#compromisedcredentials search results
🛡️ Credentials are exposed well before breaches occur. OdinEye continuously monitors hidden sources to detect compromised emails, passwords, tokens and session cookies. 🔍 Core Feature #3: Combolists & Stealer Logs Analysis #StealerLogs #CompromisedCredentials #OdinEye #DNGTech

🚨 Compromised Credentials: A Major Threat to Your Security 🚨 In 2023, Group-IB, a global cybersecurity leader, suffered a massive data breach that exposed tens of thousands of accounts, including credentials linked to Chat GPT. #CompromisedCredentials #Cybersecurity

🔑 Compromised credentials cause 80%+ of breaches. Learn how Seceon detects & stops credential misuse in real time. 👉 seceon.com/compromised-cr… #CyberSecurity #CompromisedCredentials #Seceon

Did you know that #CompromisedCredentials are the most common initial attack vector? According to the 2021 IBM Cost of a Data Breach Report, compromised credentials were responsible for 20% of breaches. #cybersecurity

RT Most firms not aware about their risky password behavior buff.ly/2MHZ7uL #ato #compromisedcredentials #passwords #identity
RT Researcher finds email accounts of top government officials ‘compromised’ buff.ly/317Bt1f #compromisedcredentials #passwords #dataleak #iam #india

Just how many passwords in your system are already compromised? Find out now: zcu.io/EASr #CyberSecurityTip #CompromisedCredentials

Think your Active Directory passwords are safe? With Enzoic’s Password Auditor, you can quickly scan your AD environment for weak, reused, or compromised passwords—at no cost. hubs.ly/Q03HJhvJ0 #PasswordSecurity #ActiveDirectory #CompromisedCredentials

Credentials can become compromised at any time. You need a service that will alert you as soon as they do - which means you need to be screening on an ongoing basis: zcu.io/Op2O #Cybersecurity #compromisedcredentials
How can companies help their employees secure their passwords? The most efficient password management tactic is to screen all #passwords against a list of commonly known and exposed credentials. #compromisedcredentials #ITsecurity #infosec

Why is #MFA so important? With #CompromisedCredentials at the top of the root cause ranking for 2023, nearly half of the cases in our recent Active Adversary report lacked MFA. Learn how to raise your defenses: bit.ly/49xRqiE

Businesses can do more than to protect users than they can do on their own. Here's how: zurl.co/7Du5 #Cybersecurity #compromisedcredentials #bestpractices #ITsecurity #InfoSec #passwords

In this day and age, you need a dynamic password #blacklist. Generic just isn't cutting it: zurl.co/YkQV #compromisedcredentials #passwords #cybersecurity #ActiveDirectory #cybersecuritytip

Businesses can do more than to protect users than they can do on their own. Here's how: zcu.io/qvby #Cybersecurity #IT #compromisedcredentials

This day and age, you need a customized password blacklist. Generic just isn't cutting it: zcu.io/NQI7 #compromisedcredentials #passwords #cybersecurity
Check how data can be applied to strengthen companies’ defenses in some of the aforementioned areas. zcu.io/udkO #threatdetection #compromisedcredentials #passwords

#CompromisedCredentials are one of the main entry points for #threat actors, cross-industry. Lock down your organizational #cybersecurity by screening for them now. zurl.co/YGtN #passwords

#CompromisedCredentials are one of the main entry points for #threat actors, cross-industry. Lock down your organizational #cybersecurity by screening for them now. zcu.io/uK6v

Just how many passwords in your Active Directory system are already compromised? Find out now by running a free scan: zurl.co/kGlz #CyberSecurityTip #CompromisedCredentials #ActiveDirectory #passwordaudit

Enzoic continuously screens for both unsafe passwords and compromised full credentials reducing the risk of a cyberattack. zcu.io/lR6a #password #compromisedcredentials #ITsecurity #InfoSec

The use of fake or compromised accounts, including those that appear verified, makes it difficult for people to distinguish legitimate interactions from fraudulent ones, further eroding trust in online platforms and communications.
Compromised indeed! Ditching the libertarian facade for a more ' transactional' R, and an insider trader clinging to power for their pension perks. #Resign
Now marked as Compromised on my index (top is the worst) Constructed Captured Compromised * Corporate Credible
A single error can cost someone a job, delay hiring, or damage trust between employers and applicants. Accurate, user-controlled credentials are not just convenient. They are essential.

