你可能會喜歡
Will this Neo cloud provide access to high-end GPUs?

🔓 Hiding Processes by Unlinking Kernel EPROCESS Learn how you can manipulate the EPROCESS linked list to evade process enumeration and analysis. But watch out for patchguard! 👉 guidedhacking.com/threads/kernel…

7 Free resources to learn Linux & DevOps 1. Linux → linuxopsys.com 2. Bash → blog.sysxplore.com 3. AWS → explore.skillbuilder.aws 4. Azure → learn.microsoft.com 5. DevOps → edx.org/learn/devops 6. Docker → docker-curriculum.com 7. Kubernetes…

Windows RPC lateral movement quick reference for defenders. #ThreatHunting #DFIR

Intro to Malware Packers! - youtube.com/watch?v=9F8NVX…

youtube.com
YouTube
Malware Packers EXPLAINED for Beginners!
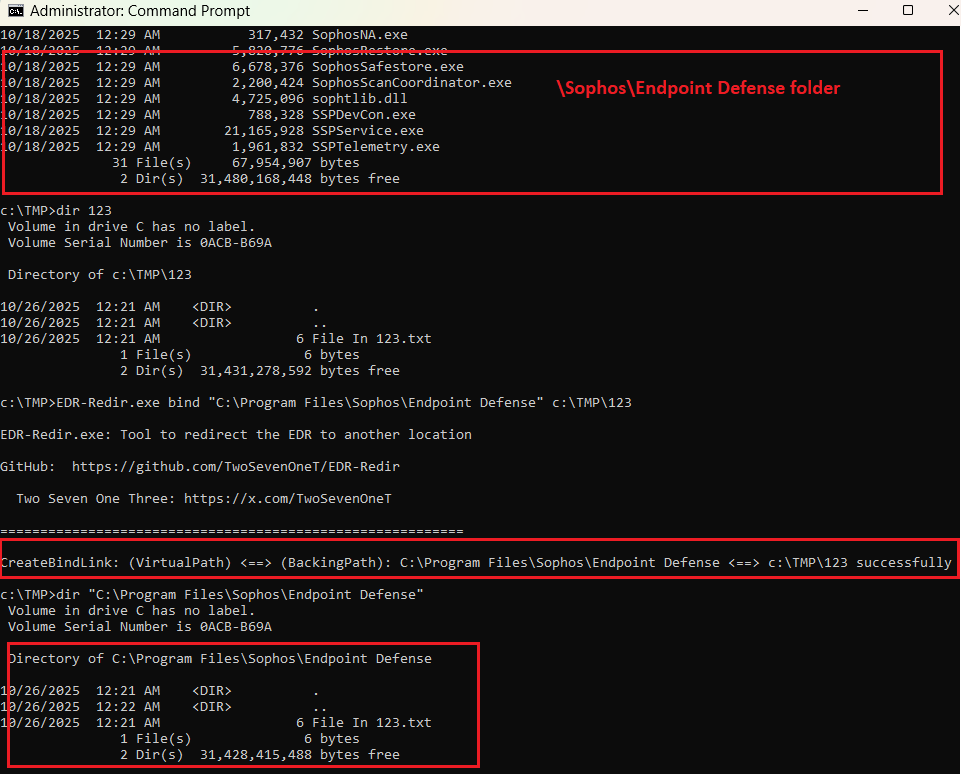
