#bluetoothvulnerabilities результаты поиска
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution dlvr.it/TMPRhH #Cybersecurity #BluetoothVulnerabilities #RemoteCodeExecution #OpenSynergy #PerfektBlue

Spanish researchers found 29 undocumented Bluetooth commands in the ESP32 microchip, endangering 1 billion devices with risks like impersonation and unauthorized access. #Spain #IoTSecurity #BluetoothVulnerabilities link: ift.tt/b5xpadV

🚗 Bluetooth flaws dubbed "PerfektBlue" impact Mercedes, Volkswagen, and Skoda vehicles—potentially exposing drivers to remote attacks. Patch and protect your ride. #CarSecurity #BluetoothVulnerabilities 🔧📡 buff.ly/lIoH9ki
How to Hack Bluetooth Devices: 5 Common Vulnerabilities hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities #cybersecurity #bluetoothdevices #hackbluetoothdevices #wirelesstechnology #hackernoontopstory
Ecovacs robot vacuums have severe Bluetooth vulnerabilities that let hackers remotely spy on users and propagate attacks to other devices. #RobotVacuums #BluetoothVulnerabilities #Hacking haywaa.com/article/ecovac…
haywaa.com
- Haywaa
- Haywaa
"How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
Contact #tracingapps unsafe if #Bluetoothvulnerabilities not fixed go.newsfusion.com/security/item/…
hackernoon: "How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution dlvr.it/TMPRhH #Cybersecurity #BluetoothVulnerabilities #RemoteCodeExecution #OpenSynergy #PerfektBlue

🚗 Bluetooth flaws dubbed "PerfektBlue" impact Mercedes, Volkswagen, and Skoda vehicles—potentially exposing drivers to remote attacks. Patch and protect your ride. #CarSecurity #BluetoothVulnerabilities 🔧📡 buff.ly/lIoH9ki
Spanish researchers found 29 undocumented Bluetooth commands in the ESP32 microchip, endangering 1 billion devices with risks like impersonation and unauthorized access. #Spain #IoTSecurity #BluetoothVulnerabilities link: ift.tt/b5xpadV

