#codingvulnerabilities search results
Interested in learning how to shore up exposure from #CodingVulnerabilities and prove #Resilience against #AppSec risks? Register for our March 7th webinar to learn how to build cyber capabilities across application development teams: hubs.ly/Q02mcMVN0

A shocking 79% of code goes out with known vulnerabilities! That’s why you need Codebashing to: 🔐Secure your code and open source components 📈Track, manage, and remediate at scale 💪Empower developers with training #CodingVulnerabilities #SecureCode #SecurityFirst

79% of code is shipped with known vulnerabilities. That’s why you need Codebashing to: 📈Gain full control and visibility 👨🏻🎓Identify areas that need improvement 💡Tailor secure code training to your needs #CodingVulnerabilities #Codebashing #FlexibleTrainingProgram
Interested in learning how to shore up exposure from #CodingVulnerabilities and prove #Resilience against #AppSec risks? Register for our March 7th webinar to learn how to build cyber capabilities across application development teams: hubs.ly/Q02mcMVN0

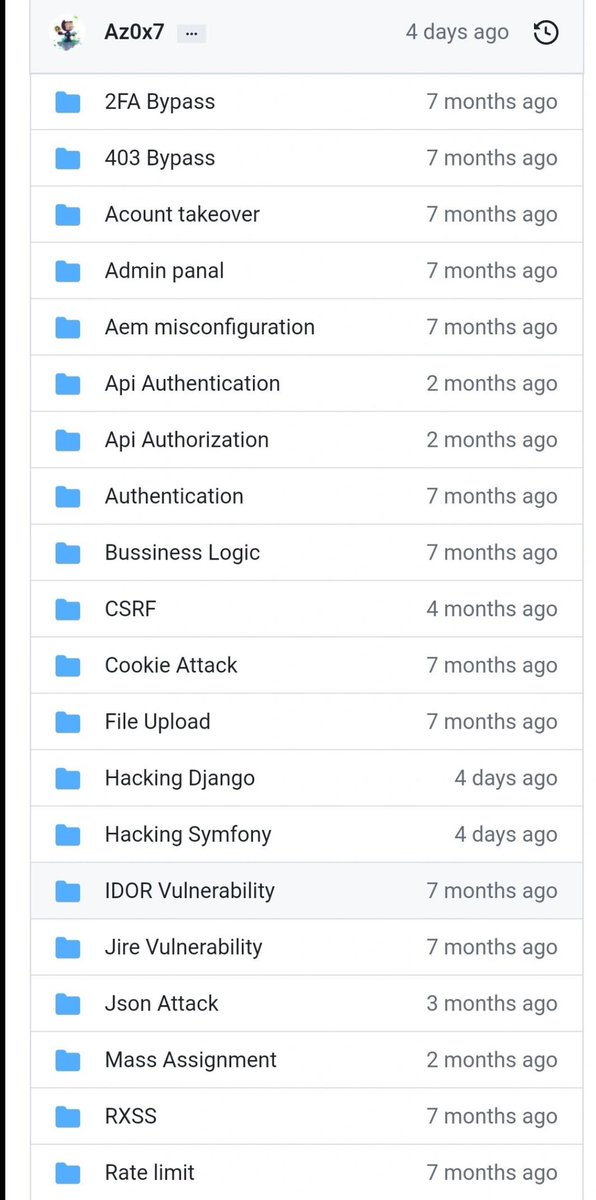
🤔Confused after collecting Subdomains. Then checkout this different types of Vulnerability checklist 👇 github.com/Az0x7/vulnerab… #bugbounty #bugbountytips #bughunting #penetrationtester #penetrationtesting #github
Digging up old path traversal vulnerabilities? 🕵️♂️ I built this scanner for CVE-2022-37122 to help you find these classic bugs on your authorized targets: Github Tool: github.com/bughuntar/CVE-… #Cybersecurity #VulnerabilityScanner #BugBounty #bugbountytips #professor #the…

Hackers 🔥 This code is from an unpatched WordPress plugin 🤯 Can you see the vulnerability? 🔎

