Join us NOW (10pm ET) in finally putting some Flare-On challenges to rest on tonight's late-night Halloween stream! Check out time travel debugging with us! youtube.com/watch?v=0PBV1Z…

youtube.com
YouTube
Binary Ninja Live Stream: Oct 31st, 2025
Just dropped: my RECON 2025 talk on Rust library recognition in malware! 🦀 Worth a watch if you're into RE or malware research. youtu.be/_JiuYkFzVgg?si… #malware #RIFT #microsoft #reverseengineering #rust

youtube.com
YouTube
Recon 2025 - Unveiling RIFT: Advanced Pattern Matching for Rust...
My Top Lessons for Becoming a Full-Time Auditor 1. Learn it the hard-way

This seems to be a common misconception, so CTF players: Zellic hires REGARDLESS of web3 experience. The main criteria is researcher skill/talent. We've hired smart pwn / VR folks with ZERO blockchain background. Don't think, "I'll wait to get better then apply"... JUST apply.
10 common JavaScript coding vulnerabilities Practical code examples.🐞💻 1- Open Redirect 2-SSRF 3-Timing Attacks 4-prototype pollution 5-NoSQLi 6-ReDoS 7-misconfiguration 8-Hard Code Vulnerability 9-mass assignment 10-Host Header Injection #BugBountyTip youtube.com/watch?v=ypNKKY…
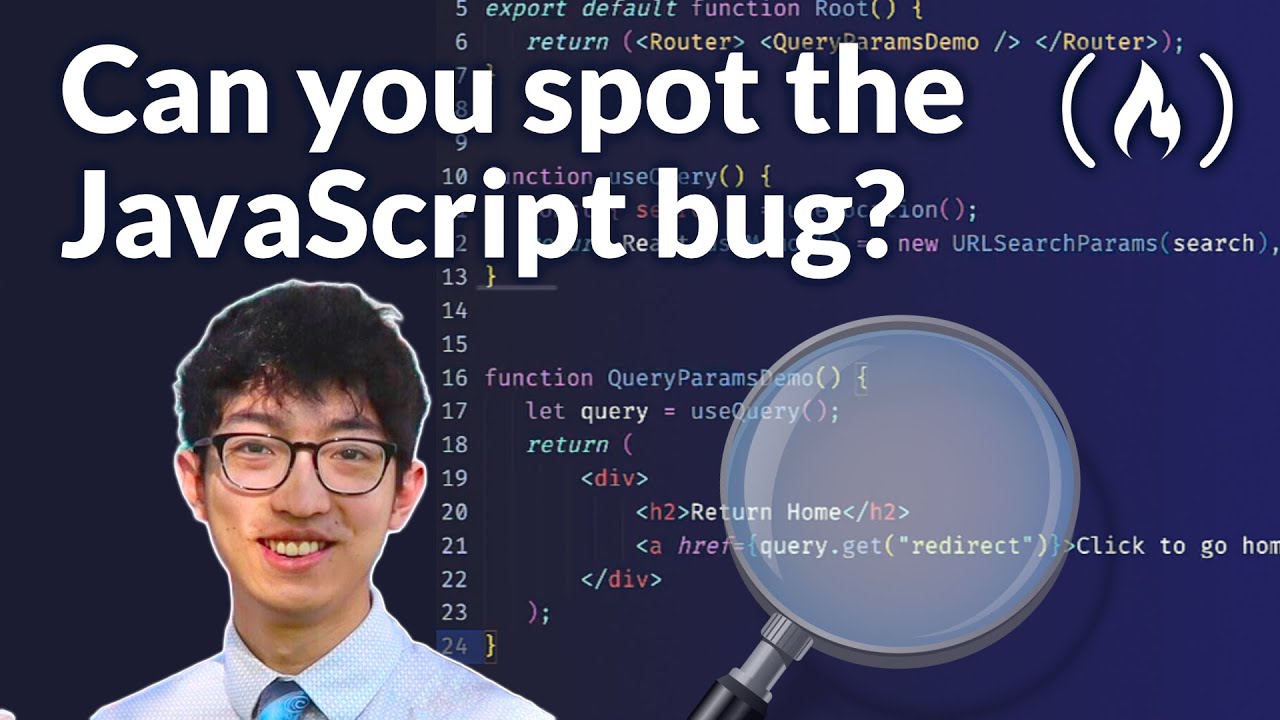
youtube.com
YouTube
JavaScript Security Vulnerabilities Tutorial – With Code Examples
Last weekend, I participated in corCTF and solved the Android Pwn challenge - corphone. It was a great challenge, and I learned a lot from it. Here's my write-up :) u1f383.github.io/android/2025/0…
[Research] smart contracts auditing 101 for pwners - PART 1 (EN) hackyboiz.github.io/2025/09/07/d4t… Hello, this is d4tura. In this research post, I summarize the core concepts required to solve the smart contract wargame "Damn Vulnerable DeFi." From the perspective of a 'pwner' more…
![hackyboiz's tweet image. [Research] smart contracts auditing 101 for pwners - PART 1 (EN)
hackyboiz.github.io/2025/09/07/d4t…
Hello, this is d4tura. In this research post, I summarize the core concepts required to solve the smart contract wargame "Damn Vulnerable DeFi."
