#binaryanalysis zoekresultaten
I often tell people IDA is like a turbocharged Notepad++ for binaries, and I reach for its type libraries whenever a blob of assembly needs context. reverselabs.dev/blog/ida-type-… #ReverseEngineering #IDAPro #BinaryAnalysis #TypeLibraries

🧩 #BinaryAnalysis for legacy devices 🧩 Source code SCA for in-development products 🧩 #SBOM validation for opaque third-party components Dario Lobozzo explains why a layered, flexible analysis approach is essential for CRA compliance #ProductSecurity #IoTSecurity
Fourth in the session was Fan et al.'s "R+R: A Systematic Study of Cryptographic Function Identification Approaches in Binaries," exploring gaps in cryptographic tool evaluation. (acsac.org/2024/program/f…) 5/6 #Cybersecurity #BinaryAnalysis

The blog post keeps going, as I said it will take some time until I finish writing it, but I think you will really like the content :D #compiler #binaryanalysis #dalvik

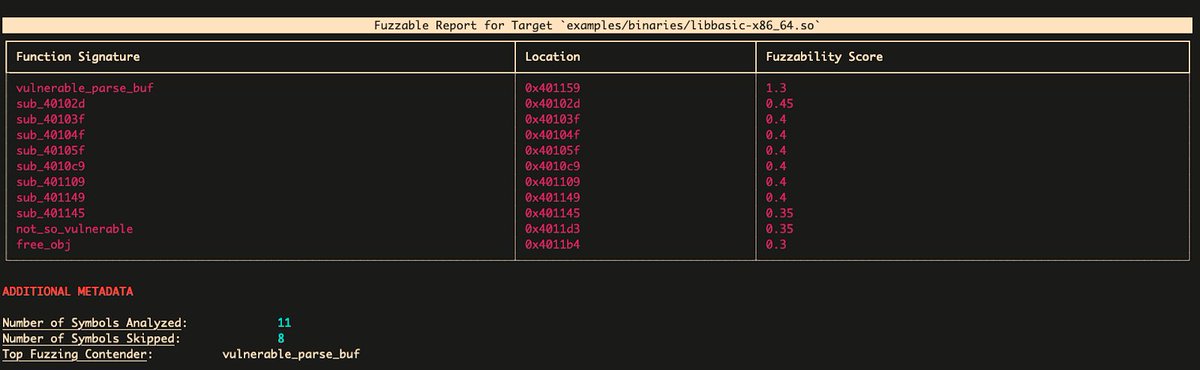
Fuzzable - Framework For Automating Fuzzable Target Discovery With Static Analysis bit.ly/3XB97Zf #BinaryAnalysis #Fuzzable
This room has stuffed ton of things into my mind, Perhaps, I should take a breath and revisit it! #reverseengineering #reversing #binaryanalysis
Why is it called “optional” if it’s required to run? 🧠 Dive into the Windows PE Optional Header with us. Full video on YouTube! 🔗 #HackDefenderAcademy #PEfile #BinaryAnalysis #module0 #class2
Securing IoT products demands deep #BinaryAnalysis. Why? Because today’s IoT software is a tangled web of global supply chains, legacy code & opaque binaries. In our Security Short, Edwin makes it clear: to protect IoT products, you have to go deeper than the surface. #IoT
Precompiled binaries are a black box risk. Without source code, you’re left with vendor docs & guesswork. In our "Security Short", Edwin stresses that the only way to truly understand what’s inside precompiled binaries is through #BinaryAnalysis. Visibility matters.
Introducing Nova, a series of foundation models for binary/assembly code. We have also released fine-tuned models for binary code decompilation. #LLM #LLM4Code #BinaryAnalysis #Security @NanJiang719, Chengxiao Wang, Kevin Liu, @XiangzheX, Xiangyu Zhang, Petr Babkin.