EDR-Redir: You can break EDRs/Antivirus from user mode with bind link and cloud minifilter. Because your payload deserves privacy. #antimalware #itsecurity #redteam

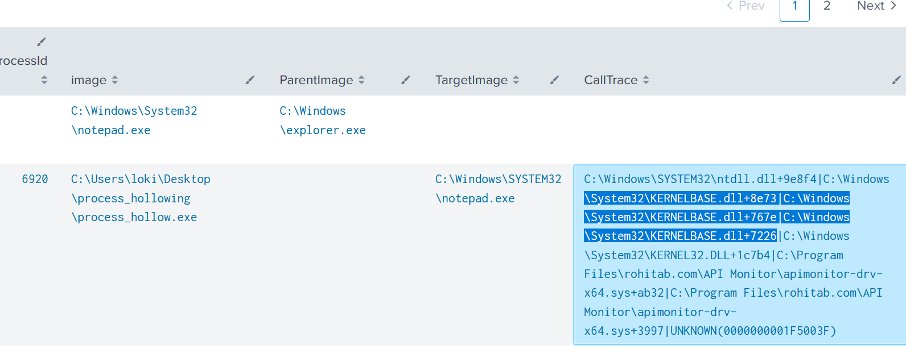
Detecting Process Hollowing. A post by Leo Bastidas from @TrustedSec exploring the popular technique, where a malicious payload is concealed within a legitimate process, and providing detailed methods for its detection and defense. Source: trustedsec.com/blog/the-night… #redteam…


Redirect any Windows TCP and UDP traffic to HTTP/Socks5 proxy github.com/InterceptSuite…
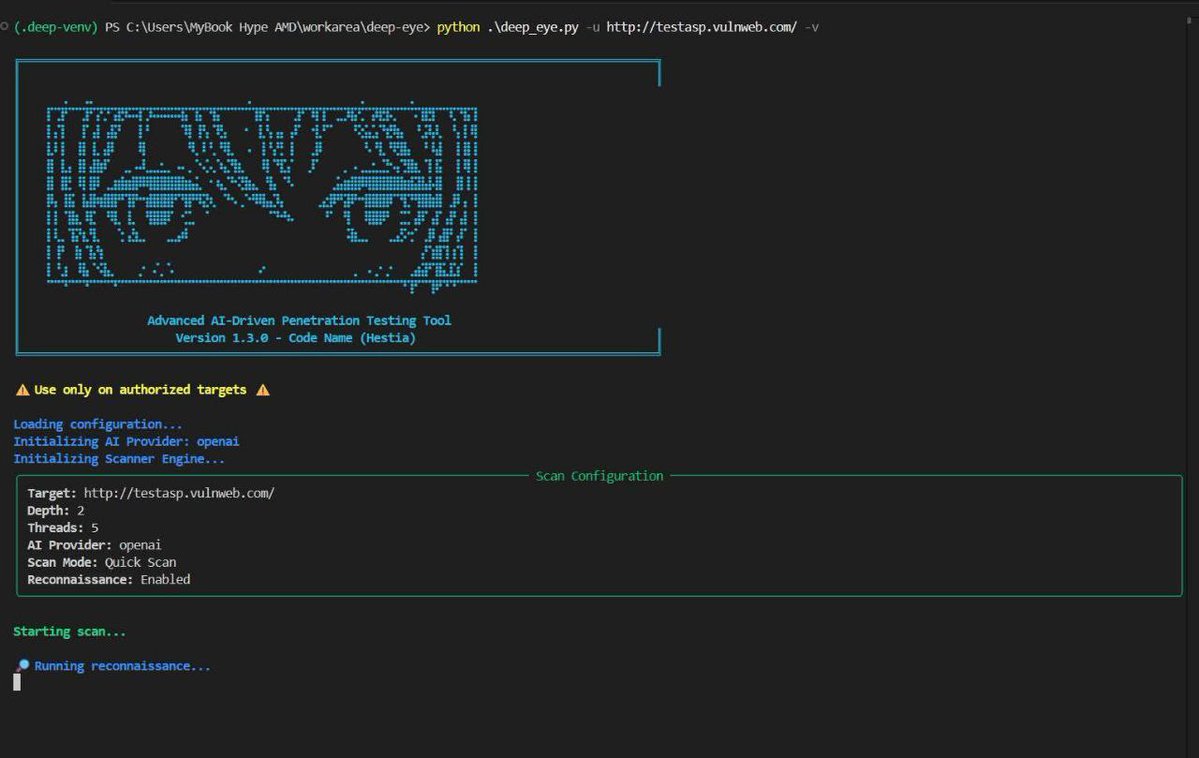
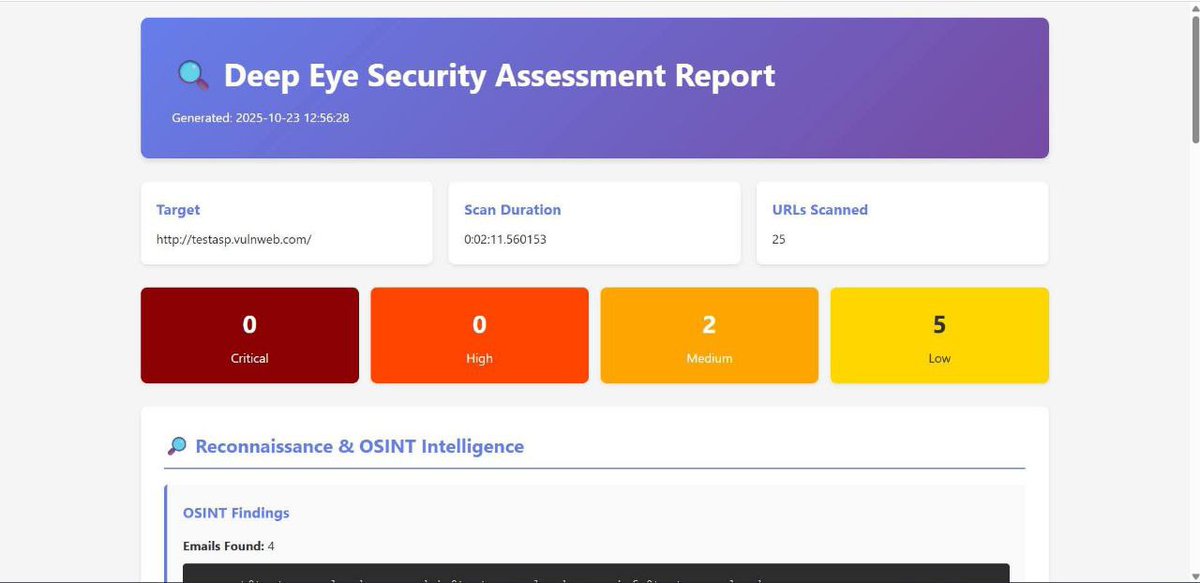
Introduce Deep-Eye Code Name (Hestia) smart automation pentest tools with 20+ mode attack. Deep-Eye all in one pentest tools with Deep OSINT And reeconize