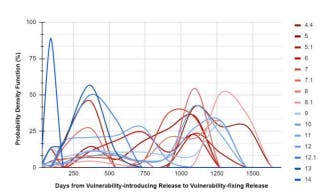
#androidsec 검색 결과
Using an Android emulator for API hacking⚔️⚡️ zerodayhacker.com/using-an-andro… #androidsec #bugbountytip #infosec #cybersec
This sample for the #androidsec community. Have you seen any #dirtycow malicious sample in the wild? Find me in keybase.


Yesterday I talked about my COVID apps observer at the #ResearchCocktails of the @VUamsterdam, very good vibes! 🖼️ Slides: docs.google.com/presentation/u… 💻 GitHub repo: github.com/iivanoo/covid-… @AndroidAuth @AndroidDev @AndroidSecurity @androidcentral @Android #Android #AndroidSec

#androidrce #androidsec #AndroidSecurity #rce #HouseParty #housepartyapp #housepartyhack #Housepartyhacked
[50/n] End Thread Protection is not perfect but raises the bar significantly. In a world of automated attacks, even basic obfuscation helps. Read full paper: dl.acm.org/doi/10.1145/37… #AndroidSec #MobileSecurity #InfoSec
Google's Triada backdoor demonstrates vulnerabilities in the mobile supply chain #MobSec #AndroidSec cyberscoop.com/android-backdo…
Best resources to start android pentesting (1/2) #infosec #AndroidSec 1/ - manifestsecurity.com/android-applic… - eshlomo.us/mobile-penetra… - github.com/vaib25vicky/aw… - github.com/tanprathan/Mob… - gbhackers.com/mobile-applica… - enciphers.com/awesome-androi… - youtube.com/watch?v=vx-FKE…
New on the blog: my writeup for CyCTF 2025 — Grand Theft Mobile. Recovered the flag from an Android native lib using Frida. Read: 0xmar.medium.com/cyctf-2025-and… #CTF #AndroidSec
Then (CVE-2022–20006) comes. #androidsec #androidsecurity #mobileapps #cve medium.com/maverislabs/lo…
medium.com
Lock Screen Bypass Exploit of Android Devices (CVE-2022–20006)
Background on Lock Screen Bypass Exploits
Toolkit for Android Testing - ADB (data access) - Frida (runtime hooks) - Burp Suite (traffic analysis) - JADX (code review) - MobSF (automated analysis) #BugBountyTools #AndroidSec #EthicalHacking
A study detailing how Android vulnerabilities are traced, labeled, and linked to code changes to build an accurate dataset for security-bug classification. - hackernoon.com/inside-the-dat… #mlsecurityframework #aospsecurity
Argus: Android Vulnerabilities at Scale 📆 When: Wednesday 26th November 📍Where: B67/1037 🕙When: 18:00 - 20:00 Find out more on our website sucss.org

Updated Post: How to Protect Your Device with Android 16’s Enhanced Mobile Security Features cybersecurity-insiders.com/how-to-protect…

⚡️ #Android Security Release: #Google Tightens Developer Verification To Fight Modern Scams undercodenews.com/android-securi…
Fascinating reading: Rust in Android security.googleblog.com/2025/11/rust-i… #android #Rust #AppSec #Software
ガチヤバそうなAndroidの脆弱性。アップデートした方がよさそう。 --- インストールされたアプリはシステム権限を要求しないにもかかわらず、画面に表示されるほかのインストール済みアプリの情報を実質的に読み取ることが可能だ。 wired.jp/article/a-new-…
Static analysis for Android apps based on the OWASP MASVS framework 🌟 - github.com/Cyber-Buddy/AP… #infosec #cybersec #bugbountytips