Excited to release sharpAngr! 🚀 A .NET port of @angr_gh that brings symbolic execution & binary analysis to C# devs. Explore, exploit, reverse—now with LINQ & async. GitHub: github.com/anhed0nic/shar… #reverseengineering #binaryanalysis #dotnet #angr
Fuzzable - Framework For Automating Fuzzable Target Discovery With Static Analysis bit.ly/3XB97Zf #BinaryAnalysis #Fuzzable

🔍How can AI unlock deeper insights into binary code? This survey decodes recent breakthroughs in semantic feature selection & embedding for binary analysis. Read more👇 academax.com/FITEE/doi/10.1… #AcadeMax #BinaryAnalysis #AI #Cybersecurity #SoftwareEngineering

[New Blog Post] DWARF Verification via Ghidra and CBMC #ghidra #verification #binaryanalysis #compiler philipzucker.com/pcode2c-dwarf/
What happens at the 𝙚𝙣𝙩𝙧𝙮 𝙥𝙤𝙞𝙣𝙩 stays at the 𝙚𝙣𝙩𝙧𝙮 𝙥𝙤𝙞𝙣𝙩... unless you analyze it 😉 🔗 academy.hack-defender.com 🔗𝙔𝙤𝙪𝙏𝙪𝙗𝙚 @hackder_official #ReverseEngineering #BinaryAnalysis #HackDefenderAcademy #TechTok #CyberTips #module0 #class2 #ida #infosec
angr-rs is here! A memory-safe, drop-in Rust port of the legendary angr binary analysis framework. Same power, zero segfaults. Rewrite-it-in-Rust complete. github.com/anhed0nic/angr… #rustlang #binaryanalysis #angr #riir #rewriteitinrust
🔍 Master binary analysis with 010 Editor! Learn hex searches, binary templates, & PE file analysis with hands-on labs. 💸 Pay what you can & start today! 👉 labs.cyber5w.com/courses/5dd828… #DFIR #BinaryAnalysis #DigitalForensics #010Editor #CyberSecurity #C5W

🛠️ The Dump: The Dump window in OllyDbg is a built-in hex viewer displaying raw binary data in memory. It typically shows two views: hexadecimal and ASCII, allowing you to inspect the binary directly. #BinaryAnalysis #OllyDbg
radare2 – Reverse engineering framework rivaling IDA. 🌐 rada.re/n/ #RETools #BinaryAnalysis
🧩 #BinaryAnalysis for legacy devices 🧩 Source code SCA for in-development products 🧩 #SBOM validation for opaque third-party components Dario Lobozzo explains why a layered, flexible analysis approach is essential for CRA compliance #ProductSecurity #IoTSecurity
Fourth in the session was Fan et al.'s "R+R: A Systematic Study of Cryptographic Function Identification Approaches in Binaries," exploring gaps in cryptographic tool evaluation. (acsac.org/2024/program/f…) 5/6 #Cybersecurity #BinaryAnalysis

I often tell people IDA is like a turbocharged Notepad++ for binaries, and I reach for its type libraries whenever a blob of assembly needs context. reverselabs.dev/blog/ida-type-… #ReverseEngineering #IDAPro #BinaryAnalysis #TypeLibraries

Hi! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hello! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 12 August 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hey! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hey! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hello! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 12 August 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hello! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hey! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hello! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hi! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hey! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 12 August 2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hey! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 12 August 2025 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hi! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hello! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on August 12, 25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Hi! ObjectSecurity's presentation video available "Unseen and Unsafe: Why ECU Cybersecurity Needs Binary-Level Truth" at GVSETS 2025 on 8/12/25 in Novi, MI. bit.ly/4lesTW9 #GVSETS #Army #binaryanalysis #binlens #objectsecurity #ObjectSecurity
Triton - Dynamic Binary Analysis (DBA) Framework j.mp/2AVlB5g #BinaryAnalysis #BinaryTranslation #InstructionSemantics #Python

Introducing Nova, a series of foundation models for binary/assembly code. We have also released fine-tuned models for binary code decompilation. #LLM #LLM4Code #BinaryAnalysis #Security @NanJiang719, Chengxiao Wang, Kevin Liu, @XiangzheX, Xiangyu Zhang, Petr Babkin.