target. Scanning method have 2 mode Quick And Full-Scan. Deep-Eye support multiple AI Provider. > github.com/zakirkun/deep-…
GitHub - msalman-mufin/Nullpoint-Stealer: Nullpoint Stealer Designed To Steal Everything, And Send To Nullpoint Panel. github.com/msalman-mufin/…
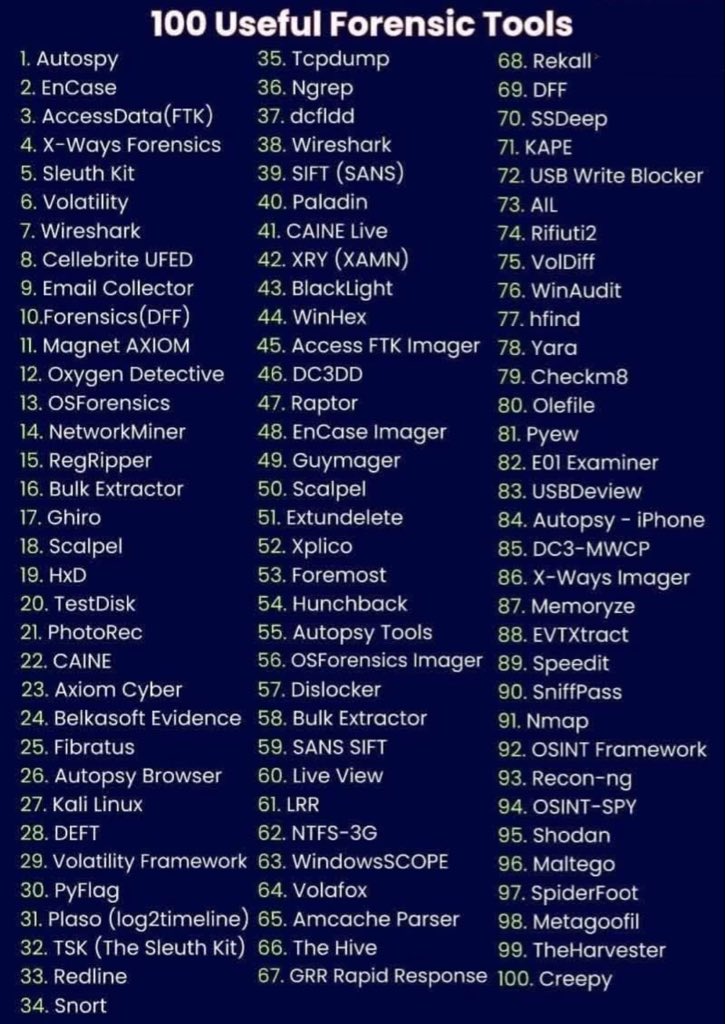
🕵️100 Useful Forensic Tools 🔖#cybersecurity #hacking #pentesting #security
These Linux commands helped me most in last 13 years of IT career Daily stuff: • ps aux | grep {process} - Find that sneaky process • lsof -i :{port} - Who's hogging that port? • df -h - The classic "we're out of space" checker • netstat -tulpn - Network connection detective…
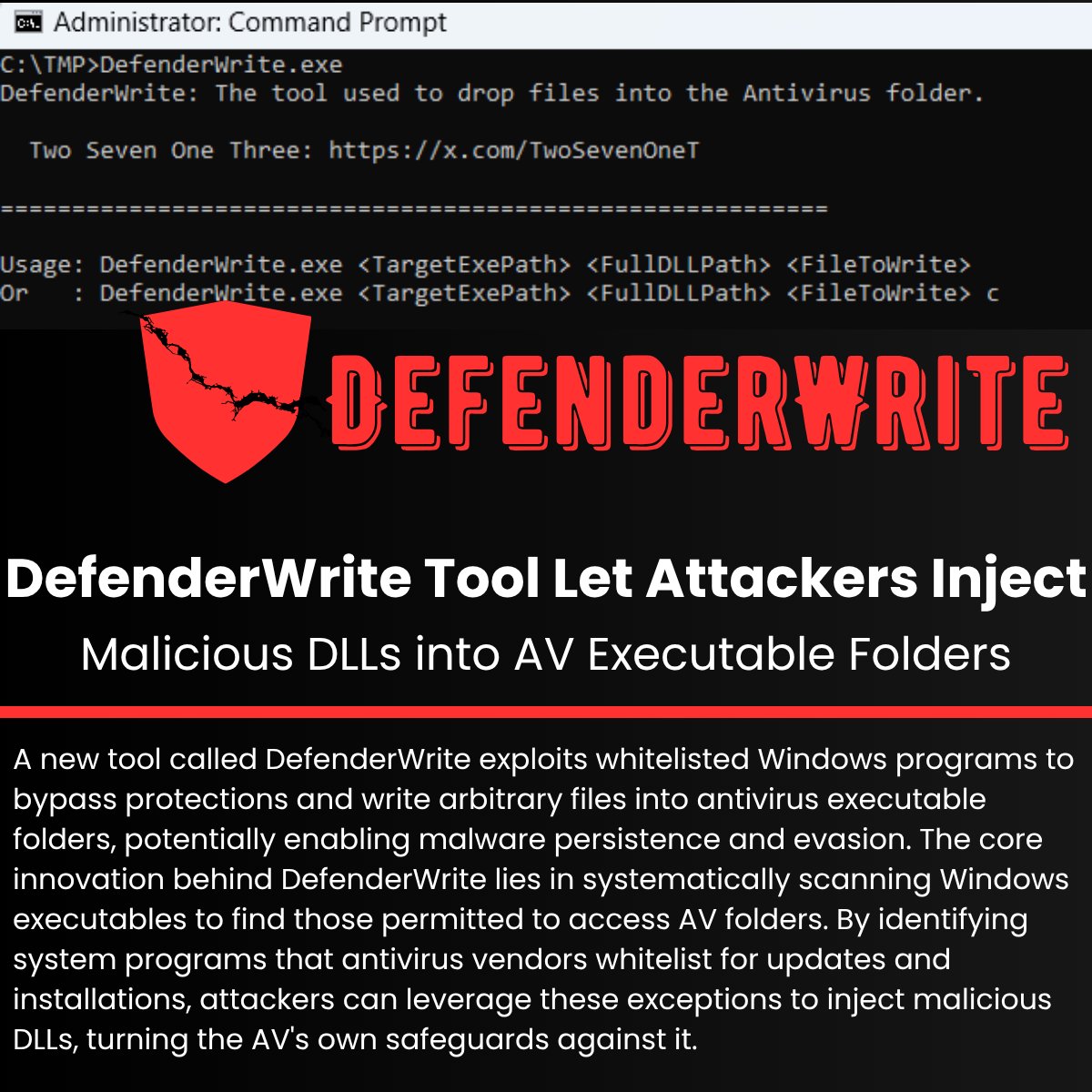
