rado_node
@rado_node
Cybersecurity enthusiast
You might like
🚀 Big Announcement! 🚀 After 8+ years of working on PayloadsAllTheThings, I’m excited to release it as an ebook on Leanpub! 📖✨ To celebrate, I’m gifting 5 free copies to random retweeters! 🔥 👉 Retweet for a chance to win Thank you all for your incredible support! 🙌…
#USA 🇺🇸 - LockBit #ransomware group has announced The Federal Reserve on its victim list. The Federal Reserve System, based in Washington D.C., is the central banking system of the United States of America that conducts monetary policy to support a healthy economy. The group…
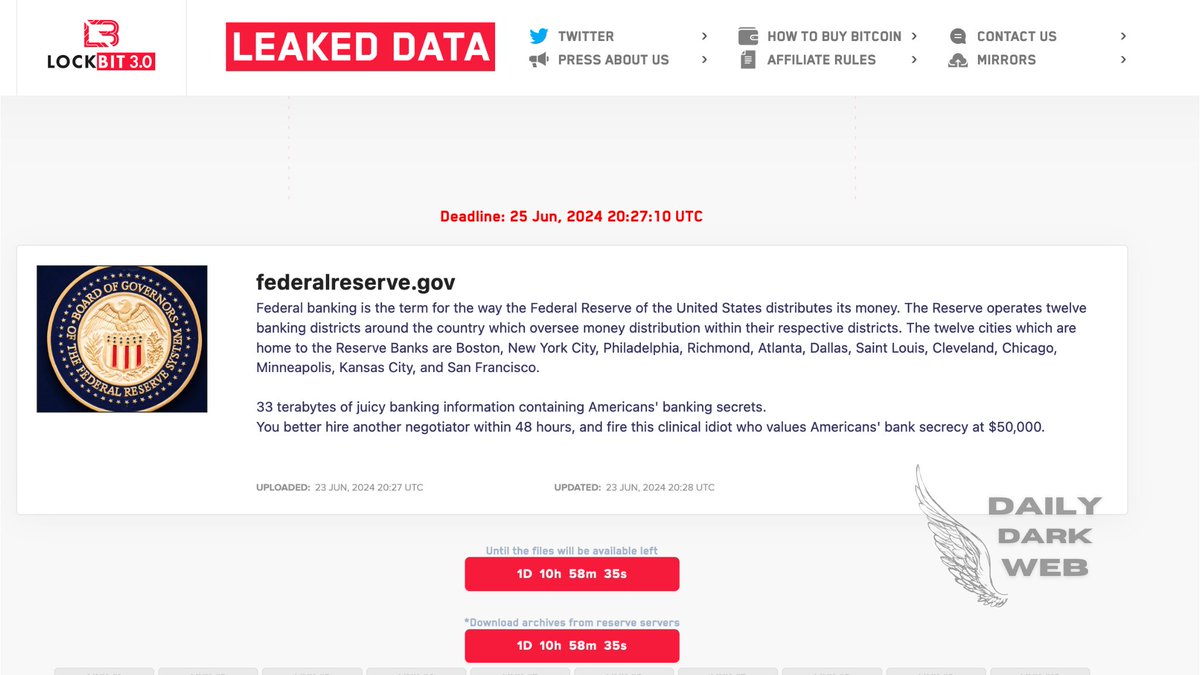
Ummmmm… this looks pretty serious!
Pro-Russian hacktivist group KillNet, Anonymous Sudan, and REvil announced their plans to take down the entire European banking system within the next 48 hours. "This is not a DDoS attack, the games are over. No money, no weapons, no Kiev regime -- this is the formula for the…
Great! You've found an IDOR on a web asset. It got fixed and you got the bounty! 💰 But the target also has a mobile application! @ManasH4rsh has a trick up his sleeve. What if that mobile application is also vulnerable to a similar IDOR? #bugbounty #bugbountytips 👇

Hacking APIs Book Giveaway sponsored by APIsec.ai! We are giving away 10 print books. One entry per: ♥️ Like 🔁 RT 👑Bonus entry to anyone who follows @apisec_ai. Ends in 48 hours!