Freki - Malware Analysis Platform j.mp/3p9fRw2 #BinaryAnalysis #Freki #Malware #MalwareAnalysis #MalwareResearch #RESTAPI

Sojobo - A Binary Analysis Framework j.mp/32BDbHp #B2R2 #BinaryAnalysis #Debugger #Fsharp #MalwareAnalysis #MalwareAnalyzer

Zelos - A Comprehensive Binary Emulation Platform j.mp/3b6uaL5 #BinaryAnalysis #CommandLine #Dynamic #Emulation #Emulator #Linux

ABD - Course Materials For Advanced Binary Deobfuscation j.mp/39aCrNf #ABD #BinaryAnalysis #BinaryExploitation #Deobfuscation

Angr - A Powerful And User-Friendly Binary Analysis Platform j.mp/2UgfvVq #Angr #BinaryAnalysis #CTF #Python #SymbolicExecution

Radare2 - UNIX-like Reverse Engineering Framework And Command-Line Toolset j.mp/3rO0vzN #BinaryAnalysis #Forensics


BinAbsInspector - Vulnerability Scanner For Binaries bit.ly/3t9651o #BinAbsInspector #BinaryAnalysis #ReverseEngineering

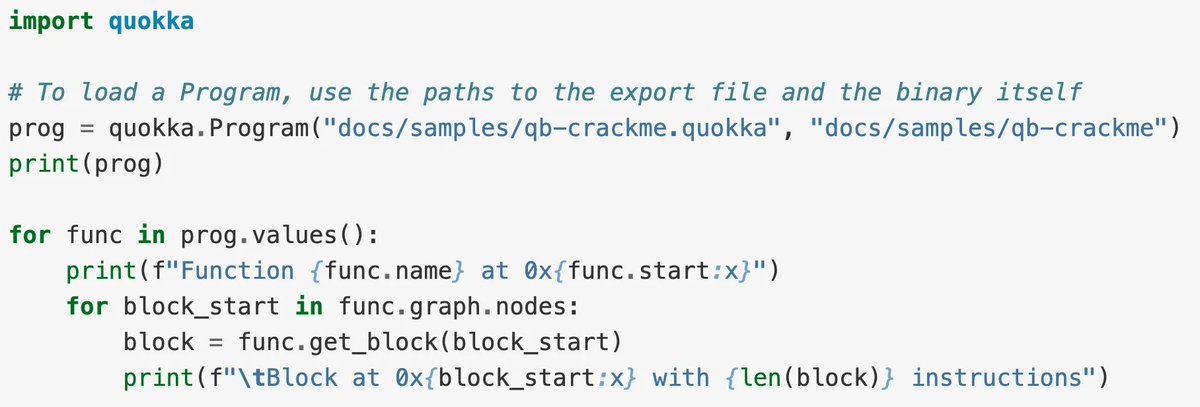
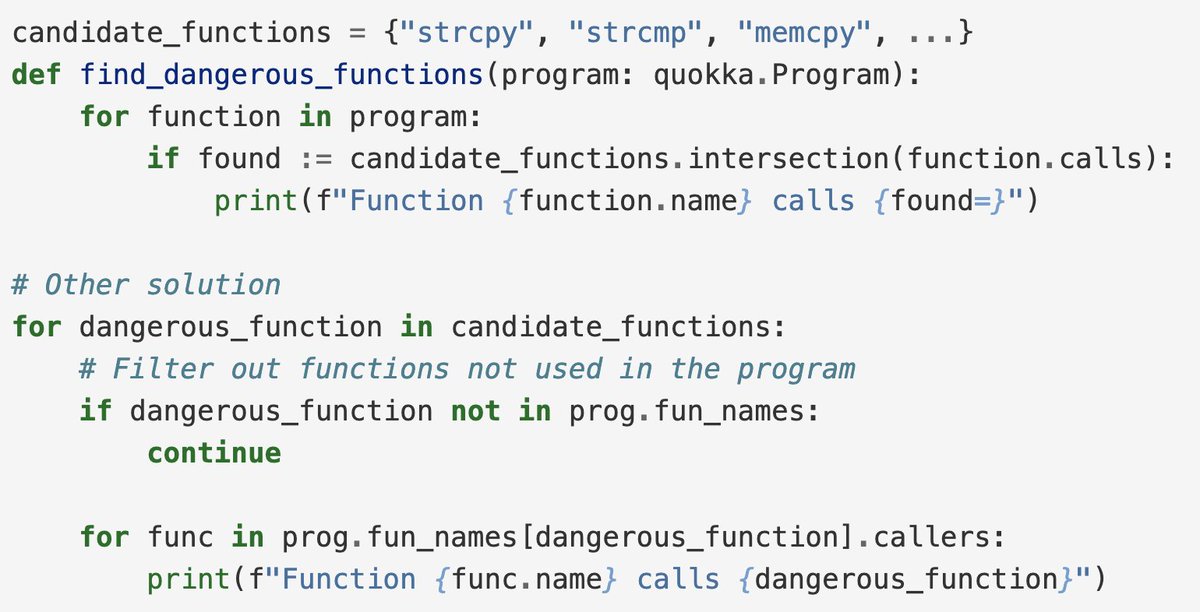
Quokka: a new binary exporter by @quarkslab Project intro: buff.ly/3Rc479I Documentation: buff.ly/3SuLMWI GitHub repo: buff.ly/3E5DSiD #binaryanalysis #disassembly #informationsecurity #cybersecurity #reverseengineering #quokka