From the perspective of a 'pwner' more…](https://pbs.twimg.com/media/G0NrBV0bEAAmVpR.jpg)
Great sereis by @8kSec on arm reversing and exploitation 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… 8ksec.io/arm64-reversin… #arm #cybersecurity
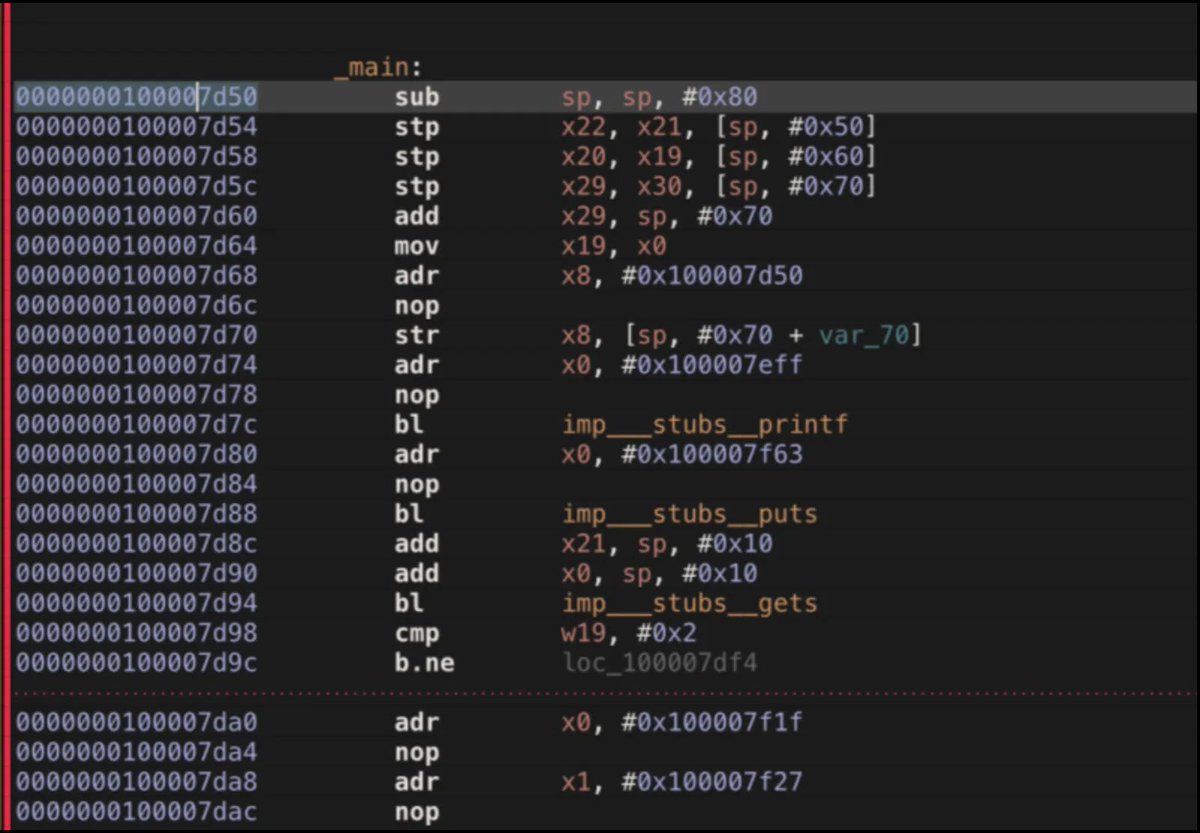
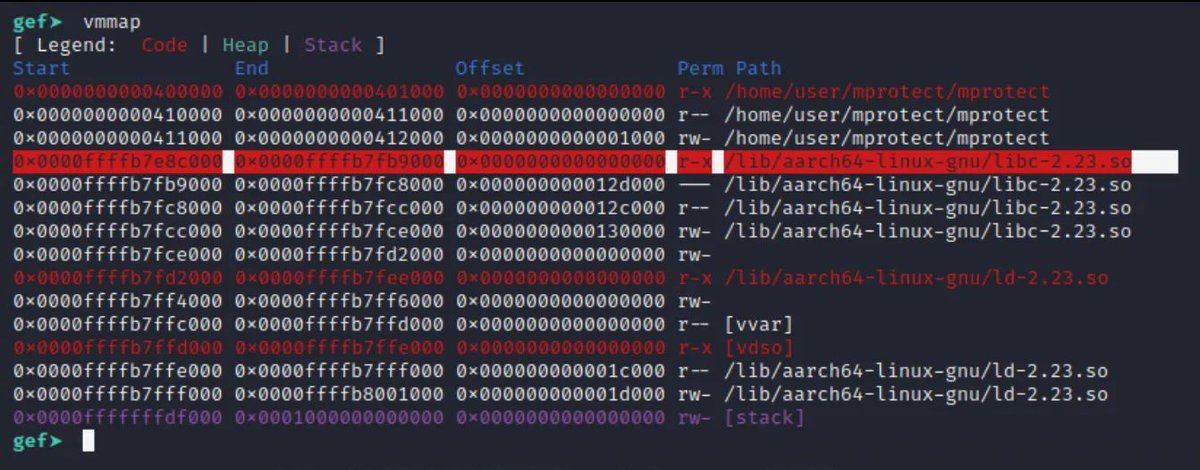

Nice ARMv8 AArch64/ARM64 tutorial mariokartwii.com/armv8/ #infosec #assembly
0-day Hunting Strategy with Eugene “Spaceraccoon” Lim x.com/i/broadcasts/1…
Awesome Reverse Engineering and Malware Analysis Roadmap📕 - github.com/x86byte/RE-MA-… #cybersec #infosec #hacking
📣 The latest instalment of our VR Development Programme resources is now available on YouTube! 📣 An introduction to ARM64, ARM32 and x86-64 assembly for vulnerability research. youtube.com/watch?v=c7utLP…

youtube.com
YouTube
VRDP Training - Assembly Code
Part 4 of the Buffer Overflow series has been posted! In today's writeup, we learn how to create a decoder stub, introduce an obligatory nop sled, and use memcpy to copy the encoded shellcode to our newly created memory region using VirtualAlloc 😺 g3tsyst3m.github.io/binary%20explo…