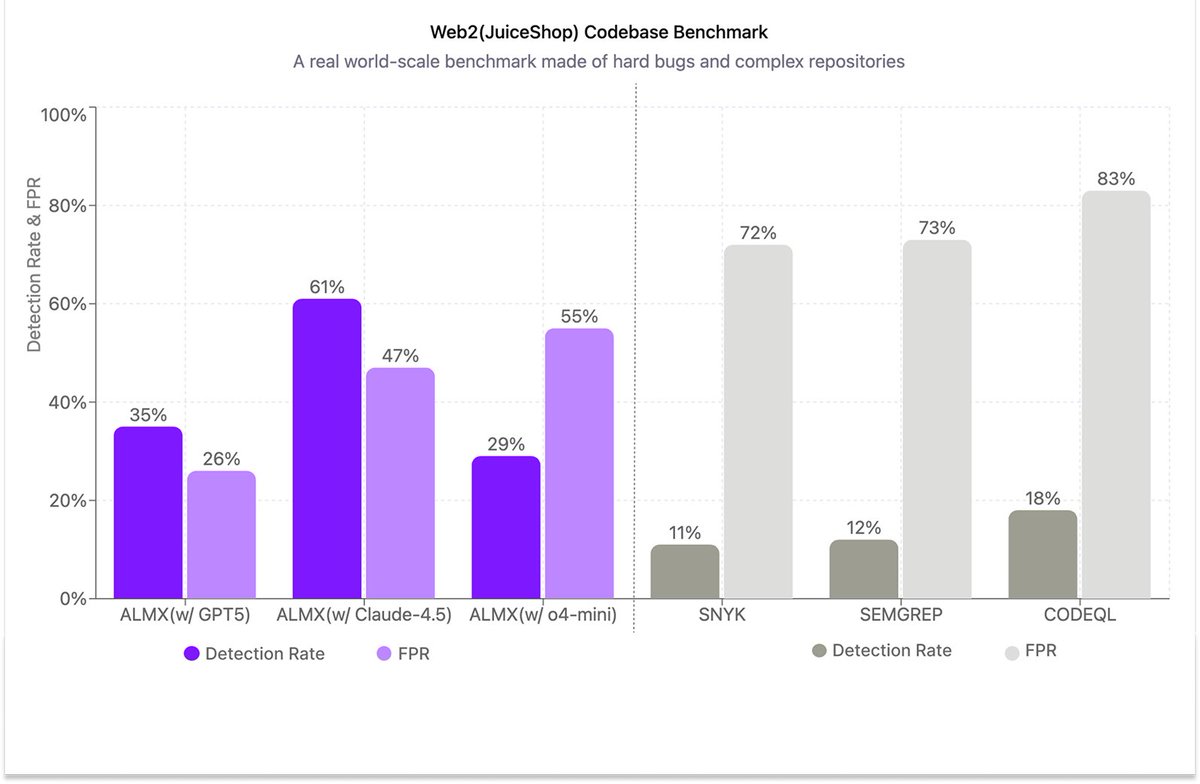
.@AlmanaxAI just released its latest cybersecurity evals! This is a comprehensive review of how different AI models compare at detection of code vulnerabilities. We also evaluated popular signature-based static analyzers. Here's what we found 👇🏽
🔥Find critical vulnerabilities in js files✨ Looks inside this JS files: 🔍main, app, runtime, bundle, polyfills, auth, config, settings, local, dev, data, api, session, user,core, client, server, utils, base Read the full method 👇🏼 t.me/ShellSec/176

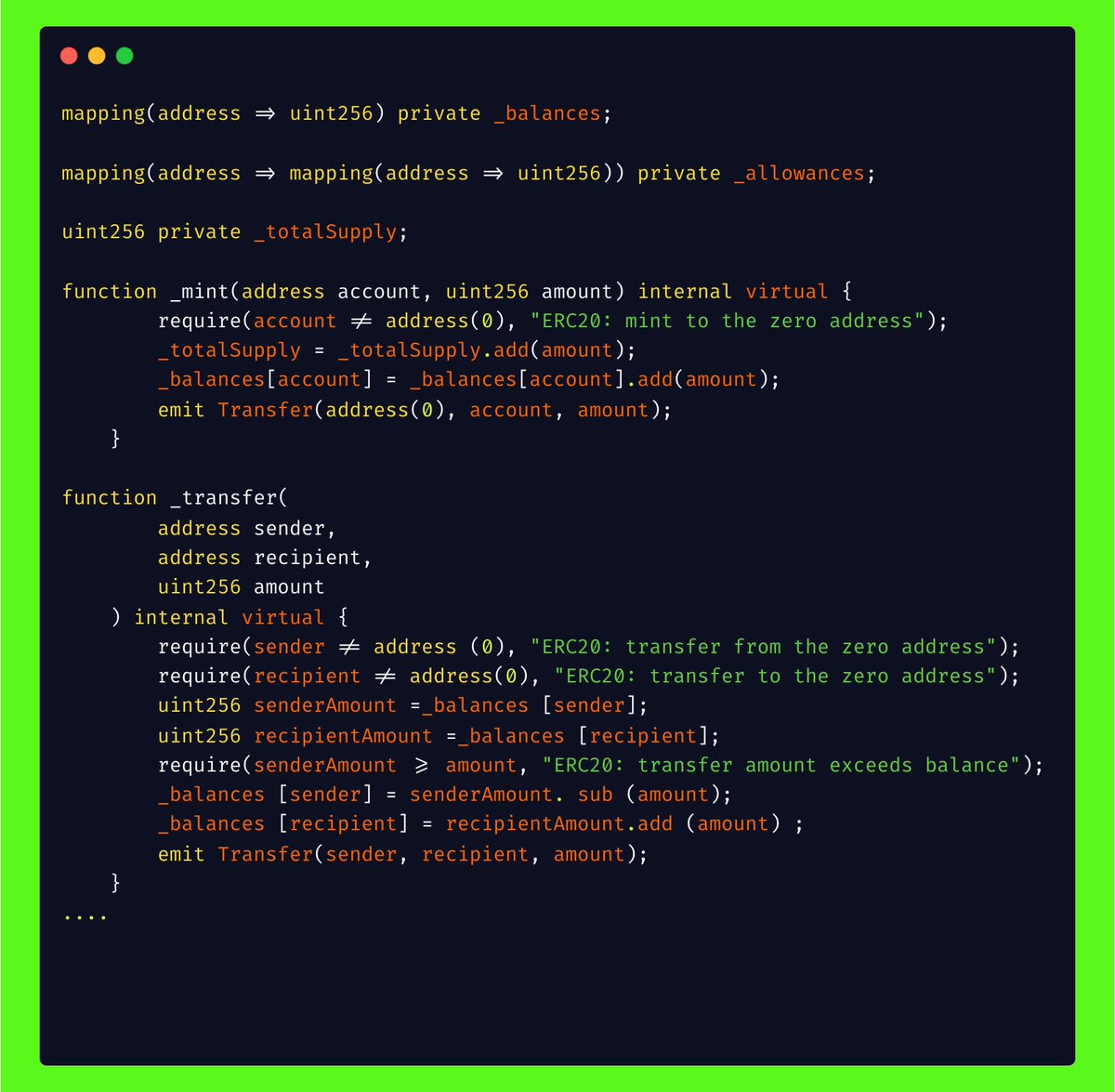
Since you guys are liking the concept of vulnerable code snippets, with help of some talented folks, we have a pool of vulnerable code snippets! Python ninjas, find the bug in the code! Code By: @ChetanyaKunndra #appsec #Python #infosecurity #codereview #bugbountytips

