#codingvulnerabilities نتائج البحث
Interested in learning how to shore up exposure from #CodingVulnerabilities and prove #Resilience against #AppSec risks? Register for our March 7th webinar to learn how to build cyber capabilities across application development teams: hubs.ly/Q02mcMVN0

A shocking 79% of code goes out with known vulnerabilities! That’s why you need Codebashing to: 🔐Secure your code and open source components 📈Track, manage, and remediate at scale 💪Empower developers with training #CodingVulnerabilities #SecureCode #SecurityFirst

79% of code is shipped with known vulnerabilities. That’s why you need Codebashing to: 📈Gain full control and visibility 👨🏻🎓Identify areas that need improvement 💡Tailor secure code training to your needs #CodingVulnerabilities #Codebashing #FlexibleTrainingProgram
Interested in learning how to shore up exposure from #CodingVulnerabilities and prove #Resilience against #AppSec risks? Register for our March 7th webinar to learn how to build cyber capabilities across application development teams: hubs.ly/Q02mcMVN0

🤔Confused after collecting Subdomains. Then checkout this different types of Vulnerability checklist 👇 github.com/Az0x7/vulnerab… #bugbounty #bugbountytips #bughunting #penetrationtester #penetrationtesting #github
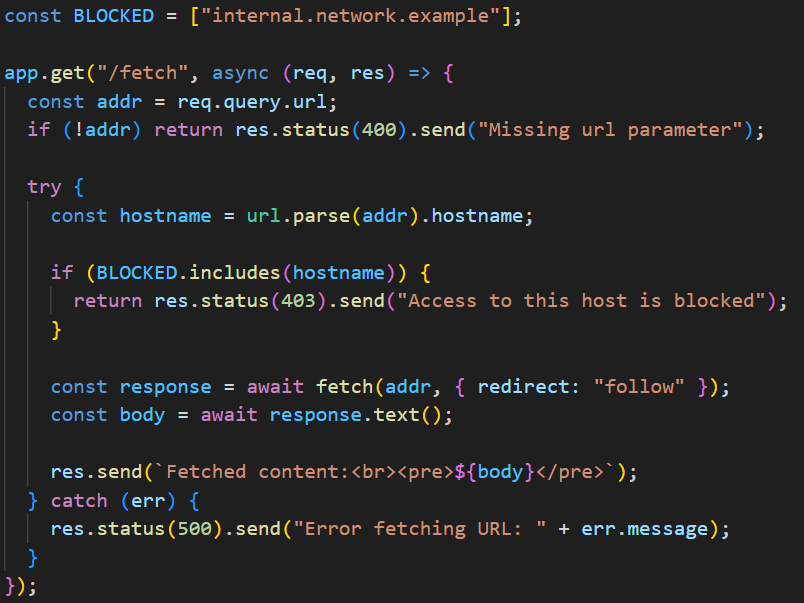
Hackers 🔥 This code contains at least 2 serious vulnerabilities. Can you spot them? 😋 What would be your exploit? 🤔
Digging up old path traversal vulnerabilities? 🕵️♂️ I built this scanner for CVE-2022-37122 to help you find these classic bugs on your authorized targets: Github Tool: github.com/bughuntar/CVE-… #Cybersecurity #VulnerabilityScanner #BugBounty #bugbountytips #professor #the…

Hackers 🔥 This code is from an unpatched WordPress plugin 🤯 Can you see the vulnerability? 🔎

🔥Find critical vulnerabilities in js files✨ Looks inside this JS files: 🔍main, app, runtime, bundle, polyfills, auth, config, settings, local, dev, data, api, session, user,core, client, server, utils, base Read the full method 👇🏼 t.me/ShellSec/176

Since you guys are liking the concept of vulnerable code snippets, with help of some talented folks, we have a pool of vulnerable code snippets! Python ninjas, find the bug in the code! Code By: @ChetanyaKunndra #appsec #Python #infosecurity #codereview #bugbountytips

Hackers 🔥 Would you say that this code is secured from path traversal attacks?🤔

This software engineer was nearly hacked by a coding interview. I've never seen this attack channel before. Be careful out there, especially vibe coders.

