mssoffsec
@r0g3rmr3n00b
Proud Indian
Tal vez te guste
Another 4-digit reward with @0x_rood ! ❤️ 1) Got a new asset alert from @profundisio 2) Found an “authorized users only” panel 3) Checked JS files and discovered an API key 4) Mapped API endpoints and confirmed the key worked 5) Was able to read, upload, and delete files +…

Q1, Q2 and Q3 2025 were fine, Q1 2025 ~$100K Q2 2025 ~$100K Q3 2025 ~$115K Q4 2025 goal is $50K or more, We will see👀 Working_On_it I need more focus and energy, New Ideas and Strategy also. #BugBounty #HackerOne #BugBountyHunter

How to extract subdomains from an ASN using dnsx! ⌨️ echo <ANS> | dnsx -silent -ro -ptr (🔗 link to dnsx in the comments) #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
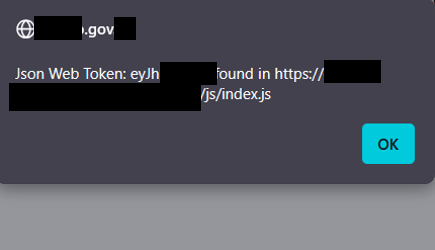
I LOVE TruffleHog browser extension 💣💣💣 Simply just browsing the web and got a serious bug without even trying 😎 I just got an admin on a government website 😆


Bug bounty life tips: - Triage downgrades your report? Ignore it, comments won’t save you. - Company says “aware of this issue”? Skip, no one helps. - CSRF and IDOR = same (in their eyes)? Skip, you’re “wrong.” - They fix your sqli while program suspended? Skip, you lose. Skip..
I submitted 5 critical reports in 2 hours due to 2 bugs. 1- The first mistake is when you add slach at the end it will bypass authentication - /api/x/x --- > 401 Unauthorized - /api/x/x/ -- > 200 Ok (2/1) #bugbounty #hackerone
I've made over 100k on SSRF vulnerabilities. They aren't always as simple as pointing it at localhost or AWS Metadata service. Here are some tricks I've picked up over the past 5 years of web app testing:
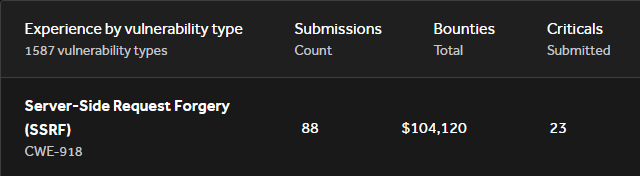
follow @hacker_ (and @boringmattress) top:
I've made $500k+ from SSRF vulnerabilities. Here are my tricks:
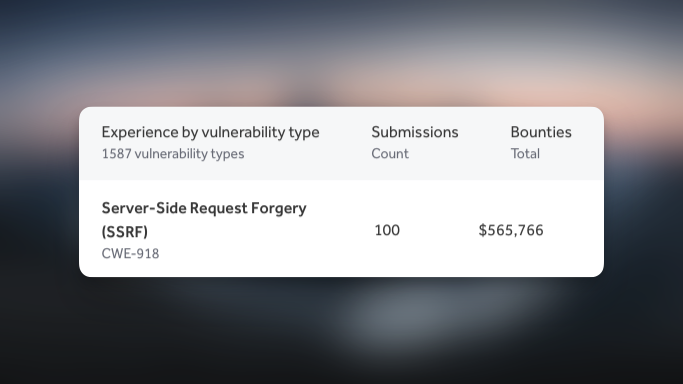
API-specific wordlists for fuzzing hidden routes & endpoints🚀 wordlists-cdn.assetnote.io/data/automated/

150$ - Info Disclosure on GoPro!⚡️ 1. In-Depth Subd Enum. 2. cat allsubs.txt | httpx -mc 200 > working.txt 3. nmap -iL working.txt -p0-65535 -oN fullscan.txt 4. dirsearch -l nmap.txt -w <wordlist> -x <status codes> -r -e <extensions> 5. Found .txt file #bugbountytip #bugbounty

Unauthenticated Access to Sensitive Customer Data via Google Dorking How I did it: - During recon, I used the dork: site:*.target.* "date of birth" ext:pdf - Found a PDF file exposing customer data. - Noticed an ID in the URL. - By changing the ID, I could access other data.




