قد يعجبك
#exploit #Kernel_Security Ksmbd Vulnerability Research Part 1 - CVE-2024-50283, CVE-2024-50285, CVE-2024-50286 - blog.doyensec.com/2025/01/07/ksm… Part 2 - Fuzzing Improvements and Vulnerability Discovery - blog.doyensec.com/2025/09/02/ksm… Part 3 - Exploiting CVE-2025-37947 -…
Introduction to windows shellcode development series. Part 1 :securitycafe.ro/2015/10/30/int… Part 2 :securitycafe.ro/2015/12/14/int… Part 3 :securitycafe.ro/2016/02/15/int…
GitHub - MorDavid/BruteForceAI: Advanced LLM-powered brute-force tool combining AI intelligence with automated login attacks github.com/MorDavid/Brute…
Jann Horn, Google Project Zero 👀 iOS/macOS googleprojectzero.blogspot.com/2025/09/pointe…
[Research] Starting Chrome Exploitation with Type Confusion 101 ^-^☆ Part 3. hackyboiz.github.io/2025/09/26/OUY… Hello — OUYA77 here. While writing my Chrome research post I found there’s more related material than I expected, so I’ve been debating how much to include and how deep to go.…
![hackyboiz's tweet image. [Research] Starting Chrome Exploitation with Type Confusion 101 ^-^☆ Part 3.
hackyboiz.github.io/2025/09/26/OUY…
Hello — OUYA77 here. While writing my Chrome research post I found there’s more related material than I expected, so I’ve been debating how much to include and how deep to go.…](https://pbs.twimg.com/media/G1whiSgaAAElRyi.jpg)
ByteCaster 🔥 – my new tool for payload encryption, obfuscation, and conversion to byte arrays. github.com/Print3M/ByteCa… - 14 output formats: C, Rust, C#, Nim, Go... - AES-256, RC4, XOR supported - IPv4Fuscation, MACFuscation, base64/32 #malware #redteam #security #infosec


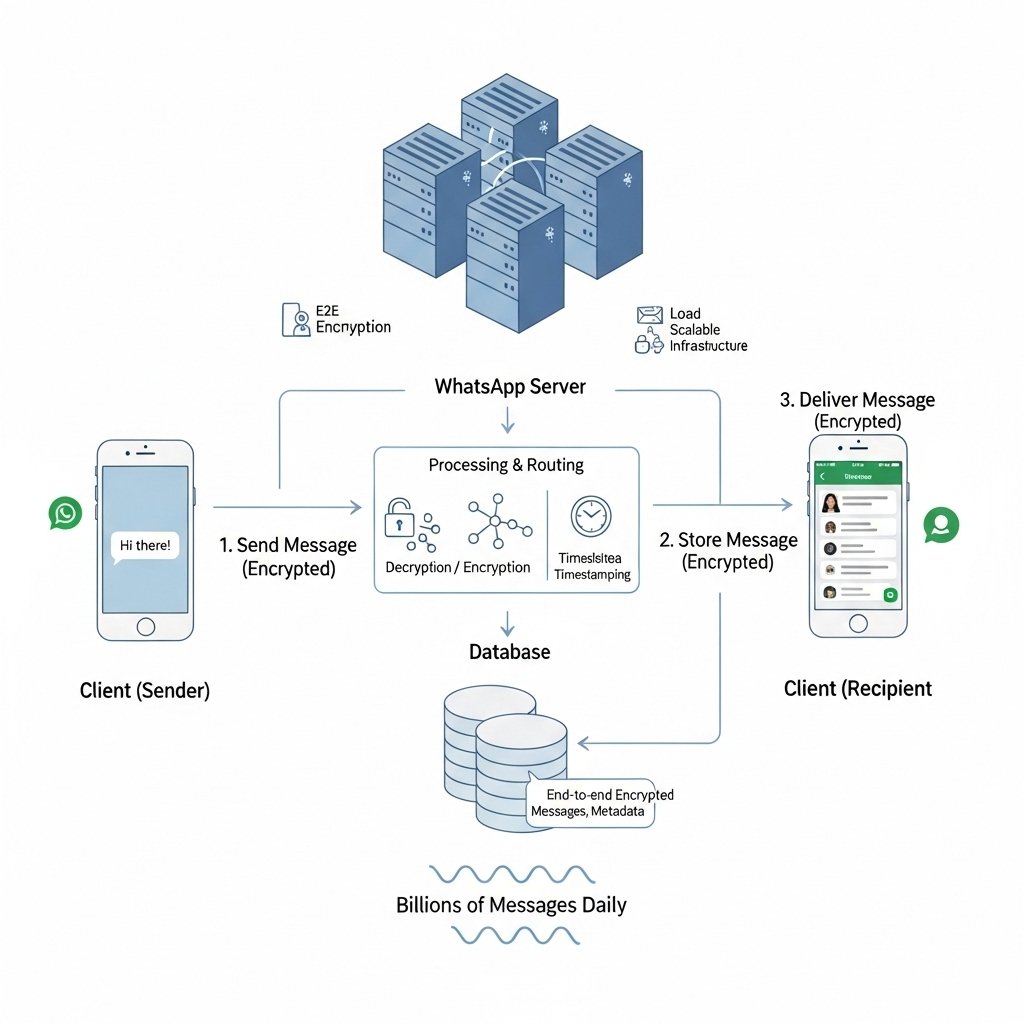
𝗛𝗼𝘄 𝗱𝗼𝗲𝘀 𝗪𝗵𝗮𝘁𝘀𝗔𝗽𝗽 𝗵𝗮𝗻𝗱𝗹𝗲 𝗯𝗶𝗹𝗹𝗶𝗼𝗻𝘀 𝗼𝗳 𝗺𝗲𝘀𝘀𝗮𝗴𝗲𝘀 𝗲𝘃𝗲𝗿𝘆 𝗱𝗮𝘆? WhatsApp is built on a 𝗵𝗶𝗴𝗵𝗹𝘆 𝗼𝗽𝘁𝗶𝗺𝗶𝘇𝗲𝗱 𝗲𝘃𝗲𝗻𝘁-𝗱𝗿𝗶𝘃𝗲𝗻 𝗮𝗿𝗰𝗵𝗶𝘁𝗲𝗰𝘁𝘂𝗿𝗲, where services for messaging, calls, media sharing, status, and…
Malware development series - advanced obfuscation with LLVM and template metaprogramming 0xpat.github.io/Malware_develo…

