#botnetattack search results
Ever wondered how cybercriminals control hundreds or thousands of infected devices at once? 🤖 These are called Botnets — and they come in many forms! #CyberSecurityAwareness #BotnetAttack #InfoSec #OnlineSafety #Senselearner

New research from Cato CTRL, reported by Tom’s Hardware, reveals that the Ballista botnet is actively targeting TP-Link Archer AX-21 routers via a high-severity RCE vulnerability. For more details, tap the link in our bio #CyberSecurity #BotnetAttack #TPLINK

ASUS routers compromised as new botnet injects SSH keys, evades detection, and survives reboots, posing persistent global backdoor threat. #CyberSecurity #BotnetAttack #ASUSRouters

Androxgh0st botnet hijacks U.S. university servers to expand global reach, targeting cloud apps and credentials in new cyber campaign. #CyberSecurity #BotnetAttack #CloudSecurity

This is what a #botnetattack looks like #learnwithsmartsecurityscan 📚 #smartsecurityscan 🔍 #cybersecurity #networksecurity #infosec #internetsecurity #digitalassets #compliance #riskmanagement #itsecurity
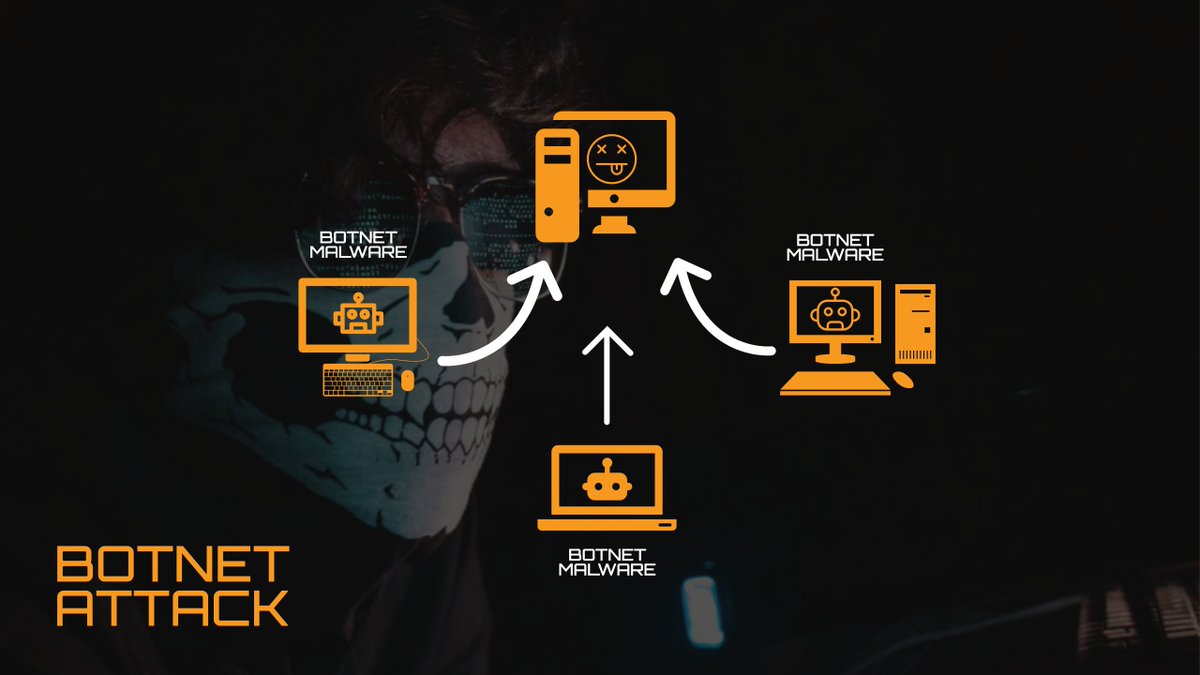
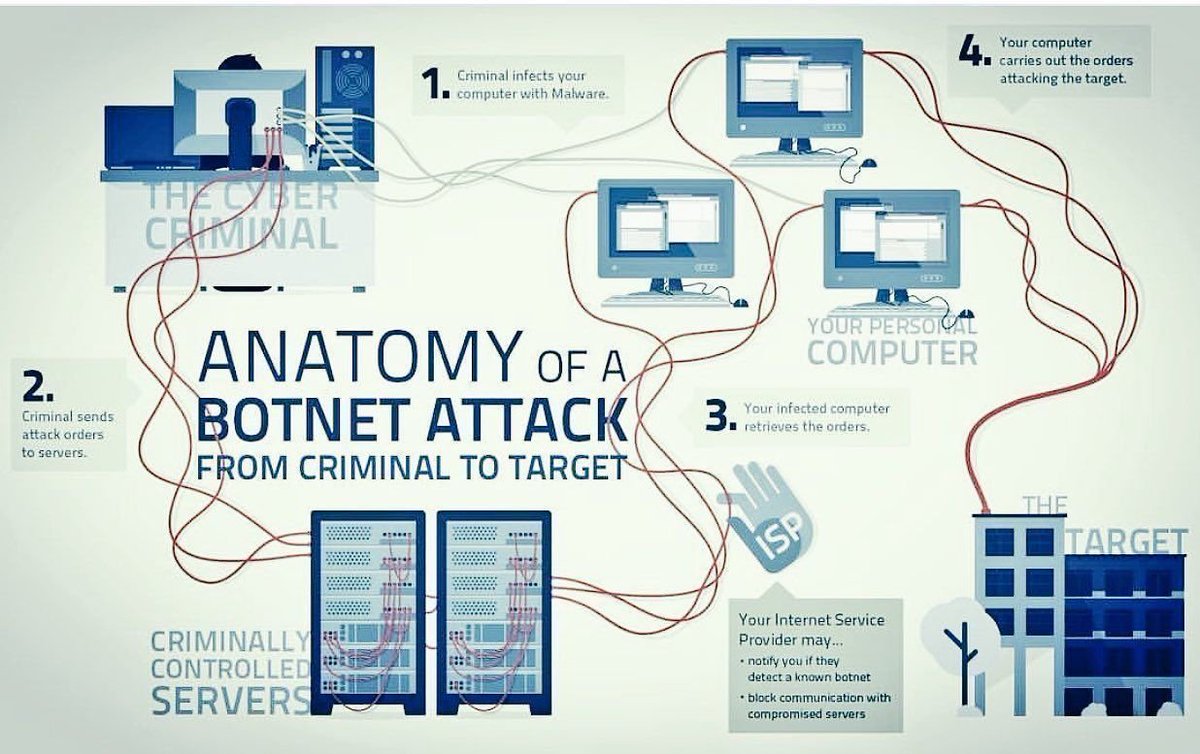
Want to learn about the anatomy of a botnet attack from criminal to target? The first step is when your computer is infected with Malware, then attack orders are sent to servers. Then what happens? Check the image below. Via The Cyber Security Hub #Cybersecurity #BotnetAttack

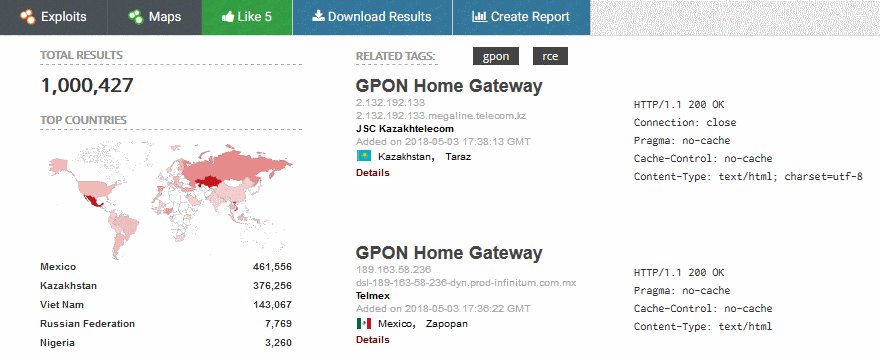
Vulnerabilities Affecting Over One Million Dasan GPON Routers Are Now Under Attack bit.ly/2wcTAXN #router #Dasan #botnetattack
What happens during a #botnetattack? Let @BullGuard protect so you never have to experience it firsthand!

