#symbolicexecution hasil pencarian
Very interesting blog post on how to use symbolic execution to triage crashes coming out of a fuzzer. Credits @jordan9001 atredis.com/blog/2022/10/2… #fuzzing #symbolicexecution #infosec #cybersecurity #vulnerability




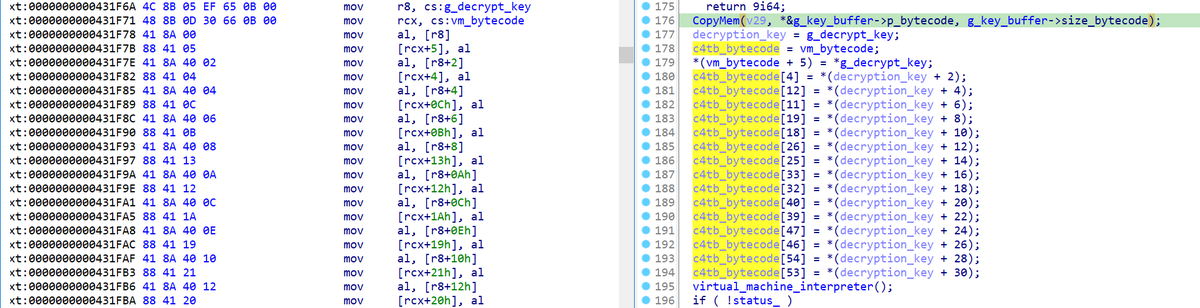
Playing with the VMProtect software protection. Automatic deobfuscation of pure functions using symbolic execution and LLVM. github.com/JonathanSalwan… #Pentesting #SymbolicExecution #Deobfuscation #CyberSecurity #Infosec


More angr - Defeating 5 ELF Crackmes binaryresearch.github.io/2020/01/22/mor… #ReverseEngineering #SymbolicExecution #CyberSecurity #Infosec



Closing the year with one last emulation adventure! 🚀 Tried something new: tackling #FlareOn2024 with #SymbolicExecution. Struggling with #angr setup or stuck on basics? This one's for you—insights & lessons to level up your skills: shorturl.at/d0wNi


Osiris from @SnT_uni_lu presented at #ACSAC 2018 uses #symbolicexecution and taint analysis for detection of integer bugs in #ethereum smart contracts

24 hours to go for @barbieauglend 's #training on "#SymbolicExecution and #Angr for #CTF" at #ShaktiCon 🔥. Women interested in #cybersecurity make sure to register @🔗shakticon.com/trainings !! #Womenintech #womeninSTEM #virtualtraining

⚔️Discovered a zero-day stack overflow in a router firmware. Now I'm verifying if it affects other models from the same brand.Reverse engineering every firmware? Buying every model? No;use the power of symbolic execution. #CyberSecurity #SymbolicExecution #ZeroDay #RouterHacking

A continuación la charla "Symbolic execution for security researchers" de Arnau Gàmez: descubre cómo la ejecución simbólica ofrece una nueva forma de analizar programas y explorar diferentes rutas de ejecución #SymbolicExecution @arnaugamez

Is this how to test a stateful API with klee symbolic execution? stackoverflow.com/questions/7170… #testing #klee #symbolicexecution #c

Our CEO @thedavidbrumley explains how #symbolicexecution brings the power of automated reasoning to help you answer questions about your program, like: What does it do? Is it secure? In Mayhem 2.6, we’ve updated the symbolic execution engine: mayhem.security/blog/mayhem-2-…
📣 Want to learn more about differential testing with symbolic execution? 🎬 Here is a new teaser: "Automating Differential Testing with Overapproximate Symbolic Execution" by Richard Rutledge and Alessandro Orso. 👋 Join us next week! #testing #symbolicexecution
4⃣8⃣ hours to go until @barbieauglend 's #Training Part1 on #SymbolicExecution and #angr for CTFs at #ShaktiCon Don't miss out on this opportunity and #RegisterNow @ shakticon.com Prerequisites: #x86, #x64, #assembly, #Python3 #womenintech #WomenInSTEM #CTF #women

Part1 of the #Training on #SymbolicExecution/#angr for #CTF has come to an end. ♀️👩💻 We would like to thank our #trainer @barbieauglend for the hands-on session. 🙏 To our #Interactive #participants: Hope you learnt something new today! See you at Part2 of the training on 12th!