Eternal-Tux: Crafting a Linux Kernel KSMBD 0-Click RCE Exploit from N-Days. willsroot.io/2025/09/ksmbd-…

Say hello to Eternal Tux🐧, a 0-click RCE exploit against the Linux kernel from KSMBD N-Days (CVE-2023-52440 & CVE-2023-4130) willsroot.io/2025/09/ksmbd-… Cheers to @u1f383 for finding these CVEs + the OffensiveCon talk from gteissier & @laomaiweng for inspiration!
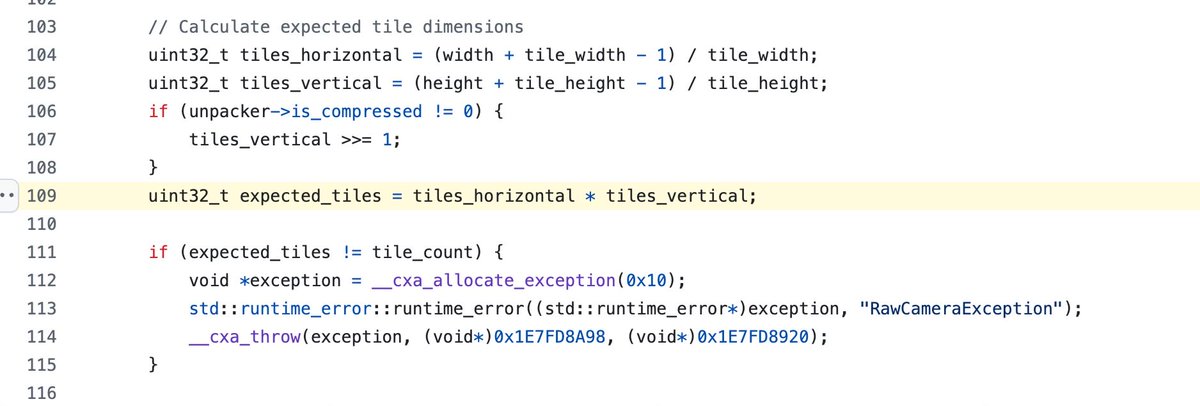
This is the iOS DNG image RawCamera parsing (CVE-2025-43300) recent used whatsapp 0click. github.com/qriousec/rawca… ( Repo included others relevant image format parser as well, look pretty auditable! )
I’ve brought you a real iOS MTE bypass retrospectively: the overflow happens inside the co-processor (no MTE), then abuses trusted RPCs to gain kernel R/W — sidestepping MTE on the AP entirely. googleprojectzero.blogspot.com/2022/06/curiou…