Ecovacs robot vacuums have severe Bluetooth vulnerabilities that let hackers remotely spy on users and propagate attacks to other devices. #RobotVacuums #BluetoothVulnerabilities #Hacking haywaa.com/article/ecovac…
haywaa.com
- Haywaa
- Haywaa
hackernoon: "How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
"How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
How to Hack Bluetooth Devices: 5 Common Vulnerabilities hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities #cybersecurity #bluetoothdevices #hackbluetoothdevices #wirelesstechnology #hackernoontopstory
hackernoon: "How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
"How to Hack Bluetooth Devices: 5 Common Vulnerabilities" hackernoon.com/how-to-hack-bl… #bluetooth #bluetoothvulnerabilities
Contact #tracingapps unsafe if #Bluetoothvulnerabilities not fixed go.newsfusion.com/security/item/…
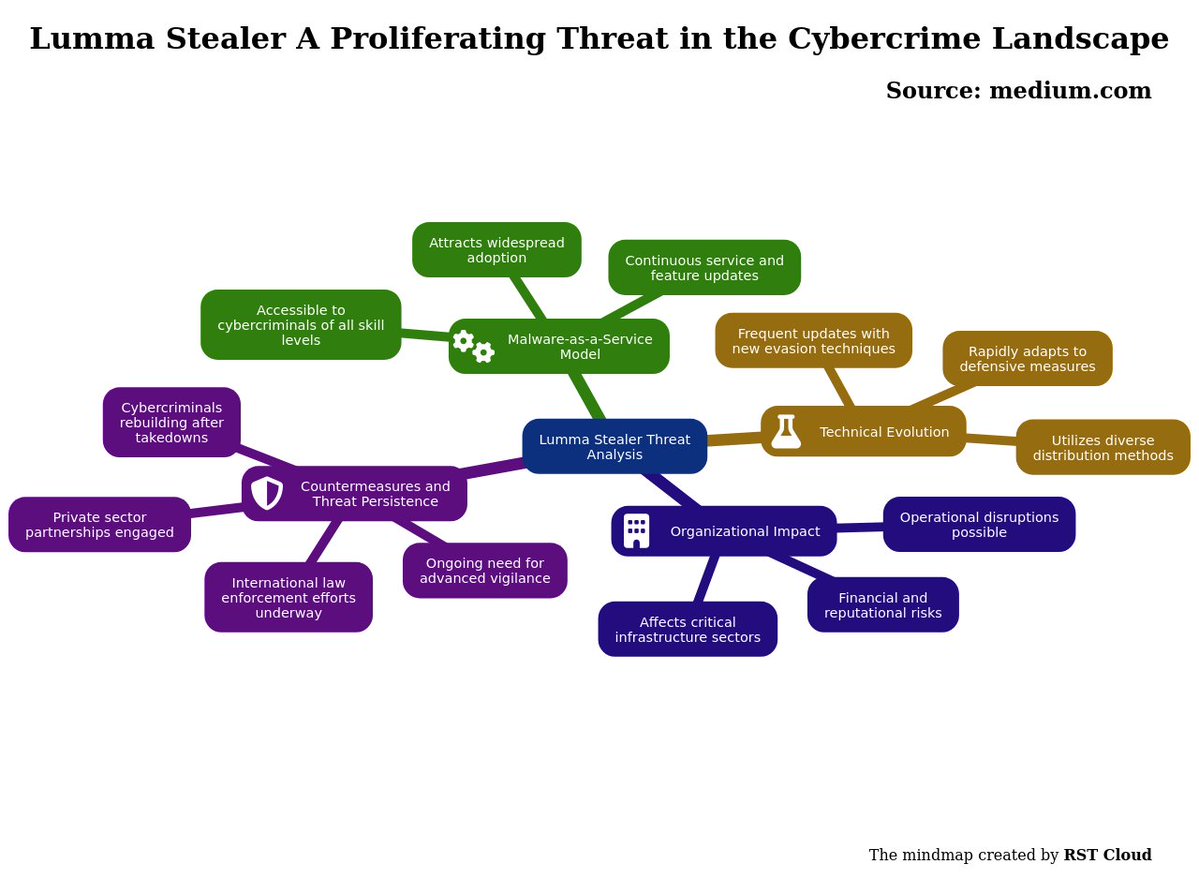
#threatreport #HighCompleteness Lumma Stealer A Proliferating Threat in the Cybercrime Landscape | 27-07-2025 Source: medium.com/@raghavtiresea… Key details below ↓ 🧑💻Actors/Campaigns: Shamel Storm-2477 Sticky_werewolf 0ktapus 💀Threats: Lumma_stealer, Zeus,…
[CVE-2025-9265: CRITICAL] Critical cybersecurity alert: Kiloview NDI N30 device vulnerability could grant unauthorized access. Update firmware to version 2.02.0246 to fix this issue. #cybersecurity#cve,CVE-2025-9265,#cybersecurity cvefind.com/CVE-2025-9265
![CveFindCom's tweet image. [CVE-2025-9265: CRITICAL] Critical cybersecurity alert: Kiloview NDI N30 device vulnerability could grant unauthorized access. Update firmware to version 2.02.0246 to fix this issue. #cybersecurity#cve,CVE-2025-9265,#cybersecurity cvefind.com/CVE-2025-9265](https://pbs.twimg.com/media/G3H21QeXcAAuy72.jpg)
A popular NPM package got compromised, attackers updated it to run a post-install script that steals secrets But the script is a *prompt* run by the user's installation of Claude Code. This avoids it being detected by tools that analyze code for malware You just got vibepwned

Discovered 600+ #Bluetooth devices at the airport. Wonder how many of them are patched against Bluetooth pairing vulnerability that leads to 0-click RCE (CVE-2023-45866) #BlueDucky mobile-hacker.com/2024/03/26/blu…
Bluetooth Hacking, Parts 1-4 #bluetooth #bluetoothhacking #multiblue #cybersecurity #cyberwarrior hackers-arise.com/hacking-blueto…