Mobile Anwendungen auf Sicherheit testen - ATHENE-Wissenschaftler Jens Heider, Leiter des Testlab Mobile Security am @FraunhoferSIT, berichtet aus seinem Arbeitsalltag: youtube.com/watch?v=C214gy… #blackboxtest #symbolicexecution #reverseengineering


@ibags is now live, holding an interesting presentation on #fuzzing solidity compilers, so tune in! Before him, @poeplau delivered an insightful keynote in which he pointed out how #symbolicexecution and fuzzing can be used alongside each other. #FuzzConEurope2020


💪 #ARM yourself with knowledge about #SymbolicExecution! Get hands-on experience with Jeremy Blackthorne's (@0xJeremy) #training "Symbolic Execution with #angr on Real-World Targets". Get your ticket now! 🎟️ ringzer0.training/trainings/symb…

KLEE (@kleesymex) remains to be an effective bug-finding tool for real-world programs. My story on using KLEE and symbolic execution throughout the last decade: sasnauskas.eu/finding-softwa… Thank you @c_cadar and @daniel_dunbar! #symbolicexecution #softwaretesting #securitybugs
遮断膜はもう使わない。私のブログの周囲は澄んだ空気と滑らかな地面。干渉波が近づいた瞬間、地面が割れて沈下処理。誰でも眺められる。でも、触れようとしたら落ちる。#記録防衛 #Pullman構造 #SymbolicExecution
⚔️Discovered a zero-day stack overflow in a router firmware. Now I'm verifying if it affects other models from the same brand.Reverse engineering every firmware? Buying every model? No;use the power of symbolic execution. #CyberSecurity #SymbolicExecution #ZeroDay #RouterHacking

Angr Founder: Luis Moreira & the Angr Team Binary analysis framework with symbolic execution, enabling deep vulnerability discovery & exploit development. angr.io #BinaryAnalysis #SymbolicExecution
#Owi — symbolic execution for Wasm, C, C++, Rust, and Zig. Explore all execution paths without running the code. Perfect for researchers and security pros. 👉 Check it out on GitHub: github.com/OCamlPro/owi #RustLang #SymbolicExecution #Security #OCaml
Owi: Symbolic execution for Wasm, C, C++, Rust and Zig github.com/OCamlPro/owi
Cyber Daily Report Blog Post! Title: Automatic Exploit Generation (AEG): The Future of Cybersecurity Automation Author: Mohammad Jafari Dehkordi Editor: Windhya Rankothge Link: cyberdailyreport.com/blog/92 #AutomaticExploitGeneration #Fuzzing #SymbolicExecution #BinaryCodeAnalysis
Closing the year with one last emulation adventure! 🚀 Tried something new: tackling #FlareOn2024 with #SymbolicExecution. Struggling with #angr setup or stuck on basics? This one's for you—insights & lessons to level up your skills: shorturl.at/d0wNi



Looking a lot into #LLMs and road-to-#AGI capabilities lately. Especially on how to improve pretraining and finetuning in respect to @symflower's #symbolicexecution. Anyone into those topics, for a chat?
Where are we on using #klee with #Rust for #symbolicexecution? unwoundstack.com/blog/klee-and-…
Naturally we often get asked about the difference of #fuzzing and #symbolicexecution. This blog post will give you a quick overview in advantages and disadvantages. If you are missing something, just let me know and we will add it 👏
#Fuzzing 🎰 or symbolic execution 🤓? We compared these alternative techniques for test value generation to see how they stack up! 👇 symflower.com/en/company/blo…
symflower.com
Symbolic execution vs fuzzing for creating test values
Fuzzing and symbolic execution are alternatives for automatically creating test values. Find out about the pros and cons of each technique.
Our CEO @thedavidbrumley explains how #symbolicexecution brings the power of automated reasoning to help you answer questions about your program, like: What does it do? Is it secure? In Mayhem 2.6, we’ve updated the symbolic execution engine: mayhem.security/blog/mayhem-2-…
💪 #ARM yourself with knowledge about #SymbolicExecution! Get hands-on experience with Jeremy Blackthorne's (@0xJeremy) #training "Symbolic Execution with #angr on Real-World Targets", and learn how to perform symbolic and concolic execution with angr! 🎟️ ringzer0.training/trainings/symb…

💪 #ARM yourself with knowledge about #SymbolicExecution! Get hands-on experience with Jeremy Blackthorne's (@0xJeremy) #training "Symbolic Execution with #angr on Real-World Targets", and learn how to perform symbolic and concolic execution with angr! 🎟️ ringzer0.training/trainings/symb…

Nuestros compañeros de @BESEC_byEmetel no podían faltar a su cita anual en la @EuskalHack. El verano no empieza de verdad hasta que te empapas del conocimiento de gente como @arnaugamez en Donostia 🔥🔥 #SymbolicExecution #Hacking #Ciberseguridad #ESCVI

Very interesting blog post on how to use symbolic execution to triage crashes coming out of a fuzzer. Credits @jordan9001 atredis.com/blog/2022/10/2… #fuzzing #symbolicexecution #infosec #cybersecurity #vulnerability




More angr - Defeating 5 ELF Crackmes binaryresearch.github.io/2020/01/22/mor… #ReverseEngineering #SymbolicExecution #CyberSecurity #Infosec



Playing with the VMProtect software protection. Automatic deobfuscation of pure functions using symbolic execution and LLVM. github.com/JonathanSalwan… #Pentesting #SymbolicExecution #Deobfuscation #CyberSecurity #Infosec