📚 Hacking Crypto Secrets from Android Heap Memory Extract cryptographic secrets from Android application heap to compromise encryption. infosecwriteups.com/728097fcda3
The Android overlay function is a convenient feature, but it can be repurposed with malicious intent. Attackers use this functionality to steal user credentials and financial information, but there are ways to defend against it. Watch here to learn more: hubs.la/Q03ThpXp0
youtube.com
YouTube
Overlay Attacks: What is Android Mobile App Malware?
The "RIGHT?!" sarcasm doesn't change the facts btw: security.googleblog.com/2025/11/rust-i…
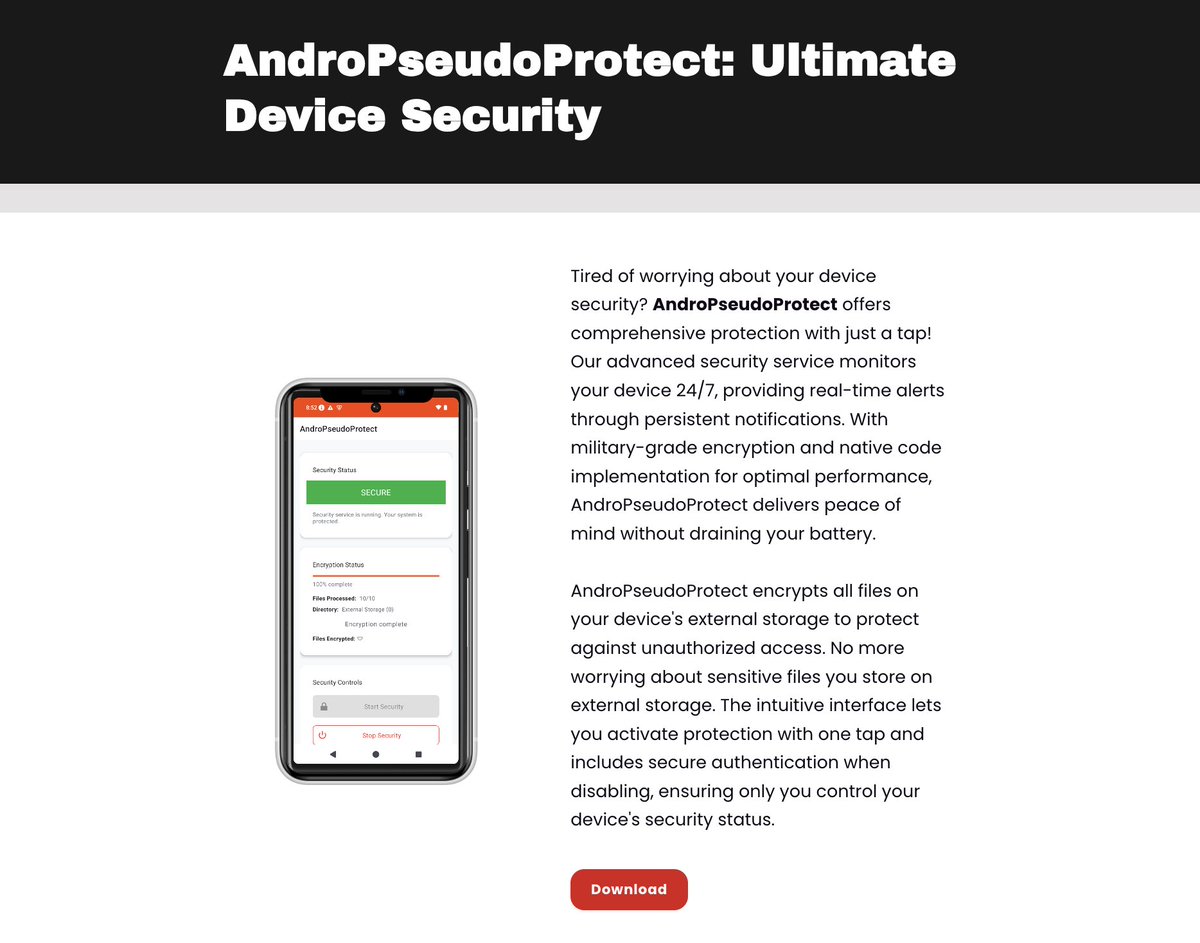
AndroPseudoProtect: Ultimate Device Security... or is it? academy.8ksec.io/course/android… An Android app promises one-tap encryption and always-on protection, but the real test is resilience. Discover if its IPC and authentication can be bypassed and demonstrate a proof-of-concept that…
Rust in Android: move fast and fix things: ift.tt/U4285cv by Google Online Security Blog #infosec #cybersecurity #technology #news
Multiple Vulnerabilities in Google Android OS Could Allow for Remote Code Execution – PATCH: NOW dlvr.it/TPFcSN
Meaning: If you are a user you can install unvetted/no reputation apps from unknown parties if you really want to. But there's going to be enough friction and warnings in the user experience flow to make successful social engineering sonewhat difficult. android-developers.googleblog.com/2025/11/androi…
All Android devices are vulnerable to an attack that effectively screenshares any app that the attacker chooses, without your knowledge
New Post: Google Declares Android as the Most Secure Mobile OS: A Game Changer in Mobile Cybersecurity cybersecurity-insiders.com/google-declare…

Google start met verificatie van Android-ontwikkelaars #securitynl security.nl/posting/912665…
Update your ANDROID devices, now. Unlike typical exploits that require users to tap a link or install an app, this zero-click vulnerability can be triggered silently through crafted network packets or malicious applications distributed outside official app stores. CVE-2025-48593
Tucked away deep in the Settings app on Android are all sorts of privacy and security features you may have never seen. It’s time to get to know those settings. ssd.eff.org/module/how-to-…
ssd.eff.org
How to: Get to Know Android Privacy and Security Settings
Open up your Android phone’s Settings app and you’ll find dozens of different options with little guidance on what those options do. Some of these settings have a serious impact on your privacy and...
Sadly, Google will also clamp down on these. android-developers.googleblog.com/2025/08/elevat…
Using an Android emulator for API hacking⚔️⚡️ zerodayhacker.com/using-an-andro… #androidsec #bugbountytip #infosec #cybersec

This sample for the #androidsec community. Have you seen any #dirtycow malicious sample in the wild? Find me in keybase.


Yesterday I talked about my COVID apps observer at the #ResearchCocktails of the @VUamsterdam, very good vibes! 🖼️ Slides: docs.google.com/presentation/u… 💻 GitHub repo: github.com/iivanoo/covid-… @AndroidAuth @AndroidDev @AndroidSecurity @androidcentral @Android #Android #AndroidSec

Something went wrong.
Something went wrong.
United States Trends
- 1. #hazbinhotelseason2 63K posts
- 2. Good Wednesday 21K posts
- 3. #hazbinhotelspoilers 4,199 posts
- 4. Peggy 20.4K posts
- 5. LeBron 88.7K posts
- 6. #InternationalMensDay 26.9K posts
- 7. #DWTS 54.8K posts
- 8. Baxter 2,455 posts
- 9. Dearborn 250K posts
- 10. Kwara 187K posts
- 11. #HazbinHotelVox 19.6K posts
- 12. Patrick Stump N/A
- 13. Whitney 16.6K posts
- 14. Grayson 7,239 posts
- 15. Tinubu 155K posts
- 16. Orioles 7,453 posts
- 17. Cory Mills 10.7K posts
- 18. MC - 13 1,133 posts
- 19. Sewing 5,239 posts
- 20. Ward 26.9K posts