This is why we can't have nice things - starlabs.sg/blog/2023/07-p… - there's a nice kernel feature which is disabled in many kernels bcoz it provides a heap spraying gadget :c Thx @patryk4815 for showing me this; Fwiw Golang implemented this github.com/golang/go/issu… too (screenshot)


Reverse engineering of Apple's iOS 0-click CVE-2025-43300 blog.quarkslab.com/patch-analysis…
#Research #cryptography "A Formal Analysis of Apple's iMessage PQ3 Protocol", 2025. ]-> formal models and proofs of Apple's iMessage PQ3 protocol - zenodo.org/records/147106… // a detailed formal model of PQ3, a precise specification of its fine-grained security properties, and…
"A Full-Chain Exploit of an Unfused Qualcomm Device" hhj4ck.github.io/qualcomm/2025/… #infosec

From Chrome renderer code exec to kernel with MSG_OOB Jann Horn @tehjh posted an article about exploiting CVE-2025-38236, a UAF in the UNIX domain sockets: googleprojectzero.blogspot.com/2025/08/from-c…
My timeline is full of 𝗶𝗢𝗦 𝟬-𝗰𝗹𝗶𝗰𝗸 𝗲𝘅𝗽𝗹𝗼𝗶𝘁 again. If you’re new to these bugs, check out my write-up on my own fuzzing experience with 𝗜𝗺𝗮𝗴𝗲𝗜𝗢 from last year. r00tkitsmm.github.io/fuzzing/2024/0…
LPE / RCE Exploits for various vulnerable "Bloatware" products: ⭐️1-click RCE in Asus DriverHub ⭐️LPE in MSI Centre (CVE-2025-27812, CVE-2025-27813) ⭐️LPE / RCE in Acer Control Centre (CVE-2025-5491) ⭐️LPE in Razer Synapse 4 (CVE-2025-27811) github.com/sensepost/bloa…
United States الاتجاهات
- 1. Chiefs 105K posts
- 2. Branch 31.8K posts
- 3. Mahomes 32.3K posts
- 4. #TNABoundForGlory 53.3K posts
- 5. #LoveCabin 1,054 posts
- 6. LaPorta 10.4K posts
- 7. #LaGranjaVIP 60.1K posts
- 8. Bryce Miller 4,367 posts
- 9. Goff 13.5K posts
- 10. Kelce 16.2K posts
- 11. Rod Wave 1,079 posts
- 12. Dan Campbell 3,698 posts
- 13. #OnePride 6,344 posts
- 14. Red Cross 29.9K posts
- 15. #DETvsKC 4,923 posts
- 16. Butker 8,432 posts
- 17. Mariners 48.8K posts
- 18. Pacheco 4,919 posts
- 19. JuJu Smith 4,034 posts
- 20. Baker 54.3K posts
قد يعجبك
-
 Akai 🇻🇳
Akai 🇻🇳
@KMA_Akai -
 wildcat
wildcat
@tacbliw -
 Exploit Pack
Exploit Pack
@Exploit_Pack -
 RedPacket Security
RedPacket Security
@RedPacketSec -
 Quang Nguyen
Quang Nguyen
@sovietw0rm -
 Luca Cecilioni
Luca Cecilioni
@HiThisIsLuca -
 Kostya Kortchinsky
Kostya Kortchinsky
@crypt0ad -
 ThreatABLE
ThreatABLE
@threatable -
 Syler
Syler
@SylerClayton -
 trustnobody
trustnobody
@l_codein -
 Ryan Mangan
Ryan Mangan
@RyMangan -
 윤재형
윤재형
@onnoveath -
 Shikaree_Hunter
Shikaree_Hunter
@Shikaree_Hunter -
 Lê Văn Hùng
Lê Văn Hùng
@iam_hscorpion -
 Deepak Goswami (जय शिव शक्ति)
Deepak Goswami (जय शिव शक्ति)
@deepakjgoswami
Something went wrong.
Something went wrong.