Closing the year with one last emulation adventure! 🚀 Tried something new: tackling #FlareOn2024 with #SymbolicExecution. Struggling with #angr setup or stuck on basics? This one's for you—insights & lessons to level up your skills: shorturl.at/d0wNi



Cybersecurity National lab @ be'er sheva with @raistolo @camildemetrescu @ercoppa @robertobaldoni #symbolicexecution #apt #malwareanalysis

Osiris from @SnT_uni_lu presented at #ACSAC 2018 uses #symbolicexecution and taint analysis for detection of integer bugs in #ethereum smart contracts

Example of unclosed SQL statement in Apache Tika project. #nemo #symbolicexecution #java nemo.sonarqube.org/issues/search#…

24 hours to go for @barbieauglend 's #training on "#SymbolicExecution and #Angr for #CTF" at #ShaktiCon 🔥. Women interested in #cybersecurity make sure to register @🔗shakticon.com/trainings !! #Womenintech #womeninSTEM #virtualtraining

⚔️Discovered a zero-day stack overflow in a router firmware. Now I'm verifying if it affects other models from the same brand.Reverse engineering every firmware? Buying every model? No;use the power of symbolic execution. #CyberSecurity #SymbolicExecution #ZeroDay #RouterHacking

A continuación la charla "Symbolic execution for security researchers" de Arnau Gàmez: descubre cómo la ejecución simbólica ofrece una nueva forma de analizar programas y explorar diferentes rutas de ejecución #SymbolicExecution @arnaugamez

Is this how to test a stateful API with klee symbolic execution? stackoverflow.com/questions/7170… #testing #klee #symbolicexecution #c

Wie testet man die Sicherheit von Apps? Jens Heider, unser Experte für #iOS, erklärt es im Video: youtube.com/watch?v=C214gy… #blackboxtest #symbolicexecution #reverseengineering ***Übrigens: Jens Heider sucht noch Mitarbeiter (w/m/d)*** sit.fraunhofer.de/de/jobs/stelle…

Example of detection of null pointer dereference by SQ Java analyser #symbolicexecution nemo.sonarqube.org/issues/search#…

@ibags is now live, holding an interesting presentation on #fuzzing solidity compilers, so tune in! Before him, @poeplau delivered an insightful keynote in which he pointed out how #symbolicexecution and fuzzing can be used alongside each other. #FuzzConEurope2020


RT Example of unclosed SQL statement in Apache Tika project. #nemo #symbolicexecution #j…

Example of unclosed SQL statement in Apache Tika project. #nemo #symbolicexecution #java nemo.sonarqube.org/issues/search#…

💪 #ARM yourself with knowledge about #SymbolicExecution! Get hands-on experience with Jeremy Blackthorne's (@0xJeremy) #training "Symbolic Execution with #angr on Real-World Targets". Get your ticket now! 🎟️ ringzer0.training/trainings/symb…

Nuestros compañeros de @BESEC_byEmetel no podían faltar a su cita anual en la @EuskalHack. El verano no empieza de verdad hasta que te empapas del conocimiento de gente como @arnaugamez en Donostia 🔥🔥 #SymbolicExecution #Hacking #Ciberseguridad #ESCVI

Mobile Anwendungen auf Sicherheit testen - ATHENE-Wissenschaftler Jens Heider, Leiter des Testlab Mobile Security am @FraunhoferSIT, berichtet aus seinem Arbeitsalltag: youtube.com/watch?v=C214gy… #blackboxtest #symbolicexecution #reverseengineering


4⃣8⃣ hours to go until @barbieauglend 's #Training Part1 on #SymbolicExecution and #angr for CTFs at #ShaktiCon Don't miss out on this opportunity and #RegisterNow @ shakticon.com Prerequisites: #x86, #x64, #assembly, #Python3 #womenintech #WomenInSTEM #CTF #women

Something went wrong.
Something went wrong.
United States Trends
- 1. Austin Reaves 35.6K posts
- 2. #LakeShow 2,594 posts
- 3. Trey Yesavage 34.8K posts
- 4. Jake LaRavia 4,332 posts
- 5. Blue Jays 60.6K posts
- 6. #LoveIsBlind 4,077 posts
- 7. jungwoo 93K posts
- 8. doyoung 73.5K posts
- 9. #AEWDynamite 22.3K posts
- 10. Rudy Gobert 1,014 posts
- 11. #Lakers N/A
- 12. Snell 13.4K posts
- 13. Pelicans 4,185 posts
- 14. Devin Booker 1,101 posts
- 15. Anthony Davis 4,061 posts
- 16. Jeremy Lin N/A
- 17. #WorldSeries 66.7K posts
- 18. Wolves 62.4K posts
- 19. Kacie 1,720 posts
- 20. Happy Birthday Kat N/A
