[CVE-2025-8915: HIGH] Hardcoded TLS private key and certificate in firmware in Kiloview N30 2.02.246 allows malicious adversary to do a Mann-in-the-middle attack via the network#cve,CVE-2025-8915,#cybersecurity cvefind.com/CVE-2025-8915
![CveFindCom's tweet image. [CVE-2025-8915: HIGH] Hardcoded TLS private key and certificate in firmware in Kiloview N30 2.02.246 allows malicious adversary to do a Mann-in-the-middle attack via the network#cve,CVE-2025-8915,#cybersecurity cvefind.com/CVE-2025-8915](https://pbs.twimg.com/media/G3H23oRWQAAo5V3.jpg)
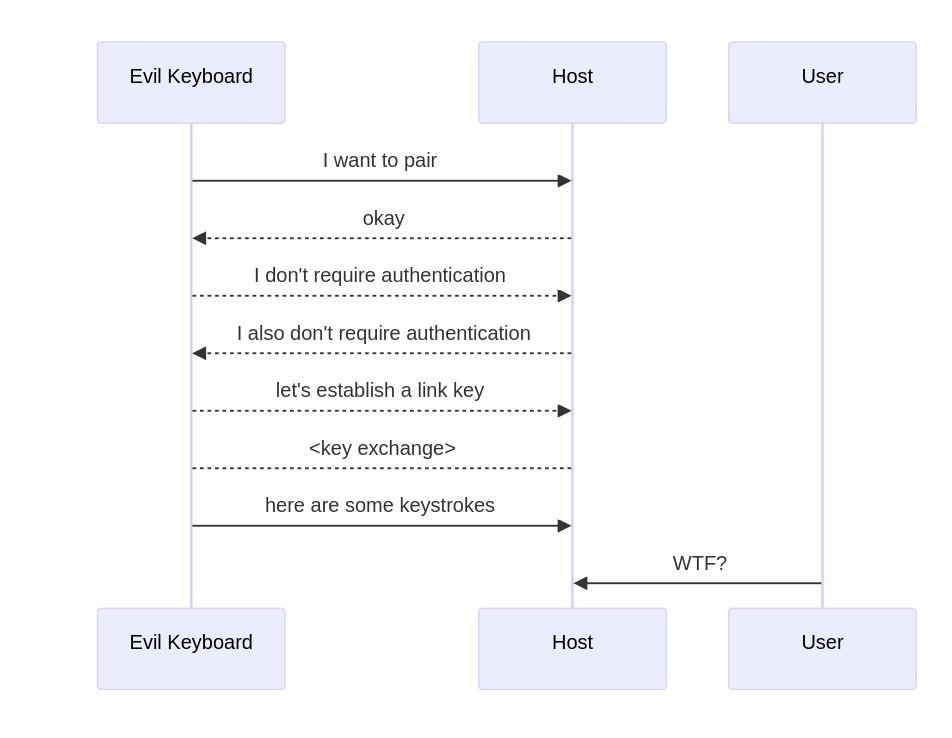
Hi, My Name is Keyboard This repository contains proof-of-concept scripts for CVE-2023-45866, CVE-2024-21306, and CVE-2024-0230 Bluetooth vulnerabilities in Android, Linux, macOS, iOS and #Windows can be exploited to pair an emulated Bluetooth keyboard and inject keystrokes…


Material on the BarkTooth bluetooth vulnerabilities family Nice reading! WP: asset-group.github.io/disclosures/br… PoC: github.com/Matheus-Garbel… Web: asset-group.github.io/disclosures/br… #bluetooth #infosec #wireless #cybersecurity #vulnerability #hacking