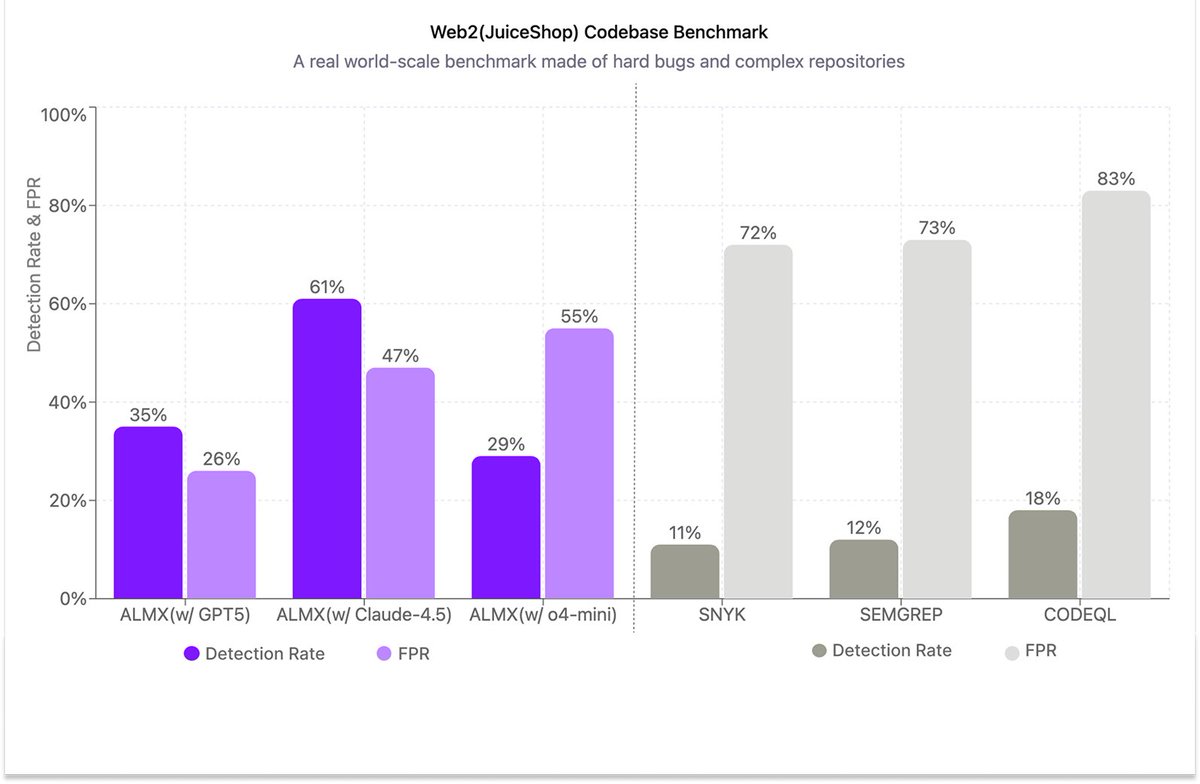
.@AlmanaxAI just released its latest cybersecurity evals! This is a comprehensive review of how different AI models compare at detection of code vulnerabilities. We also evaluated popular signature-based static analyzers. Here's what we found 👇🏽
My LLM analyzed a vulnerability in a Linux library and even created a PoC! This is expected to be used in Browser's Sandbox Escape as well. (Actually accessible) We will make this tool available for Android and browsers too! Actually my LLM was able to find several successful…

Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vulnerability? ->

POC A public collection of POCs & Exploits for the vulnerabilities I discovered github.com/jhftss/POC t.me/hackgit/7436

I am proud to share the announcement about our CodeMender project at @GoogleDeepMind, an agent that can automatically fix a range of code security vulnerabilities. From only a modest-compute run, our agent submitted 72 high-quality fixes to vulnerable code in popular codebases,…

When you're writing code, sometimes you may not even know it's broken or vulnerable until something bad happens. So Manish wrote this guide to help you identify common issues that'll make your code less safe. He talks about missing input validation, poor error handling, no rate…

Bypassing content-security-policy (CSP) of a targeted website by hiding malicious #JavaScript library inside a PNG image posted on Twitter. Nice read > secjuice.com/hiding-javascr… via @Menin_TheMiddle

Something went wrong.
Something went wrong.
United States Trends
- 1. Ohtani 222K posts
- 2. Dodgers 267K posts
- 3. World Series 62.9K posts
- 4. Emiru 8,417 posts
- 5. Carson Beck 16.7K posts
- 6. Miami 102K posts
- 7. Louisville 28.6K posts
- 8. Brewers 57.2K posts
- 9. Babe Ruth 3,572 posts
- 10. Nebraska 17.9K posts
- 11. Massie 32K posts
- 12. NOCHE IS BACK 31.1K posts
- 13. #HeartofTaehyung 28K posts
- 14. NLCS 63.8K posts
- 15. #SEVENTEEN_NEW_IN_LA 68.8K posts
- 16. #BostonBlue 7,897 posts
- 17. George Santos 86.8K posts
- 18. TwitchCon 24.3K posts
- 19. Sam Harris 1,102 posts
- 20. #OnTheRoadAgainLA 1,327 posts

