Ever wondered how fast your credentials could end up for sale? 🕵️ Between AI-powered phishing and partner weaknesses, the attack paths are multiplying and the prices are dropping. Help your IT team stop criminal activity before it becomes a headline: hubs.la/Q03Vr_lp0
newhorizons.com
The Dark Web Threat You Might Be Missing (And How Criminals Cash In)
Key Takeaways Hidden Networks: Dark web requires special tools and deliberate access Criminal Economy:...
Compromised VPN Credentials Leading Attack Vector in Ransomware Campaigns zurl.co/3HVSt
hipaajournal.com
Compromised VPN Credentials Leading Attack Vector in Ransomware Campaigns
Several cybersecurity firms have tracked a surge in ransomware attacks in Q3, 2025, as groups such as Akira, Qilin, and Inc Ransom have stepped up their Compromised credentials for VPNs and remote...
The confidence trap holding #security back buff.ly/GLoSoQF @HelpNetSecurity @ImmersiveLabs #tech #cybersecurity #infosec #business #leadership #management #cyberattacks #databreaches #CISO #CIO #CTO #CEO #incidentresponse #cyberresilience

Compromised credentials pose an extraordinary risk for organizations. Dark web monitoring can provide real-time awareness of compromised credentials so organizations can develop a plan for mitigating that risk. #DarkWeb stuf.in/bhjdwi
or compromised integrity—deepens mistrust. When those entrusted with authority fail to speak with moral clarity, their silence becomes a form of complicity, whether intended or not. And because many of these leaders share cultural or religious affiliations with violent actors
This time around it's not only compromised but fake and downgraded
BREAKING: 🇺🇸 🇸🇦 🇮🇱 Trump to sell DOWNGRADED version of the F-35 to Saudi Arabia after saying he wouldn’t. Trump wants ISRAELI fighter jets to maintain their superiority in the region. Disgusting.

🛡️ Credentials are exposed well before breaches occur. OdinEye continuously monitors hidden sources to detect compromised emails, passwords, tokens and session cookies. 🔍 Core Feature #3: Combolists & Stealer Logs Analysis #StealerLogs #CompromisedCredentials #OdinEye #DNGTech

Cursor Issue Paves Way for Credential-Stealing Attacks share.google/rXs78utrVORz2B…
Research shows 460,000 compromised credentials in FTSE 100 firms, urging vigilance with monitoring and rapid invalidation. infosecurity-magazine.com/news/half-mill… #IncidentResponse #RedTeam #PenTesting #FTSE100 #CredentialStuffing #Infostealer
infosecurity-magazine.com
Half a Million Stolen FTSE 100 Credentials Found on Criminal Sites
Socura finds 460,000 compromised credentials belonging to FTSE 100 company employees
Cursor Issue Paves Way for Credential-Stealing Attacks darkreading.com/vulnerabilitie…
Why Your Enterprise Credentials Are Still the Weakest Link #Cybersecurity csecweekly.com/p/why-your-ent…
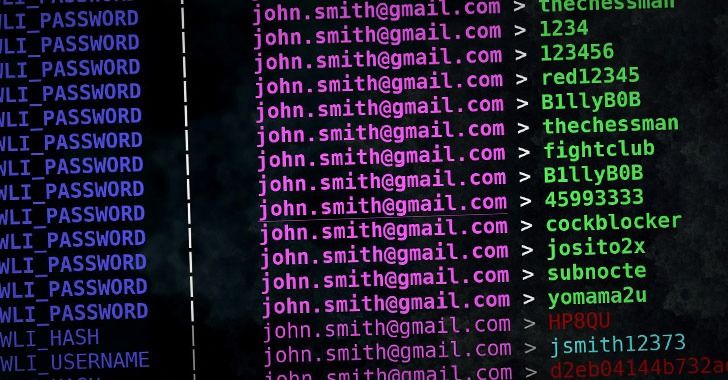
Just look at this! Emphasis on HEAVILY COMPROMISED!
A General in the Nigerian Army said a repentant Boko Haram can become the President of Nigeria. Bro the Nigerian military is heavily compromised.
🔑 Compromised credentials cause 80%+ of breaches. Learn how Seceon detects & stops credential misuse in real time. 👉 seceon.com/compromised-cr… #CyberSecurity #CompromisedCredentials #Seceon

🛡️ Credentials are exposed well before breaches occur. OdinEye continuously monitors hidden sources to detect compromised emails, passwords, tokens and session cookies. 🔍 Core Feature #3: Combolists & Stealer Logs Analysis #StealerLogs #CompromisedCredentials #OdinEye #DNGTech

