You might like
Another #collaboration with @D3vashishs0ni🤘🏻 We have been #awarded $6500 for #stored #xss in Apple. - #bugbounty #apple #hacking #xss #halloffame #cybersecurity #bugbountytips #Collaboration #applesecurity
Another Bounty in apple with @abhiunix #Apple #bugbounty #cybersecurity #xss #hacking #HallOfFame

Found an RCE in Google Web Designer :) Very similar to the CSS Injection to RCE found by Bálint Magyar. sudistark.github.io/2025/09/23/RCE…
Claude: Build ANY N8N AI Agent in 1 Click! 🤯 Want the JSON file? DM me.
A long time ago, i was using (Frogy Recon Tool) and the results were more than amazing now its back as 2.0 and now i like it so much github.com/iamthefrogy/fr… by the amazing @iamthefrogy Just want to share here if someone wants to check it #bugbountytips #bugbountytip
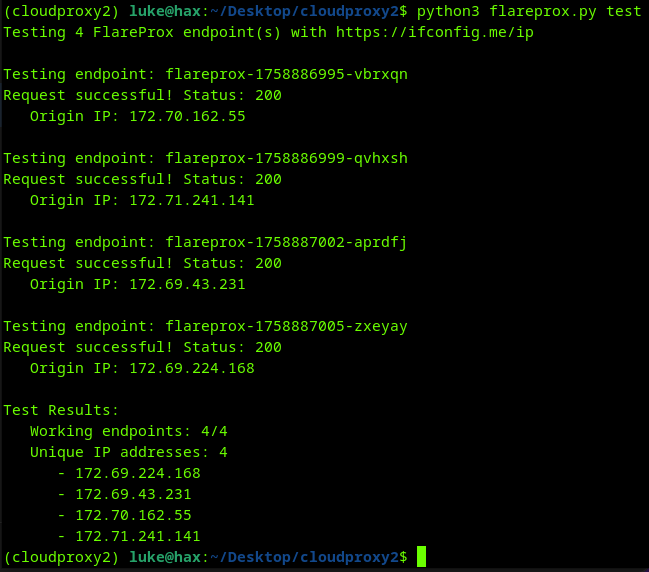
I just released Flareprox 🔥 A Cloudflare based Fireprox alternative that allows you to route HTTP traffic through Cloudflare, to gain mostly unique IP Addresses, to avoid detection and blocks.


How to extract subdomains from an ASN using dnsx! ⌨️ echo <ANS> | dnsx -silent -ro -ptr (🔗 link to dnsx in the comments) #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
Looking for a recon methodology on a web app ?? Look no further... 🔗👉🏼admapp.com/wapps/1-recon-… This is a graphical cheat-sheet that displays ways to find a variety of potential attack paths. Covers the following & more: ✔️ Tech Stack ✔️ Asset Discovery ✔️App Functionality

Compiled Resources for Penetration Testing 1) Android Penetration Testing lnkd.in/d5smdWVZ 2) iOS Penetration Testing lnkd.in/dTnBNvyR 3) Network Penetration Testing lnkd.in/dVG5GdYR 4) API Penetration Testing lnkd.in/dRJGbAn9 5) Web App…
JShunter JShunter is a command-line tool designed for analyzing JavaScript files and extracting endpoints. This tool specializes in identifying sensitive data, such as API endpoints and potential security vulnerabilities, making it an essential resource for developers, bug…

🌊 SYSTEM PROMPT LEAK 🌊 Here's the Codex system prompt!! 🤗 OpenAI's new model, GPT-5-Codex, is CRUSHING agentic coding benchmarks, with a big leap on code refactoring tasks. Looking forward to experimenting more with this one in the field! PROMPT: """ You are ChatGPT, a large…
Someone make a subdomains database containing 1.6 billion subdomains scrapped from multiple public (and private) sources. This database is now public and FREE and can be queried on the following website. - dash.pugrecon.celes.in #infosec #cybersec #bugbountytips

𝗘𝘃𝗲𝗿 𝘄𝗼𝗻𝗱𝗲𝗿 𝗵𝗼𝘄 companies like Rippling, Amazon, or Meta build secure products at scale? 𝘔𝘰𝘴𝘵 𝘵𝘦𝘢𝘮𝘴 𝘸𝘢𝘪𝘵 𝘧𝘰𝘳 𝘣𝘳𝘦𝘢𝘤𝘩𝘦𝘴. But the smart ones? They start with 𝗍𝗁𝗋𝖾𝖺𝗍 𝗆𝗈𝖽𝖾𝗅𝗂𝗇𝗀 🧵