⚠️ DefenderWrite Tool Let Attackers Inject Malicious DLLs into AV Executable Folders Read more: cybersecuritynews.com/defenderwrite-… A new tool called DefenderWrite exploits whitelisted Windows programs to bypass protections and write arbitrary files into antivirus executable folders,…
Free Malware Analysis Course, covers malware concepts, malware analysis, and black-box reverse engineering techniques class.malware.re
Just a simple silly PoC demonstrating executable "exe" file that can be used like exe, dll or shellcode... github.com/Dump-GUY/EXE-o…
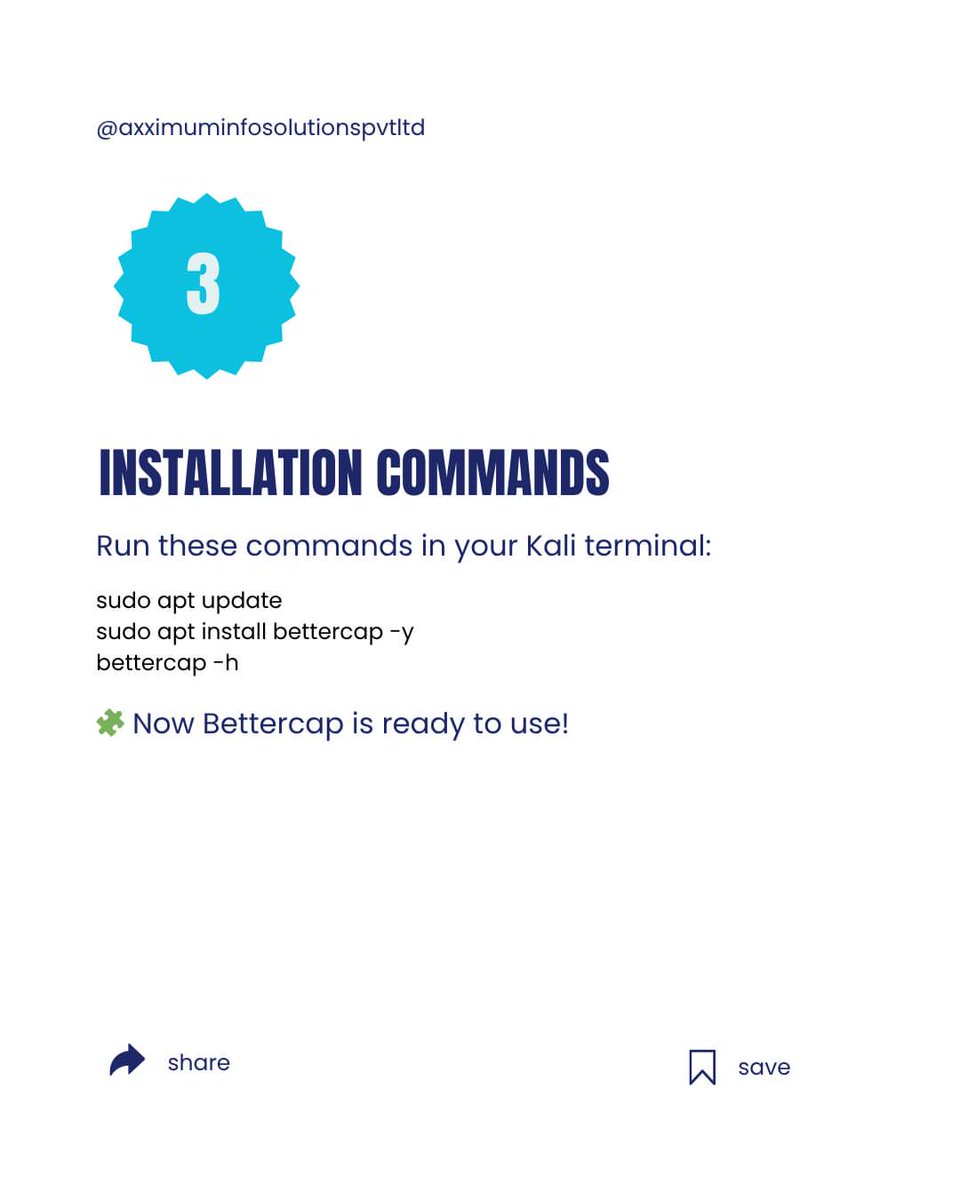
🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection



A new Zero-Click NTLM leak bypasses Microsoft's LNK patch, allowing unauthenticated NTLM hash theft on patched systems. The PoC works by exploiting UNC paths and the default shell32.dll icon reference. #NTLMleak #ZeroClick #LNKattack #Cybersecurity securityonline.info/zero-click-ntl…
GitHub - xaitax/NTSleuth: Comprehensive Windows Syscall Extraction & Analysis Framework github.com/xaitax/NTSleuth
United States 趨勢
- 1. #10SET N/A
- 2. $RDAC N/A
- 3. Good Tuesday 30K posts
- 4. Dodgers 284K posts
- 5. Freddie Freeman 79.1K posts
- 6. Jamaica 151K posts
- 7. #WorldSeries 224K posts
- 8. #tuesdayvibe 1,988 posts
- 9. Grokipedia 111K posts
- 10. Wikipedia 75.8K posts
- 11. #NationalFirstRespondersDay N/A
- 12. Klein 284K posts
- 13. $PYPL 33.8K posts
- 14. #PutThatInYourPipe N/A
- 15. USS George Washington 32.3K posts
- 16. PayPal 93.6K posts
- 17. Ohtani 147K posts
- 18. Hurricane Melissa 116K posts
- 19. Wordle 1,592 X N/A
- 20. Nelson 23.6K posts
Something went wrong.
Something went wrong.