Did you know? 84% of people will not make a purchase if they are dealing with an unsecured website. Make your website secure!. #BotnetAttack #Bots #CyberAttacks #WebsiteProtection #BeFutureReady #TechAffinity

Continuing #learnwithsmartsecurityscan lessons. Today's Lesson📚: What is a #Botnetattack ? 🕵 ️#smartsecurityscan #cybersecurity #networksecurity #iot #compliance #riskmanagement #digitalassets #vpn #sslcertificate #infosec #internetsecurity #enterprisesecurity

8/11 Botnet malware is exploiting ICS for DDoS and data destruction. Default credentials are the weak link. #BotnetAttack #SecureCredentials 🔒
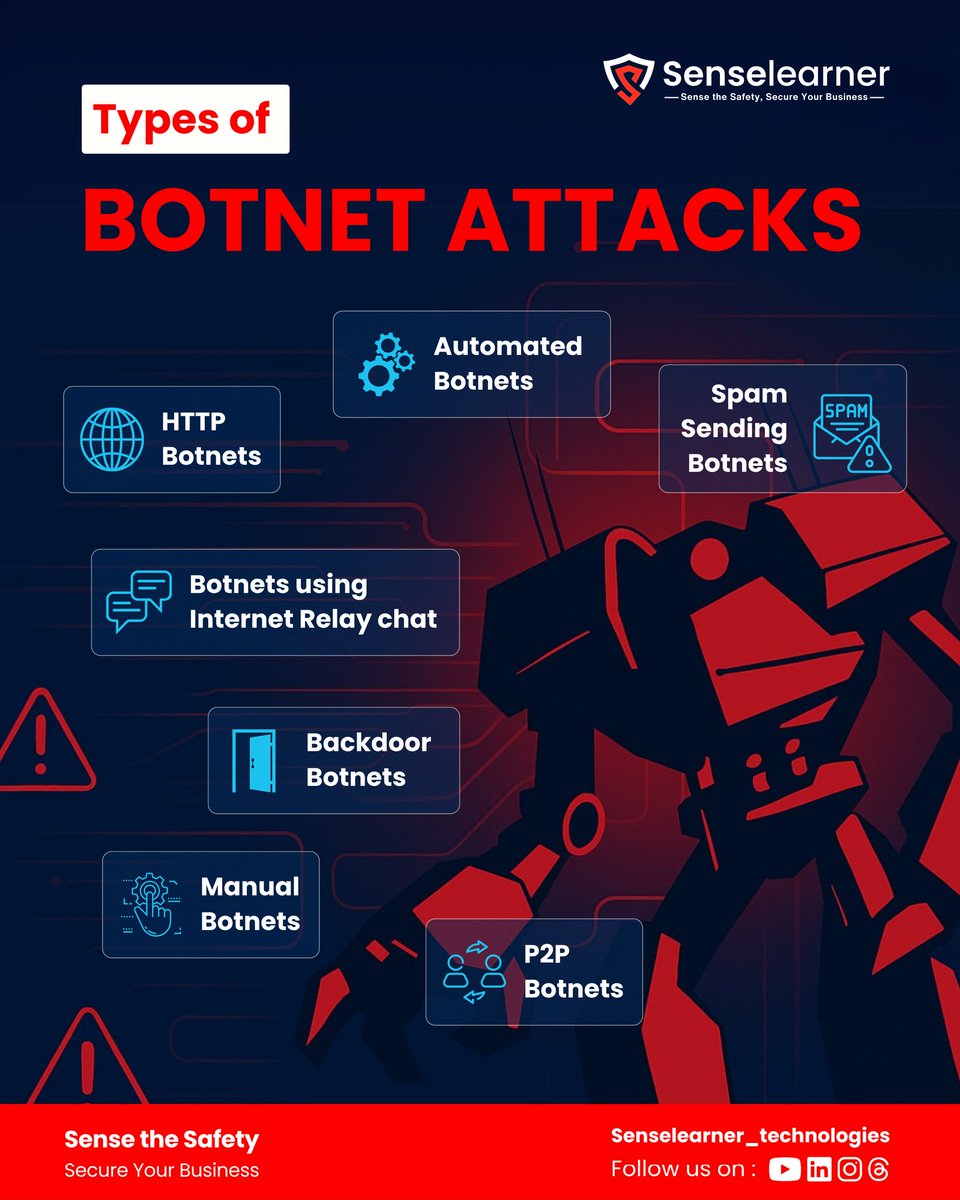
Today we discuss about "Botnet" Botnets are networks of hijacked computer devices used to conduct scams and cyberattacks. #Botnet #BotnetAttack #BotnetMalware #ttbinternetsecurity #BotnetSecurity #ttbantivirus #BotnetDetection #ttb #botnetscams #botnetsecurity
#BlueKeep #Botnet #Botnetattack Prometei Botnet: The Persistent Threat Targeting Global Systems cysecurity.news/2024/10/promet…