1/ Once upon time I was just a university student with zero coding experience. No background in Web3 security. No idea how smart contracts worked. But I knew one thing—I wanted to break into Web3. Today? I am on the path to $1M in security findings. Here’s how it happened. 🧵👇
You don’t find critical vulnerabilities by thinking like a dev. You find them by thinking like an attacker. If you want to win audit contests and get paid, read this. 🧵👇

As a Web3 Security Researcher Please learn: EVM 1. How calldata works/structured 2. Assembly, low level vulnerabilities 3. "The Journey of a Smart Contract" (tweet) 4. All types of Proxies 5. 1Inch Exploit Uniswap V3-V4 1. TWAP, observations 2. Ticks, how it works/updated…
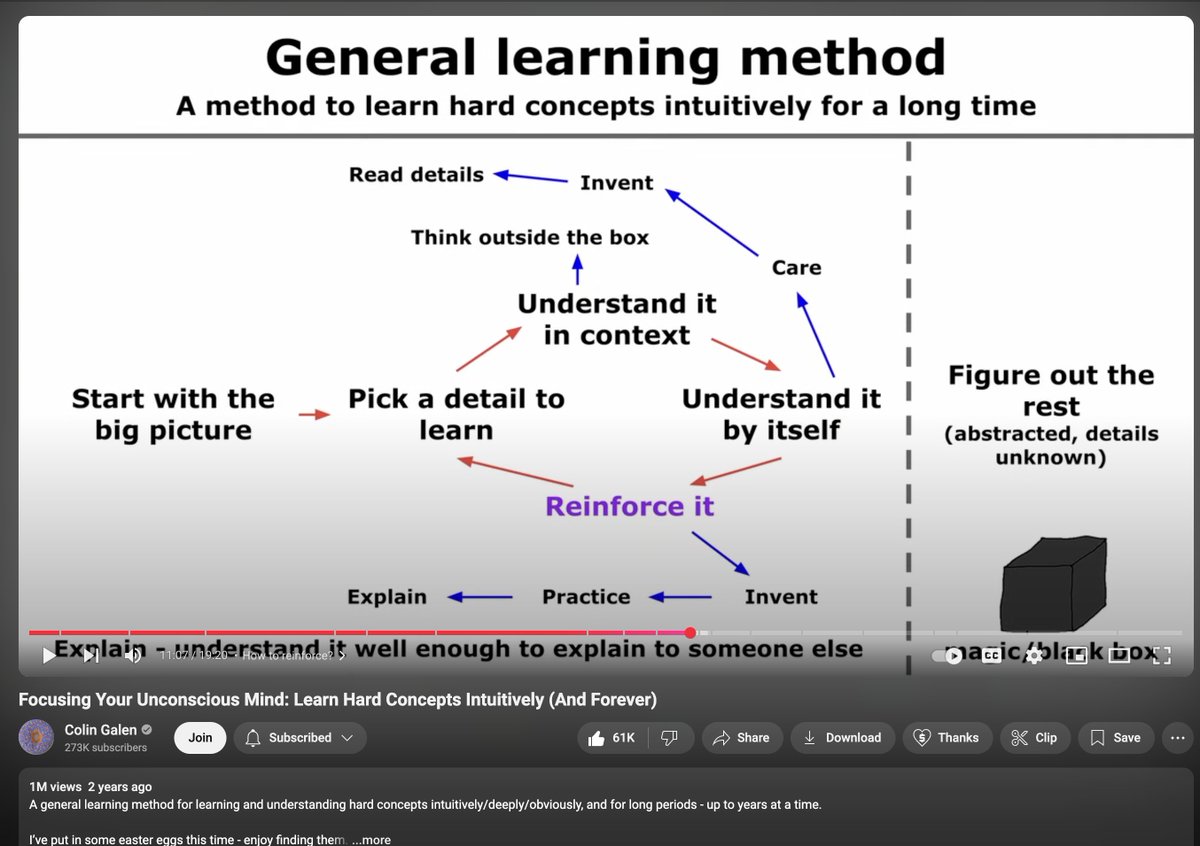
I used to think I was bad at learning hard things. I was wrong. This video completely rewired my approach. Link in comment.