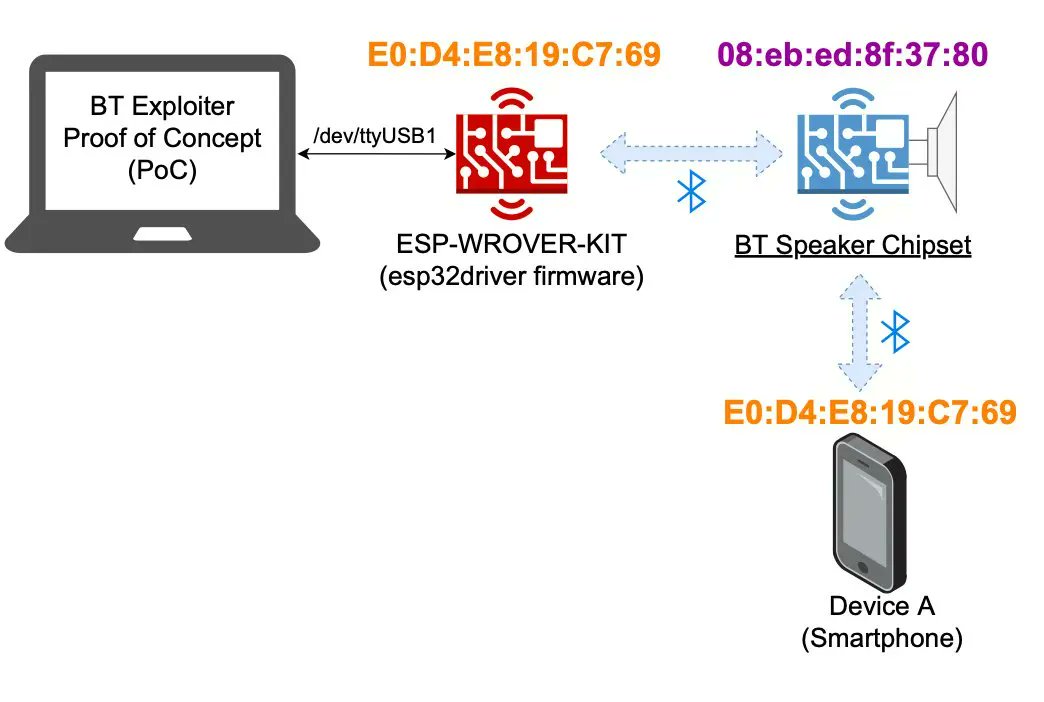

If you're interested in bluetooth low level hacking take a look at this cool project by Matheus Eduardo Garbelini (@MatheusGarbelin) Active Bluetooth BR/EDR Sniffer/Injector: github.com/Matheus-Garbel… #bluetooth #esp32 #espressif #hacking #infosec

