You might like
I just published Unauthenticated user can upload an attachment at @Hacker0x01 link.medium.com/BIRb51wPUS
حسبنا الله ونعم الوكيل عند الله تجتمع الخصوم 😢💔 #طرد_السفير_الاسراييلي_من_مصر
2 war criminals hugging 🇺🇸🇮🇱

🇮🇱🇵🇸 IDF-affiliated accounts are sharing this video serve as “proof” that Hamas bombed the Gaza Baptist Hospital. Only problem? This video is from August of 2022.
כך נראה שיגור כושל של הגי'אהד האיסלמי לתוך הרצועה
Bombing a hospital is a war crime, Israel is a terrorist
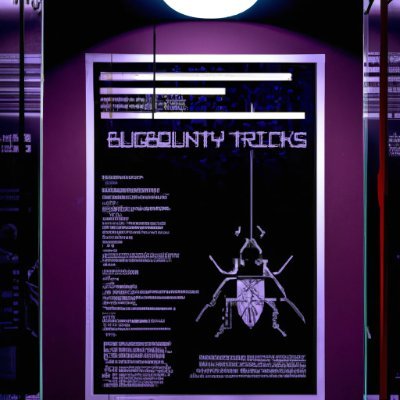
Have you ever used pastebin or codebeautify? So have developers at companies! @TakSec shows us some Google dorks that could uncover some of the data developers might have left behind on the internet! hubs.li/Q01B1Mnm0 #bugbounty #bugbountytips 👇

We found a Remote Code Execution vulnerability in every #PostgreSQL database in #IBMCloud 😱 Here is how we did it: 🧵 #HellsKeychain

Reported a critical bug to @VelasBlockchain - the issue was promptly fixed, and no funds were lost 🥳 The technical writeup can be found here: 👇🏻 🧵 mirror.xyz/orenyomtov.eth…
Knowing your target is invaluable. This is some great research on interesting flaws in Salesforce-backed websites, by @Hypn@infosec.exchange hypn.za.net/blog/2022/11/1…
Nice little-known writeup on WhatsApp exploitation: awakened1712.github.io/hacking/hackin… < technically interesting for more than one reason
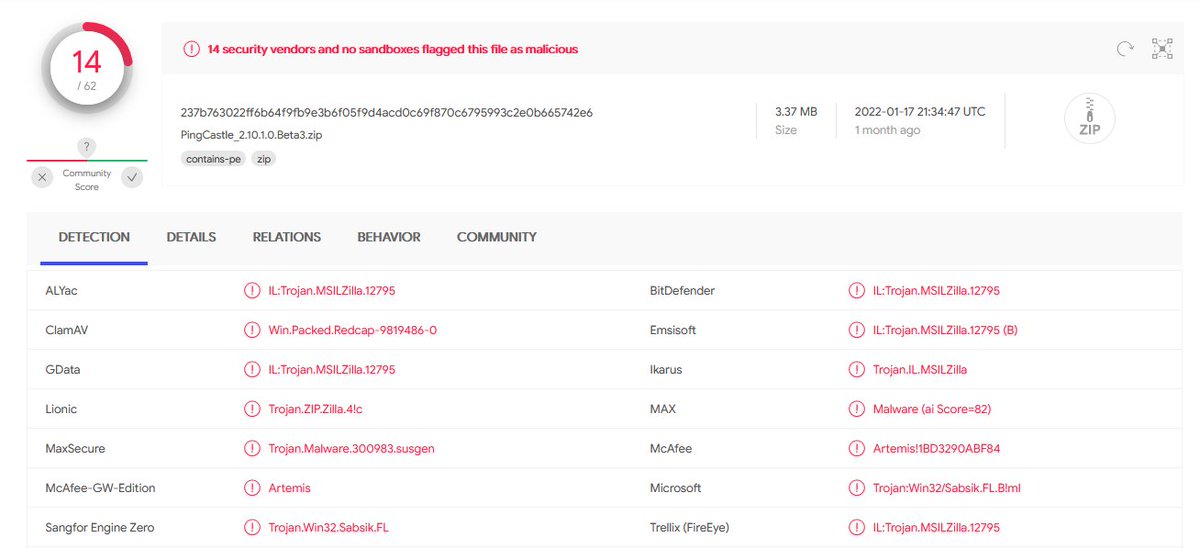
Yes, again a lot of AV is detect PingCastle Beta as malicious. Lets investigate and find the root cause. Thread 1/5
One for all & all for one ♥️
I'm raising $10,000 for @LLSusa this time around. If you have ever wanted to support me or buy me a coffee/ramen/food, please donate it to this link instead. I'll also do whatever crazy thing the top donation says. pages.lls.org/ltn/sac/sacr21…
A patch is now available for CVE-2021-33193 - the Apache HTTP/2 request line injection vulnerability I disclosed last month! It also fixes an interesting looking SSRF... httpd.apache.org/security/vulne… portswigger.net/research/http2…
Bug Bounty Info GitHub Recon using GitHub Dorks 📖 Article shahjerry33.medium.com/github-recon-i… #CyberSecurity #cybersecuritytips #Hacking #BugBounty #bugbountytip #infosec #hacker #togetherwehitharder #bugcrowd #hack #hackers #hackerone