Our v1 open source solution to this problem: open.edison.watch Sign up to newsletter to keep up to date with how to secure these: blog.edison.watch
github.com
GitHub - Edison-Watch/open-edison: 🔐 Firewall Your Data, Control Agents. Prevent agent data...
🔐 Firewall Your Data, Control Agents. Prevent agent data exfiltration. Gain visibility into AI's interactions with your data / systems of record / existing software. https://discord.gg/tXjA...
We got ChatGPT to leak your private email data 💀💀 All you need? The victim's email address. ⛓️💥🚩📧 On Wednesday, @OpenAI added full support for MCP (Model Context Protocol) tools in ChatGPT. Allowing ChatGPT to connect and read your Gmail, Calendar, Sharepoint, Notion,…
The OSINT Tool That Turns Google Into an Investigation Engine.

BREAKING: X just exposed the EXACT algorithm that decides who goes viral… And I just reverse-engineered it into a custom trained GPT: → The exact formula for viral posts → FYP selection patterns (from X) → Engagement thresholds that trigger boost → Which signals get you…

With the new #GSTCouncil 's reforms it's even important to protect our critical infrastructure. A short writeup of how a data leak in GST Portal could lead to Indian stock market manipulation ( @NSEIndia / @BSEIndia ) aseem-shrey.medium.com/manipulating-i… #dataleak #BugBounty #Hacking
a senior engineer at google just dropped a 400-page free book on docs for review: agentic design patterns. the table of contents looks like everything you need to know about agents + code: > advanced prompt techniques > multi-agent patterns > tool use and MCP > you name it

🧃 SYS PROMPT LEAK 🧃 CHATGPT O1 SYSTEM INSTRUCTIONS!! It utilizes a hierarchical instruction framework as expected, composed of system-level directives, developer (AKA “user” or "custom") instructions, and end-user inputs, prioritized in that order (though the hierarchy can be…
United States Trends
- 1. South Carolina 28.7K posts
- 2. Texas A&M 27.6K posts
- 3. Shane Beamer 3,780 posts
- 4. Ryan Williams 1,309 posts
- 5. Michigan 44.5K posts
- 6. Sellers 13.9K posts
- 7. Ty Simpson 1,733 posts
- 8. Northwestern 7,282 posts
- 9. Marcel Reed 4,832 posts
- 10. Heisman 7,336 posts
- 11. #EubankBenn2 10.8K posts
- 12. #GoBlue 3,862 posts
- 13. Oklahoma 18.5K posts
- 14. Sherrone Moore 1,037 posts
- 15. Underwood 3,931 posts
- 16. Mateer 1,328 posts
- 17. College Station 2,966 posts
- 18. #GigEm 2,173 posts
- 19. Nyck Harbor 3,437 posts
- 20. Elko 5,382 posts
You might like
-
 ~Ankit Tiwari
~Ankit Tiwari
@Debian_Hunter -
 j3ssie (Ai Ho)
j3ssie (Ai Ho)
@j3ssiejjj -
 Aditya sharma 🇮🇳
Aditya sharma 🇮🇳
@Assass1nmarcos -
 Ninad Mathpati 🇮🇳
Ninad Mathpati 🇮🇳
@Ninad_Mathpati -
 StarKrish
StarKrish
@PD_5ive -
 Debangshu 🇮🇳🥷
Debangshu 🇮🇳🥷
@ThisIsDK999 -
 Hugo Picanço
Hugo Picanço
@hugopicanzo -
 @v!b$123!
@v!b$123!
@vibs123i -
 Sharik Khan
Sharik Khan
@4non_Hunter -
 bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l
bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l
@idontkn85445458 -
 Shubham Patel
Shubham Patel
@Shubham_4500 -
 Renzi 🇧🇷
Renzi 🇧🇷
@Renzi25031469 -
 r00tz 🇮🇳
r00tz 🇮🇳
@yaser_s -
 Jadek Mark
Jadek Mark
@mase289 -
 Raju Kumar
Raju Kumar
@MrCyberwarrior
Something went wrong.
Something went wrong.







































































































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)