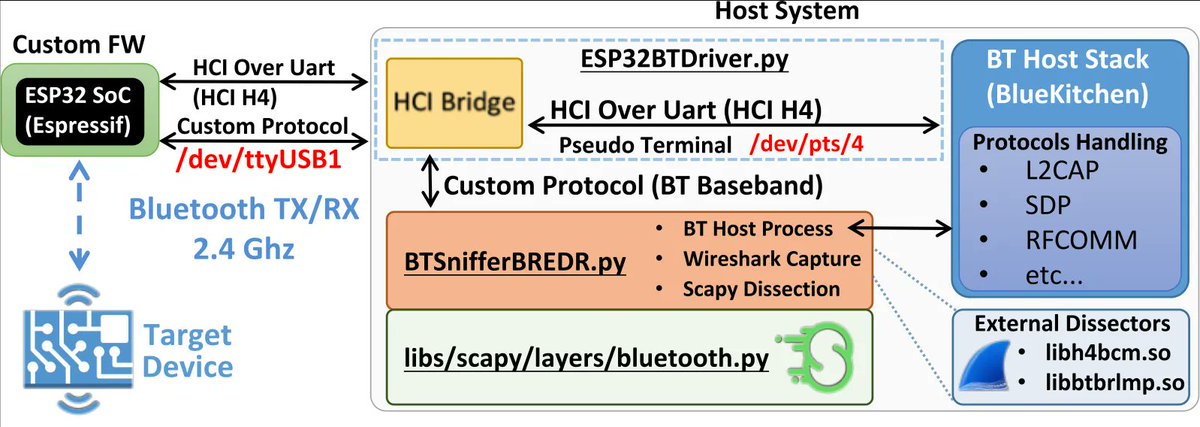
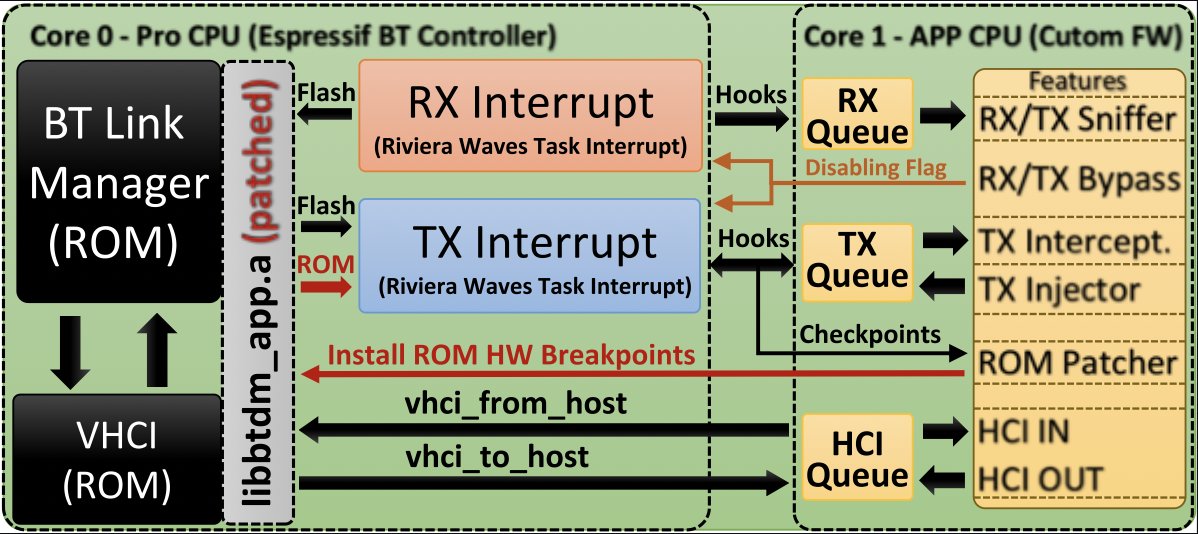
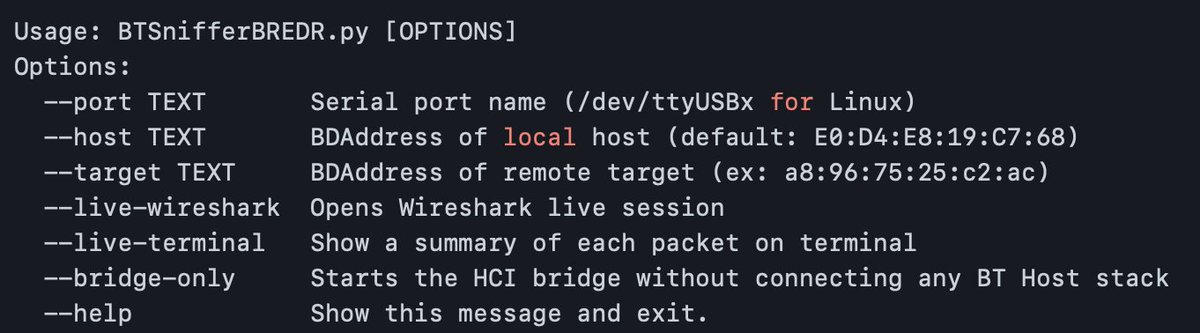
Bluetooth Hacking, Part 2: Bluetooth Recon #bluetooth #bluetoothhacking #multiblue #cybersecurity #CyberWarrior hackers-arise.com/post/2018/01/3…

🔵 Bluetooth Hacking: A comprehensive guide! Part 1: hackers-arise.com/post/bluetooth… Part 2: hackers-arise.com/post/2018/01/3… #cybersecurity #infosec #hacking #BugBounty #bugbountytips