Palo Alto Detects New Prometei Botnet Attacks Targeting Linux Servers cysecurity.news/2025/06/palo-a… #Botnet #Botnetattack #cryptocurrencymining

Botnets have many positive purposes & uses, but they can be used maliciously in the form of a botnet attack. To learn what is a botnet attack & how to protect yourself, see the link: - ow.ly/uBwq50z01Pm - #CyberMonday #CyberSecurity #BotnetAttack #KCG #KlettConsultingGroup

⚠️🔒 Gafgyt botnet targets #vulnerable Zyxel routers! 💻 Thousands of daily attacks exploit an unpatched 2017 vulnerability. Upgrade your firmware to protect against takeover. 💪🛡️ #Cybersecurity #BotnetAttack #ProtectYourNetwork 🔐✅

The RondoDox botnet exploits a critical RCE vulnerability (CVE-2025-24893) in XWiki versions before 15.10.11 and 16.4.1, deploying remote shells and crypto miners since November. #XWikiFlaw #BotnetAttack #RondoDox ift.tt/7BS3YmD
RondoDox botnet exploits unpatched XWiki servers via critical CVE-2025-24893 vulnerability to deploy crypto miners and launch DDoS attacks. Exploitation began in March, surging in Nov 2025. #XWikiExploit #BotnetAttack #France ift.tt/45zdWek
A massive botnet from over 100,000 IPs across multiple countries, including Brazil, targets US RDP services using RD Web Access timing and login enumeration attacks. Enhanced RDP defenses recommended. #RemoteAccess #BotnetAttack #Brazil ift.tt/Kw4BLpO
RondoDox botnet leverages an exploit shotgun targeting 50+ vulnerabilities across 30+ vendors, compromising routers, DVRs, and CCTV worldwide since mid-2025. Key CVEs: 2023-1389, 2024-3721, 2024-12856. #BotnetAttack #ExploitShotgun #GlobalThreat ift.tt/1dfwNcL
Prometei botnet cilja Linux servere sajberinfo.com/2025/07/01/pro… #botnetattack #credentialtheft #cryptominingmalware #cryptominingthreats #dataexfiltration #linuxexploit #linuxserversattacked #monerominer #prometeibotnet #serverexploitation #serversecurity
sajberinfo.com
Prometei botnet cilja Linux servere - Sajber Info Security
Nedavna ponovna pojava Prometei botnet mreže inficiranih uređaja je istakla zabrinutost za administratore Linux servera širom sveta, pokazuje istraživanje
Palo Alto Detects New Prometei Botnet Attacks Targeting Linux Servers cysecurity.news/2025/06/palo-a… #Botnet #Botnetattack #cryptocurrencymining

