. #WeekndTourLeaks 1,036 posts
Potrebbero piacerti
Something went wrong.
Something went wrong.