Jayesh Thakur
@h4z3x04
i use arch linux btw...!!
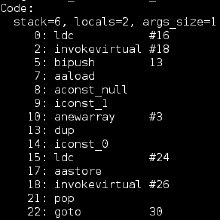
Somebody asked me recently if you can exploit an XSS scenario like this: x.y(1,INJECT); where x and y are not defined. You cannot break out of the script tag, but you can break out of the function call. I tried everything I could think of to abuse error handling and hoisting…
If you're a beginner in #infosec, amidst the AI FOMO, some tips :- - Learn JavaScript!! (I can't stress this enough) - Expose yourself to a variety of technologies. - Read a lot of writeups(helps build pattern-matching skill) - Try to do hard things and Don't get comfortable.
Hello everyone ♥ a little bit write-up of #bugbountytip #bugbountytips I am going to write here ..... Title: getting unauthorized access on 3rd party's/workspaces & and building your checklist for quickly locating bugs there via massive recon we know that its helpful to look…

.@gr3pme's threat modelling methodology when approaching new targets. The goal is to list every possible attack vector, regardless of likelihood, as a reference for future exploration. This is a powerful yet extremely underrated skill for bug hunters! Take note!

What’s the current best cli based tech/stack identification / fingerprinting tooling out there today? Used to love github.com/urbanadventure… are there any newer and better tools?
Yesterday, I tried to find out where the Deepseek servers are located, but I couldn't because they are Cloudflare-protected. Just now, someone randomly sent me a link to: "CF-Hero is a reconnaissance tool that uses multiple data sources to discover the origin IP addresses of…

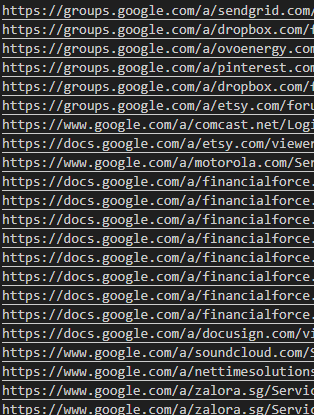
How to find SQL Injection at scale, targeting URLs 👇🔥 Credits: @0x3n0 #recontips #bugbountytips #bugbounty #AttackSurface #sqli #sqlmap

Critical logic issue lead to bypass file upload filtering #bugbountytip #infosec #bugbountytips #bugbounty hamzadzworm.medium.com/critical-logic…
🚨 Comprehensive Web Application Security Checklist 🧾 Source - securitycipher.com/web-applicatio… #bugbounty #bugbountytips #bugbountytip #hackerone #bugcrowd #infosec #cybersecurity #pentesting #redteam #informationsecurity #securitycipher #technology #coding #code #recon #ai #llm…

Just released my blog post "Bidding Like a Billionaire - Stealing NFTs With 4-Char CSTIs"! It's about a very impactful and technically interesting client-side bug I found in a major NFT site. matanber.com/blog/4-char-cs…
Understanding EVERY Token in Entra ID 🔎 Not all tokens are equal. There are many different types with different uses and benefits. In this blog, I break down each token and what they are used for and which tokens are the most "valuable" for an attacker to obtain. Full blog…

Learn how to conceal payloads in URL credentials and abuse them for DOM XSS and DOM Clobbering. portswigger.net/research/conce…
🚨Ilya Sutskever finally confirmed > scaling LLMs at the pre-training stage plateaued > the compute is scaling but data isn’t and new or synthetic data isn’t moving the needle What’s next > same as human brain, stopped growing in size but humanity kept advancing, the agents and…


Almost 700 hours into bug bounties. Out of 40 programs I spent time on, I only got paid on 5. There's a pattern I noticed and I think it's worth sharing. Here's my analysis: (a thread - 1/x) #bugbounty #bugbountytips

Ever wonder why some people succeed while others don't? 🙋 It all comes down to taking action. 🙄 Most people have ambitions and goals, but very few actually take the necessary steps to achieve them. Let's dive into this concept 🧵👇

Becoming a pro in finding client-side bugs is simple. Not easy, but simple. 1. Go through a JS tutorial and understand the basics. 2. Ready everything on this blog 8x until you understand it: ysamm.com 3. Read JS for Hackers by @garethheyes 4x Then go hack stuff
Just released the write-up for CVE-2024-4367, a bug I found recently in PDF.js (and hence in Firefox), resulting in arbitrary JavaScript execution when opening a malicious PDF. codeanlabs.com/blog/research/…
Hey guys, I just published How a Single Parameter Led to Two ATO Cases link.medium.com/WY5CIcbSHJb #ItTakesACrowd #EthicalHacking #CyberSecurity #SaturdayVibes
link.medium.com
How a Single Parameter Led to Two ATO Cases
Hey guys, Today, I’m excited to share an intriguing story about how a single parameter in an application led to two account takeover cases…
United States Trends
- 1. #CARTMANCOIN 1,572 posts
- 2. Broncos 64.6K posts
- 3. Broncos 64.6K posts
- 4. yeonjun 191K posts
- 5. Bo Nix 17.8K posts
- 6. Geno 18.2K posts
- 7. $SMILEY N/A
- 8. Sean Payton 4,682 posts
- 9. Kenny Pickett 1,501 posts
- 10. daniela 38.5K posts
- 11. #TNFonPrime 3,976 posts
- 12. #criticalrolespoilers 4,741 posts
- 13. Chip Kelly 1,947 posts
- 14. Bradley Beal 3,391 posts
- 15. Jalen Green 7,168 posts
- 16. TALK TO YOU OUT NOW 25.2K posts
- 17. Pete Carroll 1,914 posts
- 18. Kehlani 8,990 posts
- 19. Jeanty 6,481 posts
- 20. byers 28.7K posts
Something went wrong.
Something went wrong.