Androxgh0st botnet hijacks U.S. university servers to expand global reach, targeting cloud apps and credentials in new cyber campaign. #CyberSecurity #BotnetAttack #CloudSecurity

What Is a Botnet Attack in Cyber Security and How To Prevent Learn what a botnet attack is and simple steps you can take to keep your systems safe online. skillogic.com/blog/what-is-a… #cybersecuritycourse #botnetattack #skillogiccybersecuritycourse #skillogicinstitute
ASUS routers compromised as new botnet injects SSH keys, evades detection, and survives reboots, posing persistent global backdoor threat. #CyberSecurity #BotnetAttack #ASUSRouters

Ever wondered how cybercriminals control hundreds or thousands of infected devices at once? 🤖 These are called Botnets — and they come in many forms! #CyberSecurityAwareness #BotnetAttack #InfoSec #OnlineSafety #Senselearner


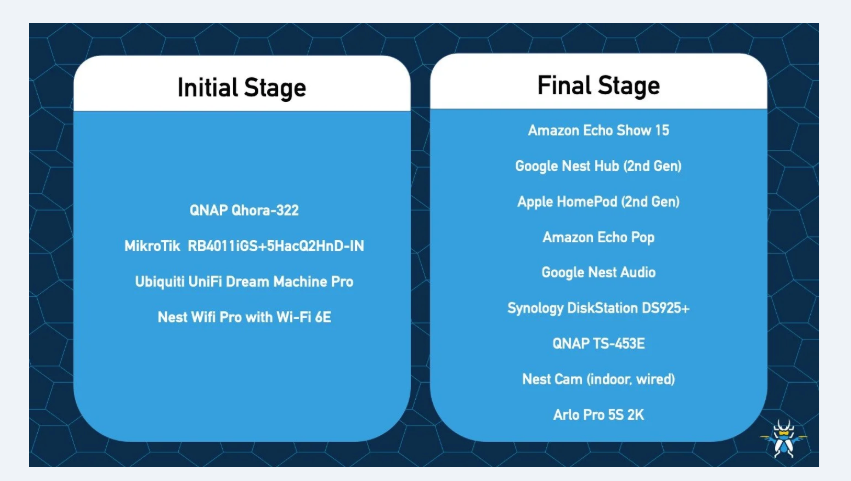
A new botnet, AyySSHush, has compromised over 9,000 ASUS routers by exploiting a vulnerability. Update firmware, check for suspicious activity, and reset if infected. #ASUSRouter #BotnetAttack #AyySSHush #Cybersecurity #RouterSecurity securityexpress.info/over-9000-asus…
New research from Cato CTRL, reported by Tom’s Hardware, reveals that the Ballista botnet is actively targeting TP-Link Archer AX-21 routers via a high-severity RCE vulnerability. For more details, tap the link in our bio #CyberSecurity #BotnetAttack #TPLINK

🚨 Massive Botnet Targets Microsoft 365 Accounts! A 130,000+ device botnet is bypassing MFA to hack Microsoft 365 accounts via password-spraying attacks! #CyberSecurity #Microsoft365 #BotnetAttack #MFABypass #InfoSec #PasswordSpraying #ThreatAlert scworld.com/news/botnet-of…
scworld.com
Botnet of 130,000 compromised devices targets Microsoft 365 accounts
Attackers target password spraying attacks on Microsoft 365 accounts to run account takeovers.
🚨 Cyber Alert! Over 13,000 MikroTik routers have been hijacked by a botnet, fueling malspam campaigns and other cyberattacks. Is your network safe from this growing threat? 🛡️ 💡Secure your devices. Contact us:ow.ly/Y5F850UL7Xq . . . #BotnetAttack #MikroTik #Safeaeon

