mssoffsec
@r0g3rmr3n00b
Proud Indian
You might like
I asked 10+ top bug hunters who made over $500k+ about their secrets. Here’s what they said: 1. They work insanely hard (280+ hrs/month) even after earning millions. 2. They master 1–3 programs deeply. 3. Speed matters. Never break your momentum. 1/n
Another 4-digit reward with @0x_rood ! ❤️ 1) Got a new asset alert from @profundisio 2) Found an “authorized users only” panel 3) Checked JS files and discovered an API key 4) Mapped API endpoints and confirmed the key worked 5) Was able to read, upload, and delete files +…

Q1, Q2 and Q3 2025 were fine, Q1 2025 ~$100K Q2 2025 ~$100K Q3 2025 ~$115K Q4 2025 goal is $50K or more, We will see👀 Working_On_it I need more focus and energy, New Ideas and Strategy also. #BugBounty #HackerOne #BugBountyHunter

How to extract subdomains from an ASN using dnsx! ⌨️ echo <ANS> | dnsx -silent -ro -ptr (🔗 link to dnsx in the comments) #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
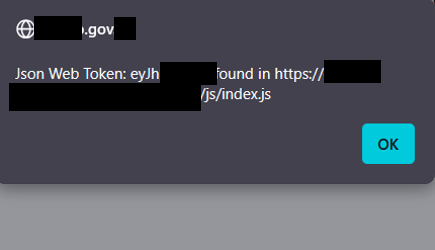
I LOVE TruffleHog browser extension 💣💣💣 Simply just browsing the web and got a serious bug without even trying 😎 I just got an admin on a government website 😆


Bug bounty life tips: - Triage downgrades your report? Ignore it, comments won’t save you. - Company says “aware of this issue”? Skip, no one helps. - CSRF and IDOR = same (in their eyes)? Skip, you’re “wrong.” - They fix your sqli while program suspended? Skip, you lose. Skip..
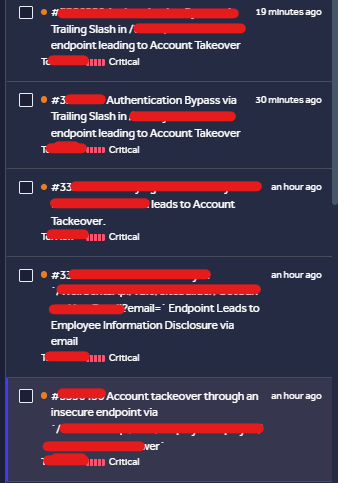
I submitted 5 critical reports in 2 hours due to 2 bugs. 1- The first mistake is when you add slach at the end it will bypass authentication - /api/x/x --- > 401 Unauthorized - /api/x/x/ -- > 200 Ok (2/1) #bugbounty #hackerone
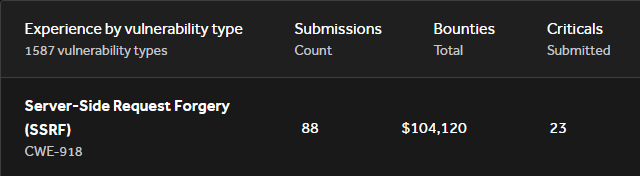
I've made over 100k on SSRF vulnerabilities. They aren't always as simple as pointing it at localhost or AWS Metadata service. Here are some tricks I've picked up over the past 5 years of web app testing:
follow @hacker_ (and @boringmattress) top:
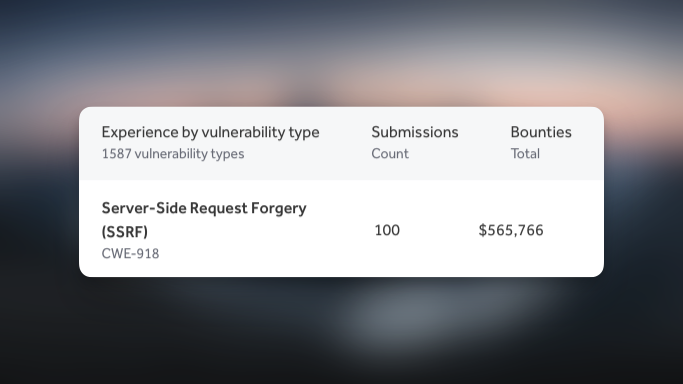
I've made $500k+ from SSRF vulnerabilities. Here are my tricks:
API-specific wordlists for fuzzing hidden routes & endpoints🚀 wordlists-cdn.assetnote.io/data/automated/

150$ - Info Disclosure on GoPro!⚡️ 1. In-Depth Subd Enum. 2. cat allsubs.txt | httpx -mc 200 > working.txt 3. nmap -iL working.txt -p0-65535 -oN fullscan.txt 4. dirsearch -l nmap.txt -w <wordlist> -x <status codes> -r -e <extensions> 5. Found .txt file #bugbountytip #bugbounty

Unauthenticated Access to Sensitive Customer Data via Google Dorking How I did it: - During recon, I used the dork: site:*.target.* "date of birth" ext:pdf - Found a PDF file exposing customer data. - Noticed an ID in the URL. - By changing the ID, I could access other data.