Detect It Easy - Program For Determining Types Of Files For Windows, Linux And MacOS j.mp/2YeTkUZ #BinaryAnalysis #Debugger #Mac

IDA Free has been upgraded to the latest IDA version 7.7SP1! This light but powerful tool can quickly analyze the binary code samples and allow users to take a closer look at the results. Try it out for free hex-rays.com/ida-free/ #IDAFreeware #Binaryanalysis #HexRays

DECAF - Short for Dynamic Executable Code Analysis Framework j.mp/2nPu1bS #AnalysisFramework #BinaryAnalysis #CodeAnalysis

RetDec - A Retargetable Machine-Code Decompiler Based On LLVM j.mp/355V575 #ARM64 #BinaryAnalysis #Debugging #Decompiler #RetDec

E9Patch - A Powerful Static Binary Rewriting Tool j.mp/2Wxs6q3 #BinaryAnalysis #BinaryInstrumentation #BinaryPatching #Chrome

Kam1n0 - Assembly Analysis Platform bit.ly/3feC9wU #BinaryAnalysis #DataMining #Kam1n0 #Kam1n0Community #SymbolicExecution

DrSemu - Malware Detection And Classification Tool Based On Dynamic Behavior j.mp/2V3rVDv #BinaryAnalysis #DetectMalware #DrSemu

Manticore - Symbolic Execution Tool For Analysis Of Binaries And Smart Contracts j.mp/2A0zheG #BinaryAnalysis #Blockchain #Linux

Goblin - An Impish, Cross-Platform Binary Parsing Crate, Written In Rust j.mp/2DIl8Fp #BinaryAnalysis #CrossPlatform #Fuzzing

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 67.5K posts
- 2. Cowboys 67.5K posts
- 3. LeBron 88.3K posts
- 4. Gibbs 17.6K posts
- 5. Pickens 12.3K posts
- 6. Brandon Aubrey 6,770 posts
- 7. #OnePride 9,482 posts
- 8. Ferguson 10.1K posts
- 9. #DALvsDET 5,978 posts
- 10. Goff 8,184 posts
- 11. CeeDee 9,848 posts
- 12. Eberflus 2,117 posts
- 13. Bland 8,183 posts
- 14. DJ Reed N/A
- 15. Shang Tsung 17.1K posts
- 16. Al Michaels N/A
- 17. Schotty 1,669 posts
- 18. Austin Reaves 13.4K posts
- 19. Turpin 2,122 posts
- 20. #LakeShow 4,410 posts