Bluetooth vulnerabilities in Android, Linux, macOS, iOS and Windows can be exploited to pair an emulated bluetooth keyboard and inject keystrokes without user confirmation : github.com/skysafe/reblog… credits @marcnewlin Slides : github.com/marcnewlin/hi_… CVE's : CVE-2024-0230…
🔥 BLURtooth (CVE-2020-15802) A new unpatched #Bluetooth pairing vulnerability could let attackers bypass authentication and easily target vulnerable nearby devices. Read details — thehackernews.com/2020/09/new-bl… #infosec #cybersecurity #tech

🔍 Bluetooth Security Awareness: Understanding Mobile Device Vulnerabilities 🛡️ 📱 🔐

SweynTooth vulerabilities family. Cool reading for anyone interested in Bluetooth security and hacking. White paper: asset-group.github.io/disclosures/sw… PoCs: github.com/Matheus-Garbel… Vuln site: asset-group.github.io/disclosures/sw… #infosec #wireless #bluetooth #cybersecurity
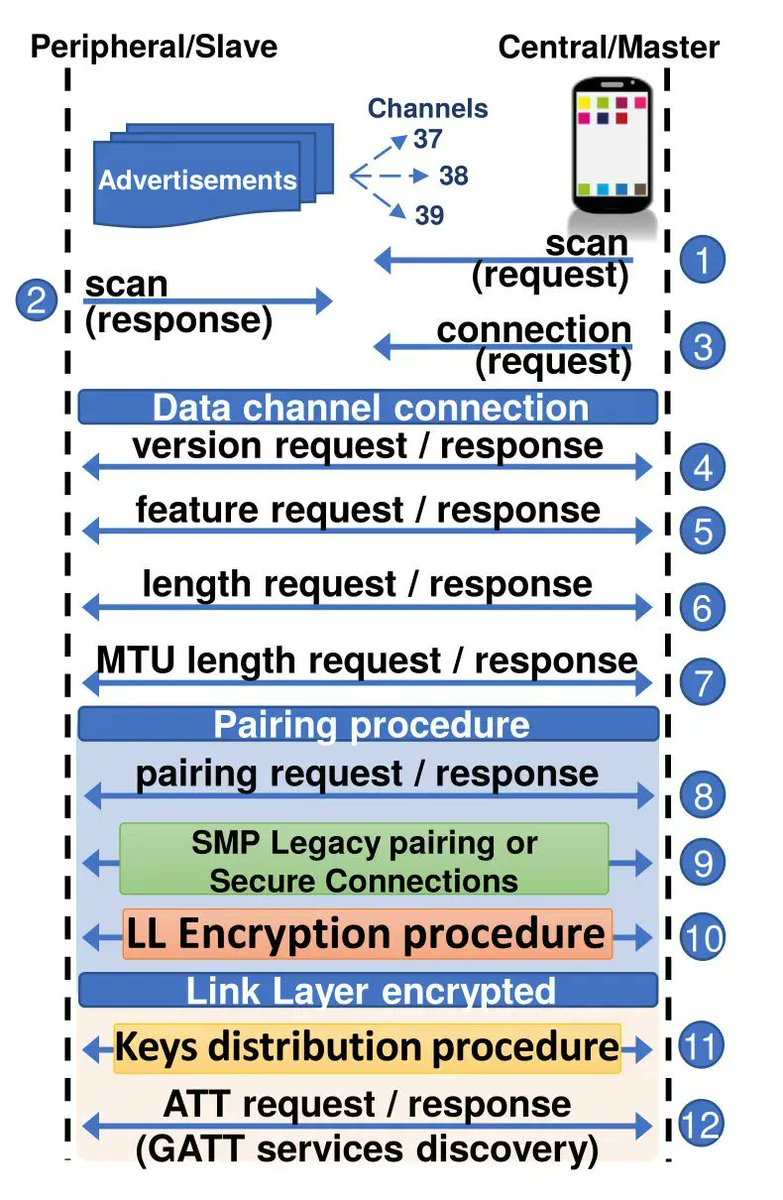