This is what a #botnetattack looks like #learnwithsmartsecurityscan 📚 #smartsecurityscan 🔍 #cybersecurity #networksecurity #infosec #internetsecurity #digitalassets #compliance #riskmanagement #itsecurity

Continuing #learnwithsmartsecurityscan lessons. Today's Lesson📚: What is a #Botnetattack ? 🕵 ️#smartsecurityscan #cybersecurity #networksecurity #iot #compliance #riskmanagement #digitalassets #vpn #sslcertificate #infosec #internetsecurity #enterprisesecurity

What happens during a #botnetattack? Let @BullGuard protect so you never have to experience it firsthand!

Did you know? 84% of people will not make a purchase if they are dealing with an unsecured website. Make your website secure!. #BotnetAttack #Bots #CyberAttacks #WebsiteProtection #BeFutureReady #TechAffinity

Want to learn about the anatomy of a botnet attack from criminal to target? The first step is when your computer is infected with Malware, then attack orders are sent to servers. Then what happens? Check the image below. Via The Cyber Security Hub #Cybersecurity #BotnetAttack

New research from Cato CTRL, reported by Tom’s Hardware, reveals that the Ballista botnet is actively targeting TP-Link Archer AX-21 routers via a high-severity RCE vulnerability. For more details, tap the link in our bio #CyberSecurity #BotnetAttack #TPLINK

Ever wondered how cybercriminals control hundreds or thousands of infected devices at once? 🤖 These are called Botnets — and they come in many forms! #CyberSecurityAwareness #BotnetAttack #InfoSec #OnlineSafety #Senselearner


#BlueKeep #Botnet #Botnetattack Prometei Botnet: The Persistent Threat Targeting Global Systems cysecurity.news/2024/10/promet…

ASUS routers compromised as new botnet injects SSH keys, evades detection, and survives reboots, posing persistent global backdoor threat. #CyberSecurity #BotnetAttack #ASUSRouters

Androxgh0st botnet hijacks U.S. university servers to expand global reach, targeting cloud apps and credentials in new cyber campaign. #CyberSecurity #BotnetAttack #CloudSecurity

⚠️🔒 Gafgyt botnet targets #vulnerable Zyxel routers! 💻 Thousands of daily attacks exploit an unpatched 2017 vulnerability. Upgrade your firmware to protect against takeover. 💪🛡️ #Cybersecurity #BotnetAttack #ProtectYourNetwork 🔐✅

Palo Alto Detects New Prometei Botnet Attacks Targeting Linux Servers cysecurity.news/2025/06/palo-a… #Botnet #Botnetattack #cryptocurrencymining

Vulnerabilities Affecting Over One Million Dasan GPON Routers Are Now Under Attack bit.ly/2wcTAXN #router #Dasan #botnetattack

Today we discuss about "Botnet" Botnets are networks of hijacked computer devices used to conduct scams and cyberattacks. #Botnet #BotnetAttack #BotnetMalware #ttbinternetsecurity #BotnetSecurity #ttbantivirus #BotnetDetection #ttb #botnetscams #botnetsecurity

Two Hackers Plead Guilty to Creating & Using Mirai Botnet for Massive DDoS Attacks dlvr.it/Q6x5cZ #Botnetattack #ddosattack via @TheHackersNews