#malcat is an amazing tool - if you want to see it in action, you can watch the author show off it's many features in this live stream: youtube.com/live/yzC_539sR…
youtube.com
YouTube
Learn How to Dissect Binary Files with the Creator of Malcat!
If you need to identify #malware quickly, give #malcat a try: its Kesakode code identification is fast and can even work offline! More info: doc.malcat.fr/analysis/kesak…
United States الاتجاهات
- 1. Mason 36.8K posts
- 2. #RiyadhSeason 7,805 posts
- 3. Syracuse 7,913 posts
- 4. Lincoln Riley 1,287 posts
- 5. Arch Manning 2,612 posts
- 6. Joe Jackson 1,111 posts
- 7. Oregon 26.4K posts
- 8. #TheRingIV 3,409 posts
- 9. Stoops 1,594 posts
- 10. #AEWFullGear 6,241 posts
- 11. #AEWTailgateBrawl N/A
- 12. Kansas State 2,880 posts
- 13. Jeremiyah Love 3,529 posts
- 14. Vandy 3,246 posts
- 15. Jonathan Smith N/A
- 16. Sadiq 8,020 posts
- 17. #GoBlue 2,358 posts
- 18. Harden 30.6K posts
- 19. Fran Brown N/A
- 20. Arkansas 9,357 posts
Something went wrong.
Something went wrong.