Fancy becoming a full-time #BugBounty hunter but don't have the money to support it? @intigriti is trying to change that portswigger.net/daily-swig/bug…
portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.
"All versions of Samba prior to 4.13.17 are vulnerable to an out-of-bounds heap read write vulnerability that allows remote attackers to execute arbitrary code as root on affected Samba installations that use the VFS module vfs_fruit,".... thehackernews.com/2022/01/new-sa…
Just like Google Search can be used to search for vulnerable websites/systems, IoT devices, and sensitive data (the method is known as Google hacking or dorking), VirusTotal’s APIs and tools can be used to find files containing stolen data. helpnetsecurity.com/2022/01/18/vir…
helpnetsecurity.com
VirusTotal Hacking: Finding stolen credentials hosted on VirusTotal - Help Net Security
Popular online service VirusTotal can be used to collect credentials stolen by malware, researchers at SafeBreach have found.
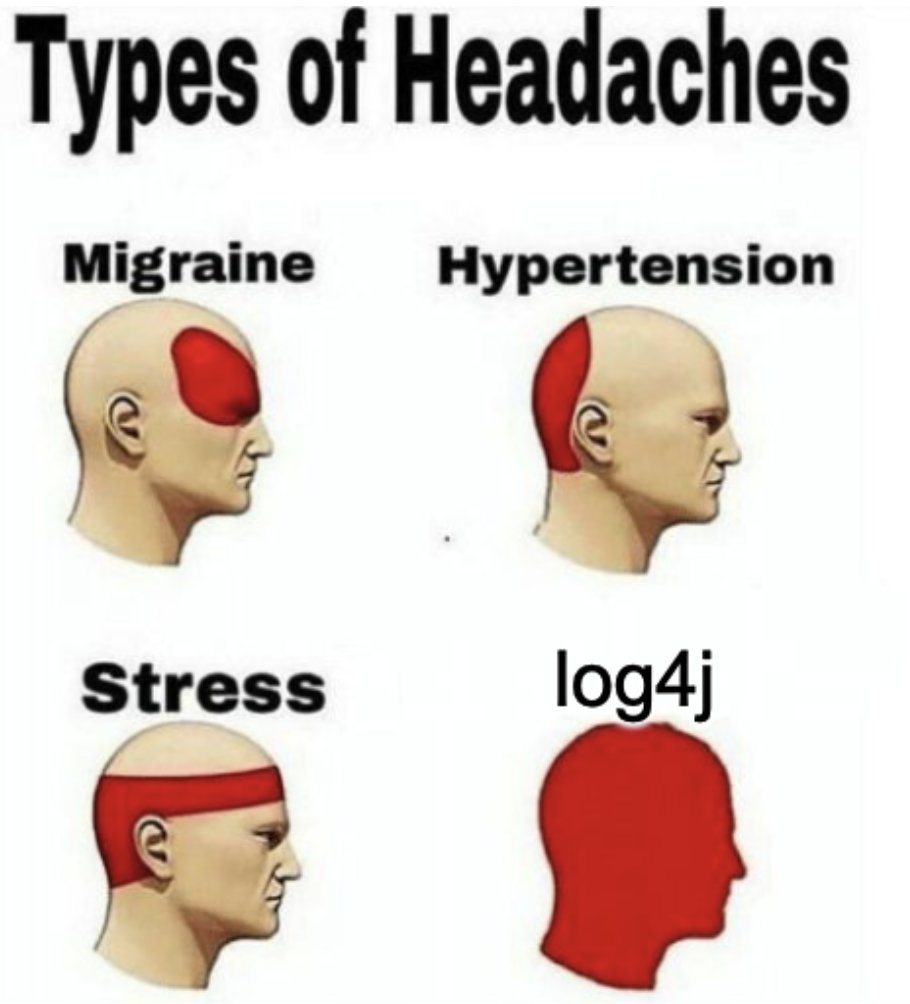
“It’s Log4Shell, Jim,” as Commander Spock never actually said, “But not as we know it.” nakedsecurity.sophos.com/2022/01/07/log…
Am I too old to get into cybersecurity? YouTube Video: youtu.be/vlqmC1aEUSk #cybersecurity #infosec #redteam #hacking #ethicalhacking #hacker #kalilinux #ine #oscp @ITJunkie

#HackTheBox Remote video is now up! A fun easy windows box that involves utilizing an Umbraco RCE to get shell, then modifying a service get a root shell. Change up the PS Cradle I use to run nishang, and first time using RoguePotato - youtu.be/iyYqgseKUPM
youtube.com
YouTube
HackTheBox - Remote
United States Trends
- 1. Josh Allen 17,1 B posts
- 2. Jags 14,4 B posts
- 3. Bills 100 B posts
- 4. Trevor Lawrence 4.354 posts
- 5. Tony Romo 1.485 posts
- 6. #BUFvsJAX 3.530 posts
- 7. Parker Washington 1.192 posts
- 8. Joe Brady 1.312 posts
- 9. #BLACKWHALE 339 B posts
- 10. #DUUUVAL 3.368 posts
- 11. Keon Coleman N/A
- 12. Go Birds 15,3 B posts
- 13. Dalot 38,5 B posts
- 14. Tuten 1.273 posts
- 15. Cunha 18 B posts
- 16. Shaq Thompson N/A
- 17. McDermott 2.251 posts
- 18. Stirtz N/A
- 19. Nantz N/A
- 20. Welbeck 8.019 posts
Something went wrong.
Something went wrong.