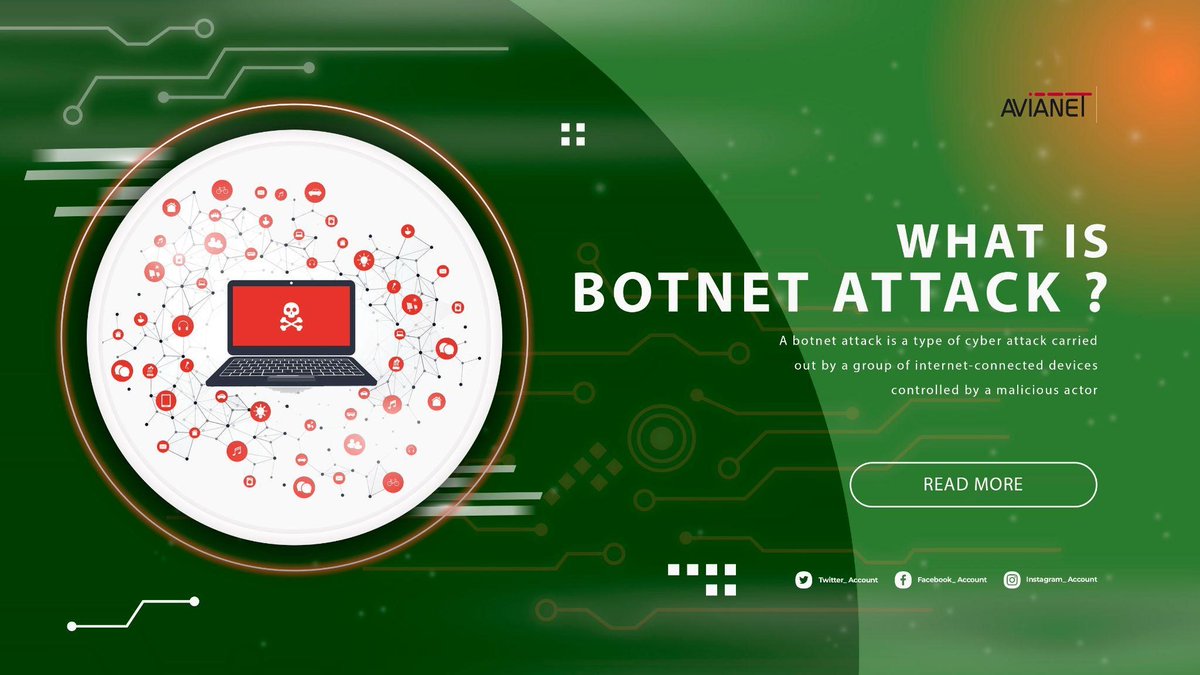
Do You Have Idea That What is a #botnetattack and How Does It Work? Connect with AVIANET to know more about #technology updates #cybersecurityawareness #cyberattack Get in touch - avianet.aero
Someone is Using Mirai Botnet to Shut Down Internet… rd.cempal.com/MbpNgJ #Botnetattack #ddosattack #DistributedDenialofServiceattacks

Botnets have many positive purposes & uses, but they can be used maliciously in the form of a botnet attack. To learn what is a botnet attack & how to protect yourself, see the link: - ow.ly/uBwq50z01Pm - #CyberMonday #CyberSecurity #BotnetAttack #KCG #KlettConsultingGroup

Something went wrong.
Something went wrong.
United States Trends
- 1. Everton 106K posts
- 2. Comey 150K posts
- 3. GeForce Season 2,676 posts
- 4. Amorim 40.5K posts
- 5. Seton Hall 1,764 posts
- 6. Manchester United 66.1K posts
- 7. Pickford 7,528 posts
- 8. Mark Kelly 97.6K posts
- 9. #MUNEVE 13.5K posts
- 10. Dorgu 16K posts
- 11. #MUFC 20.4K posts
- 12. Opus 4.5 6,780 posts
- 13. Zirkzee 19.7K posts
- 14. Gueye 25.9K posts
- 15. Keane 16.3K posts
- 16. Amad 10.9K posts
- 17. Maui 4,301 posts
- 18. Hegseth 36.2K posts
- 19. UCMJ 14.8K posts
- 20. Man U 31.4K posts