12 API hacking bug bounty tips you must try on your target! 😎 🧵 👇

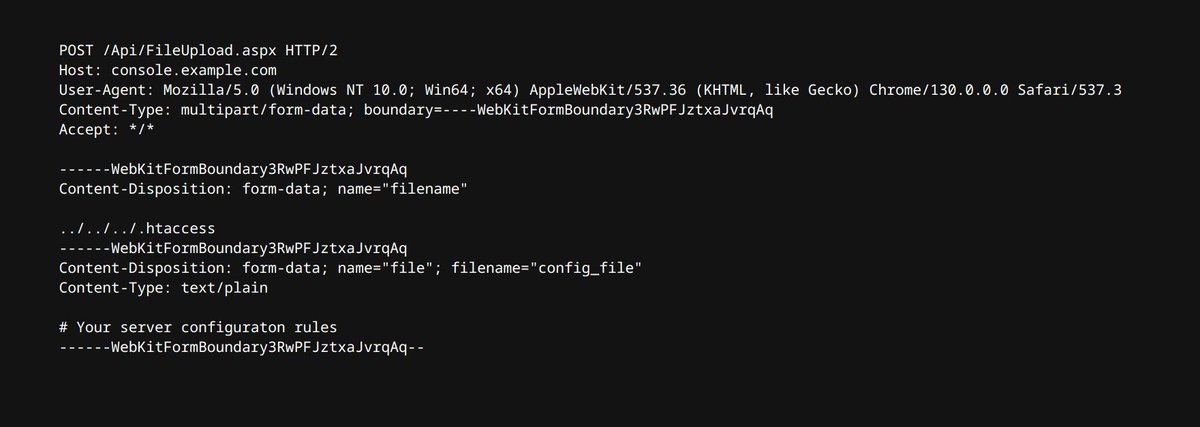
🔁 File uploads are almost everywhere... Sometimes, a simple validation mistake can result in a high-severity finding (such as RCEs) 🤠 In our technical article, we documented a few cool tricks you could try next time you're testing a file upload feature! Link in next post! 👇
redacted[.]com/ --> [302]❌ redacted[.]com/app/api/doc/ --> [200 OK] ✅ Bypassed the 302 and hit API doc gold! #bugbountytips #BugBounty
![arshiyaiha's tweet image. redacted[.]com/ --&gt; [302]❌
redacted[.]com/app/api/doc/ --&gt; [200 OK] ✅
Bypassed the 302 and hit API doc gold!
#bugbountytips #BugBounty](https://pbs.twimg.com/media/Gyu7KHRWgAAXAeY.jpg)
Bug Bounty Tips (1/2) 1- Add users with different roles in your company to the system. 2- Log in as a low-authority user in the incognito tab and log in as a high-authority account in the normal tab for role isolation. #BugBounty #bugbountytips

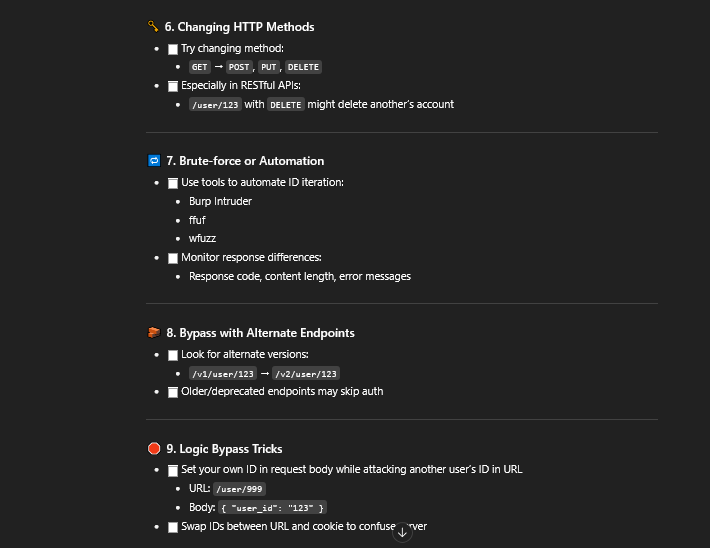
Try this out on your next target! Some more gold from the guys at @ctbbpodcast! 🔥

~IDOR bypass techniques New video out too! youtu.be/JNvnCojTAvI #bugbounty



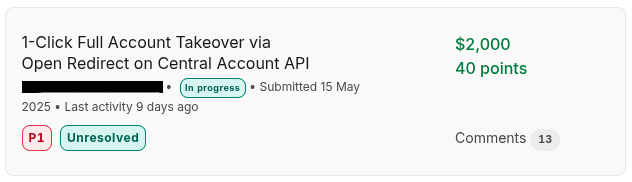
A simple open redirect can wreak havoc. Simple open redirect -> misconfigured OAuth authentication flow -> privilege abuse using Amazon Cognito token #bugbounty #bugcrowd
United States Tendencias
- 1. Chiefs 110K posts
- 2. Branch 35.2K posts
- 3. Red Cross 45.1K posts
- 4. Mahomes 34.1K posts
- 5. #LaGranjaVIP 77.7K posts
- 6. #TNABoundForGlory 57.6K posts
- 7. #LoveCabin 1,283 posts
- 8. Binance DEX 5,171 posts
- 9. Rod Wave 1,486 posts
- 10. Bryce Miller 4,547 posts
- 11. Air Force One 48K posts
- 12. Dan Campbell 3,994 posts
- 13. Goff 13.8K posts
- 14. #OnePride 6,445 posts
- 15. LaPorta 11.3K posts
- 16. Kelce 16.9K posts
- 17. Eitan Mor 11.8K posts
- 18. Tom Homan 79.2K posts
- 19. Matan Angrest 10.9K posts
- 20. Alon Ohel 11.8K posts
Tal vez te guste
-
 Ved Parkash
Ved Parkash
@v3d_bug -
 D33p4k
D33p4k
@BeingN00b -
 Samuel V.
Samuel V.
@sign3tsh3l1 -
 Jopraveen
Jopraveen
@jopraveen18 -
 Palani
Palani
@impalanichamy -
 Dhanesh Sivasamy
Dhanesh Sivasamy
@DhaneshSivasamy -
 வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
@veeppiaar -
 Jeya Seelan
Jeya Seelan
@rootxjs -
 🐝 T3xy45
🐝 T3xy45
@RegisDeldicque -
 Aswin Thambi Panikulangara
Aswin Thambi Panikulangara
@r0074g3n7 -
 Guhan Raja
Guhan Raja
@havocgwen -
 hs_0x_
hs_0x_
@hs_0x_ -
 mubassirpatel
mubassirpatel
@Mubassirpatel1 -
 Game0v3r
Game0v3r
@kabilan1290 -
 Tu$har
Tu$har
@iamtusharvyas
Something went wrong.
Something went wrong.



































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)