12 API hacking bug bounty tips you must try on your target! 😎 🧵 👇

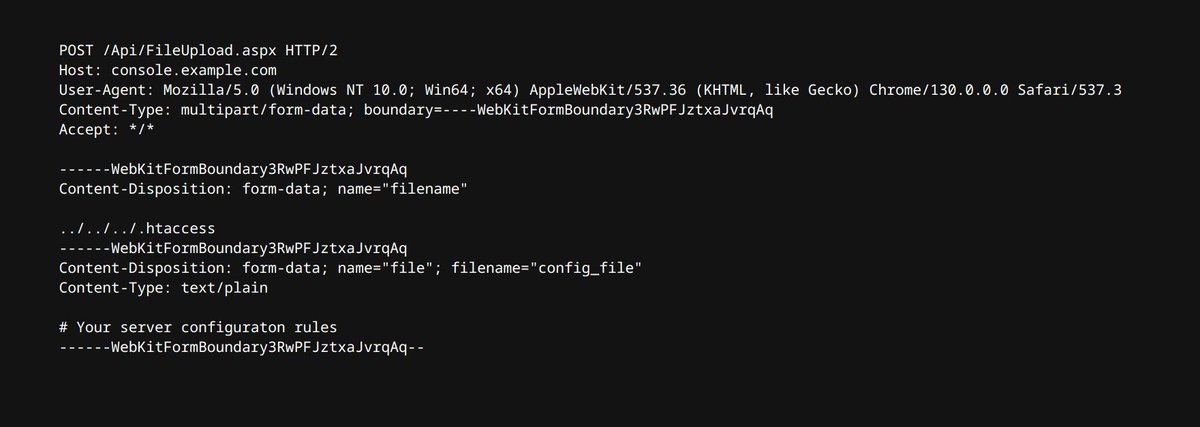
🔁 File uploads are almost everywhere... Sometimes, a simple validation mistake can result in a high-severity finding (such as RCEs) 🤠 In our technical article, we documented a few cool tricks you could try next time you're testing a file upload feature! Link in next post! 👇
redacted[.]com/ --> [302]❌ redacted[.]com/app/api/doc/ --> [200 OK] ✅ Bypassed the 302 and hit API doc gold! #bugbountytips #BugBounty
![arshiyaiha's tweet image. redacted[.]com/ --&gt; [302]❌
redacted[.]com/app/api/doc/ --&gt; [200 OK] ✅
Bypassed the 302 and hit API doc gold!
#bugbountytips #BugBounty](https://pbs.twimg.com/media/Gyu7KHRWgAAXAeY.jpg)
Bug Bounty Tips (1/2) 1- Add users with different roles in your company to the system. 2- Log in as a low-authority user in the incognito tab and log in as a high-authority account in the normal tab for role isolation. #BugBounty #bugbountytips

Try this out on your next target! Some more gold from the guys at @ctbbpodcast! 🔥

~IDOR bypass techniques New video out too! youtu.be/JNvnCojTAvI #bugbounty



United States Trends
- 1. phil 65.6K posts
- 2. phan 70.2K posts
- 3. Columbus 211K posts
- 4. President Trump 1.23M posts
- 5. Middle East 312K posts
- 6. Springer 11K posts
- 7. Gilbert 9,266 posts
- 8. Doug Eddings N/A
- 9. Kincaid 1,277 posts
- 10. Falcons 12.3K posts
- 11. Yesavage 3,095 posts
- 12. Mike McCoy N/A
- 13. Thanksgiving 58.8K posts
- 14. Cam Talbot N/A
- 15. Martin Sheen 1,107 posts
- 16. #LGRW 1,966 posts
- 17. Brian Callahan 12.8K posts
- 18. Titans 35.6K posts
- 19. John Oliver 8,736 posts
- 20. Macron 239K posts
You might like
-
 Ved Parkash
Ved Parkash
@v3d_bug -
 D33p4k
D33p4k
@BeingN00b -
 Samuel V.
Samuel V.
@sign3tsh3l1 -
 Jopraveen
Jopraveen
@jopraveen18 -
 Palani
Palani
@impalanichamy -
 Dhanesh Sivasamy
Dhanesh Sivasamy
@DhaneshSivasamy -
 வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
@veeppiaar -
 Jeya Seelan
Jeya Seelan
@rootxjs -
 🐝 T3xy45
🐝 T3xy45
@RegisDeldicque -
 Aswin Thambi Panikulangara
Aswin Thambi Panikulangara
@r0074g3n7 -
 Guhan Raja
Guhan Raja
@havocgwen -
 hs_0x_
hs_0x_
@hs_0x_ -
 mubassirpatel
mubassirpatel
@Mubassirpatel1 -
 Game0v3r
Game0v3r
@kabilan1290 -
 Tu$har
Tu$har
@iamtusharvyas
Something went wrong.
Something went wrong.



































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)