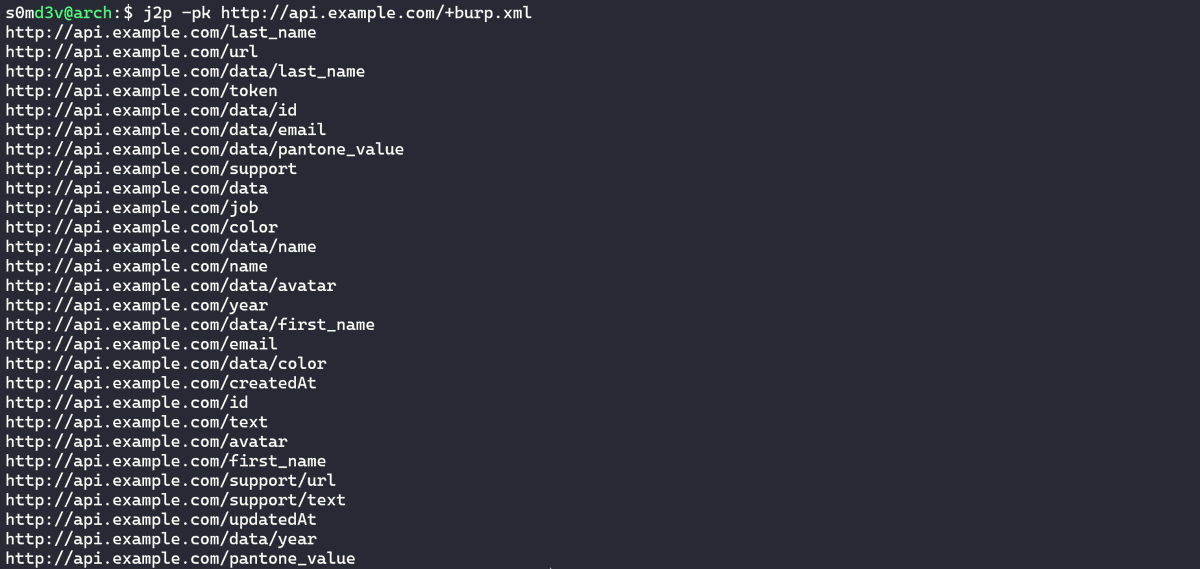
Created a tool for finding hidden endpoints, especially on APIs. It fetches JSON responses from @Burp_Suite history and creates a url paths wordlist from JSON keys. Github: github.com/s0md3v/dump/tr…
Parameter Pollution: PHP internally uses parse_str() to parse parameters so it sees the char "[" & "_" as the same. PHP by default will use the last param as valid. In cases PHP is running on backend but front end validates the param, we can smuggle fake params to php. #BugBounty

United States Trends
- 1. Pond 242K posts
- 2. Daboll 37.7K posts
- 3. Veterans Day 22.7K posts
- 4. Jimmy Olsen 2,422 posts
- 5. Schoen 19.6K posts
- 6. Zendaya 9,950 posts
- 7. Go Birds 12.7K posts
- 8. Downshift N/A
- 9. #jimromeonx N/A
- 10. #OTGala8 76.5K posts
- 11. McRib 1,150 posts
- 12. Hanoi Jane 1,366 posts
- 13. Giants 73.4K posts
- 14. Johnny Carson N/A
- 15. NCAA Tournament 1,841 posts
- 16. Biker 3,984 posts
- 17. Oreos 6,961 posts
- 18. Joe Dirt N/A
- 19. Joe Burrow 6,429 posts
- 20. Dart 23.2K posts
You might like
-
 Japz (h4nt3rx) 🕷️🏴☠️
Japz (h4nt3rx) 🕷️🏴☠️
@japzdivino -
 Vipin Panchal
Vipin Panchal
@dirtycoder0124 -
 CMD - Constantin
CMD - Constantin
@CMD_0_0 -
 Mauricio
Mauricio
@FirewallFiasco -
 Gopesh Sharma
Gopesh Sharma
@MrSharmaX -
 Yusuf Aydın
Yusuf Aydın
@h1_yusuf -
 Efkan
Efkan
@mefkansec -
 (((gamliel)))
(((gamliel)))
@Gamliel_InfoSec -
 Mukul Lohar
Mukul Lohar
@ironfisto -
 Aryan Rupala
Aryan Rupala
@Aryan_2808 -
 Scalar
Scalar
@Scalar360 -
 Shubham Pathak
Shubham Pathak
@ShubhamPthk
Something went wrong.
Something went wrong.