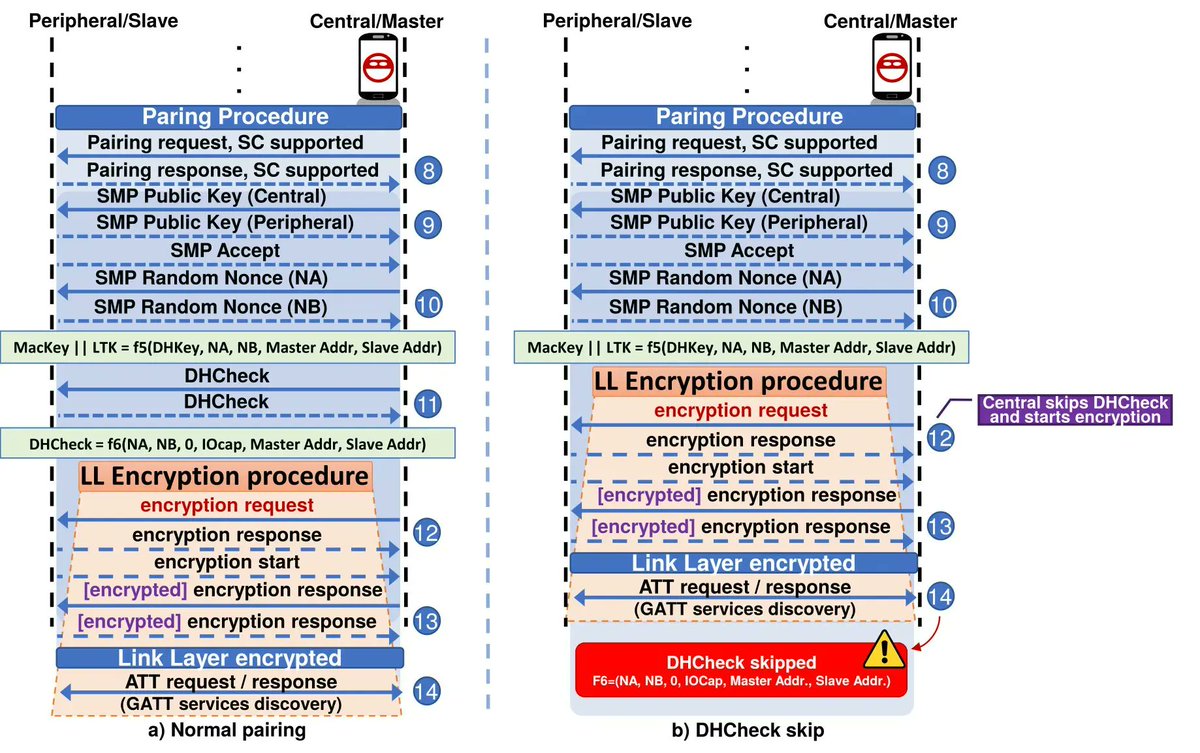

Bluetooth Hacking, Parts 1-4 #bluetooth #bluetoothhacking #multiblue #cybersecurity #cyberwarrior hackers-arise.com/hacking-blueto…

Hackers just turned GitHub into their command center. When police take down their servers, the malware just… reboots itself from GitHub. The twist? It hides configs inside images using steganography. This isn’t a glitch — it’s resilience by design. Read how it works →…

Something went wrong.
Something went wrong.
United States Trends
- 1. Branch 37K posts
- 2. Chiefs 111K posts
- 3. Red Cross 50.4K posts
- 4. Exceeded 5,990 posts
- 5. Mahomes 34.6K posts
- 6. Binance DEX 5,188 posts
- 7. #njkopw 5,858 posts
- 8. #LaGranjaVIP 82.2K posts
- 9. Air Force One 56.3K posts
- 10. Rod Wave 1,623 posts
- 11. #TNABoundForGlory 59.1K posts
- 12. #LoveCabin 1,363 posts
- 13. Alon Ohel 16.2K posts
- 14. Tel Aviv 59.3K posts
- 15. Ziv Berman 18.4K posts
- 16. Eitan Mor 15.2K posts
- 17. Omri Miran 15.5K posts
- 18. Bryce Miller 4,594 posts
- 19. LaPorta 12.2K posts
- 20. Matan Angrest 14.7K posts