🚨 Compromised Credentials: A Major Threat to Your Security 🚨 In 2023, Group-IB, a global cybersecurity leader, suffered a massive data breach that exposed tens of thousands of accounts, including credentials linked to Chat GPT. #CompromisedCredentials #Cybersecurity

Love'em or Hate'em, #Passwords Are Here to Stay. Read the Business Impact Brief by 451 Research. zcu.io/9BQu #compromisedcredentials #passwordsecurity #infosec #ITsecurity

RT Most firms not aware about their risky password behavior buff.ly/2MHZ7uL #ato #compromisedcredentials #passwords #identity

Why is #MFA so important? With #CompromisedCredentials at the top of the root cause ranking for 2023, nearly half of the cases in our recent Active Adversary report lacked MFA. Learn how to raise your defenses: bit.ly/49xRqiE

Think your Active Directory passwords are safe? With Enzoic’s Password Auditor, you can quickly scan your AD environment for weak, reused, or compromised passwords—at no cost. hubs.ly/Q03HJhvJ0 #PasswordSecurity #ActiveDirectory #CompromisedCredentials

Businesses can do more than to protect users than they can do on their own. Here's how: zurl.co/7Du5 #Cybersecurity #compromisedcredentials #bestpractices #ITsecurity #InfoSec #passwords

🕵️♂️ Dark Xposed's advanced technology increases the chances of discovering compromised credentials, helping our clients stay protected from cyber attacks. #cybersecurity #compromisedcredentials

How do you know which #compromisedcredentials can actually cause damage to your organization? Our Product Manager, Eli Domoshnitsky, put together some helpful tips for #security teams to figure out which compromised credentials to focus on, via @cloudsa: okt.to/zub0CE

Credentials can become compromised at any time. You need a service that will alert you as soon as they do - which means you need to be screening on an ongoing basis: zcu.io/Op2O #Cybersecurity #compromisedcredentials

Just how many passwords in your system are already compromised? Find out now: zcu.io/EASr #CyberSecurityTip #CompromisedCredentials

How can companies help their employees secure their passwords? The most efficient password management tactic is to screen all #passwords against a list of commonly known and exposed credentials. #compromisedcredentials #ITsecurity #infosec

We're excited to announce our partnership with @SpyCloud! Combining Pentera’s automated #penetration testing with SpyCloud’s data, organizations are provided with a fast path to identify and prioritize #exploitablethreats from #compromisedcredentials. okt.to/JFOZVm

Did you know that #CompromisedCredentials are the most common initial attack vector? According to the 2021 IBM Cost of a Data Breach Report, compromised credentials were responsible for 20% of breaches. #cybersecurity

RT Researcher finds email accounts of top government officials ‘compromised’ buff.ly/317Bt1f #compromisedcredentials #passwords #dataleak #iam #india

In this day and age, you need a dynamic password #blacklist. Generic just isn't cutting it: zurl.co/YkQV #compromisedcredentials #passwords #cybersecurity #ActiveDirectory #cybersecuritytip

Police Arrest 21 WeLeakInfo Customers Who Bought Breached Personal Data buff.ly/2WI38o6 #passwords #databreach #compromisedcredentials #ato #identity
#CompromisedCredentials are one of the main entry points for #threat actors, cross-industry. Lock down your organizational #cybersecurity by screening for them now. zcu.io/uK6v

Businesses can do more than to protect users than they can do on their own. Here's how: zcu.io/qvby #Cybersecurity #IT #compromisedcredentials

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 37.9K posts
- 2. Nimmo 12.8K posts
- 3. Trevor Lawrence 2,610 posts
- 4. Mets 19K posts
- 5. Browns 53.7K posts
- 6. Ceedee 7,290 posts
- 7. Semien 8,442 posts
- 8. #FlyEaglesFly 11.5K posts
- 9. Colts 40.2K posts
- 10. Giants 87.6K posts
- 11. Chiefs 82.7K posts
- 12. Shedeur 53.4K posts
- 13. Gibbs 18.5K posts
- 14. Turpin 3,223 posts
- 15. Jerry Jeudy 4,805 posts
- 16. Geno 9,126 posts
- 17. Jameis 43.9K posts
- 18. Pickens 5,496 posts
- 19. Tomlin 9,221 posts
- 20. Lions 63.8K posts