Hackers 🔥 Would you say that this code is secured from path traversal attacks?🤔

Hackers 🔥 This code contains at least 2 serious vulnerabilities. Can you spot them? 😋 What would be your exploit? 🤔
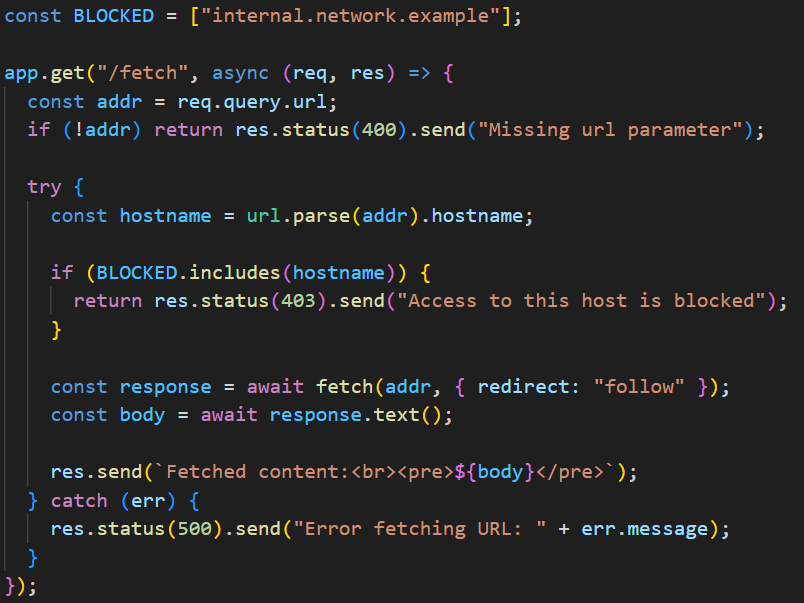
This software engineer was nearly hacked by a coding interview. I've never seen this attack channel before. Be careful out there, especially vibe coders.

Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vulnerability? ->

POC A public collection of POCs & Exploits for the vulnerabilities I discovered github.com/jhftss/POC t.me/hackgit/7436

Bypassing content-security-policy (CSP) of a targeted website by hiding malicious #JavaScript library inside a PNG image posted on Twitter. Nice read > secjuice.com/hiding-javascr… via @Menin_TheMiddle

CVE-2023-31102: 7-Zip Remote Code Execution Vulnerability securityonline.info/cve-2023-31102… #opensource #pentesting #infosec #security #vulnerability

Something went wrong.
Something went wrong.
United States Trends
- 1. Ohtani 200K posts
- 2. Dodgers 246K posts
- 3. Dodgers 246K posts
- 4. Carson Beck 16.1K posts
- 5. $SAWA 1,658 posts
- 6. Miami 99.7K posts
- 7. Louisville 27.6K posts
- 8. Nebraska 17.7K posts
- 9. Brewers 54.9K posts
- 10. Babe Ruth 3,126 posts
- 11. NLCS 57.6K posts
- 12. #SmackDown 56.1K posts
- 13. #BostonBlue 7,712 posts
- 14. Rhule 4,529 posts
- 15. Emiru 4,849 posts
- 16. 3 HRs 10.1K posts
- 17. Minnesota 48K posts
- 18. George Santos 79.5K posts
- 19. 10 Ks 4,347 posts
- 20. Massie 28.1K posts